-
Posts
9254 -
Joined
-
Last visited
-
Days Won
369
Everything posted by anyweb
-
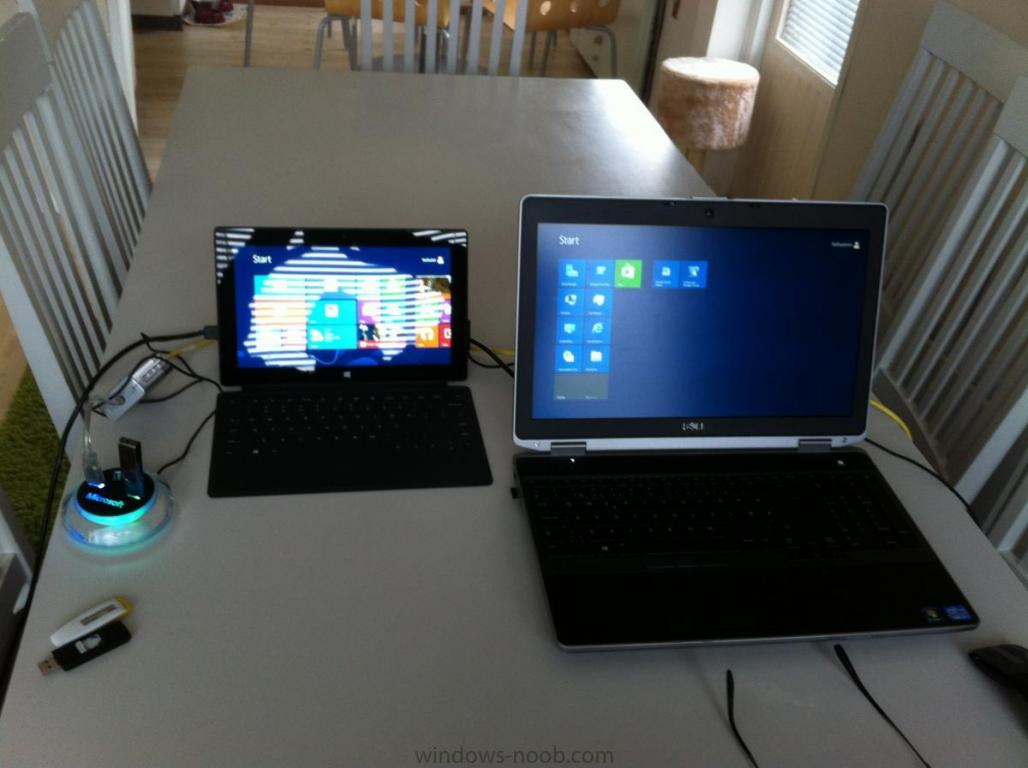
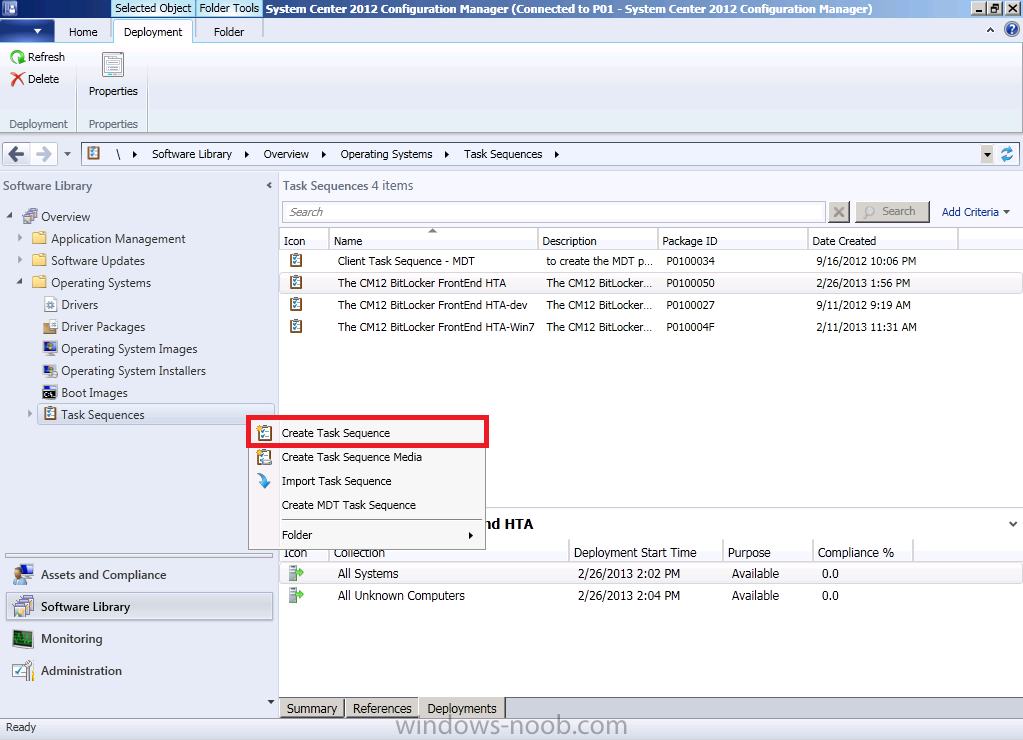
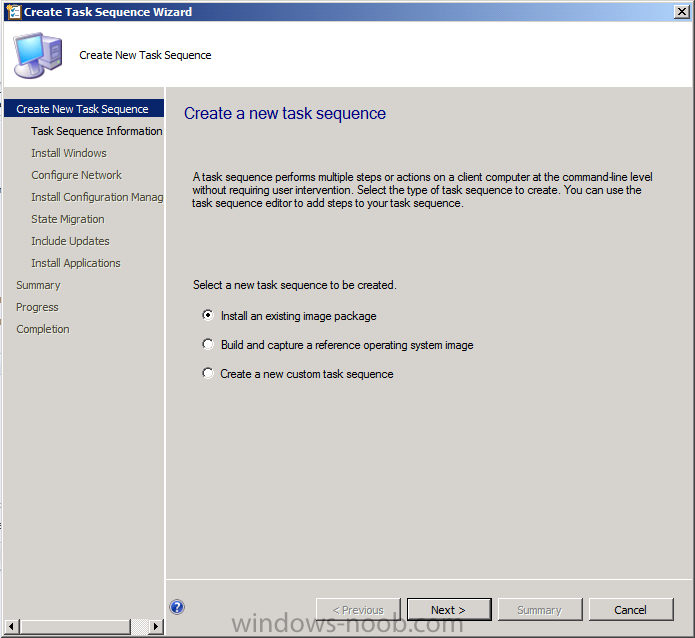
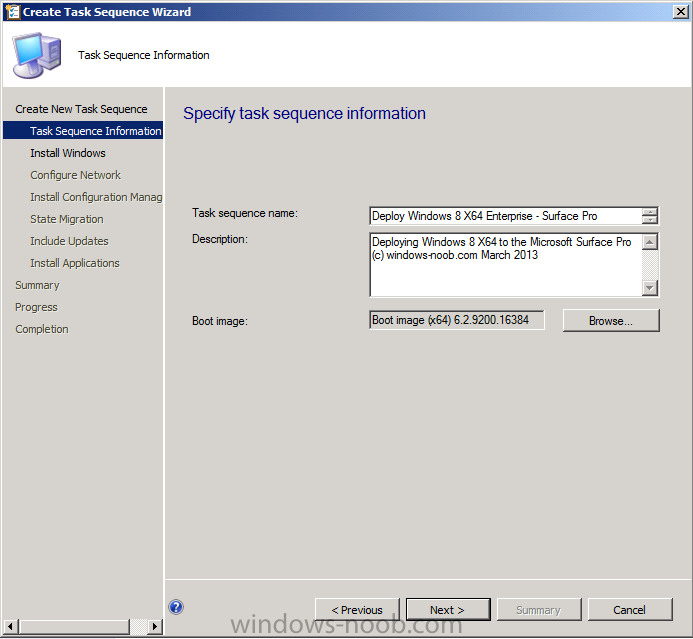
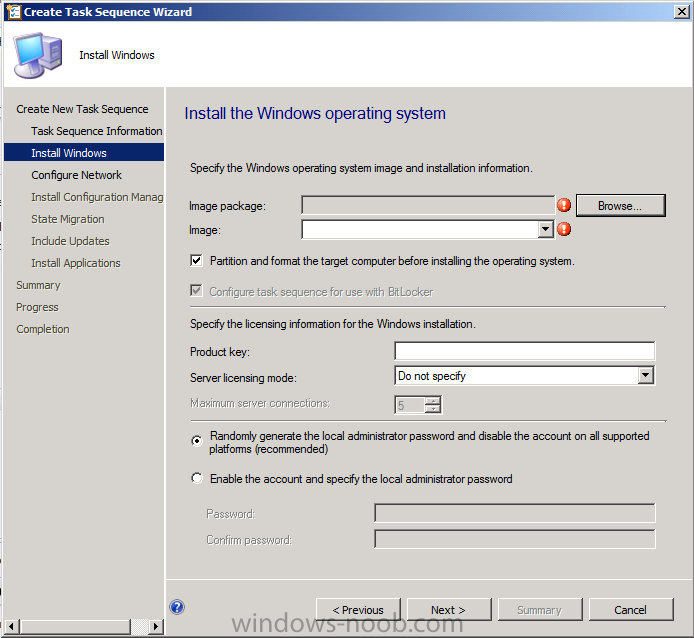
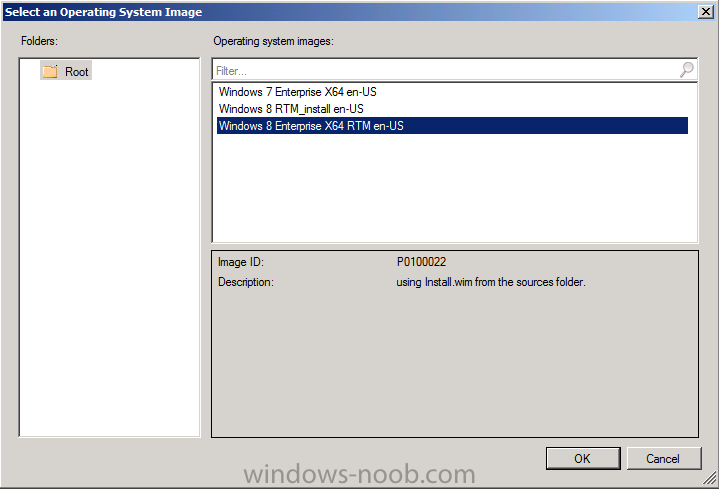
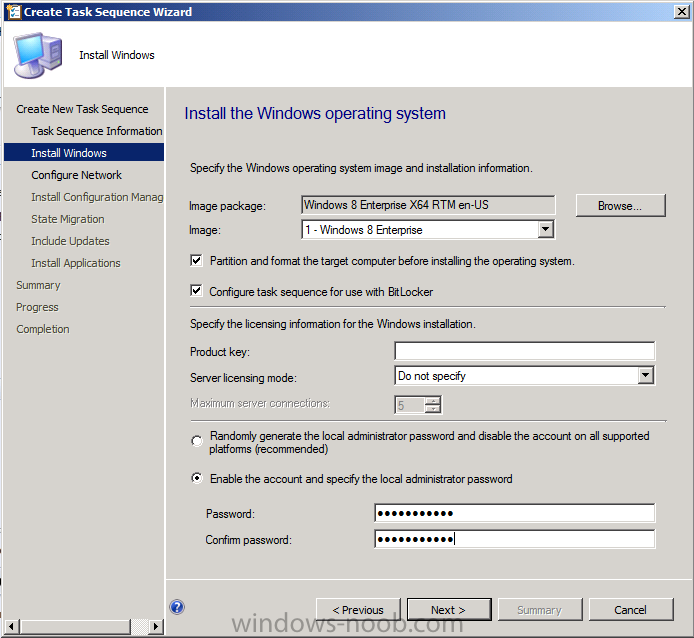
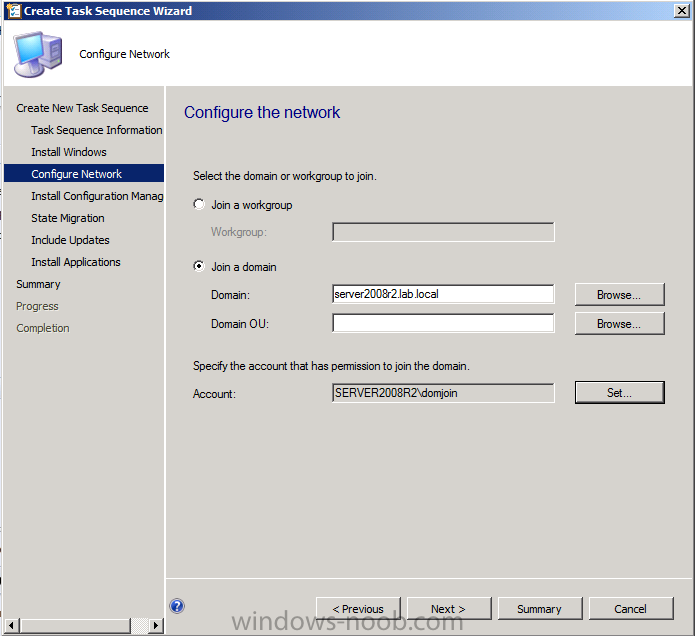
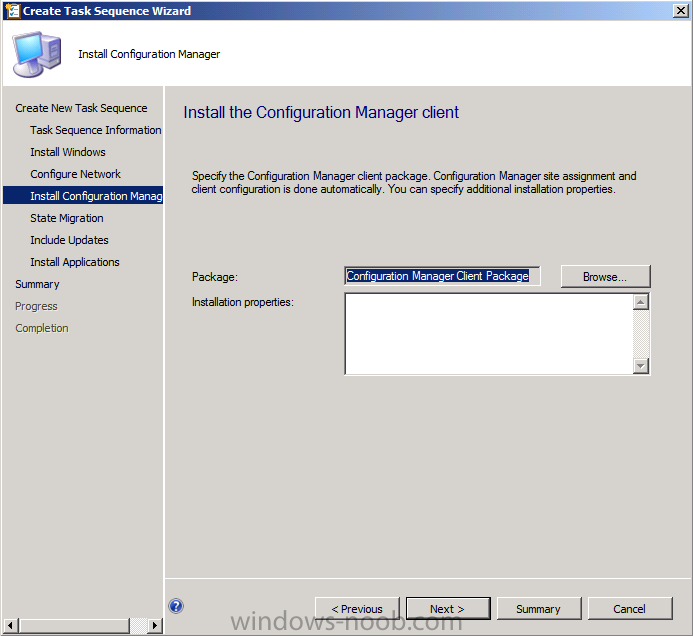
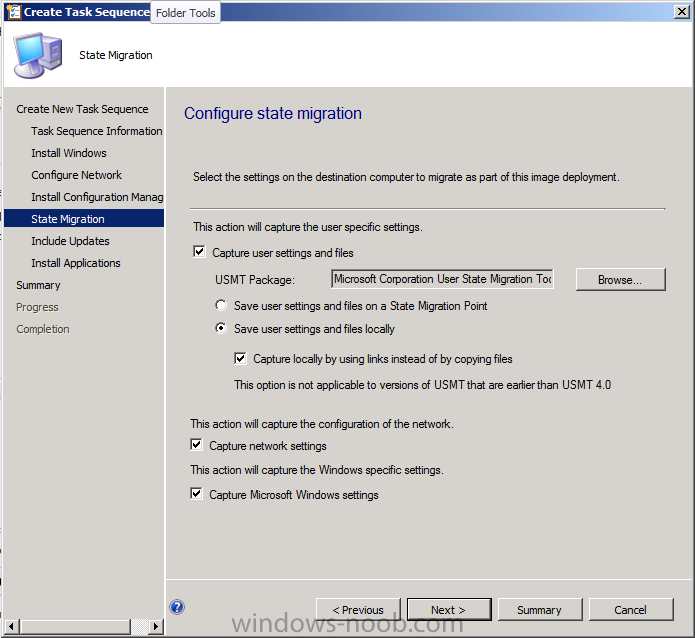
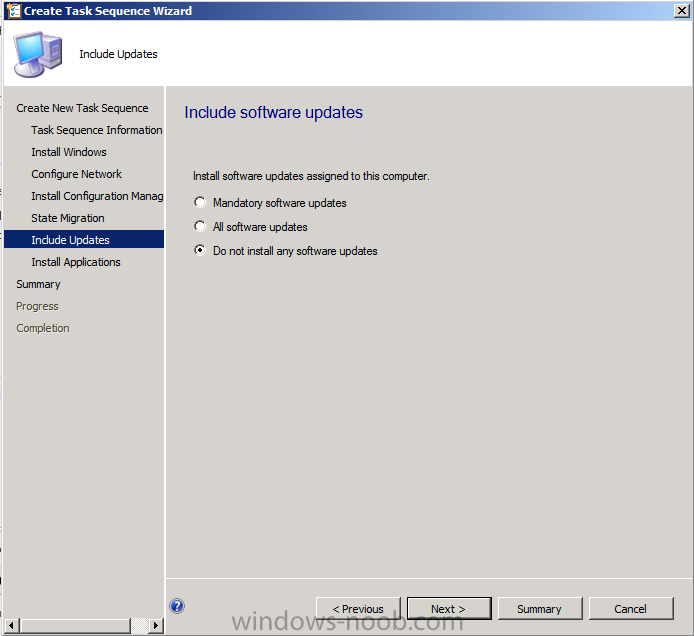
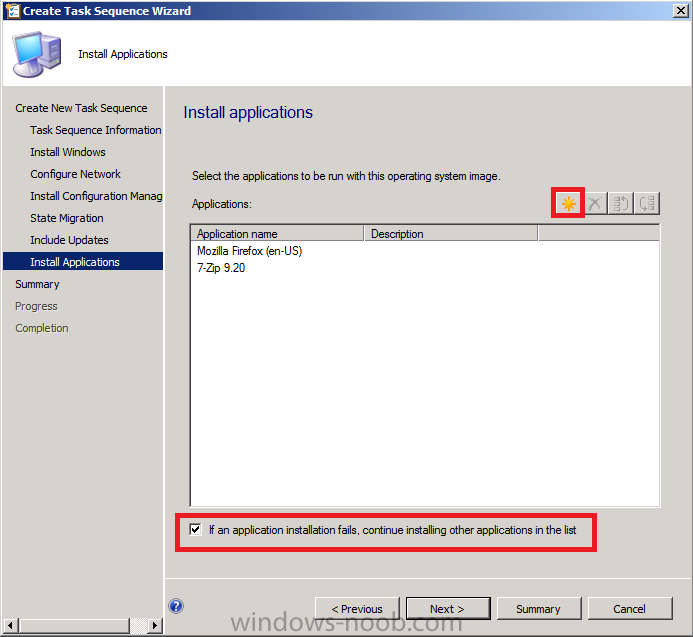
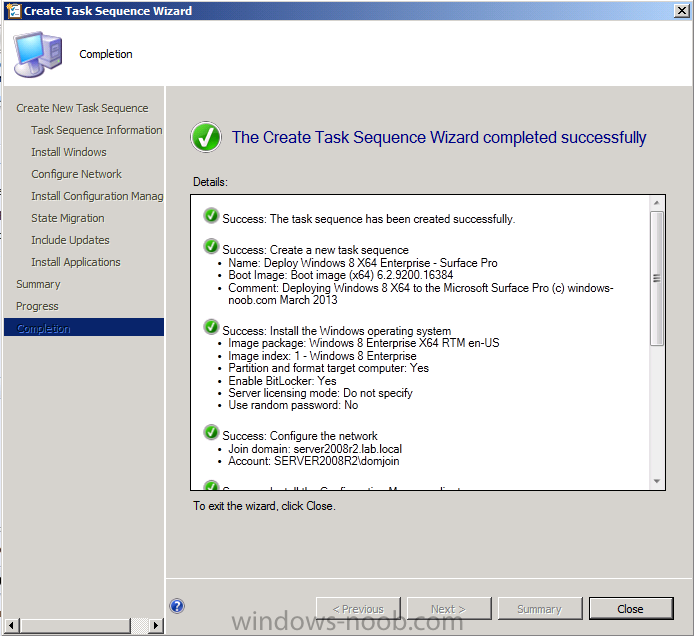
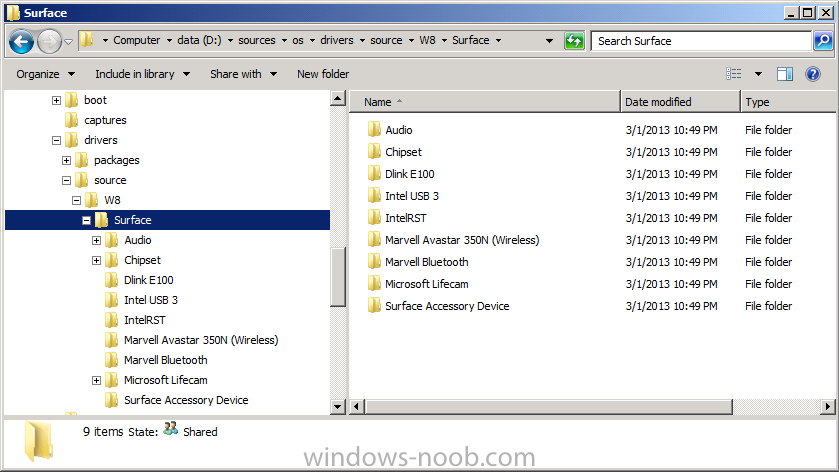
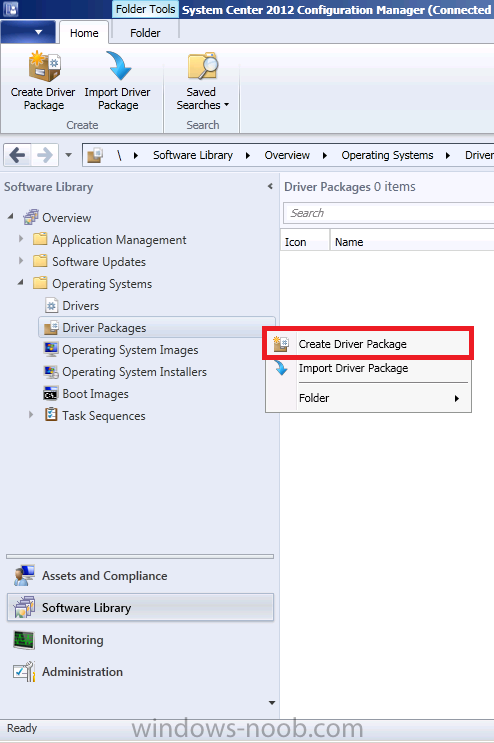
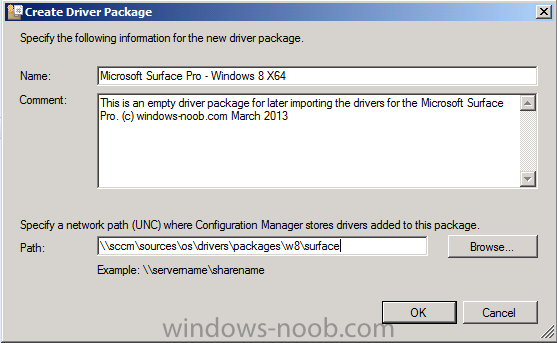
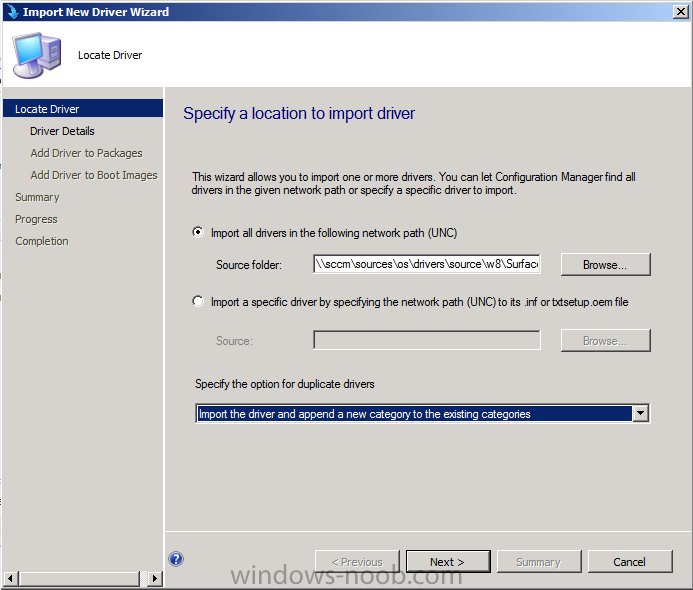
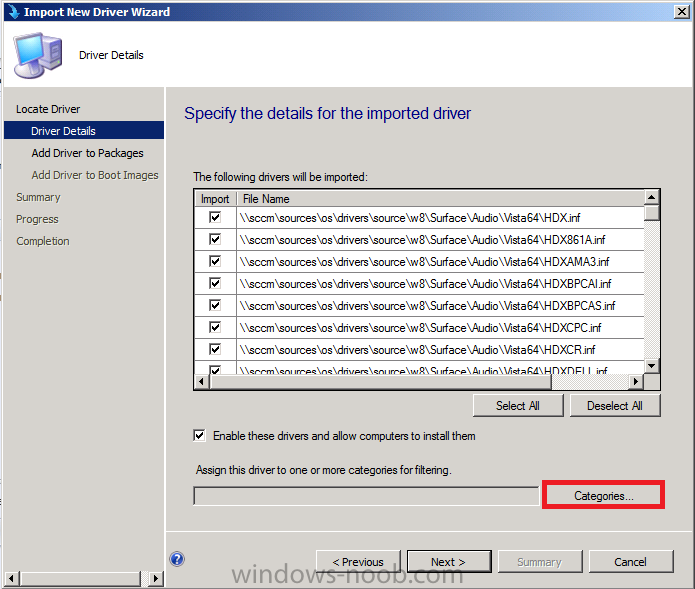
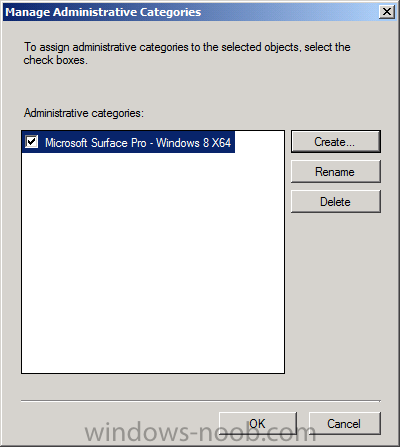
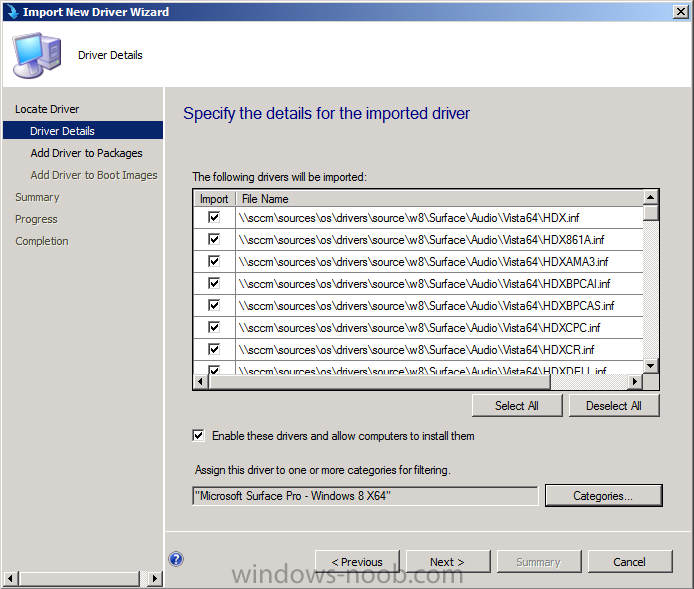
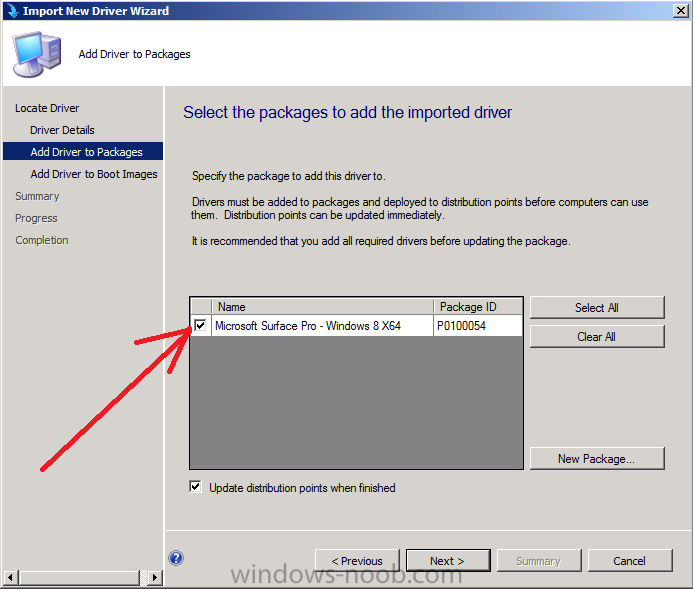
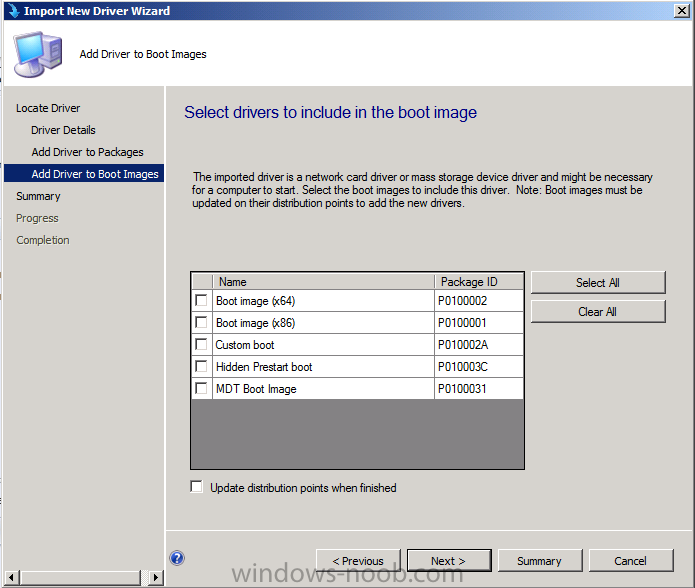
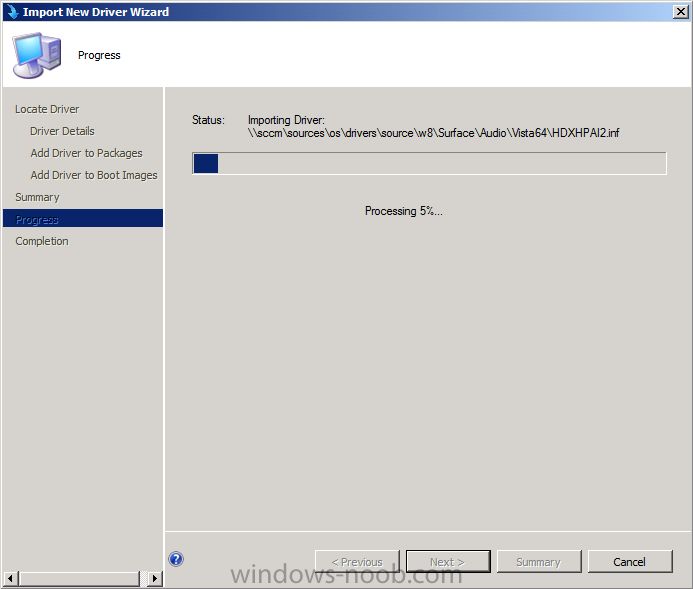
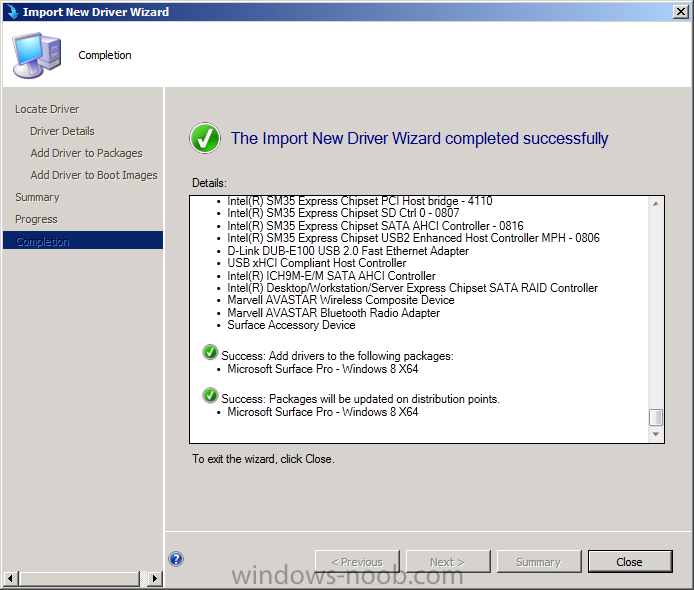
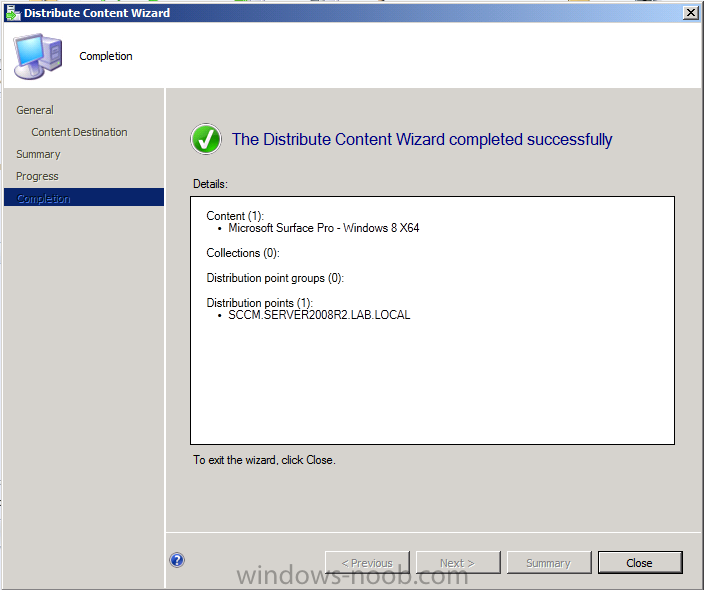
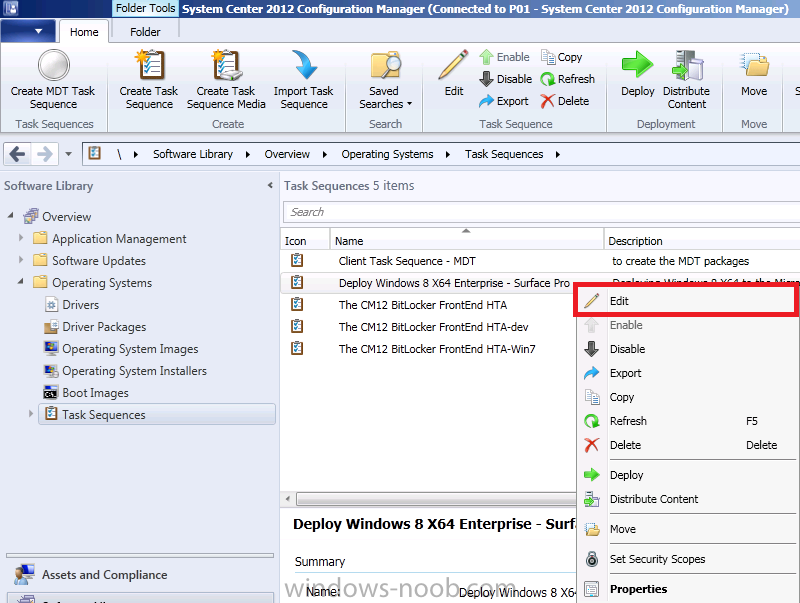
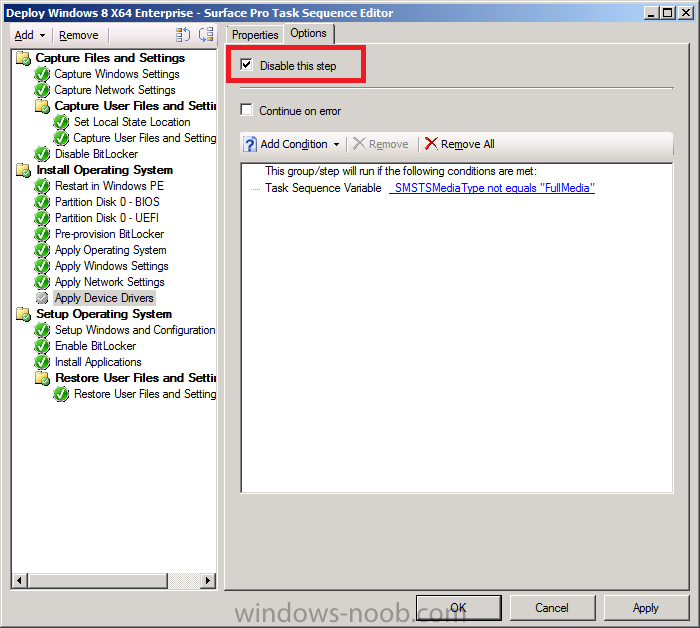
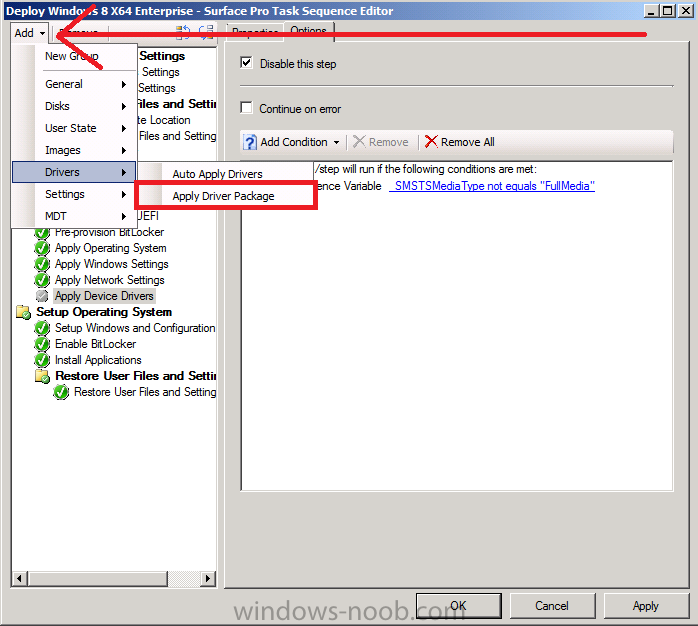
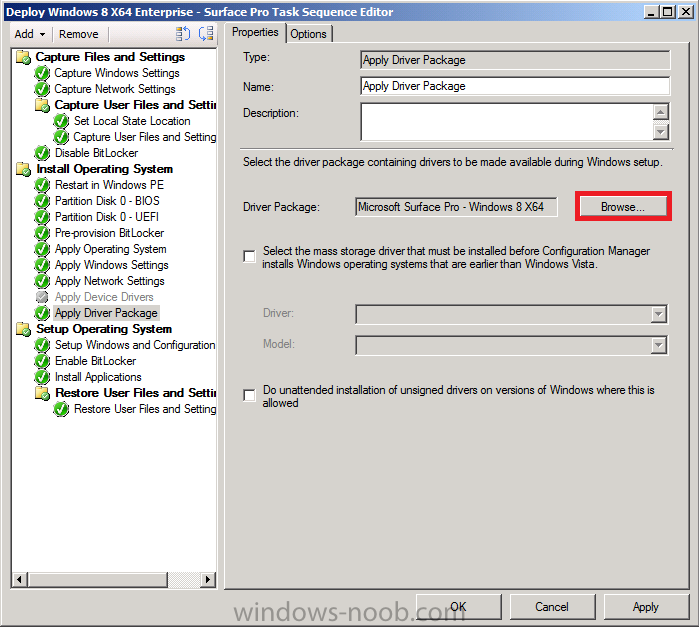
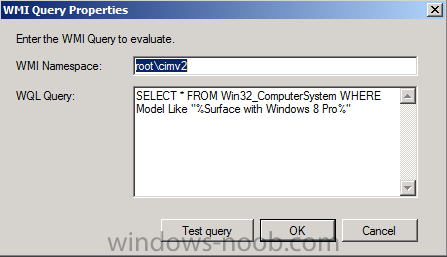
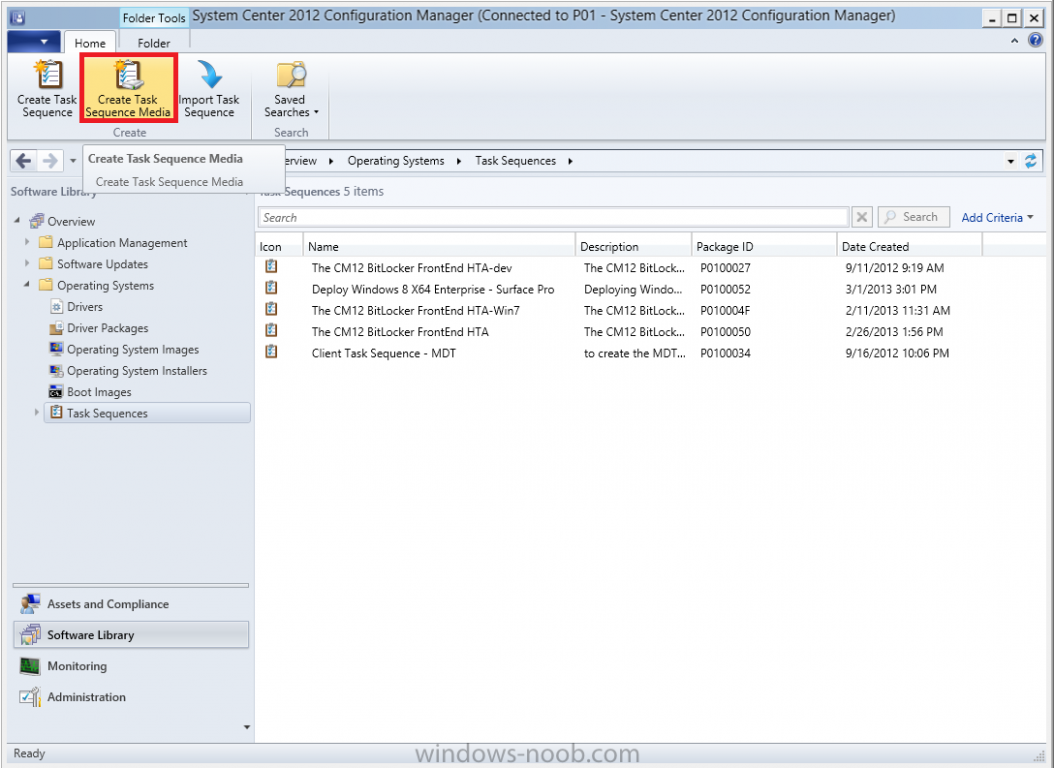
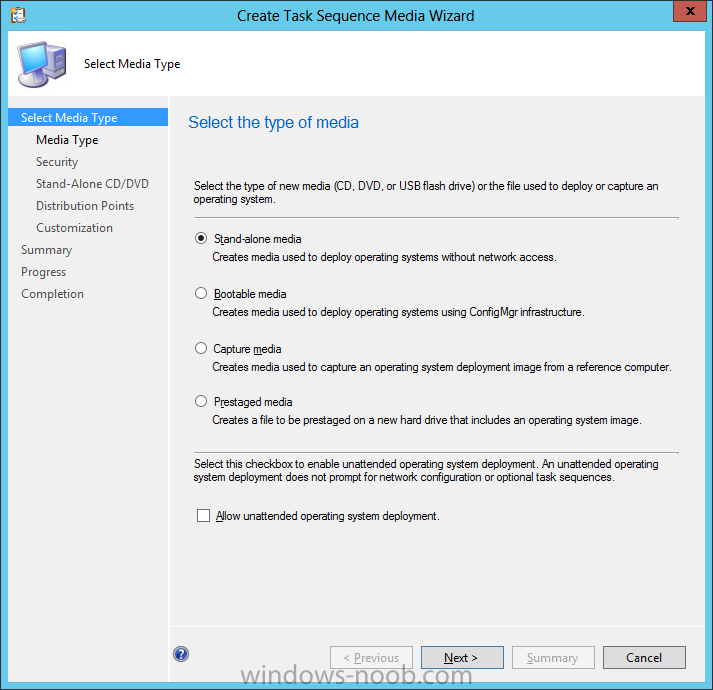
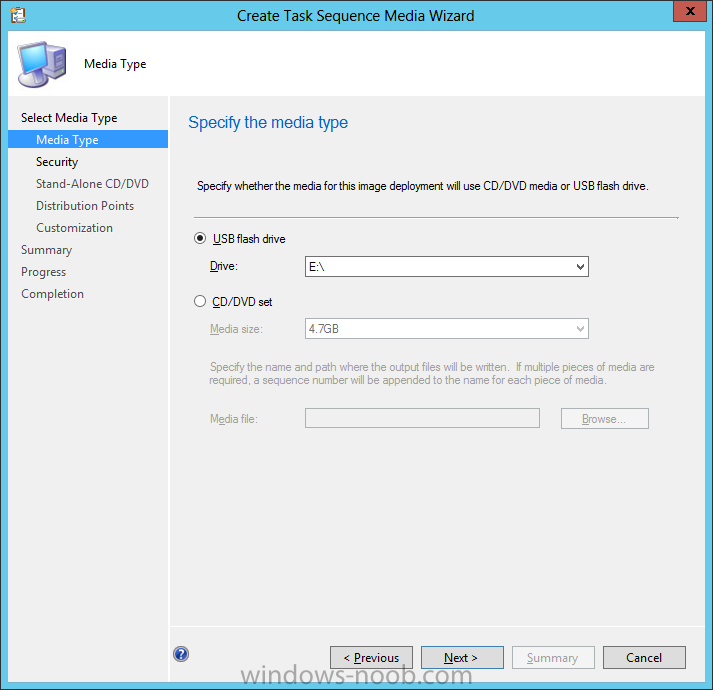
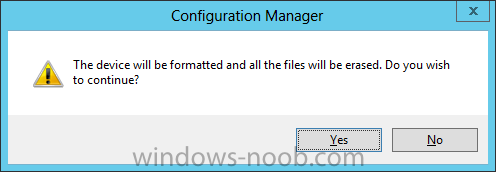
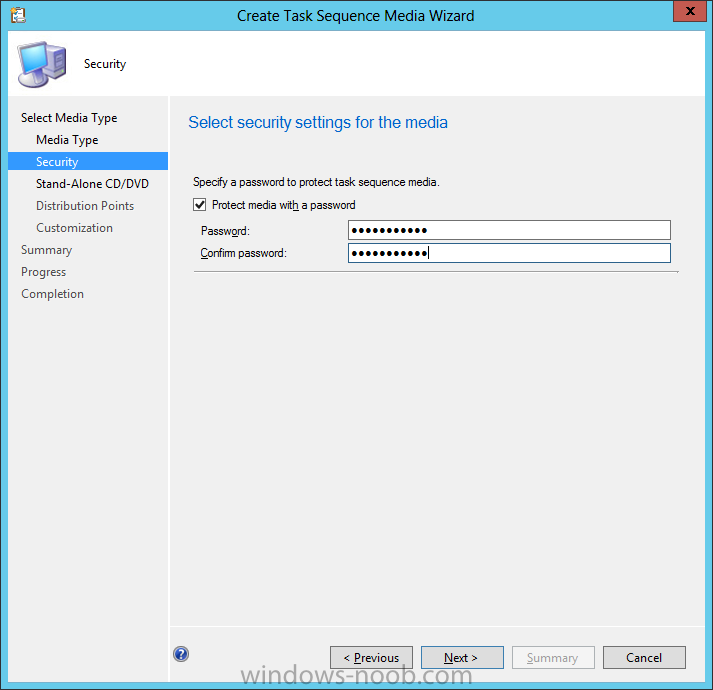
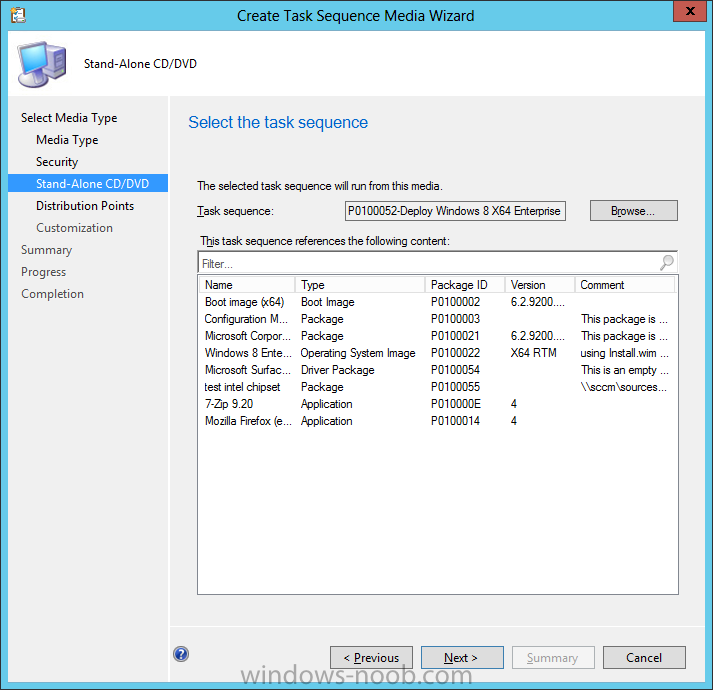
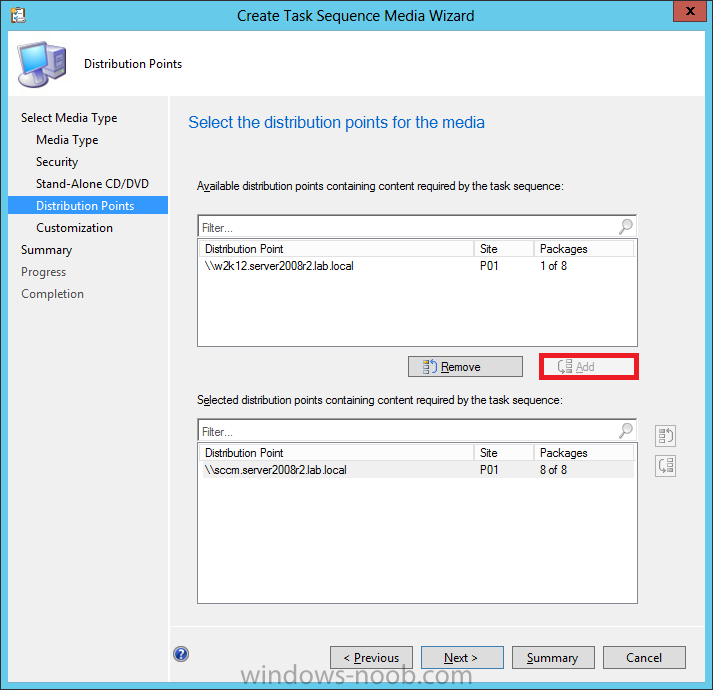
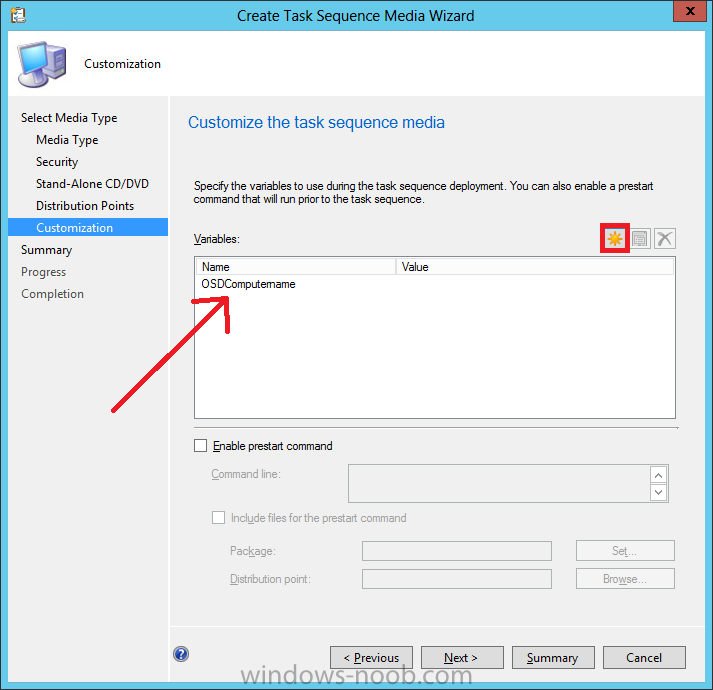
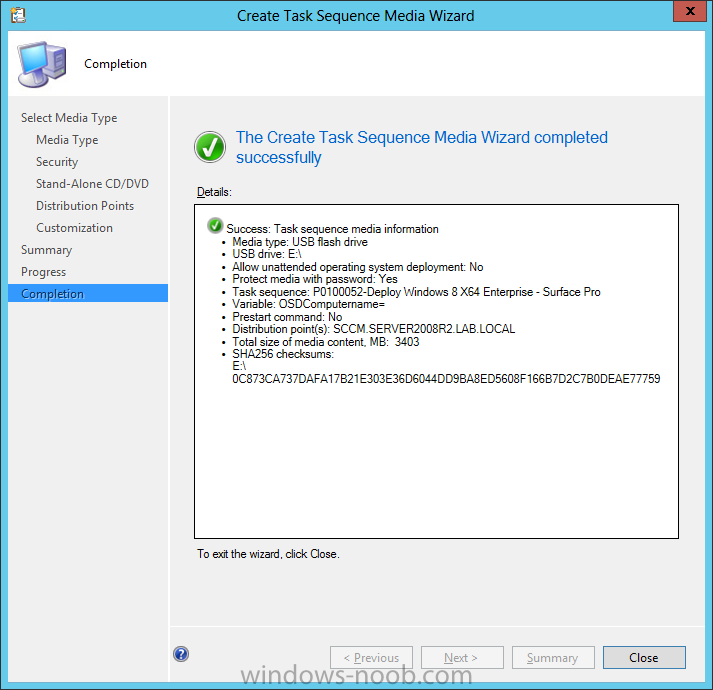
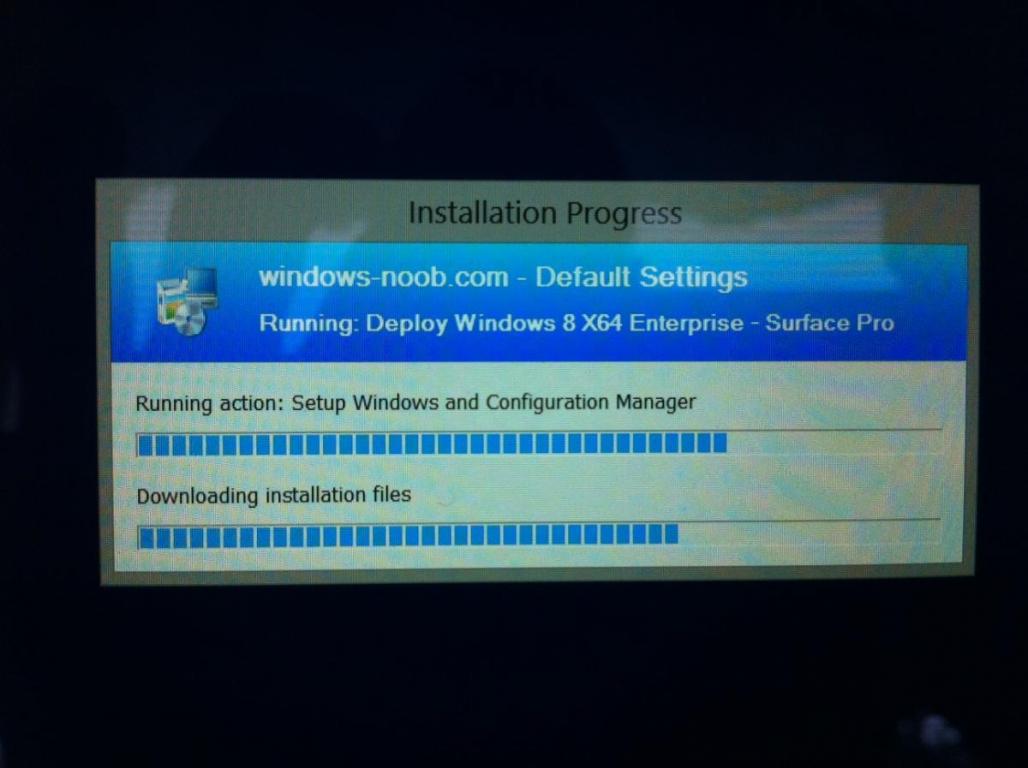
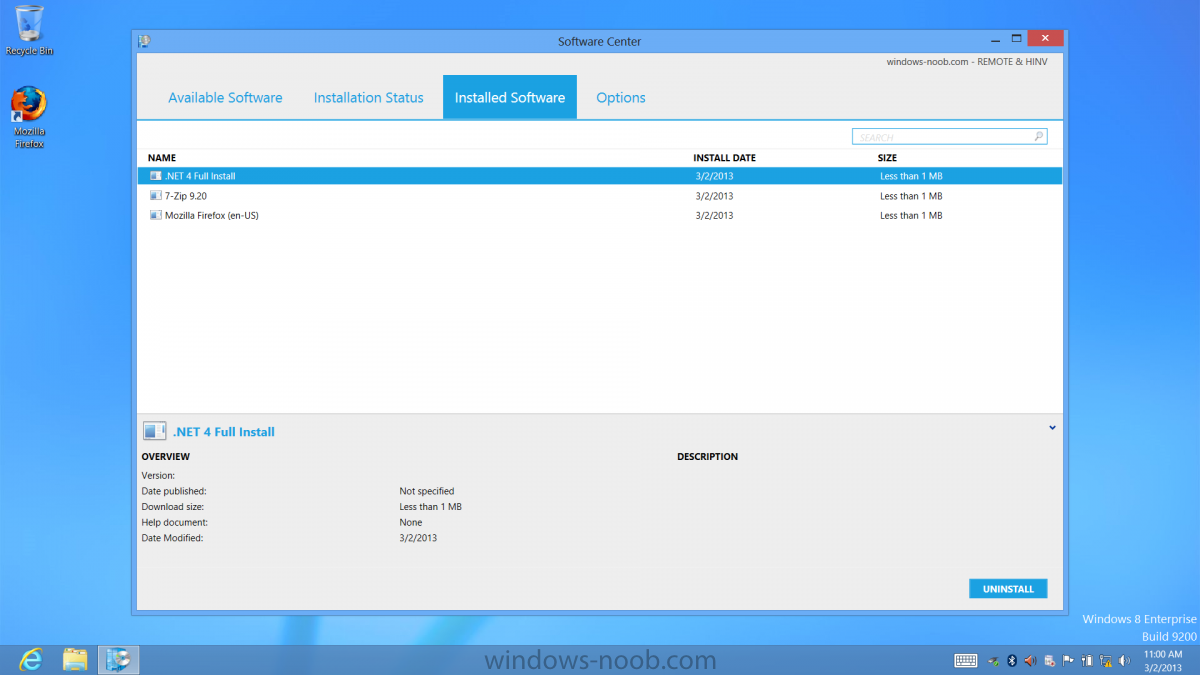
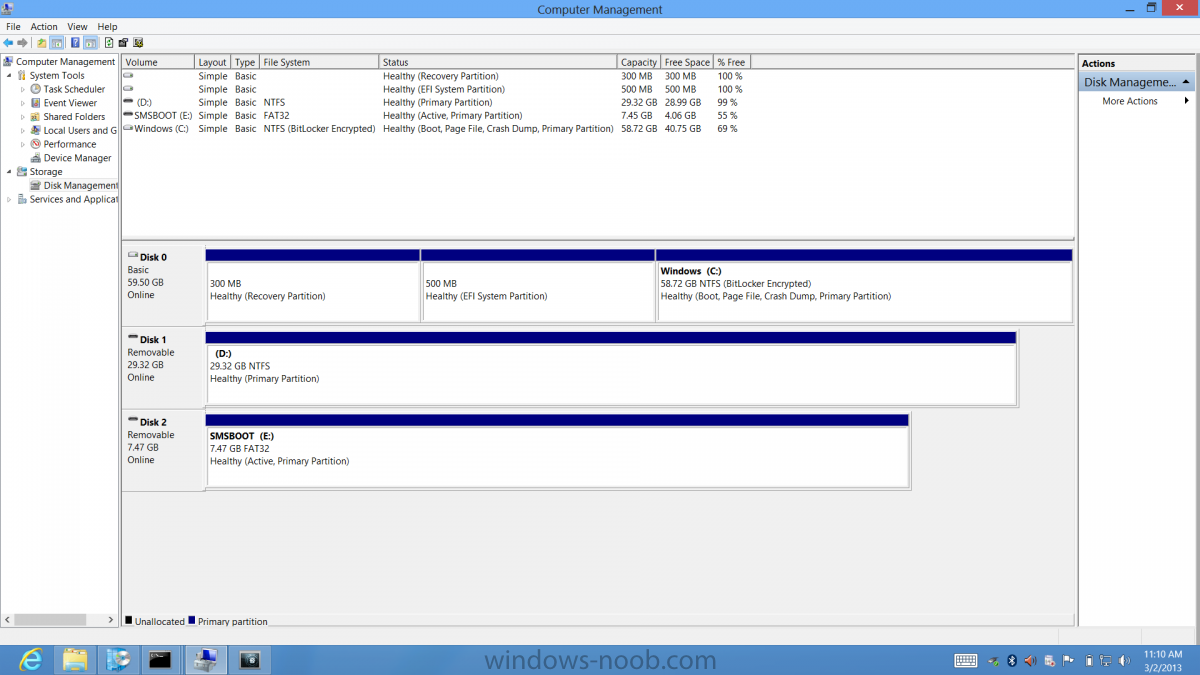
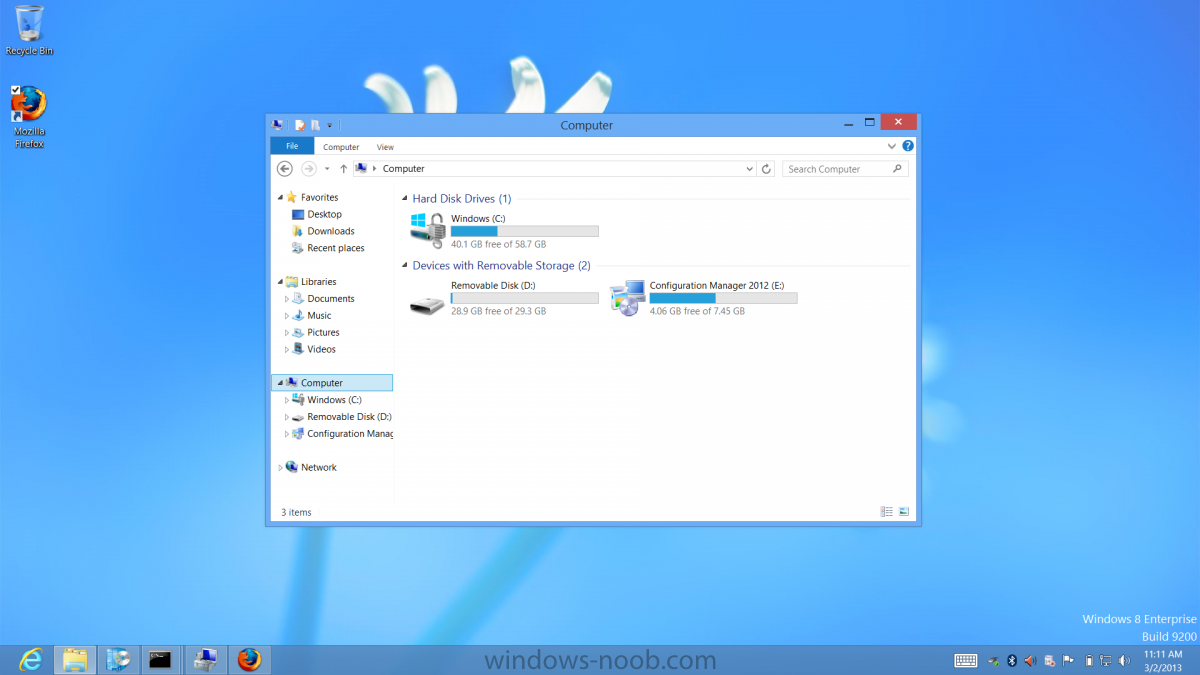
Introduction Now that the Microsoft Surface Pro is available organizations are buying it and re-imaging the default Windows 8 Professional installation with their own corporate install (usually means installing an Enterprise edition of Windows 8). In this post I'll show you how to install Windows 8 X64 Enterprise in UEFI mode, with BitLocker enabled using USB based Standalone media created using Configuration Manager 2012 SP1. Note: Use this guide with care, it is provided to assist you with imaging your Surface Pro in an automated way. windows-noob.com will not be held responsible for any problems that may arise as a result of deploying Windows 8 X64 to your Surface Pro using the methods described below. First of all, re-imaging the Surface Pro is not that straight forward given the fact that the device has no external facing network card (RJ-45), however it does however have a USB 3 port so you can connect USB devices and use them accordingly. Secondly, the Surface Pro is UEFI only and 64 Bit so you can only install a 64bit UEFI capable operating system on it. Thirdly, the Surface Pro has only got one USB 3 port, and we are going to use this port to do our imaging, however we want to connect both a USB flash key and a USB network dongle at the same time, as a result we will use a USB 4-port hub to split one USB port into many. Lastly, and more importantly there is no ability in the current Surface Pro firmware to boot over the network, (it's rumored to be available in a later firmware release from Microsoft, no ETA on that however) therefore we'll use USB Standalone media to install our corporate image. (Update, see the note below about PXE boot). For the purpose of this guide i've used some additional hardware listed below: USB network dongle model dlink Dub E-100 8GB USB key USB 4-port hub So, in the photo below you can see the Surface Pro is connected to a USB 4-port hub, and that hub has a USB key and USB Network dongle attached, that is in turn connected to my Configuration Manager 2012 SP1 Server environment running on HyperV (it's a LAB). Update: After writing this guide, Microsoft have released a PXE capable Network adaptor for the Surface Pro available from here. I don't have access to one but if you'd like me to test it, feel free to send one my way. Step 1. Create the task sequence In the System Center 2012 Configuration Manager SP1 console navigate to Software Library, select operating systems and right click on task sequences, select Create Task Sequence The Create New Task Sequence wizard appears, choose Install an existing image package On the Specify Task Sequence information screen give the task sequence a suitable name like Deploy Windows 8 X64 Enterprise - Surface Pro and choose the X64 boot image (this is very important as it will not boot with the x86 boot image) Note: For UEFI deployments, you must use the boot image matching the architecture of the system being deployed. So for x86 only hardware it must be an x86 boot image and for x64 hardware it must be an x64 boot image. The Surface Pro is X64 hardware therefore you must use a 64 bit boot image. for the Install the windows operating system step click on Browse and select the Windows 8 Install.wim file (from the sources folder on your Windows 8 media) which has been previously added as an Operating System Image and distributed to your distribution points, fill in the product key and change the administrator password so if your deployment fails for any reason and it's not domain joined you'll at least be able to login and troubleshoot. Note that the BitLocker ability is now available and you can select or deselect it if you wish, if you do select it then keep in mind that you may need to extend the Active Directory Schema to support Bitlocker. fill in the domain join details in the Configure the Network step and verify your domain join account settings by clicking on verify before continuing point to your Configuration Manager Client package in the Install the configuration manager client step if you want to migrate users data then make your appropriate choices in the Configure State Migration step on the include software updates screen, it's not selected by default so leave it like that and then add some applications by clicking on the Yellow starburst and selecting your application, to continue installing applications if one fails, select the appropriate checkbox and click next through to completion Step 2. Import drivers for the Surface Pro into Configuration Manager We need to install drivers for the Surface Pro during installation of Windows 8 otherwise certain functionality won't work (like wireless for example), you could use something like Driver Genius to extract the drivers stored on your Surface Pro before you wipe it or use the drivers that someone else has already extracted, I like using ready made drivers so head on over to this site, and download those drivers and extract them to your Configuration Manager server somewhere like \\sccm\sources\os\drivers\source\W8\Surface Update: Microsoft has released a driver pack for the Surface Pro here. The extracted drivers should look something like this: Once done, create a new empty driver package by right clicking on Driver Packages and choose Create Driver Package give the package a suitable name like Microsoft Surface Pro - Windows 8 X64 and note that the path is for the driver package itself and not the drivers we extracted above, so keep them separate, in this case use \\sccm\sources\os\drivers\packages\w8\Surface Next wee need to import the drivers (into the package), so In the configuration Manager console select Drivers, right click and choose Import driver point to the UNC path where you copied the extracted files eg: \\sccm\sources\os\drivers\source\w8\surface on the specify the details for the imported driver step click on Categories and click create, give the category a name like Microsoft Surface Pro - Windows 8 X64 so our driver details now looks like this on the Add drivers to packages screen select our Microsoft Surface Pro - Windows 8 X64 package we will not be adding any drivers to any boot images so click next through that step and click next through the wizard and it will start importing the drivers (warning, can take some time....) After a (long) while the driver import should complete Lastly, don't forget to select the Driver Package and distribute it to your distribution points by right-clicking the driver package and choosing Distribute content. Step 3. Edit the Task Sequence Now we want to edit the task sequence to change how it applies drivers, so right click on the Task Sequence and choose Edit Disable the Apply Device Drivers step by selecting it, clicking on the options tab and selecting disable this step once done, click on Add then Drivers then Apply Driver Package like in the screenshot below select the Microsoft Surface Pro - Windows 8 X64 driver package by clicking on browse then click on the Options tab and click on add condition then query wmi, use the following WMI query SELECT * FROM Win32_ComputerSystem WHERE Model Like "%Surface with Windows 8 Pro%" Tip: If you want to set the DPI (dots per inch) on the Surface Pro display then please see this post. Step 4. Create the Task Sequence standalone media Now everything is in place to create the Standalone media, so insert a USB key into your computer running a Configuration Manager console and browse to Task Sequences in the Operating System Deployment section. In the ribbon click on Create Task Sequence media when the Select the type of media screen appears, choose Stand-alone media on the Specify the media type screen select USB (first option) and select the drive letter corresponding to your USB key answer yes to the format prompt enter a security password (to ensure that no one accidently wipes a device) and click on browse to select our previously created Task Sequence next you'll see what packages are on distribution points, select the ones appropriate for your environment (if you forgot to distribute a package exit the wizard and fix that, then start this process again), in the example below i've clicked on Add and added 8 of 8 next you can add any computer variables or a prestart command, i've covered those elsewhere but for this task sequence i'll add the OSDComputername variable and leave it blank to forcefully prompt for a computername during deployment otherwise we'll get the MININT-xxxxxx name. click next at the summary and accept any UAC prompt, it will begin creating the USB media and after a while it will complete. Step 5. Boot from the USB stand-alone media Shutdown the Surface Pro and when it is powered off, make sure the USB 4 port hub with the USB stand-alone media and USB Network dongle is connected, then press and hold the volume down key on the left side of the Surface Pro and press the power button once. If you do the combination correctly, the system will attempt to boot from the USB stand-alone media. Below you can see the boot process (YouTube video with no narration sorry) and I also enter the ComputerName as part of that process, yes you can even see one of our cats, called Trauma in the background. Ok once the process kicks off you can sit back and admire the automation via Configuration Manager 2012 SP1, it will install all the drivers included in your Driver Package and join the domain, then it will Setup windows and Configuration Manager, reboot and enable BitLocker install your Applications and eventually present you with the login screen. Login and you'll see the Surface Pro is installed with Windows 8 X64 Enterprise, it has BitLocker Enabled, it's paritioned for UEFI and it's managed by Configuration Manager 2012 SP1. Now is that cool or what ? oh yeah ! some more screenshots below Troubleshooting notes You can enter the bios/firmware screen by shutting down the OS, then press and hold Volume UP and then press the power button. The bios/firmware screen allows you to enable or disable secure boot amongst other things. Secure Boot is a feature that helps prevent unauthorized firmware, operating systems, or UEFI drivers (also known as Option ROMs) from running at boot time. For further details please see http://technet.microsoft.com/en-us/library/hh824987.aspx You can bring up the command prompt during the task sequence deployment provided that you've enabled command support in the boot image and press the FN key plus the Settings key (which corresponds to F8) Summary Imaging the Surface Pro does present some technical challenges given it's current firmware and lack of a physical RJ-45 network port, and the fact that it is 64 bit hardware in UEFI mode, however it's possible to image the Surface Pro with an UEFI compatible 64bit Operating System using standalone media from Configuration Manager 2012 SP1. Update. PXE boot has become available since the time of writing this guide but only if you use the official network adapter supplied from Microsoft.
-
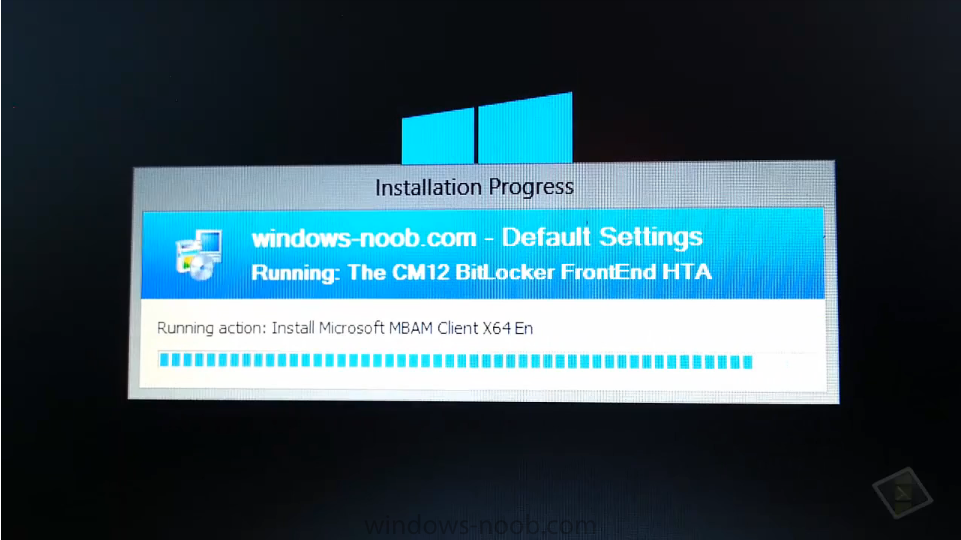
here's a live demo I did in Seattle during the 2013 Global MVP summit, I demo'd the CM12 BitLocker FrontEnd HTA to a few other Configuration Manager MVP's and Rob Marshall decided to video it ! so here's the result, the lighting quality is a bit low (video'd with a mobile phone.), apologies for that and we were both tired after a long day attending sessions, however it was an on-the-spur-of-the-moment thing and we wanted to share the experience In this demo I did a refresh from Windows 8 BitLockered to Windows 8 BitLockered using an MBAM 2.0 backend and of course using Configuration Manager 2012 Service Pack 1 cheers ! niall
-
what does your scanstate.log reveal ?
-
can you attach the logs in the root of C: which are created by setup
-
i moved your post from a BitLocker post to here, why did you post your question there ? raise a new topic when posting about something unrelated please.... as regards your problem, please explain your issue, is it related to Bitlocker, yes/no ?
-

SCCM SP1 OSD Deployment to Only media and PXE
anyweb replied to jdmiller's topic in Configuration Manager 2012
did you delete the task sequences or the deployments ? -
Developers have had early access to Internet Explorer 10 for Windows 7 for a few months now, but Microsoft is making the final release available to consumers and businesses today. Available in 95 languages, Windows 7 users will be auto upgraded to IE10 in the coming weeks, with the initial push targeted at IE10 Release Preview users. Internet Explorer 10 on Windows 7 includes improved JavaScript performance, and a focus on battery life improvements for mobile PCs. Although Internet Explorer 10 has been available on Windows 8 since October 26th, Microsoft opted for a delayed Windows 7 schedule to ensure the release was fully ready, a decision that drew some criticism from users waiting on an updated browser. Windows 7 users will now get integrated spell checking and auto-correct within IE10, as well as improved support for web standards like the latest CSS3 improvements. The user interface in IE10 for Windows 7 is largely the same as IE9, so users won't get the fullscreen experience that's available in Windows 8. Nevertheless, Internet Explorer 10 is now available to download for Windows 7. via > http://www.theverge.com/2013/2/26/4029306/internet-explorer-10-windows-7-download?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+WinRumors+%28WinRumors%29
-

SCCM 2012 or SCCM 2012 SP1 on initail install?
anyweb replied to pnyce24's topic in Configuration Manager 2012
I'd recommend you set it up in a lab first (always recommended) and test your hardware with it, shouldn't take too long and will reveal any problems you may/may not have.- 5 replies
-
- sccm 2012 SP1
- sccm 2012
-
(and 1 more)
Tagged with:
-

how to deploy applications in untrusted forest
anyweb replied to ankurpathak's topic in Configuration Manager 2012
what does the MSI log file of the application you are installing, tell you about that (very common) error ? -

SCCM 2012 or SCCM 2012 SP1 on initail install?
anyweb replied to pnyce24's topic in Configuration Manager 2012
SP1 offers so many new features that it's what i'd recommend, however be aware that the new ADK requirements means you have WinPE4 and that means that hardware older than 3 years may have problems PXE booting... until Johan Arwidmark posts his workaround- 5 replies
-
- sccm 2012 SP1
- sccm 2012
-
(and 1 more)
Tagged with:
-

Non OS Deployment task sequence HTA splash screen
anyweb replied to JeffPitt's topic in Configuration Manager 2007
and for those that don't know, the reason your users never saw the HTA popup originally is because task sequences run in System Context, whereas running a package can run in User context. -
is this a build and capture task sequence or a deploy task sequence ? can you post the SMSTS.log and the ccmsetup.log and client.msi.log files please
-
Introduction One of the user definable sources for updates for Endpoint Protection definition updates is an UNC file share, but how you populate that share can mean success or failure when it comes to deploying definition updates from a UNC file share for System Center 2012 Endpoint Protection using System Center 2012 Configuration Manager SP1. In addition to populating the share correctly, you also need to define your AntiMalware Policy UNC path source correctly otherwise the definition updates will never be found. In this post I’ll explain how you can set this up and how to verify it’s working. Step 1. Create a Share and populate with folders First of all on your chosen server create a folder called SCEP_UNC_DEFS and share it to Domain Users and Domain Computers. Beneath this folder create another folder called Updates with two sub folders for both architectures like so Step 2. Populate the share with definition updates Now that we’ve created our template folder structure we need to populate it with the actual definition updates for the prospective architecture. For x64, download the following files and place them in the X64 folder. Antimalware full definitions (http://go.microsoft.com/fwlink/?LinkID=121721&clcid=0×409&arch=x64) Antimalware delta definitions (http://go.microsoft.com/fwlink/?LinkId=211054) Network-based exploit definitions (http://go.microsoft.com/fwlink/?LinkId=197094) For x86, download the following files and place them in the X86 folder. Antimalware full definitions (http://go.microsoft.com/fwlink/?LinkID=121721&clcid=0×409&arch=x86) Antimalware delta definitions (http://go.microsoft.com/fwlink/?LinkId=211053) Network-based exploit definitions (http://go.microsoft.com/fwlink/?LinkId=197095) Step 3. Create a new Antimalware Policy In the Assets and Compliance workspace, expand Endpoint Protection, select Antimalware Policies, right click and choose Create AntiMalware Policy, give it a name like Custom SCEP UNC DEF policy and select Definition Updates from the available choices (you may of course add more sections but for the purpose of this post this is sufficient). Click on Set Paths and enter the path to the Updates folder which is a sub directory of the SCEP_UNC_DEFS file share, click on Add when done. eg: \\server\scep_unc_defs\updates Next click on Set Source, make sure to select Updates from UNC Shares and use the UP button to bring this to the top choice (if you want it as the first option checked when more than one source is selected). Step 4. Create a collection to target the Antimalware Policy Right click on Devices Collections, and choose create device collection, give it a suitable name like Endpoint Protection UNC_DEFS you can populate it however you want (queries or direct membership) and then move it to somewhere suitable if required. Step 5. Change the Antimalware Policy priority right click on your new antimalware policy and choose Increase Priority, make this the highest priorty you can as SP1 uses Client side merge of AntiMalware policies and we want this source for definition updates to take priority on any computers in this collection. Step 6. Deploy the Antimalware Policy Right click on the AntiMalware Policy and choose Deploy point it to the collection we created above Step 7. Verify the UNC file share is being used Now everything is in place to deploy definition updates via an UNC file share, but we need to prove that don’t we. On a Windows client computer that you’ve added to our collection we created above, run the following Configuration Manager client action, Machine Policy Retrieval & Evaluation Cycle. This will ensure that our client has the latest Antimalware Policies targeted to it including the one we created above, to verify that our policy is indeed targeted to this computer please see this post, you should see something similar to the following in the registry, depending on what Antimalware Policies are applied to this client however we are only interested in our Custom SCEP UNC Def policy and it is indeed listed below. Do not proceed with the verification until your Windows client has our Custom SCEP_UNC_Def policy applied. Once done, open an Administrative command prompt and browse to the following folder C:\Program Files\Microsoft Security Client\ and execute the following command MpcmdRun.exe -SignatureUpdate as per below screenshot. If all went well then you’ll see Signature Update Finished. Open the following log file for final verification C:\Users\Administrator\AppData\Local\Temp\MpCmdRun.Log and you should see search started (UNC Share) along with the following text, Update Completed Successfully. (hr: 0×00000000) You can open the SCEP client, click on the updates tab and review the Definition Update versions for further verification. And there you have it, your SCEP client has updated it’s definition updates from your UNC file share as specified in your Custom Antimalware Policy, and you’ve proven the fact !. Troubleshooting Tip: If you fail to get this to work and see the following error instead, Error: Signature Update failed with hr=80070002 then verify you are pointing at the correct UNC File share directory as listed in my guide above then try again. Summary System Center 2012 Configuration Manager SP1 is a powerful management solution and you can use custom antimalware policies to update Endpoint Protection via multiple or single sources, including using UNC file shares, this ability gives great flexibility and control over how you want those definition updates deployed. If you’d like to automate the download of those definition updates please review the following post. until next time, from Seattle, cheers niall
-

SCCM SP1 OSD Deployment to Only media and PXE
anyweb replied to jdmiller's topic in Configuration Manager 2012
ok can you clarify the below as the new option comes with SP1.,