-
Posts
9258 -
Joined
-
Last visited
-
Days Won
371
Everything posted by anyweb
-
my experience was back when I wrote the script used in this blogpost, and at that time, it was the only way I could get Windows Autopilot to work in our environment. Our environment has changed since then and no longer uses the same type of proxy, you could say now that it now resembles a transparent proxy and therefore there's no longer any need to use the script. if you can, avoid using Hybrid azure ad join, it's more trouble than it's worth. When I initially wrote the script it was so that we could test Windows Autopilot on the internal LAN, a lot has changed since then and we've learned a lot too. The best advice I can give you is to try modifying this script to work with your environment, or determine if you need it at all based on what happens in Windows Autopilot, maybe you can add exclusions for the urls used during Windows Autopilot, there are lots of options. as regards point 3, you could always use a different network (think of it as an enrollment network) to get your devices through Windows Autopilot OOBE and complete enrollment, you could then apply whatever network/proxy settings you want AFTER windows autopilot is complete using some of the methods I describe here
-

Displaying a welcome page after Windows Autopilot completes
anyweb replied to anyweb's topic in Microsoft Intune
ok so the script will create a scheduled task for each user but basically won't do anything for defaultuser0, as that's not a real user, it's only used by Windows Autopilot during the ESP, so... after the Account Setup phase (user account) part of the ESP is done, and you logon to the desktop, what scheduled tasks do you see ? -

Displaying a welcome page after Windows Autopilot completes
anyweb replied to anyweb's topic in Microsoft Intune
hi @MagnusL I've tested it with AzureAd joined devices only as that's what we use, and it works fine in that scenario, so when you checked task scheduler can you show me what it did create ? ive not seen a defult0 user before, DefaultUser0 yes, but not the other one... did you heavily modify the scripts ? -
there's only one way to find out, try it ! i recommend trying it out using a virtual machine connected to the same network as the network you intend to test, that way you can try different settings in the script on the fly
-

Displaying a welcome page after Windows Autopilot completes
anyweb replied to anyweb's topic in Microsoft Intune
hi, the link works fine you just need to be logged in to download files from windows-noob.com -
how did you configure WSUS, did you use SQL or SQL express, if you used SQL, which version ? have you looked at event viewer for more details ?
-
ok have you updated Server 2016 with the latest patches from windows update ?
-
is WSUS separate from Configuration Manager ? what version of Windows Server is it running on ?
-
Introduction I saw an interesting tweet from @brucesaaaa where he talked about issues observed in multiple tenants during Windows Autopilot enrollment with required Win32 apps. The following was seen for required deployments of Win32 apps during Windows Autopilot enrollment: ESP did not flag these apps as required Required apps took hours and hours to install App install output codes (like for reboots) were not working Problem The problem was investigated and narrowed down to the version of Microsoft Win32 Content Prep Tool that the technicians were using to create the Win32 apps. The is very easy to understand as many admins simply download the tool and re-use it over and over. I’m guilty of that too !, the app I created below was created with 1.8.2.0 and the current version is 1.8.3. I’m not sure what version of the app that caused their issues but as soon as they downloaded the latest version and repackaged their apps the problems went away. Analysis I did some checking with a Win32 app I recently created. If you rename the app from it’s original filename.intunewin extension to filename.zip you can extract the contents. Open the detection.xml file in the metadata folder. If you open the XML file in a suitable reader, you can see the version of the tool that it was made with by reviewing the ToolVersion property highlighted below in yellow. If you start the Microsoft Win32 Content Prep Tool (IntuneWinAppUtil.exe) and use a -v it’ll show the version info. IntuneWinAppUtil -v I guess that Microsoft could force that people use the latest and greatest version of their tool by scanning that detection.xml file prior to accepting the file. Or at the very least inform the user of possible problems if they choose to ignore the fact. This should bypass any issues caused by using older versions of the tool to package the Win32 App. Interesting problem, let’s see where it goes ! cheers niall
-
i'm using the most up to date windows 11 and my taskbar doesn't autohide, i'd imagine lots of people would complain if that did happen without their involvement
-
i've never noticed that, are you sure you are not setting some policy/registry key for that ?
-
I think this covers it.. Primary sites support the installation of site system roles on computers in remote forests. When a site system role accepts connections from the internet, as a security best practice, install the site system roles in a location where the forest boundary provides protection for the site server (for example, in a perimeter network). To install a site system role on a computer in an untrusted forest: Specify a Site System Installation Account, which the site uses to install the site system role. (This account must have local administrative credentials to connect to.) Then install site system roles on the specified computer. Select the site system option Require the site server to initiate connections to this site system. This setting requires the site server to establish connections to the site system server to transfer data. This configuration prevents the computer in the untrusted location from initiating contact with the site server that's inside your trusted network. These connections use the Site System Installation Account. To use a site system role that was installed in an untrusted forest, firewalls must allow the network traffic even when the site server initiates the transfer of data. Additionally, the following site system roles require direct access to the site database. Therefore, firewalls must allow applicable traffic from the untrusted forest to the site's SQL Server: Asset Intelligence synchronization point Endpoint Protection point Enrollment point Management point Reporting service point State migration point For more information, see Ports used in Configuration Manager.
-
if the other forest is untrusted: Install site system roles in that untrusted forest, with the option to publish site information to that Active Directory forest To use a site system role that was installed in an untrusted forest, firewalls must allow the network traffic even when the site server initiates the transfer of data. When a two-way forest trust exists, Configuration Manager doesn't require any additional configuration steps.
-
With the shift in the computing paradigm to the cloud, the Azure ecosystem is quickly becoming a critical platform for IT pros to grasp and adopt. But how do you make the leap while maintaining security, manageability, and cost-control? Whether you’re making new VMs directly in the cloud, have VMs in your own datacenter and are looking to migrate to Azure, or you’re looking to manage VMs with cloud-based tools regardless of where they live, The SysAdmin Guide to Azure Infrastructure as a Service (Iaas) will teach you to set up and maintain a high-performing Azure IaaS environment. Written by veteran IT consultant and trainer Paul Schnackenburg, Altaro’s free 100+ page second edition eBook covers how to create VMs, size them correctly, and manage storage, networking, and security, along with backup. You’ll also learn how to operate groups of VMs, deploy resources based on templates, manage security, and automate your infrastructure. There are also two new chapters on Automanage and Azure Arc to help you bring a lot of automation to IaaS, all lessening the burden on your time. One thing that has changed significantly over the past couple of years is the shift towards making IaaS VMs more like PaaS services. VMs are great but they require a lot of maintenance and care, whereas all the business is really interested in are the applications and data that run inside of them. This explains the popularity of PaaS services such as managed Kubernetes (AKS) and Azure Functions (serverless). If you’re new to the cloud (or have experience with Amazon Web Services and/or Google Cloud Platform but not Azure) this eBook will cover the basics as well as advanced skills. And given how fast things change in the cloud, it covers the why (as well as the how) so that as features and interfaces are updated, you’ll know how to proceed. Make the cloud work for you - download your free copy today!
-

Azure AD joined device is not enrolling into Intune
anyweb replied to learningmode's topic in Microsoft Intune
did the event logs reveal anything about the problem ? -

How can I renew an expired secret in an Azure Function app
anyweb posted a topic in Microsoft Intune
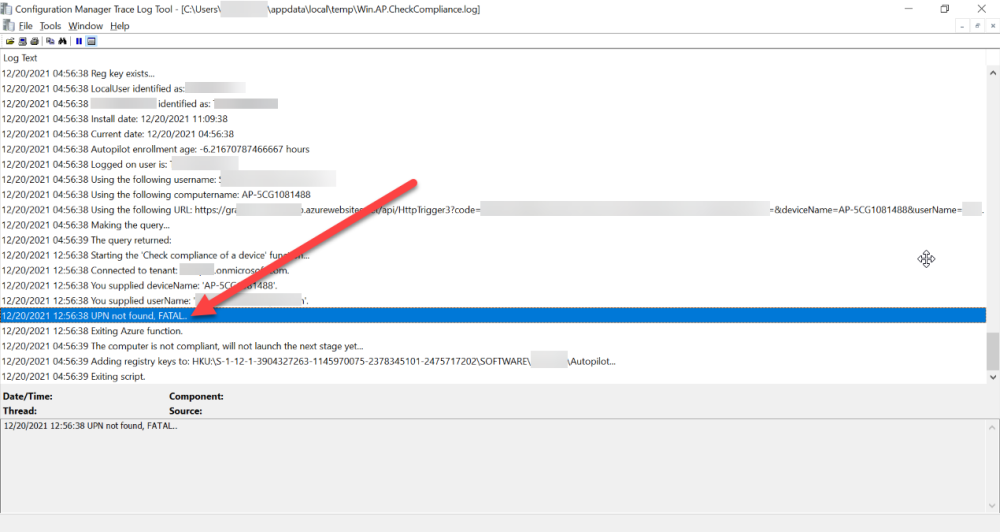
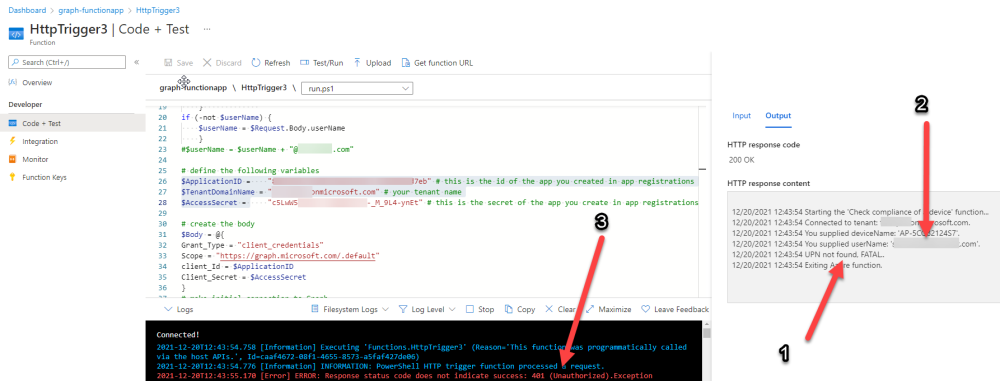
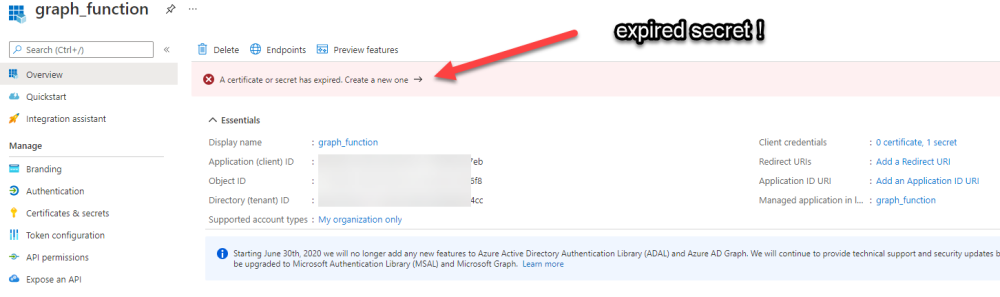
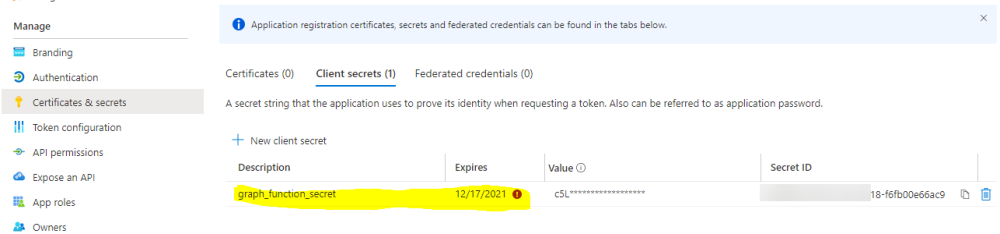
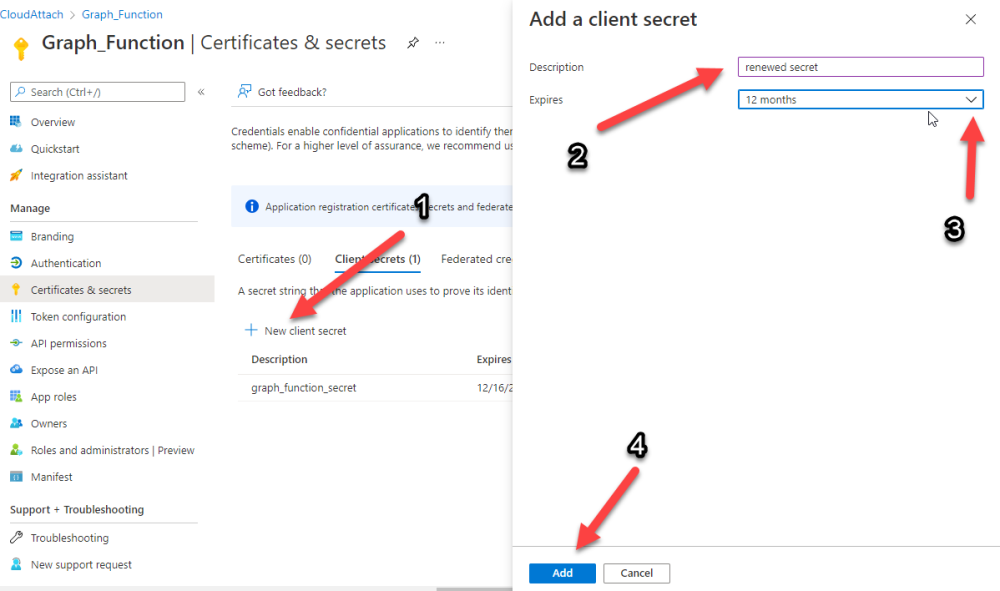
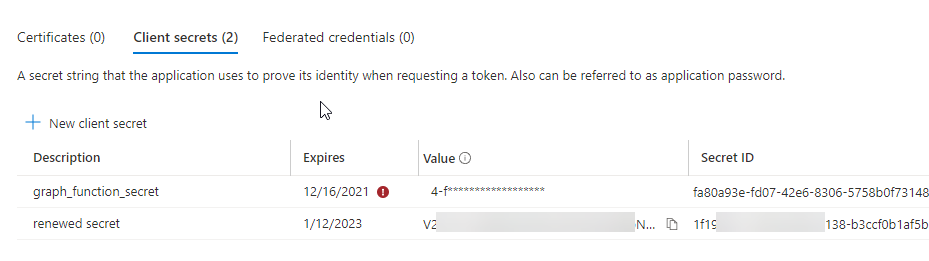
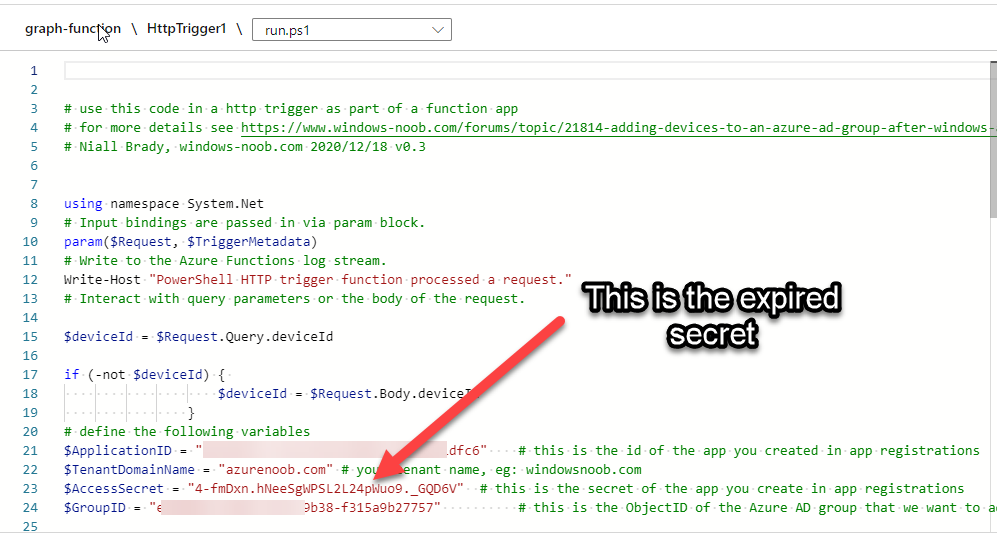
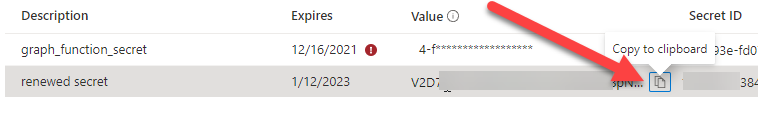
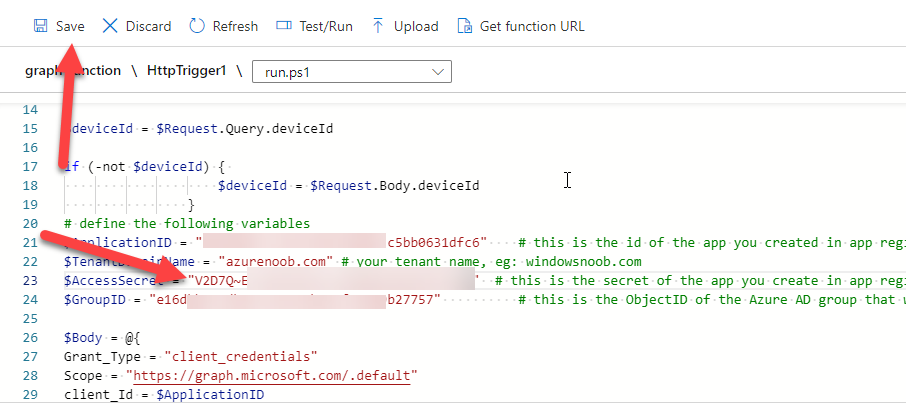
Introduction If you've been looking at my guides, you'll know that I've used httptriggers in functionapps to add functionality to Windows Autopilot, below are some examples of that. Adding devices to an Azure AD group after Windows Autopilot is complete - part 1 Adding devices to an Azure AD group after Windows Autopilot is complete - part 2 Gathering logs and sending an email when resetting Windows Autopilot - part 1 Gathering logs and sending an email when you need to reset Windows Autopilot - part 2 Gathering logs and sending an email when you need to reset Windows Autopilot - part 3 Adding devices or users to an Azure AD group after Windows Autopilot is complete but only when the device is marked as Compliant Using the updated & secure Retire My PC app via Company Portal These work great, but for security reasons the secret attached to the function app itself will expire (after 6 months by default) and should be renewed before that time. Trust me, I learned the hard way. Discovering the problem You might forget to renew the secret and that's when you'll notice things not behaving the way they should. I first became aware of the problem before Christmas, I came into work on the Monday, and kicked off some Windows Autopilot installs but they didn't work correctly. I noticed that the triggers responsible for adding devices to Azure AD groups after Windows Autopilot is complete, but only when the device is marked as compliant were no longer working. I started my investigation on a client with the issue, and the following was reported in the log file. One line jumped out at me, UPN not found, FATAL. Yeah, that doesn't sound good. I then logged into Azure and found the trigger responsible. I fed it with some known good values and looked at the output. The first thing to note is it output the same error (1), even though I supplied a known good UPN (2). Therefore, I knew the error UPN not found, FATAL was a red-herring. I also noticed that there were error code 401 (unauthorized) in the console output (3). That was my first clue ! Next, I select App Registrations in Azure Active Directory, selected the Graph_function app and was greeted with a red error on top showing me that a certificate or secret had expired. Clicking on Certificates and secrets, showed the expired secret. Fixing expired secrets Now that I identified the problem, it was time to fix it. In the Certificates & secrets section, click on + New client secret (1), give it a suitable name (2), select when it expires from the drop down menu (3) and finally Add it (4). The new secret will appear. Notice the expiry date. Now, copy the new secret value. Next, locate the trigger(s) that use the previous secret. It's stored as $AccessSecret in my httptrigger examples. Replace that expired value with the value you copied from the newly created secret and then save your changes. Job done ! Repeat the above exercise for each trigger that uses the expired secret. Conclusion Nothing lasts forever, especially secrets. Now that you know how to renew your expired secrets, maybe it's a good idea to look at your app registrations and take note of when they expire, and pro-actively renew them before they expire next time ! If you'd like to automate that take a look at Peter Klapwijk's post here. -

Windows 10 20H2 RSAT tools are failing to install from FOD
anyweb replied to lalajee's question in Windows 10
here's the error, verify that the source files are in the locations specified in your -source path, Add-WindowsCapability : The source files could not be found. -
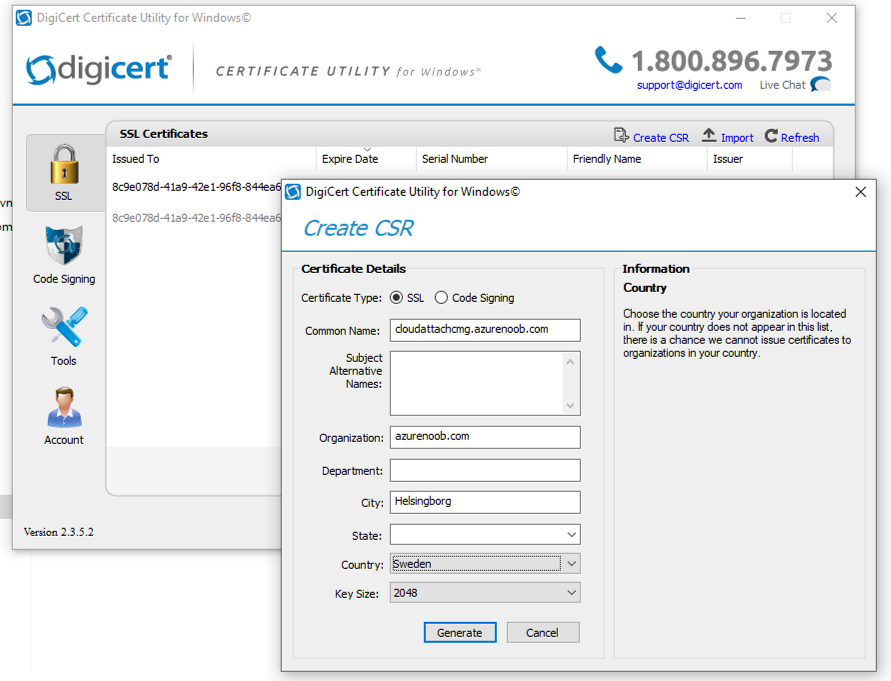
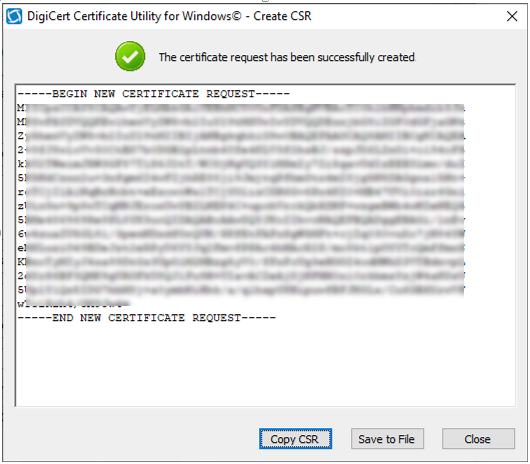
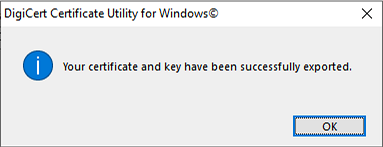
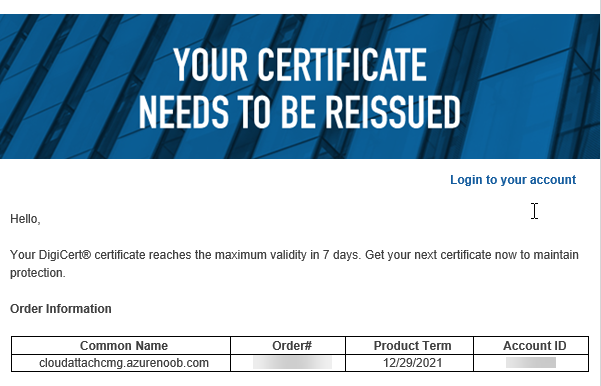
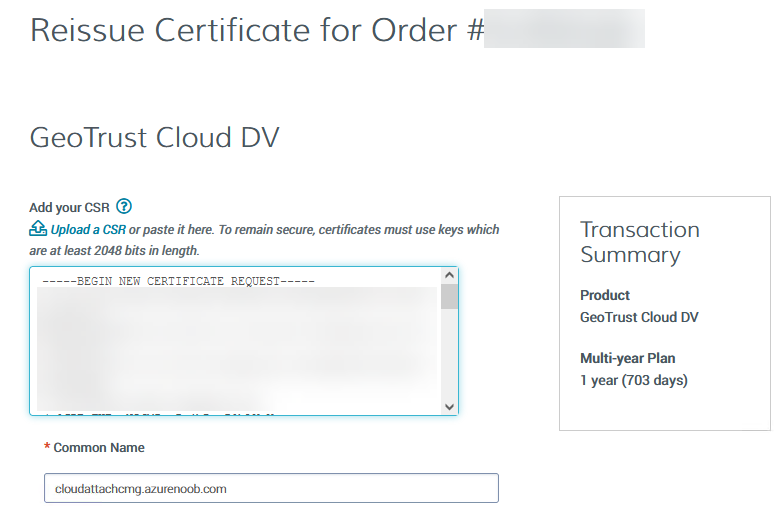
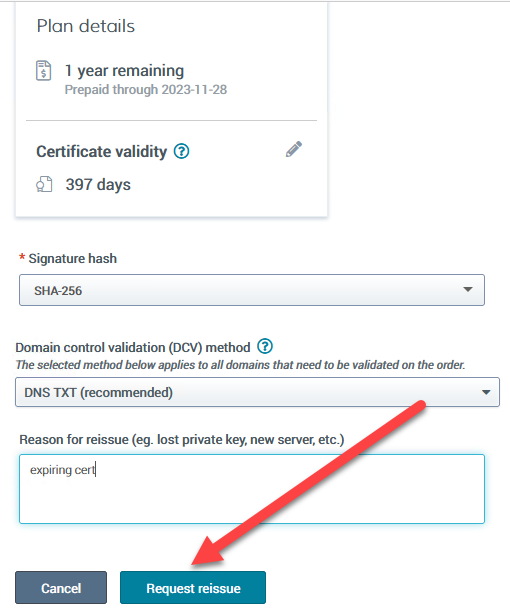
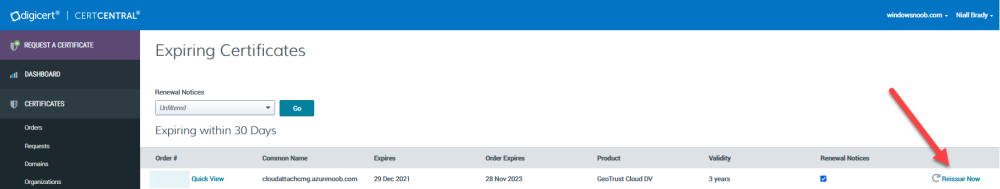
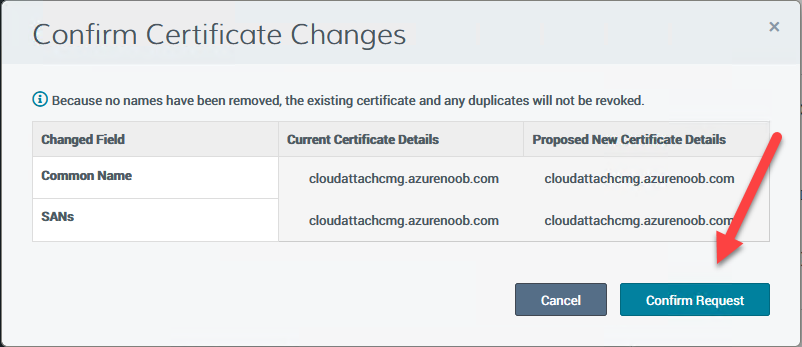
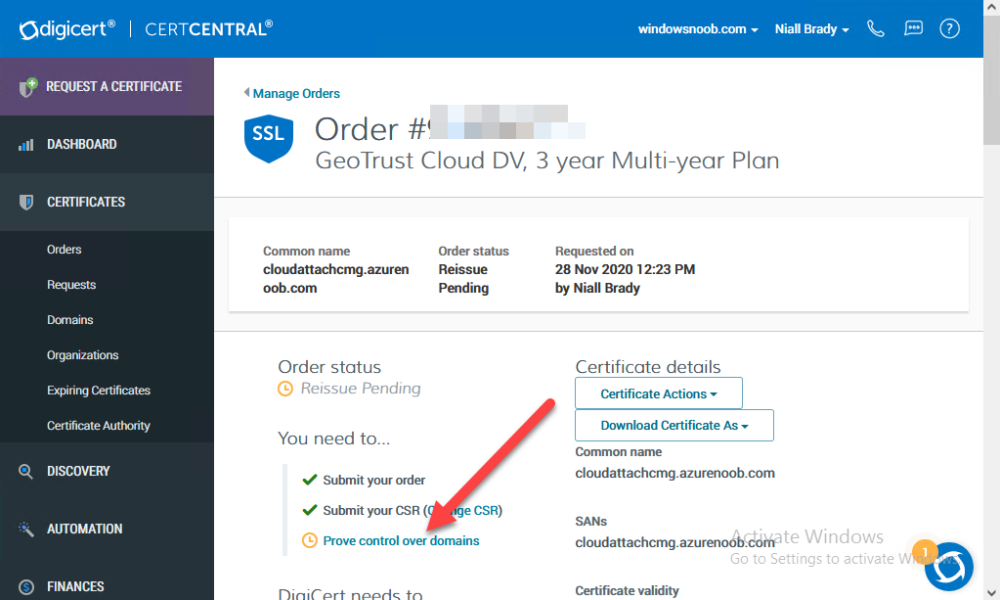
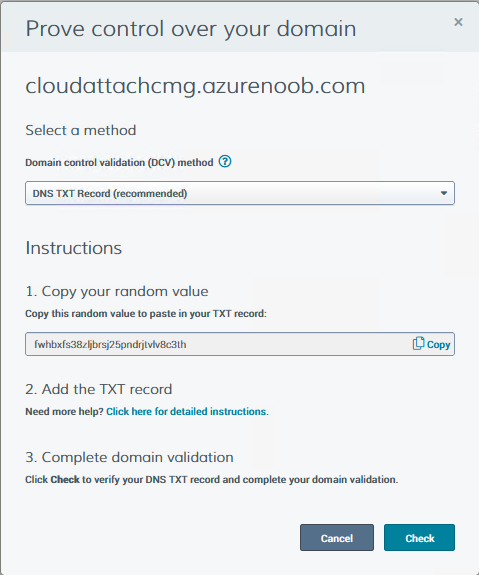
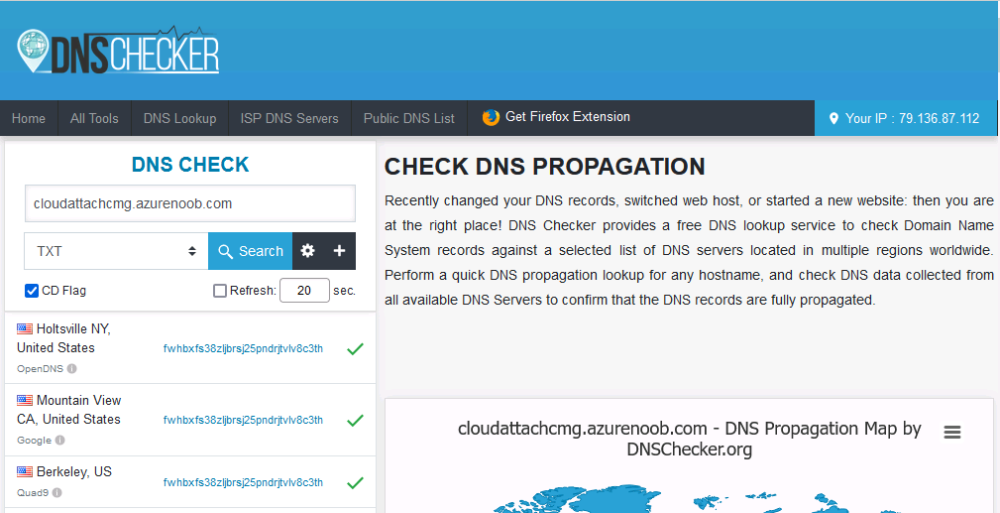
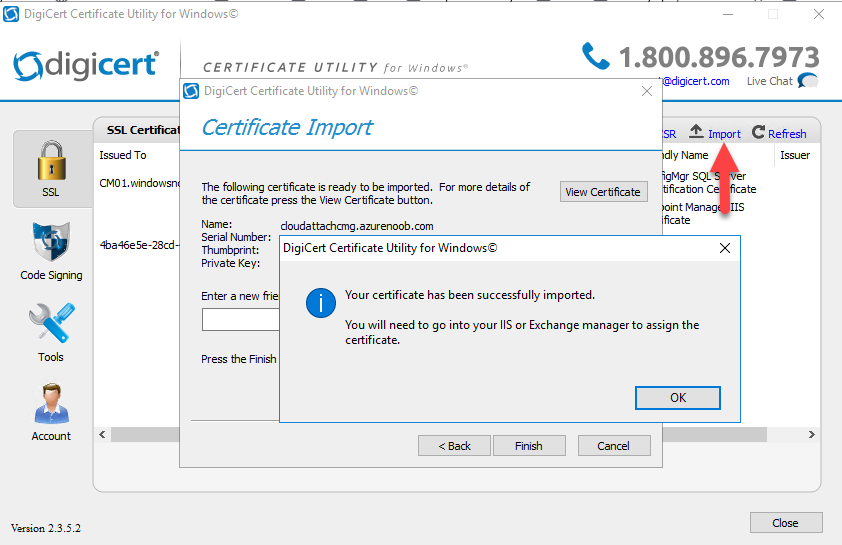
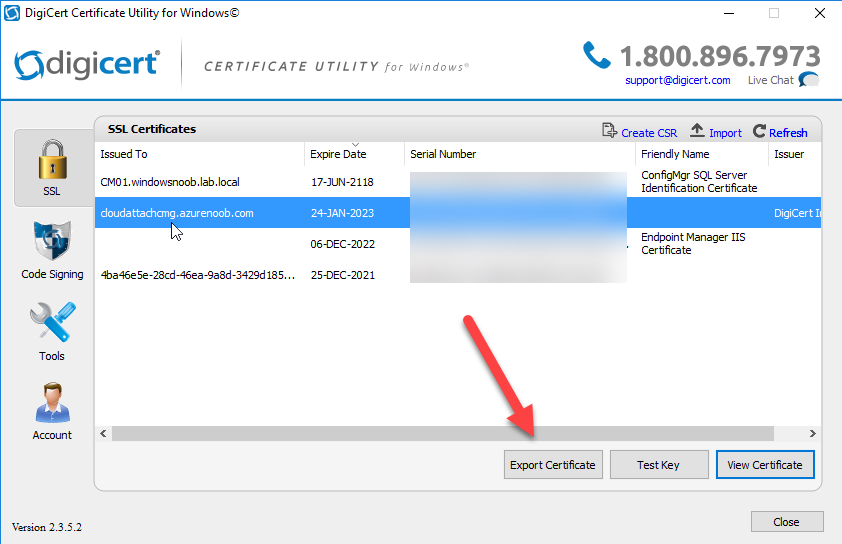
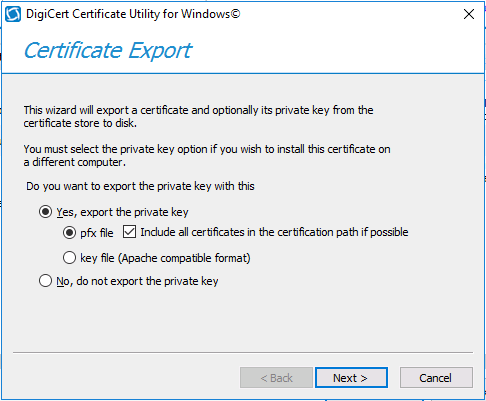
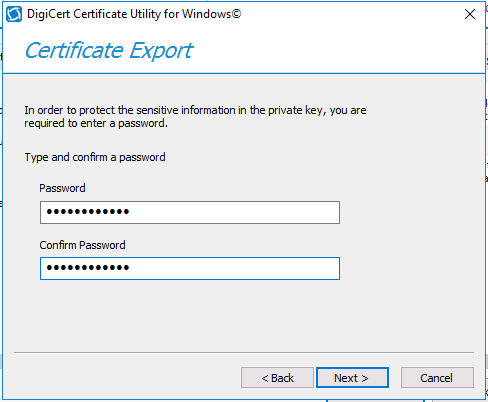
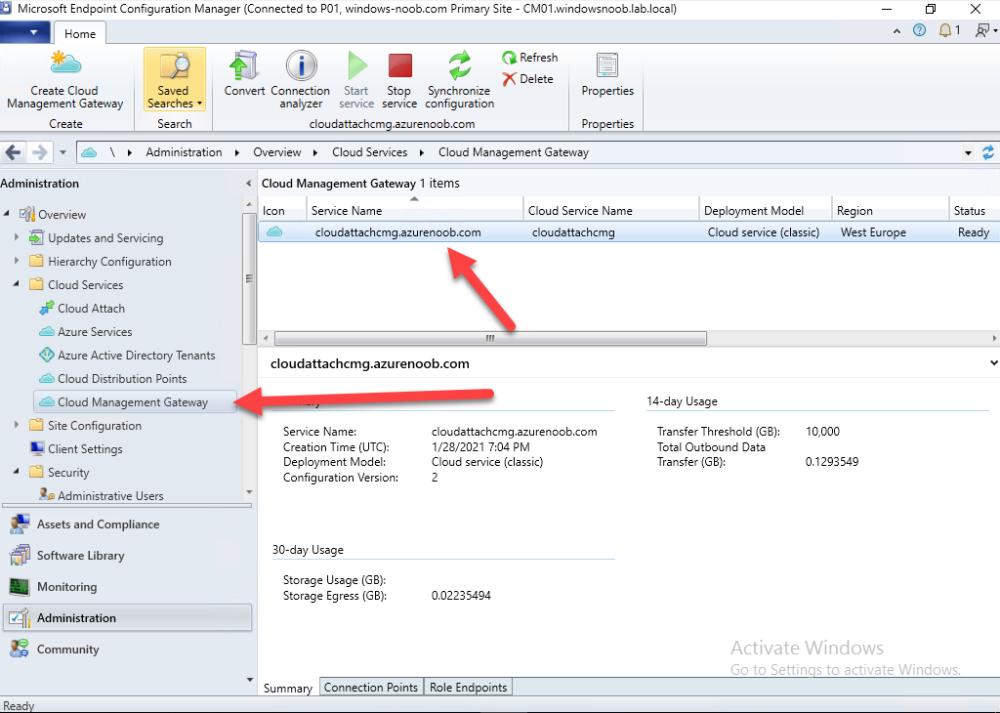
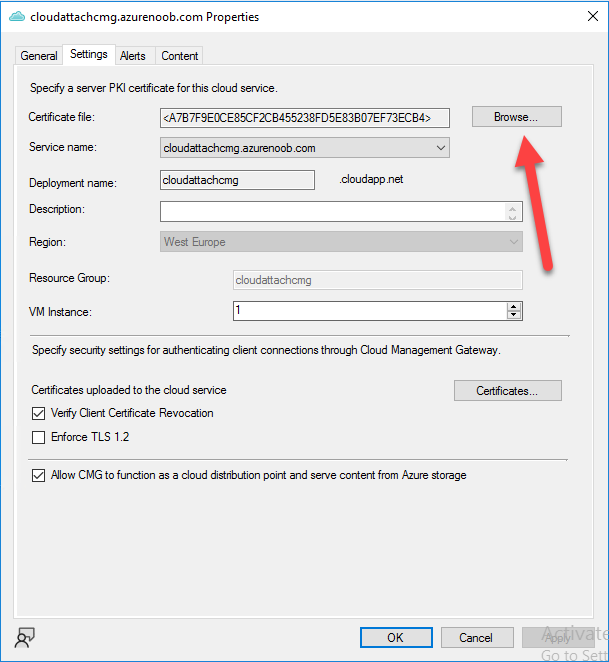
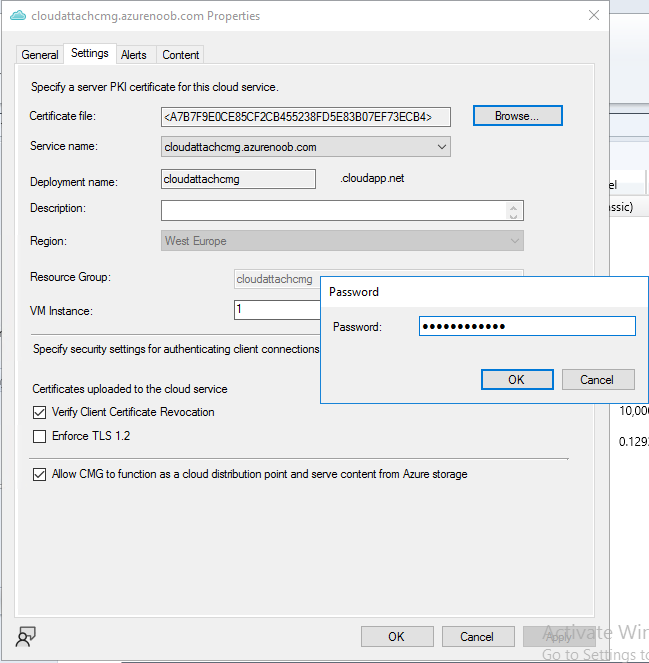
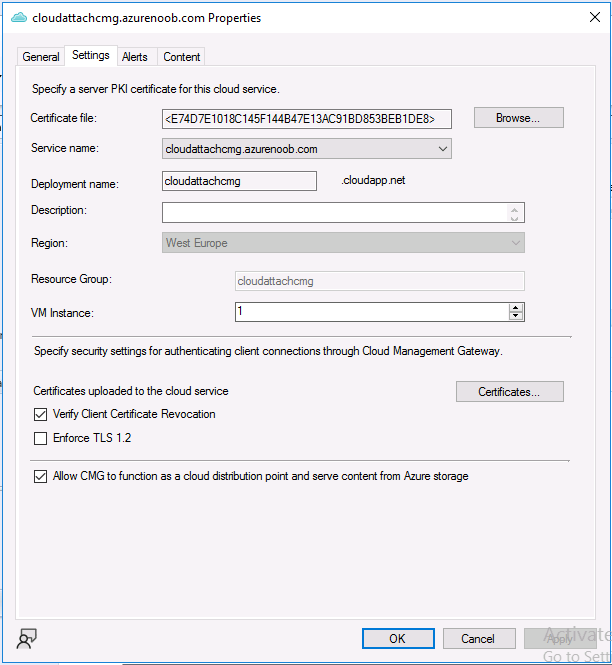
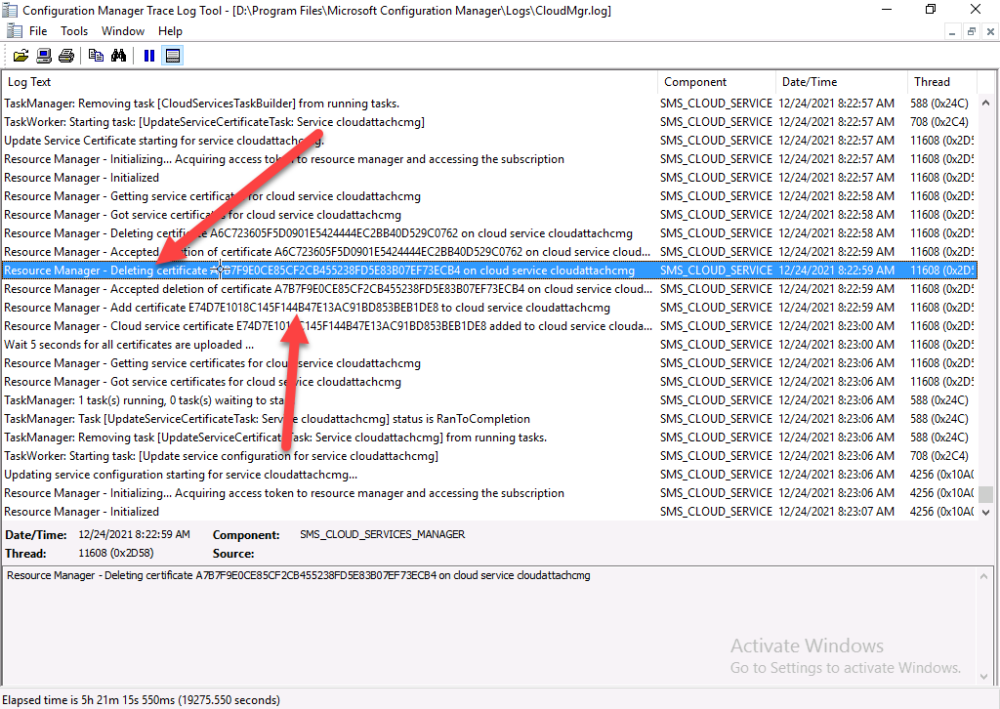
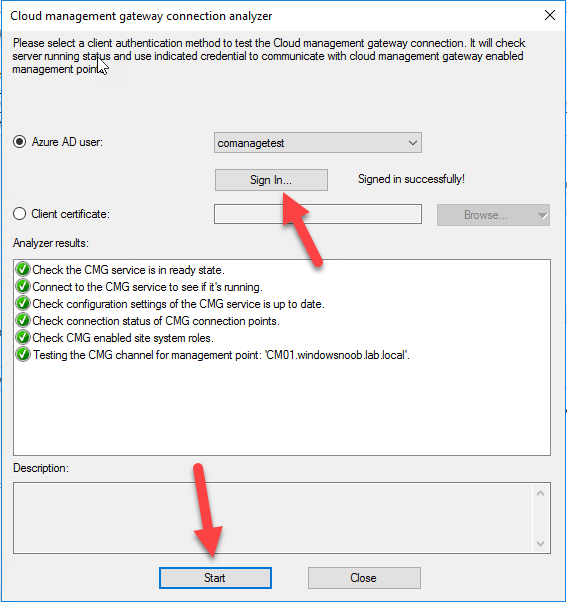
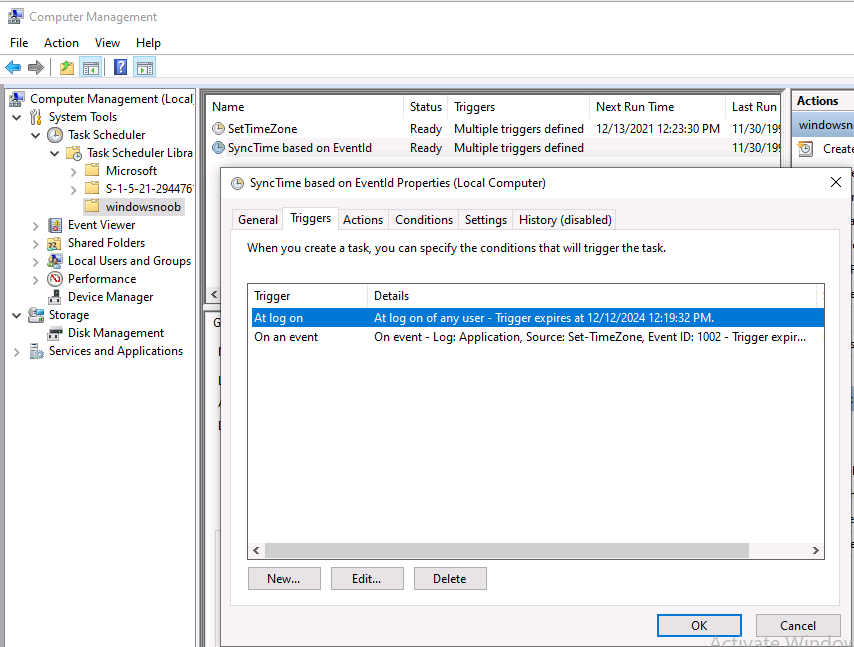
Introduction This is part 9 in a series of guides about cloud attach in Microsoft Endpoint Manager, with the aim of getting you up and running with all things cloud attach. This part will focus on renewing expiring certificates. This series is co-written by Niall & Paul, both of whom are Enterprise Mobility MVP’s with broad experience in the area of modern management. Paul is 5 times Enterprise Mobility MVP based in the UK and Niall is 11 times Enterprise Mobility MVP based in Sweden. In part 1 we configured Azure AD connect to sync accounts from the on premise infrastructure to the cloud. In part 2, we prepared Azure resources for the Cloud Management Gateway, in part 3 we created the cloud management gateway and verified that everything was running smoothly. In part 4 we enabled co-management. With co-management, you retain your existing processes for using Configuration Manager to manage PCs in your organization and you gain the additional advantage of being able to transfer workloads to the cloud via Endpoint Manager (Intune). In part 5 we enabled the compliance policies workload and reviewed how that affected a co-managed computer. In this part we will enable conditional access and see how that can be used to deny access to company resources. In part 6 we configured conditional access and used it to deny access to company resources unless the device was encrypted with BitLocker. In part 7 we showed you how to co-manage Azure AD devices. In part 8 we enabled Tenant Attach and looked briefly at it's features. In this part we'll renew a soon to be expired certificate which we created about a year ago in part 2. Below you can find all parts in this series. Cloud attach - Endpoint Managers silver lining - part 1 Configuring Azure AD connect Cloud attach - Endpoint Managers silver lining - part 2 Prepare for a Cloud Management Gateway Cloud attach - Endpoint Managers silver lining - part 3 Creating a Cloud Management Gateway Cloud attach - Endpoint Managers silver lining - part 4 Enabling co-management Cloud attach - Endpoint Managers silver lining - part 5 Enabling compliance policies workload Cloud attach - Endpoint Managers silver lining - part 6 Enabling conditional access Cloud attach - Endpoint Managers silver lining - part 7 Co-managing Azure AD devices Cloud attach - Endpoint Managers silver lining - part 8 Enabling tenant attach Cloud attach - Endpoint Managers silver lining - part 9 Renewing expiring certificates <- you are here Cloud attach - Endpoint Managers silver lining - part 10 Using apps with tenant attach A certificates validity is set in stone when it's created, and as time passes the certificates validity will eventually expire. When a certificate expires, anything that relied on it to approve communication will no longer work, so keeping a close eye on your certificates validity and noting when they expire is a good practice to avoid any disruption to services within your organization. Note: The Configuration Manager console (as of ConfigMgr version 2111) does NOT keep you alerted of the expiring certificate, so you'll have to keep track of it yourself by paying attention to those emails from your certificate provider. Digicert does however notify you by email about the coming expiration, at 90 days, 30 days and 7 day intervals. Step 1. Create a new CSR Note: You should avoid using the CSR generated during the initial certificate creation, as this is not secure and can compromise your SSL certificate usage. In Part 2 of this series, we downloaded a digital certificate utility from DigiCert for creating a Certificate Signing Request (CSR) but you can do this process on an IIS server see here. A CSR is a block of encoded text that is given to a Certificate Authority when applying for an SSL Certificate. It is usually generated on the server where the certificate will be installed and contains information that will be included in the certificate such as the organization name, common name (domain name), locality, and country. Source Using the tool above (from Digicert, our external SSL certificate provider, there are many to choose from), click on Generate to create the CSR. After generating the CSR, save it to a file. Step 2. Reissue the expiring certificate Next, login to your certificate provider (in this case Digicert) and locate the soon to be expired certificate. To the right click on Reissue Now. In the window that appears paste in the newly generated CSR from step 1. Enter a reason why you want the certificate reissued and then click on Request reissue. Finally, click on Confirm request. At this point, you will see a summary screen like this, take note that to complete the process you'll have to prove ownership of the domain by clicking on Prove control over domains. We chose the option to use a DNS TXT Record (recommended). Copy the TXT record and then login to your Domain Name registrar (eg: godaddy) and select the domain name, then paste in the DNS txt record value, below is the record created from above. Note: If your domain name registrar is GoDaddy or uses the same UI as GoDaddy, you may need to temporarily delete any CNAME that matches the hostname prior to adding the TXT record. After validating the TXT record, you can delete the TXT record and add the CNAME back. This seems to be a bug in their UI. After creating the TXT record you can verify it with dnschecker.org, as shown here, this is helpful in troubleshooting whether your DNS record (TXT, CNAME etc...) is valid or not. Be sure to enter the cloudattachcmg prefix (yours will be different obviously) into the record for the TXT DNS validation otherwise it might have problems finding the TXT record. Step 3. Download the CRT After verifying that you own the domain, you'll be able to download the reissued CRT (certificate) from the certificate provider (eg: DigiTrust). Step 4. Import the CRT Next, import the downloaded CRT back into the Digicert tool by clicking on Import and pointing it to the extracted CRT file in the zip you downloaded. Step 5. Export the pfx Select the Imported certificate, click on Export Certificate choose the option to export pfx You'll be prompted for a password and you'll be informed of the successful export. Step 6. Reconfigure the Cloud Management Gateway In the ConfigMgr console, select Cloud Services and select Cloud Management Gateway. In the CMG properties, choose the Settings tab and click Browse beside the currently expiring PKI certificate Point it to the previously exported PFX file and enter the password when prompted Click Apply, notice that the Certificate File will have changed The CloudMgr.log will record this old certificate deletion and the addition of the reissued certificate. At this point, the hard work is done and your certificate is reissued, and your CMG is reconfigured to use the new certificate. You can verify the CMG is working properly by running the Connection Analyzer. Job done, please join us in the next Cloud Attach blog post, early next year !
-
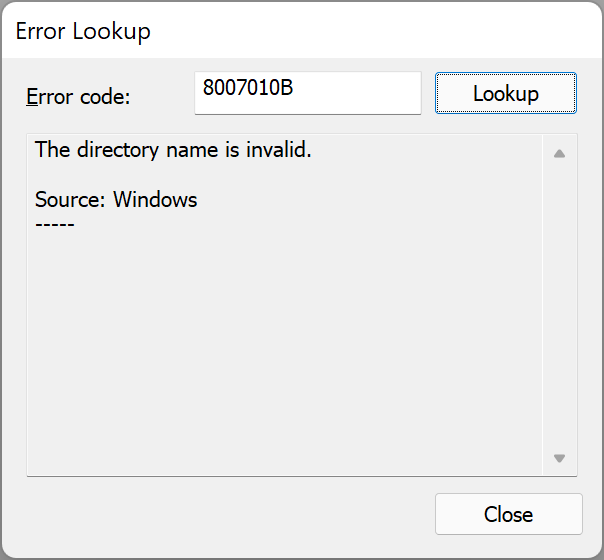
the first problem seems to be this CreateProcessAsUser failed. Code(0x8007010B) which translates to... you could try pressing F8 when the HTA is on screen, and running your powershell script manually to see if that gives any clues, or modify the original script to include logging to capture the exception message to a log file so we see what's actually wrong, that's what i'd do...
-
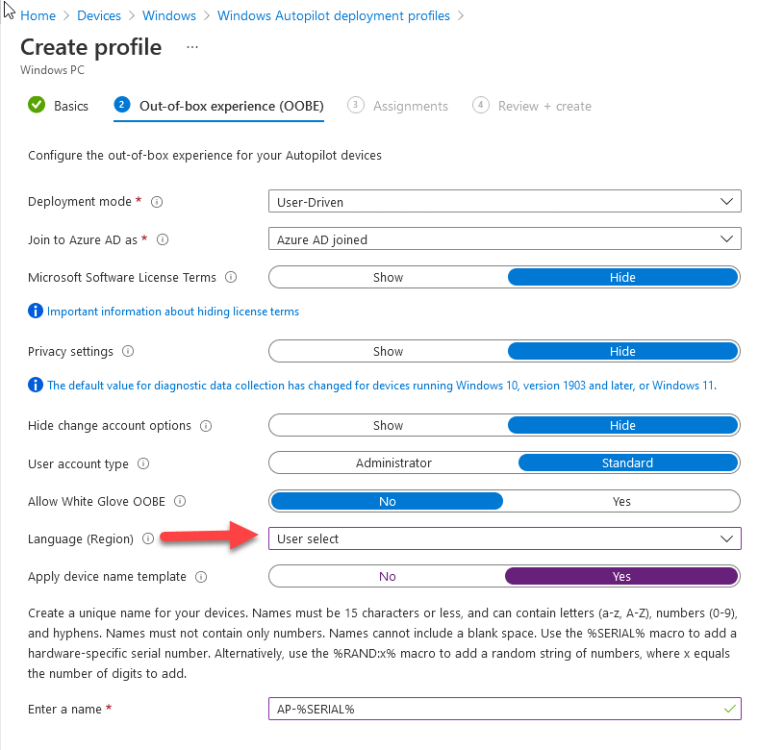
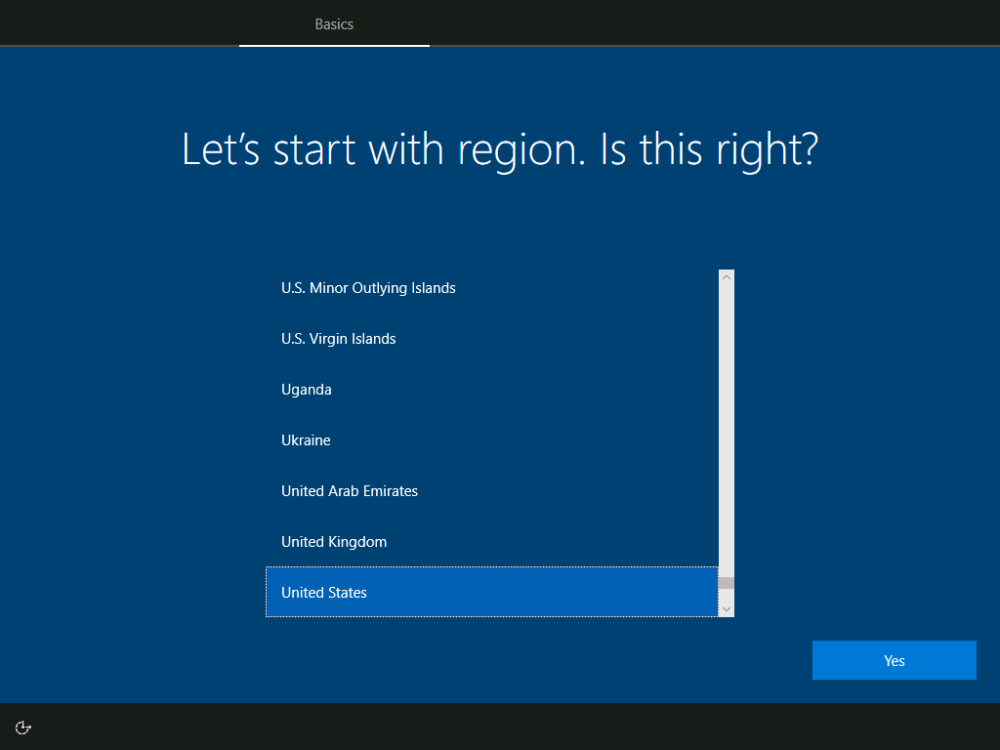
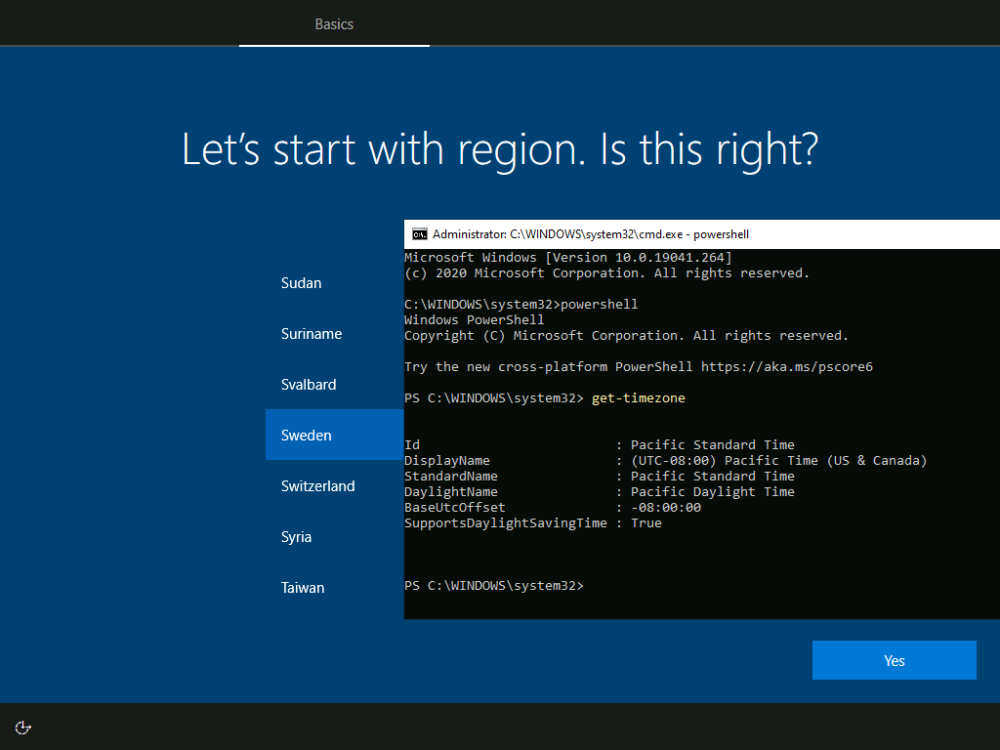
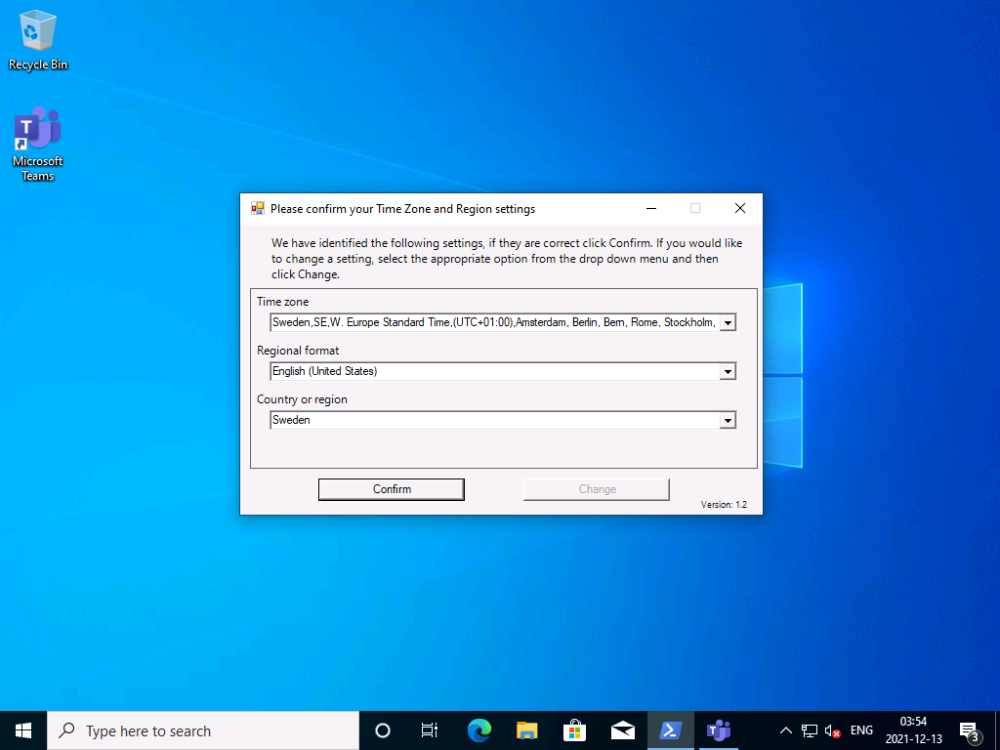
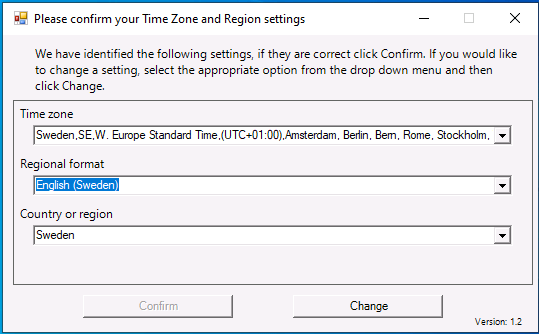
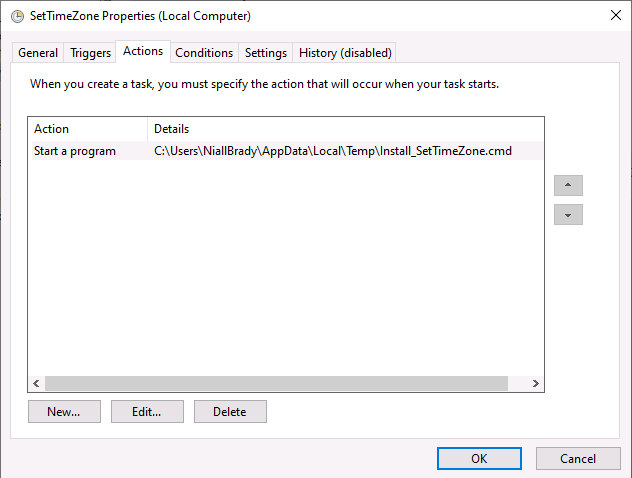
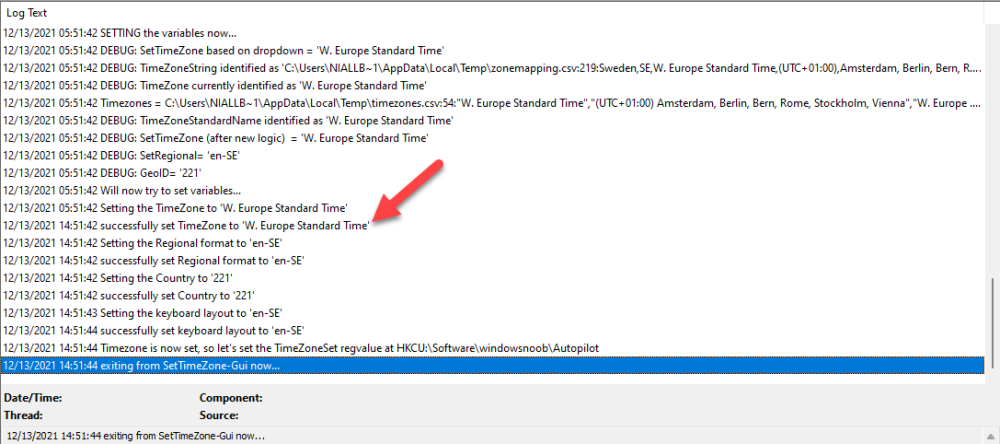
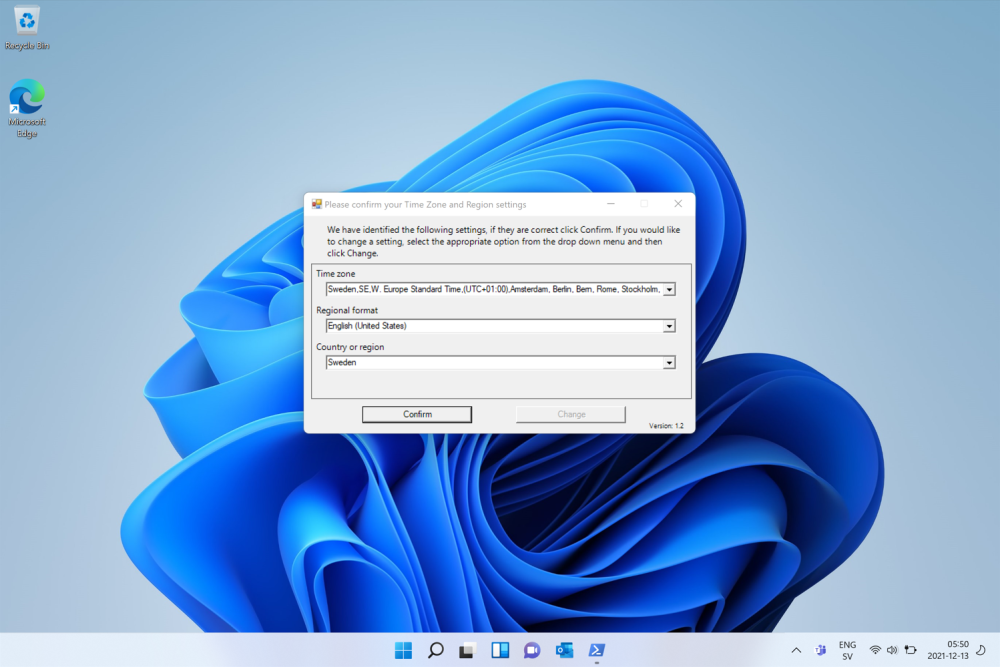
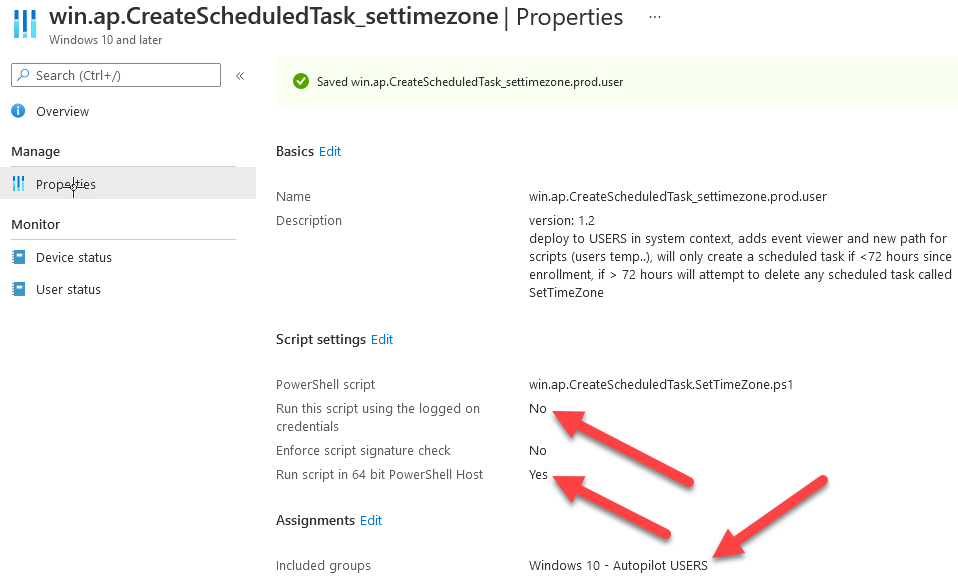
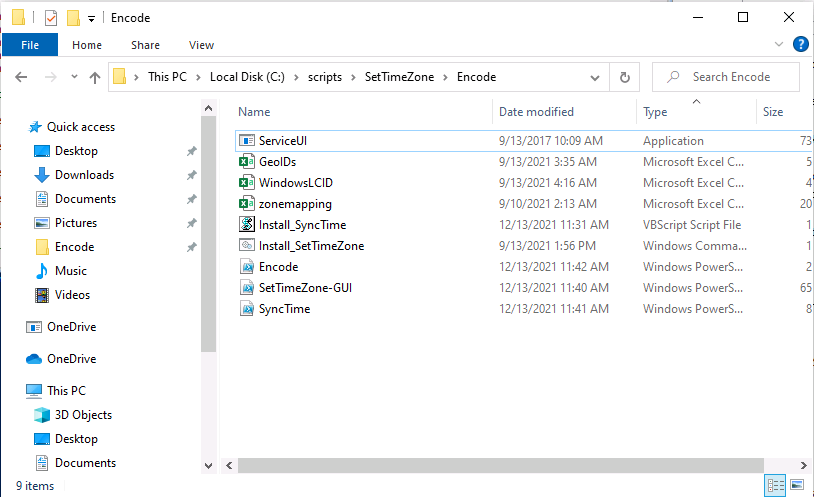
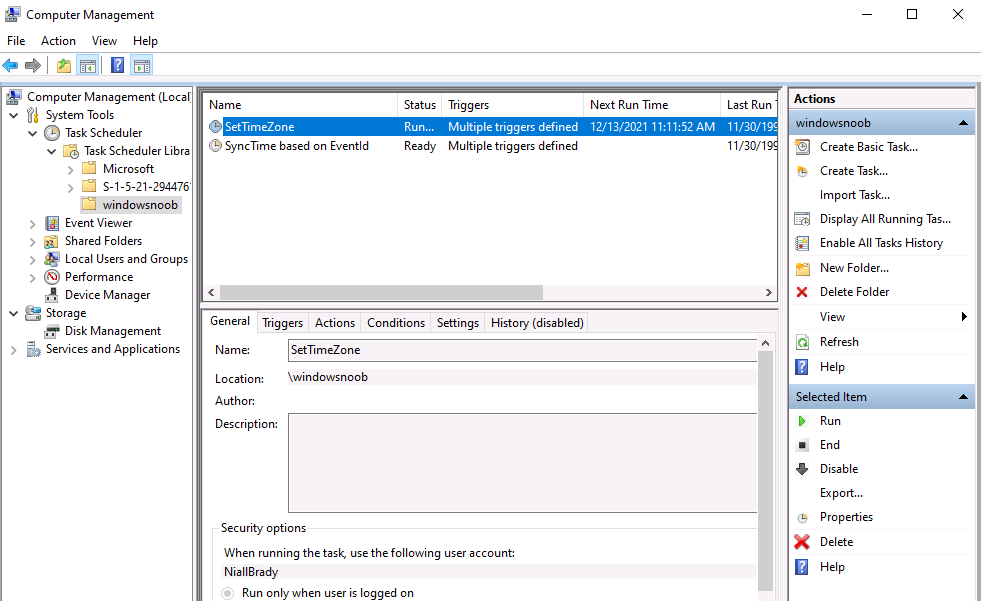
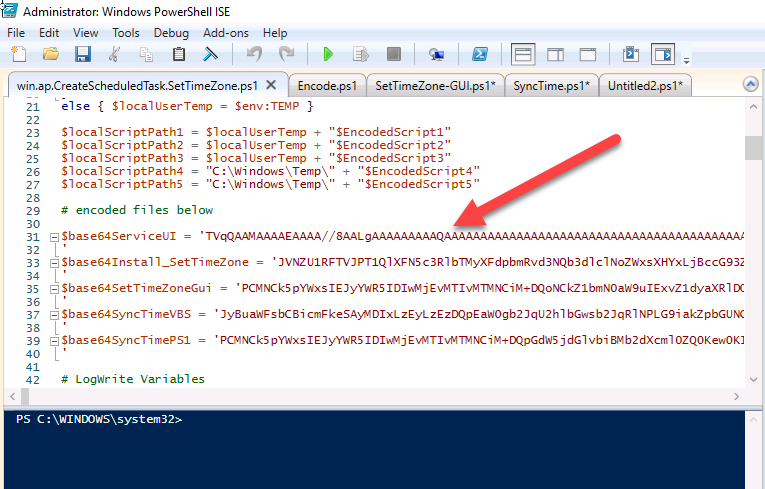
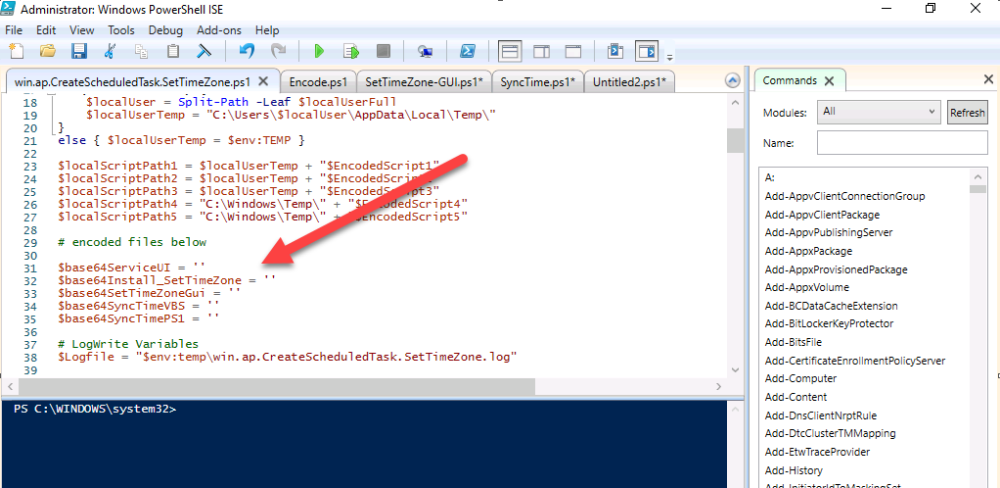
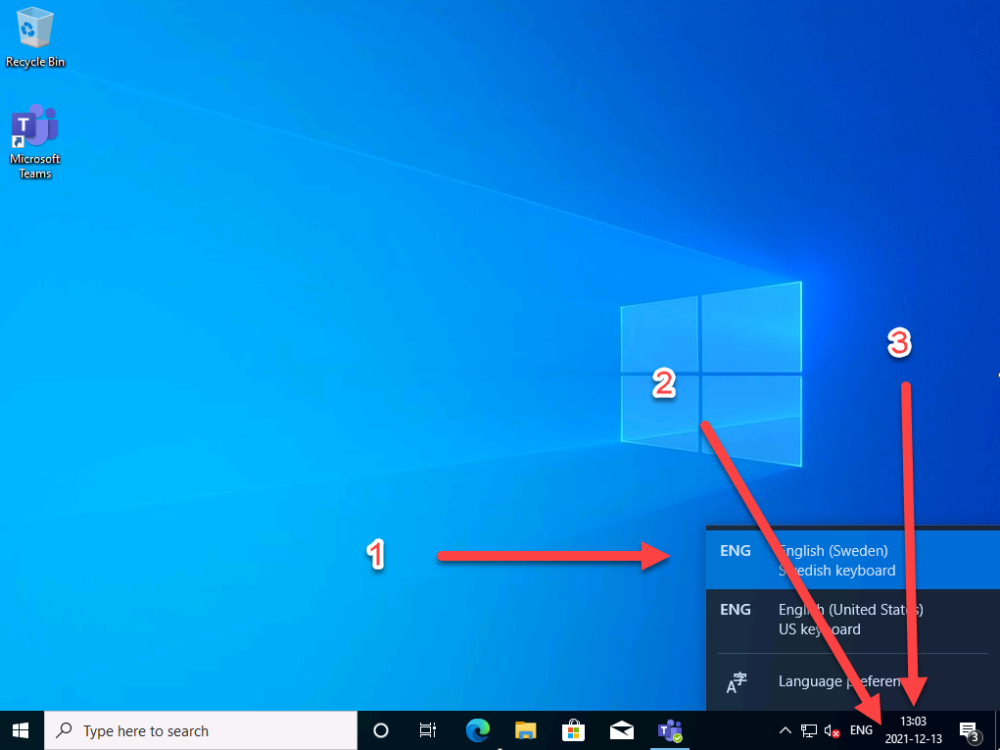
Introduction When users complete Windows Autopilot Out of Box Experience (OOBE), they can be asked to confirm Country and Keyboard settings, based on what is configured in the following Windows Autopilot Deployment Profile settings. Below is the Windows Autopilot deployment profile settings used for this blog post, notice how the User account type is set to Standard. Notice also that the Privacy settings setting is set to Hide. Your users will most likely be used to seeing the region related screens during OOBE, for example: However if you disable Privacy Settings in the Windows Autopilot Deployment profile, even though you might allow users to select Country and Keyboard settings, Windows Autopilot still sets the Time Zone to Pacific Standard Time. You can confirm this behavior by pressing left shift+F10 and typing PowerShell then Get-TimeZone. This Time Zone will apply regardless of what country the user selects. Even if your users are tech-savvy enough to find out where in Windows Settings they need to change these region based settings, if they are a standard user (which they should be in today's security conscious world), changing the timezone may leave them with incorrect time and incorrect regional format settings in the operating system. To fix this you could use Geo location and Azure services as per Nickolaj's post here, provided of course that: Your company allows Geo location Your company is not using any proxies or VPN's that mask the users actual location. This solution is not affected by either of these things, doesn't need local administrative permissions and does not require enabling privacy settings. This solution prompts the end user to confirm (or change) the detected settings, and then uses some back end magic to set everything in place including triggering a time sync. This method works even for standard (non administrator) users. Requirements The method requires that you use the English (En-US) version of Windows 10 as delivered from your OEM. If any other language is applied from the factory then it might cause some of the logic to fail. If you do go down that route, then you'll need to prepare language specific versions of the zonemapping.csv and other files as necessary. So let's get started. You can always install language packs later. Step 1. Get the scripts Note: You can only download these files when logged on as a member of https://www.windows-noob.com Note: Intune has a hard block of 200,000 bytes per PowerShell script. To get around this limit, I've removed most of the original comments from the Powershell scripts. The resulting script can be uploaded to Intune as it's less than the 200,000 bytes limit even with all the files encoded. If you'd like a copy of the version with comments included to help with troubleshooting, scroll to the very bottom of this blog post. Download the condensed ZIP: win.ap.CreateScheduledTask.SetTimeZone_CONDENSED_VERSION.zip Extract the condensed ZIP file to C:\Scripts\SetTimeZone Step 2. Get ServiceUI.exe from MDT You'll need the ServiceUI.exe executable file to display user interfaces (UI) to end users when operating in SYSTEM context. To get the file, download and install MDT somewhere and navigate to C:\Program Files\Microsoft Deployment Toolkit\Templates\Distribution\Tools\x64. To download MDT click here. Copy the ServiceUI.exe file to your extracted SetTimeZone\Encode folder so it looks like this. Step 3. Modify the scripts Open SetTimeZone-GUI.ps1 and SyncTime.ps1 in PowerShell ISE and make changes as appropriate. Once done editing those scripts to suit your needs save the changes. Then run the Encode script to generate the encoded txt files which you will paste into the variables highlighted below. you can do that by locating the appropriate TXT file for each encoded file, for example for ServiceUI.exe it'll be the ServiceUI.txt file, open it in notepad, copy the contents of that file using CTRL+A and CTRL+C and paste the results using CTRL+V into the associated variable, once you've done all 5 encoded files it'll look something like this If you are happy with all the changes in win.ap.CreateScheduledTask.SetTimeZone.ps1, save the changes. Step 4. Deploy it from Intune In Microsoft Endpoint Manager, select devices, scripts and add a new PowerShell script. Fill in some details like so. Deploy it to your Windows Autopilot users (start with a small group of users to test...), note that if you deploy this script to users that have already enrolled, the script checks if the enrollment was within the last 72 hours and if it was it will run, but if the enrollment was more than 72 hours ago, it'll do nothing. Step 5. Test it out First off, let's see what the expected outcome is. After Windows Autopilot enrollment is complete, and the user has logged on to the desktop, shortly after they login they will see a popup window asking them to Confirm or Change their Time Zone and Region settings. Below is an example of that. The user can confirm the settings by simply clicking Confirm, or if they want to change any of the options they can do so by clicking the relevant drop down menu. In this example the user changed the Regional format to English (Sweden), from English (United States) and after clicking Change the settings are applied. The following will occur when Confirm or Change is clicked. The keyboard layout is set (1), the regional format is in the chosen format (2) and the time will change to the selected timezone within one minute (3). The time sync takes place via an event generated in event viewer by the SetTimeZone-Gui script. Windows 11 support Does it work with Windows 11 ? absolutely ! see here: Job done ! Troubleshooting Note: If you are testing this on a hyper-v virtual machine, please disable enhanced mode. There are three log files generated by this solution win.ap.CreateScheduledTask.SetTimeZone.log located in C:\Windows\Temp win.ap.SetTimeZone-GUI.log located in C:\Users\<username>\appdata\local\Temp win.ap.synctime.log located in C:\Windows\Temp Here you can see it changing the time zone as revealed in the log file time change... the following scheduled tasks are created. The SetTimeZone scheduled task will run within a few minutes of the user logging in, it runs the following script. which in turn launches Powershell and our SetTimeZone-Gui.ps1 script %SYSTEMROOT%\System32\WindowsPowerShell\v1.0\powershell.exe -NoProfile -WindowStyle Hidden -ExecutionPolicy Bypass -File %temp%\SetTimeZone-Gui.ps1 That will launch the UI shown previously, allowing the end user to confirm or change the detected settings. Once the user confirms or changes the timezone settings an event ID will be generated which will in turn launch the Synctime Based on EventId task. Magic ? If the user ignores the popup and restarts the computer, it will appear again after logging on every time they logon for 7 days. You can change that behavior via the scripts settings.Ok that's it for this blog post, see you next time, cheers niall Related: https://smsagent.blog/2022/05/13/beware-of-changing-regional-format-after-intune-enrolment/ Footnote: Here is the commented version of ZIP. This version of the scripts cannot be uploaded to Intune as it's too big, use for troubleshooting purposes only.win.ap.CreateScheduledTask.SetTimeZone_COMMENTED_VERSION.zip