-
Posts
9176 -
Joined
-
Last visited
-
Days Won
366
Everything posted by anyweb
-
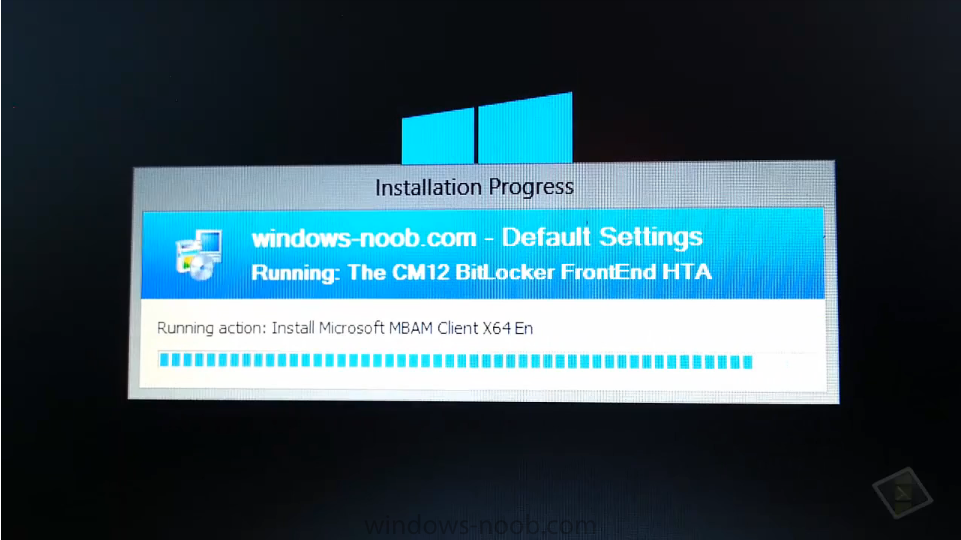
here's a live demo I did in Seattle during the 2013 Global MVP summit, I demo'd the CM12 BitLocker FrontEnd HTA to a few other Configuration Manager MVP's and Rob Marshall decided to video it ! so here's the result, the lighting quality is a bit low (video'd with a mobile phone.), apologies for that and we were both tired after a long day attending sessions, however it was an on-the-spur-of-the-moment thing and we wanted to share the experience In this demo I did a refresh from Windows 8 BitLockered to Windows 8 BitLockered using an MBAM 2.0 backend and of course using Configuration Manager 2012 Service Pack 1 cheers ! niall
-
what does your scanstate.log reveal ?
-
can you attach the logs in the root of C: which are created by setup
-
i moved your post from a BitLocker post to here, why did you post your question there ? raise a new topic when posting about something unrelated please.... as regards your problem, please explain your issue, is it related to Bitlocker, yes/no ?
-

SCCM SP1 OSD Deployment to Only media and PXE
anyweb replied to jdmiller's topic in Configuration Manager 2012
did you delete the task sequences or the deployments ? -
Developers have had early access to Internet Explorer 10 for Windows 7 for a few months now, but Microsoft is making the final release available to consumers and businesses today. Available in 95 languages, Windows 7 users will be auto upgraded to IE10 in the coming weeks, with the initial push targeted at IE10 Release Preview users. Internet Explorer 10 on Windows 7 includes improved JavaScript performance, and a focus on battery life improvements for mobile PCs. Although Internet Explorer 10 has been available on Windows 8 since October 26th, Microsoft opted for a delayed Windows 7 schedule to ensure the release was fully ready, a decision that drew some criticism from users waiting on an updated browser. Windows 7 users will now get integrated spell checking and auto-correct within IE10, as well as improved support for web standards like the latest CSS3 improvements. The user interface in IE10 for Windows 7 is largely the same as IE9, so users won't get the fullscreen experience that's available in Windows 8. Nevertheless, Internet Explorer 10 is now available to download for Windows 7. via > http://www.theverge.com/2013/2/26/4029306/internet-explorer-10-windows-7-download?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+WinRumors+%28WinRumors%29
-

SCCM 2012 or SCCM 2012 SP1 on initail install?
anyweb replied to pnyce24's topic in Configuration Manager 2012
I'd recommend you set it up in a lab first (always recommended) and test your hardware with it, shouldn't take too long and will reveal any problems you may/may not have.- 5 replies
-
- sccm 2012 SP1
- sccm 2012
-
(and 1 more)
Tagged with:
-

how to deploy applications in untrusted forest
anyweb replied to ankurpathak's topic in Configuration Manager 2012
what does the MSI log file of the application you are installing, tell you about that (very common) error ? -

SCCM 2012 or SCCM 2012 SP1 on initail install?
anyweb replied to pnyce24's topic in Configuration Manager 2012
SP1 offers so many new features that it's what i'd recommend, however be aware that the new ADK requirements means you have WinPE4 and that means that hardware older than 3 years may have problems PXE booting... until Johan Arwidmark posts his workaround- 5 replies
-
- sccm 2012 SP1
- sccm 2012
-
(and 1 more)
Tagged with:
-

Non OS Deployment task sequence HTA splash screen
anyweb replied to JeffPitt's topic in Configuration Manager 2007
and for those that don't know, the reason your users never saw the HTA popup originally is because task sequences run in System Context, whereas running a package can run in User context. -
is this a build and capture task sequence or a deploy task sequence ? can you post the SMSTS.log and the ccmsetup.log and client.msi.log files please
-
Introduction One of the user definable sources for updates for Endpoint Protection definition updates is an UNC file share, but how you populate that share can mean success or failure when it comes to deploying definition updates from a UNC file share for System Center 2012 Endpoint Protection using System Center 2012 Configuration Manager SP1. In addition to populating the share correctly, you also need to define your AntiMalware Policy UNC path source correctly otherwise the definition updates will never be found. In this post I’ll explain how you can set this up and how to verify it’s working. Step 1. Create a Share and populate with folders First of all on your chosen server create a folder called SCEP_UNC_DEFS and share it to Domain Users and Domain Computers. Beneath this folder create another folder called Updates with two sub folders for both architectures like so Step 2. Populate the share with definition updates Now that we’ve created our template folder structure we need to populate it with the actual definition updates for the prospective architecture. For x64, download the following files and place them in the X64 folder. Antimalware full definitions (http://go.microsoft.com/fwlink/?LinkID=121721&clcid=0×409&arch=x64) Antimalware delta definitions (http://go.microsoft.com/fwlink/?LinkId=211054) Network-based exploit definitions (http://go.microsoft.com/fwlink/?LinkId=197094) For x86, download the following files and place them in the X86 folder. Antimalware full definitions (http://go.microsoft.com/fwlink/?LinkID=121721&clcid=0×409&arch=x86) Antimalware delta definitions (http://go.microsoft.com/fwlink/?LinkId=211053) Network-based exploit definitions (http://go.microsoft.com/fwlink/?LinkId=197095) Step 3. Create a new Antimalware Policy In the Assets and Compliance workspace, expand Endpoint Protection, select Antimalware Policies, right click and choose Create AntiMalware Policy, give it a name like Custom SCEP UNC DEF policy and select Definition Updates from the available choices (you may of course add more sections but for the purpose of this post this is sufficient). Click on Set Paths and enter the path to the Updates folder which is a sub directory of the SCEP_UNC_DEFS file share, click on Add when done. eg: \\server\scep_unc_defs\updates Next click on Set Source, make sure to select Updates from UNC Shares and use the UP button to bring this to the top choice (if you want it as the first option checked when more than one source is selected). Step 4. Create a collection to target the Antimalware Policy Right click on Devices Collections, and choose create device collection, give it a suitable name like Endpoint Protection UNC_DEFS you can populate it however you want (queries or direct membership) and then move it to somewhere suitable if required. Step 5. Change the Antimalware Policy priority right click on your new antimalware policy and choose Increase Priority, make this the highest priorty you can as SP1 uses Client side merge of AntiMalware policies and we want this source for definition updates to take priority on any computers in this collection. Step 6. Deploy the Antimalware Policy Right click on the AntiMalware Policy and choose Deploy point it to the collection we created above Step 7. Verify the UNC file share is being used Now everything is in place to deploy definition updates via an UNC file share, but we need to prove that don’t we. On a Windows client computer that you’ve added to our collection we created above, run the following Configuration Manager client action, Machine Policy Retrieval & Evaluation Cycle. This will ensure that our client has the latest Antimalware Policies targeted to it including the one we created above, to verify that our policy is indeed targeted to this computer please see this post, you should see something similar to the following in the registry, depending on what Antimalware Policies are applied to this client however we are only interested in our Custom SCEP UNC Def policy and it is indeed listed below. Do not proceed with the verification until your Windows client has our Custom SCEP_UNC_Def policy applied. Once done, open an Administrative command prompt and browse to the following folder C:\Program Files\Microsoft Security Client\ and execute the following command MpcmdRun.exe -SignatureUpdate as per below screenshot. If all went well then you’ll see Signature Update Finished. Open the following log file for final verification C:\Users\Administrator\AppData\Local\Temp\MpCmdRun.Log and you should see search started (UNC Share) along with the following text, Update Completed Successfully. (hr: 0×00000000) You can open the SCEP client, click on the updates tab and review the Definition Update versions for further verification. And there you have it, your SCEP client has updated it’s definition updates from your UNC file share as specified in your Custom Antimalware Policy, and you’ve proven the fact !. Troubleshooting Tip: If you fail to get this to work and see the following error instead, Error: Signature Update failed with hr=80070002 then verify you are pointing at the correct UNC File share directory as listed in my guide above then try again. Summary System Center 2012 Configuration Manager SP1 is a powerful management solution and you can use custom antimalware policies to update Endpoint Protection via multiple or single sources, including using UNC file shares, this ability gives great flexibility and control over how you want those definition updates deployed. If you’d like to automate the download of those definition updates please review the following post. until next time, from Seattle, cheers niall
-

SCCM SP1 OSD Deployment to Only media and PXE
anyweb replied to jdmiller's topic in Configuration Manager 2012
ok can you clarify the below as the new option comes with SP1., -

High CPU Usage on SCCM's SQL Instance
anyweb replied to Aurock's topic in Configuration Manager 2012
do your component logs reveal any problems ?- 13 replies