-
Posts
9258 -
Joined
-
Last visited
-
Days Won
371
Everything posted by anyweb
-

Build and Capture not installing applications [2012 R2]
anyweb replied to SMSNewb's topic in Configuration Manager 2012
your client is in a workgroup so being in an AD SITE boundary will not work ! try the boundary trick, it takes only a few minutes to do, i had the Execution status received: 24 (Application download failed ) InstallApplication 5/7/2014 2:02:01 PM 2988 (0x0BAC) problem and it solved it for me. -

looking for help to start learning USMT with sccm 2012
anyweb replied to P3nnyw1se's question in How do I ?
start by learning how USMT works, and to do so i'd recommend you read this old post i wrote. Create two custom task sequences as it describes and start testing capture user state (get that working first) and once it's working 100% everytime, then test restoring that data in a separate task sequence, once you have mastered that, you can start looking at the complexity that there is in refresh scenarios. You obviously wobn't be using USMT 3 listed in the guide, however you can use USMT as provided in your ADK (assesment and deployment kit), here are the usmt requirements http://technet.microsoft.com/en-us/library/hh824913.aspx and here's the version of ADK used in your version of Configuration Manager - http://www.microsoft.com/en-us/download/details.aspx?id=30652 -

having to 'clean' in diskpart before f12
anyweb replied to P3nnyw1se's topic in Configuration Manager 2012
if you use the mdt integrated task sequences they have multiple steps for dealing with partitions, are you ? -
SCEP should be able to automaticallyt uninstall Microsoft Security Essentials, however i'd test it first on a test system and see what happens.
-
it's pretty easy, here's how, follow Justins guide below. http://setupconfigmgr.com/installing-a-secondary-site-configuration-manager-configmgr-2012-sp1/ cheers niall
-

Build and Capture not installing applications [2012 R2]
anyweb replied to SMSNewb's topic in Configuration Manager 2012
is your device in a boundary ? I usually create a boundary that is a one-ip iprange for my build and capture virtual machine, -
this should give you some ideas (it's for USMT 3.x and CM2007 but you'll see past that) http://www.windows-noob.com/forums/index.php?/topic/918-how-can-i-use-usmt-3-0-1-in-sccm-2007-sp1/
-

No Task Sequence Advertised for Unknown Computers
anyweb replied to tainted's topic in Configuration Manager 2012
search for the mac address of the computer you are booting in Configuration Manager, if it's found, then the device is not unknown, it's known. -
that is not the entire log, are there no more logs in the C:\Windows\Ccmsetup folder or subfolders ?
-
you are either managed by Intune, or ConfigMgr not both, so users created in Windows Intune (before or after Windows Intune is integrated with Configuration Manager) will remain in the Windows Intune users group in the Intune Account Portal, however users synched via dirsync will not. Most if not all of your management after you've enabled Intune Integration should be in the Configuration Manager console.
-
no what did you try exactly, you need to give more details ok ?
-
what does your ccmsetup.log file reveal ?
-

Customization of Internet Explorer 9 (HKCU key!) problems
anyweb replied to Atomic12's topic in Configuration Manager 2007
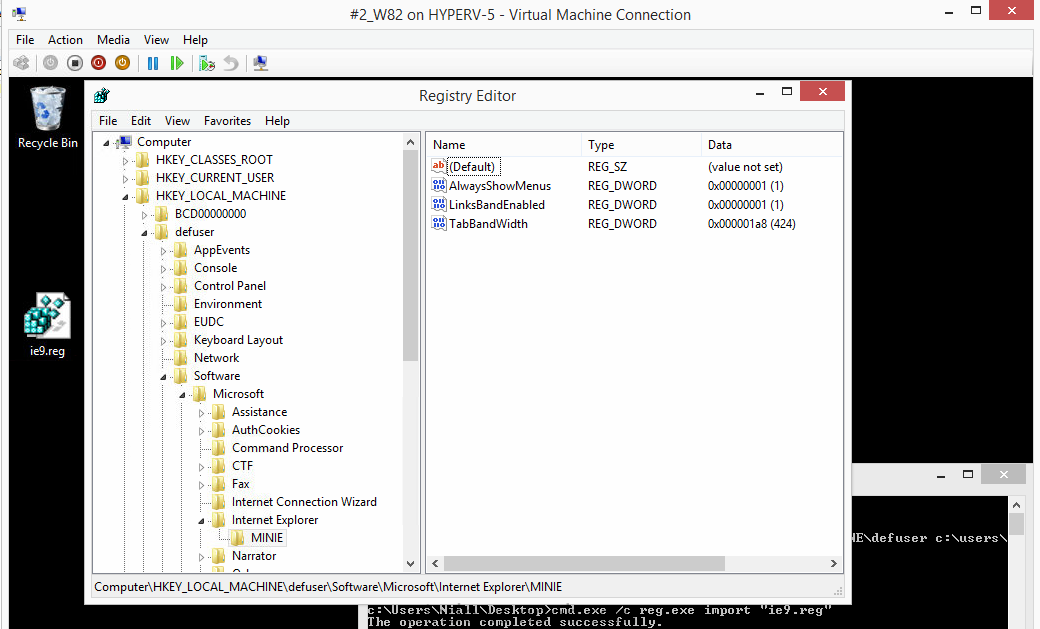
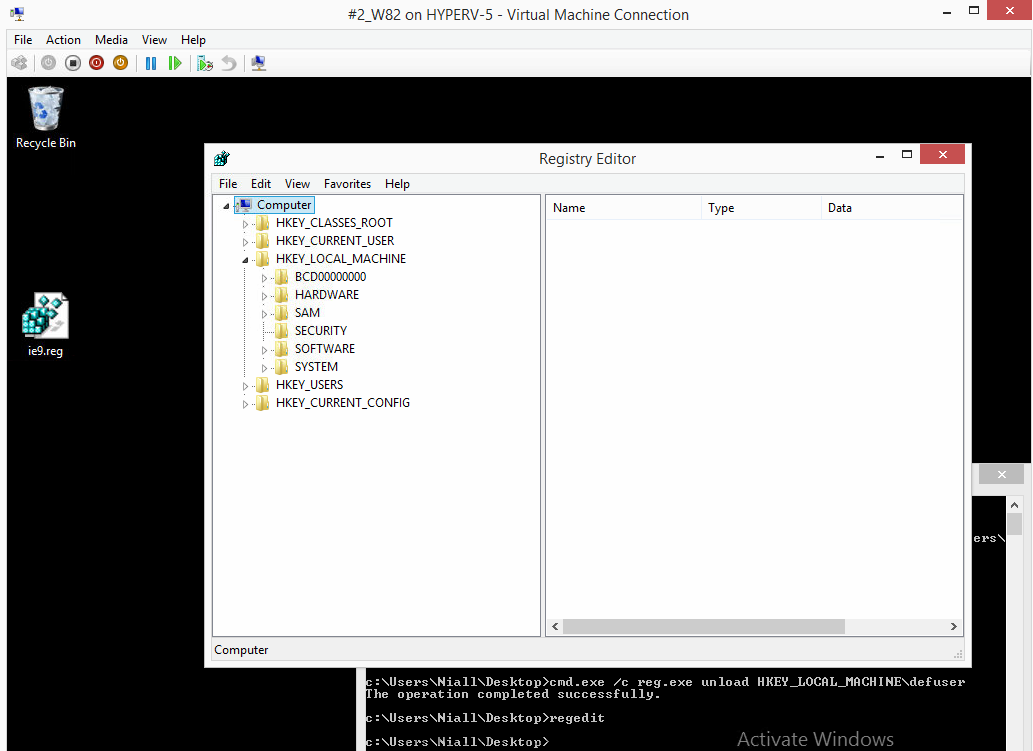
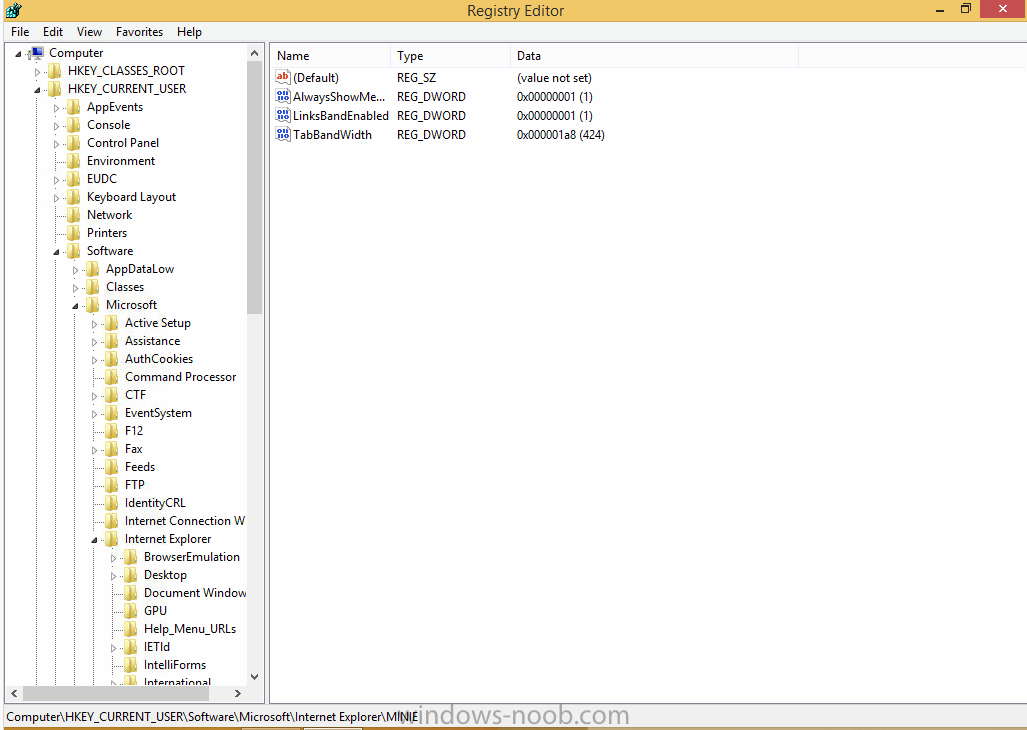
i've just tested your reg key with the defuser path in it, and it works just fine..before i do the final command (reg unload) i verified the defuser path in the registry, see screenshot below, the default user hive is loaded in hklm\defuser...., i applied your reg key to that defuser hive. then i closed regedit (as you can't unload when it's open), and then after i unload the registry i open it again to see how things look, notice no defuser path, that is correct, now, you are probably wondering where the HKCU settings have gone, well they are applied to 'default user' hive (all new users) so login to this computer as a new user and then check the hkcu path for your changes... and the setting is indeed in the registry as you see above, starting IE shows the change also. So your reg key works, the defuser process applies the change for all users (all new user profiles created on a machine) whereas as pure HKCU reg key (with no defuser references) will make the change for the current logged on user only. cheers niall- 18 replies
-
- HKCU
- Customization
-
(and 2 more)
Tagged with:
-

Customization of Internet Explorer 9 (HKCU key!) problems
anyweb replied to Atomic12's topic in Configuration Manager 2007
go back a few steps, in the link i posted have you verified that it applies any key's to the hkcu ? if you follow my guide without any spelling mistakes does it work or not ?, for now forget about IE, and just try creating a test reg key under hkcu if you don't commit the changes (as in my guide - cmd.exe /c reg.exe unload HKEY_LOCAL_MACHINE\defuser) then the reg key you are applying to hklm will stay in hklm and not move to hkcu as regards your reg.exe command,. have you verified that it is correct ?- 18 replies
-
- HKCU
- Customization
-
(and 2 more)
Tagged with: