-
Posts
9252 -
Joined
-
Last visited
-
Days Won
369
Everything posted by anyweb
-

Password Protect a Task Sequence?
anyweb replied to thadkew's question in Frontends, HTA's and Web Services
you could also use the BitLocker FrontEnd HTA to do this here http://www.windows-noob.com/forums/index.php?/topic/4811-introducing-the-bitlocker-frontend-hta/ -
the only thing to think about is if there are any Group Policies pointing to the old WSUS server you'll need to remove them as ConfigMgr will want to control software update delivery
-
lots of errors in there, can you verify that your management point is working, this link is for cm07 but it works the same way http://technet.microsoft.com/en-us/library/bb932118.aspx and once again, in monitoring, system status, component status, are things looking all green or mostly red ? any obvious issues in there (like management point being dead ?)
-

issues deploying power management SCCM 2007 R3
anyweb replied to jackface_o's topic in Configuration Manager 2007
have you tried pushing the configuration manager client to the client AFTER upgrading to R3 ?- 2 replies
-
- power management
- SCCM 2007
-
(and 1 more)
Tagged with:
-
is it definetly restarting ? when you do run chkdsk are you seeing lots of errors found ? if so consider running a chkdsk 'job' on these systems one week before they are to be migrated, as an idea....
-
Introduction During Windows 8 deployments, if you are using wireless capable computers then you’ll most likely have wireless enabled on them by default and this means that the following screen will most likely appear during Windows 8 setup (OOBE). The installation will halt until you pick a wireless network or until you click on the Connect to a wireless network later link. That is great if you want to connect to a wireless network during setup, but not great if you want everything automated, so how do we stop this screen from popping up ? We can create a custom unattend.xml file to change this behavior and the best way of doing this is by using Windows SIM which is a component of the Deployment Tools which in turn is part of the Windows Assessment and Deployment Kit (Windows ADK). So if you havn’t installed the ADK yet, do so now. Step 1. Start Windows SIM Start up Windows SIM located in the start menu on your Server 2012 install or it can be found here on traditional Server 2008R2 start menu The application will appear pretty bland on first start but we’ll change that soon enough Step 2. Select a Windows Image and create a new Answer File Click on File and choose Select Windows Image, browse to the path of your Windows 8 media and select the Install.WIM file located in the sources folder of that media, if it’s the first time you’ve done this you’ll get a message about the Catalog File being missing, answer Yes. Note that you’ll need to be logged on as a local administrator of this machine. Next you’ll see Windows SIM is mounting the image to generate the catalog file and once it’s done mounting the image and generating the catalog file you’ll see your image listed in the Windows Image section of Windows SIM. Now click on the File menu again, and choose New Answer File, this will populate our Answer File Pane with the 7 passes of a Windows Deployment. Step 3. Add our changes to the answer file Expand Components and scroll down the component called amd64_Microsoft-Windows-Shell-Setup_6.2.9200.16384_neutral click on the plus to the left of this component and find a section in it called OOBE (out of box experience), select it. You will note that the settings associated with this section are listed to the right in the OOBE Properties window pane however we cannot do anything with them until we add them to a Pass. Right click on OOBE and choose Add Setting to Pass 7 oobeSystem find the setting HideWirelessSetupInOOBE and click on the drop down menu, select TRUE to hide this. Step 4. Save our Changes to the Answer File And for the purposes of this post, we are done with editing this unattend.xml (however feel free to experiment with the settings listed), click on File and choose Save Answer file as Save the file on your Configuration Manager server in your \\server\sources\os\unattend xml\ folder as HideWirelessSetupInOOBE.xml. (If you are are doing many customizations in your xml name it unattend.xml for simplicity) Step 5. Create a Package in Configuration Manager Now we need to create a package containing this unattend.xml file within Configuration Manager 2012. In the Software Library workspace, select Application Management, Packages, and choose Create Package. fill in some details about the package making sure to select This Package Contains source files and browse to the UNC where you saved your Unattend.xml file earlier. Click next and select Do not create a program (as none is needed) and continue through the wizard to completion. Step 6. Distribute Content Now that our package is made we need to distribute the content to our distribution points otherwise our clients cannot find it. Right click on our newly created package and choose Distribute Content. The Distribute Content wizard appears, select next Add your distribution points by selecting Add, select Distribution Point from the drop down menu and placing a check mark beside any DP you want to include, and then click next through the remainder of this wizard Step 7. Edit your task sequence Now all the steps are in place to edit our task sequence to add our unattend file, so select your Deploy Windows 8 task sequence, right click and choose Edit. and select the Apply Operating Image step, in this step place a checkmark in Use an unattended or sysprep answer file for a custom installation and browse to our previously created package, select the package, click ok and type in the name of our unattend.xml file as in the screenshot below: Click Apply and you are done, try a new deployment and note that you are no longer prompted to Connect to a wireless network during OOBE. cheers niall
-
Introduction To UEFI The Legacy BIOS that we are all accustomed to has been around for a long time and is showing it’s age, for example it cannot handle discs larger than 2TB in size. Realizing the need for change, Intel originally created the Intel Boot Initiative back in 1998. Within a few years a bunch of well known companies (including Microsoft, HP, Dell, AMD and others) got together and formed the UEFI specfication which was the next logical step in its evolution. Unified Extensible Firmware Interface (UEFI) is meant as a replacement for the legacy BIOS present in all IBM PC-compatible personal computers.As a result, most modern computers today will have a bios that is both Legacy (bios) and UEFI capable, for example on a Dell Latitude E6320 you have both options available in the BIOS screen under the General, boot Sequence, Boot List Options menu. More than likely it’s already set to Legacy, but we will be changing that later in this post. Microsoft introduced UEFI for x86-64 Windows operating systems with Windows Server 2008 and Windows Vista Service Pack 1, so the 64-bit versions of Windows 7 are compatible with EFI. 32-bit UEFI is not supported since vendors did not have any interest in producing native 32-bit UEFI firmware because of the mainstream status of 64-bit computing. Windows 8 includes further optimizations for UEFI systems, including a faster startup and secure boot support. With the recent release Windows 8 RTM and updates released for Configuration Manager 2012 to support Windows 8 (amongst other things via the CTP release of SP1) we now have the ability to create task sequences with UEFI abilities built in. But first before you try using UEFI please understand one thing, it’s very different to what you are used to with the traditional bios so there is a learning curve. Don’t expect PXE boot (via UEFI) to work currently as network drivers for it are not readily available (you might see them on certain servers, contact your hardware manufacturer for details). Step 1. Verify your client computer supports UEFI Most OEM manufacturers are releasing UEFI capable computers nowadays but check the actual bios/computer specifications online first (or verify with the manufacturer) before attempting this. In my BIOS screenshots in this post I’m using a Dell Latitude E6320 with Bios version A05. This laptop is both Legacy Bios and UEFI capable. If your computer is not UEFI capable then you’ll have to get one that is (if you are lucky, a bios upgrade on your computer to the latest version may enable this functionality). Step 2. Upgrade ConfigMgr to SP1 To deploy Windows 8 in Configuration Manager 2012, you’ll need to install the Windows Assessment and Deployment Kit and to upgrade ConfigMgr to Service Pack 1 which is currently in Community Technology Preview phase (CTP 1). See here for a link describing how to install both.Note: As a result this means you have to do this in your LAB as the CTP release is not supported in production. Step 3. Add Operating System Image. In your newly updated ConfigMgr console, click on the Software Library workspace, Operating System Deployment and select Operating System Images, right click and choose Add Operating System Image When the wizard appears, browse to the path of the Windows 8 installation media, and select the Install.WIM file contained in the Sources folder of that media. (This is ok, Windows will not get installed on D: like it used to) continue through that wizard until completion. Step 4. Distribute Content to your DP’s Right-click your newly added Windows 8 WIM image and choose Distribute Content, select your dp’s and you are good to go complete the wizard. You can review content status to verify that your WIM image has reached your distribution points. Step 5. Create a Deploy Task Sequence In this post we will create a Deploy task sequence, in a future post I will explain how to do a Build and Capture task sequence and link it here.Right click on Task Sequences, and choose Create Task Sequence, choose Install an existing image package fill in some details about the task sequence including a descriptive name, make sure to select a X64 boot image (64 bit boot image). Select our previously added Windows 8 RTM install.wim file and make sure that the format and partition step is selected, also type in your Windows Product Key (blanked below) and enter an administrator password. Note: if you are using a previously captured Windows 8 WIM file which has more than one image index, make sure to select the image index that contains the Operating System otherwise you will not be given any UEFI options in the task sequence. continue through the wizard until completion . Right click on your new task sequence, choose Edit, take note of the Partition Disk 0 – UEFI step, if it is not present, please review my Note above. Step 6. Deploy the Task Sequence Right click our task sequence, select Deploy, choose a suitable collection, and make the task sequence available (optional). Note the new options on the Deployment Settings screen, select only media and PXE. complete the wizard. Note: Don’t deploy task sequence to All Systems in production, otherwise bad things can happen. Instead, use specifically created OSD collections and add resources that you want to Deploy to those collections. This is a LAB so for the purposes of this post it’s ok.Step 7. Create Task Sequence Media (USB Flash Drive)In the ribbon select Create Task Sequence Media, select the first option (Standalone) and click next. Note: If you select Allow unattended operating system deployment and do not set a password on your media you risk the chance of getting a system wiped and having it’s OS replaced if you leave the USB flash drive plugged in.Select USB Flash Drive and point to your inserted USB key. Enter a security password if required then at the next screen select our Deploy Windows 8 X64 RTM – UEFI task sequence, wait until the referenced packages are listed in the box below. Add your distribution points and click through to completion and now you can take a break while the USB Flash Drive get’s created.. Step 8. Change the bios to UEFI mode On your UEFI capable computer, boot into the BIOS Setup screen and enable UEFI as the boot type. The screenshot below is from a Dell E6320 (the UEFI bios options look different on Lenovo but can enable the same functionality), select boot sequence, and then Boot List Option in the bios screen, by default Legacy is selected, choose UEFI from the list. Save your settings and exit from the Bios. Now you are ready to boot to UEFI. Step 9. Start the deployment Boot the computer and press F12 to get a one-time-boot menu, notice the UEFI device is listed as UEFI: INT13(USB,0×80) Select the UEFI device and press enter to start deploying, you’ll notice once the partitioning step starts that it is partitioning the disk for UEFI. Note: if it states that it’s partitioning the disk for BIOS instead then you are not getting a UEFI deployment and you’ll need to press F8 and start reading the SMSTS.log file to find out why. During our UEFI deployment, if you examine the SMSTS.log file you should see a line that reads:- and that the read only variable _SMSTSBootUEFI is set to True.Once Windows has finished deploying you run can diskpart you’ll see it has created the UEFI partitions also. Step 10. Verification In addition to checking your partition layout, you can open an administrative command prompt and type bcdedit /v to list the Windows Boot Manager (should be listed as EFI) and Windows boot Loader should reference winload.efi. And you can run msinfo32 to see BIOS Mode listed as UEFI (thanks Mattias) That’s it, job done, you are deploying Windows 8 systems with UEFI using Configuration Manager 2012. (you can deploy Windows 7 with UEFI in the same way with this guide) Step 11. Further reading about UEFI. The following links will give you some good information about UEFI. Introduction to UEFI Extensible Firmware Interface (EFI) and Unified EFI (UEFI) Windows and GPT FAQ Sample: Configure UEFI/GPT-Based Hard Drive Partitions by Using Windows Setup Troubleshooting UEFI if your USB key just flashes the LED when trying to boot to UEFI mode and your screen remains blank then verify that the Operating System you are trying to deploy matches the architecture of the boot image attached to that task sequence, for example, if you are Deploying Windows 7X64 in UEFI mode, the boot image must be X64 also If you create task sequence media using the ISO option (CD/DVD) and then extract/copy that content to your USB flash memory then it will be missing certain required EFI files. Note that doing it this way is unsupported !. cheers niall
-
and here's an index of all the parts I've written to make it easier to find the answer http://www.windows-noob.com/forums/index.php?/topic/4045-system-center-2012-configuration-manager-guides/
-
check KB2018585 and see how to implement that in this screenshot http://www.windows-noob.com/forums/index.php?/topic/1885-webcast-%23-1-using-offline-mode-in-windows-pe/page__st__20
-
MDT 2012 Update 1 merges that task sequence with the ZTI one - see http://blogs.technet...-sequences.aspx The choice that you make ends up configuring a specific step in the resulting task sequence: So if you want to dynamically choose “wizard or not”, you can remove this step and instead set the value through CustomSettings.ini.
-
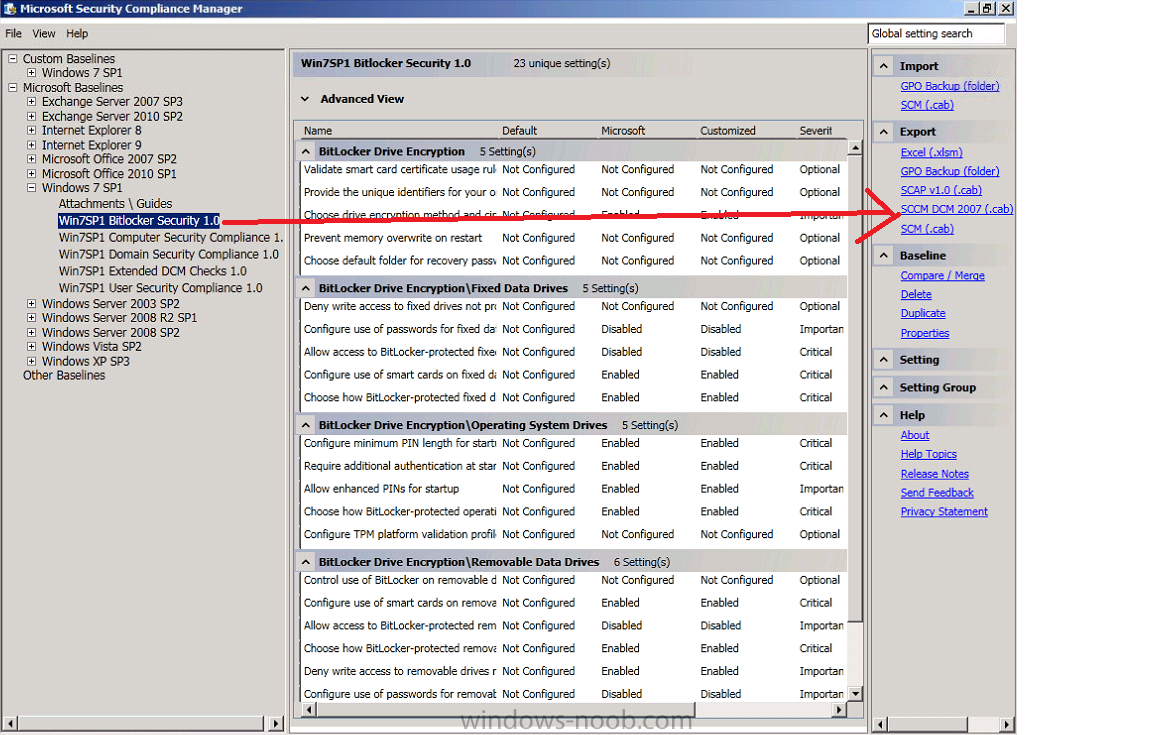
ok i've moved these posts and as Peter says, please create a new topic elsewhere especially if the question has nothing to do with the original topic and as an aside, in the administration workspace, Client Settings you can suspend Bitlocker PIN Entry on restart (check the computer agent section) and you could use Compliance Settings to enforce BitLocker settings, Security Compliance Manager has many baselines connected with this that you can import and implement, look for the one called Windows 7SP1 BitLocker Security, you can then export this baseline and use it within compliance settings in Configuration Manager. that said, management of BitLocker itself is normally carried out using MBAM or via Active Directory tools
-

using Multiple Task Sequences via PXE
anyweb replied to anyweb's question in Troubleshooting, Tools, Hints and Tips
what does your smspxe.log file tell you ? search for the MAC address of the vm you are booting. -
leave WDS alone, configuration manager will configure it for you. Are you using the RTM release of configuration manager 2012 ?
-
heh good stuff, hopefully you are only testing the CTP release in a lab as it's not for production use, cheers niall
-
Description of Cumulative Update 1 for System Center 2012 Configuration Manager Issues that are fixed Administrator Console When a new distribution point is added to a package that contains more than 100 existing distribution points, the new distribution point cannot be added, and you receive the following error message in the Administrator Console: The SMS Provider reported an error. When you click Details in the error message, a "Quota Violation" message is displayed that is followed by the details of the stack trace. The link to the online privacy statement for the Customer Experience Improvement Program in the Administrator Console is fixed. Application Management If a Deployment Type is added or changed before Distribution Manager processes an earlier change, the content may not be sent to a child site. The prestaged content file for a Deployment Type (DT) is not created for remote Distribution Points when there are multiple DTs for the same application. For more information about prestaged content, go to the following Microsoft TechNet website: Operations and Maintenance for Content Management in Configuration Manager Asset Intelligence Volume license editions of Microsoft SQL Server 2012 may be duplicated in the Asset Intelligence Installed_Software_data hardware inventory class. Microsoft SQL Server 2008 R2 Service Pack (SP1) is not listed in the Asset Intelligence License 01D - Microsoft License Ledger Products on a Specific Computer report. The pre-provisioned Asset Intelligence Synchronization Point certificate is updated with a new expiration date. Client When a dynamic list is used for the Install Application task sequence, not all deployment types will be installed. This issue occurs when one of the deployment types restarts the computer. In this case, any deployment type after the restart is not installed. The state messages that are associated with each application indicate Success. This issue can be seen most clearly in the smsts.log file on the client when the log file is filtered in the CMTrace for entries that contain the text "Installing application." The following is an example sequence: Installing application 'App 1' Installing application 'ContentID for App 1' has started. Please refer to DCMAgent.log for the details on this job. JobID='{JobID1}' Installing application 'App 2' Installing application 'ContentID for App 2' has started. Please refer to DCMAgent.log for the details on this job. JobID='{JobID2}' Installing application 'App 3 - Exit Code 3010' Installing application 'ContentID for App 3' has started. Please refer to DCMAgent.log for the details on this job. JobID='{JobID3}' Installing application 'App 4' Installing application 'ContentID for App 2' has started. Please refer to DCMAgent.log for the details on this job. JobID='{JobID4}' Note Both 'App 2' and 'App 4' share the same content ID. In this example sequence, 'App 4' was not installed following the restart that 'App 3' triggered. Out of Band Management Power Control and Clear Audit Log collection-based actions fail for externally provisioned AMT clients. The amptopmgr.log file contains entries that resemble the following entry: Error: CSMSAMTDiscoveryTask::Execute, discovery to client_computer failed. General Worker Thread Pool: Error, Can not execute the task successfully. Remove it from task list. Site Database Replication Link Analyzer incorrectly detects a syscommittab system table issue and suggests reinitialization if the SQL Errorlog contains the following string: 3999 A primary device cannot be selected for user-based pre-deployment if the device does not have the Configuration Manager client installed. Site Systems A Reporting Services Point may not be installed or start if the SQL Reporting Service does not start within one minute. The srssp.log file may contain entries that resemble the following entry: Starting service 'ReportServer' Time out has expired and the operation has not been completed. The SMS Executive service may stop unexpectedly if the Exchange Connector PowerShell cmdlet fails. The EasDisc.log file may contain entries that resemble the following entry: ERROR: [MANAGED] Cmdlet failed: Starting a command on remote server failed with the following error message: The WinRM client cannot complete the operation within the time specified. Check if the machine name is valid and is reachable over the network and firewall exception for Windows Remote Management service is enabled. For more information, see the about_Remote_Troubleshooting Help topic. The Site System Status Summarizer component may cause the SMS Executive service to stop unexpectedly if the site server fully qualified domain name (FQDN) is more than 50 characters, and the default installation path is used. The relevant entries from the Exception Information section of the crash.log files contain the following entry: Thread name = SMS_SITE_SYSTEM_STATUS_SUMMARIZER Executable = C:\Program Files\Microsoft Configuration Manager\bin\x64\smsexec.exe Exception = eeeeffff (EXCEPTION_SMS_FATAL_ERROR) Known issues Update of the Administrator Console When the Administrator Console is first installed, a copy of the Adminconsole.msi file is cached in the %Temp% folder of the user who initiated the installation. If that MSI file is missing, the Configmgr2012adminui-rtm-kb2717295-i386.msp update file may not be applied. When this update is distributed by using Software Distribution, the installation may fail, and an exit code of 1603 is logged in the excecmgr.log file. To resolve this issue, reinstall the original release of the Administrator Console by using Consolesetup.exe, then apply this update. Back to the top | Give Feedback How to obtain Cumulative Update 1 for System Center 2012 Configuration Manager A supported hotfix is available from Microsoft. However, this hotfix is intended to correct only the problems that are described in this article. Apply this hotfix only to systems that are experiencing the problems described in this article. This hotfix might receive additional testing. Therefore, if you are not severely affected by this problem, we recommend that you wait for the next software update that contains this hotfix. If the hotfix is available for download, there is a "Hotfix download available" section at the top of this Knowledge Base article. If this section does not appear, contact Microsoft Customer Service and Support to obtain the hotfix. Note If additional issues occur or if any troubleshooting is required, you might have to create a separate service request. The usual support costs will apply to additional support questions and issues that do not qualify for this specific hotfix. For a complete list of Microsoft Customer Service and Support telephone numbers or to create a separate service request, visit the following Microsoft website: http://support.microsoft.com/contactus/?ws=supportNote The "Hotfix download available" form displays the languages for which the hotfix is available. If you do not see your language, it is because a hotfix is not available for that language. Back to the top | Give Feedback File information The English version of this hotfix has the file attributes (or later file attributes) that are listed in the following table. The dates and times for these files are listed in Coordinated Universal Time (UTC). When you view the file information, it is converted to local time. To find the difference between UTC and local time, use the Time Zone tab in the Date and Time item in Control Panel. Download it here
-
Data error (cyclic redundancy check). < run chkdsk on the drive you are trying to capture from, oh and please tell me you are not building an image on real hardware ? and then capturing it ? that will cause you problems and makes it harder to automate everything if at all possible, try to build and capture on virtual hardware and use a separate task sequence to deploy the captured image to multiple types of hardware
-
hi Julian zip up all the logs on that client in it's CCM\LOGS folder and attach them here, if you cannot attach them then use skydrive or dropbox.
-
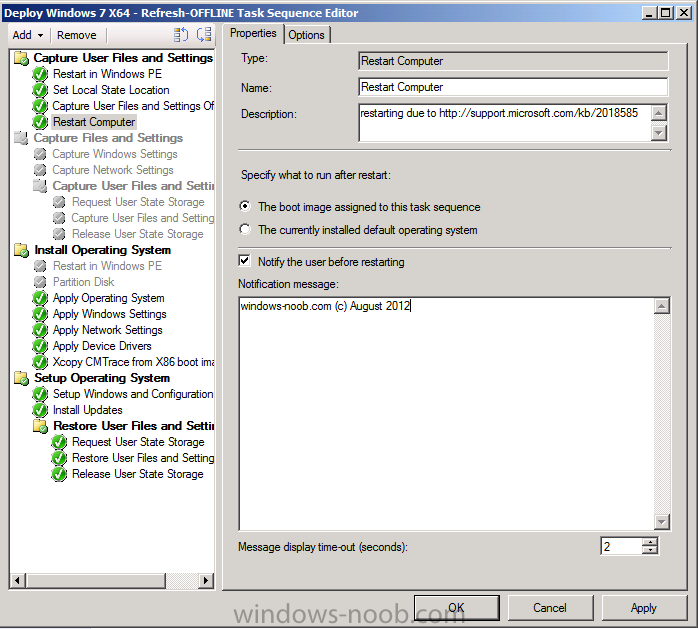
add a Restart Computer step after it has captured User state as in the screenshot below then you'll be ok, review the following to see why http://support.micro....com/kb/2018585
-
can you attach your unattend.xml please ? and both smsts*.log files
- 5 replies
-
- Language Packs
- Regional Settings
-
(and 1 more)
Tagged with:
-

using SCCM 2012 in a LAB - Part 6. Deploying Software Updates
anyweb replied to anyweb's topic in Configuration Manager 2012
use ADR (automatic deployment rules) to do your patch tuesday monthly updates. I'll do a new post on that sooner or later -
hi SpecialEd, the reason I've chosen to use custom ports is because it's a recommended best practice from Microsoft, see here as regards your original issue, do you have any of the logs you sent to Microsoft i'd be happy to look at them to figure out your problem