-
Posts
9251 -
Joined
-
Last visited
-
Days Won
369
Everything posted by anyweb
-
Introduction If you haven’t already noticed I’m currently blogging about a series of DEM in 20 webinars from 1E and I’ve linked each one that I’ve covered below for your perusal. In today’s blog post I’ll focus on how to deal with that Change Management Success Rate Struggle. That’s a mouthful, but in a nutshell what it means is how can you cope with the onslaught of issues raised both pre and post change for a change management request. Every company has to deal with change management, possibly even more so now with so many people still working from home. Not only will you learn how to deal with the change management success rate, but get real time data before and after the change. Episode 1. How to find and fix Slow Endpoints Episode 2. That crashy app Episode 3. Dealing with annoying admin requests Episode 4. That Change Management Success Rate Struggle Why is change control important ? Help Desk International (HDI) referenced that 80% of incidents are caused by internal change. That’s a huge percentage. “80% of incidents are caused by internal change” If we could just control that better and get an idea of what the output would be like before we roll it out into production then we’d have less incidents and more time to do the job we we’re hired to do. Change Control Requests Change control usually starts with a change control request form for the desired change, in this example it’s for a global Zoom upgrade. Zoom is telecommunication software for holding meetings, and it became hugely popular during the ongoing Covid pandemic due to so many workers having to work from home. As new features are added, or security patches released, new versions need to be pushed out, and that all starts with a change control request. In Robs’ line of business (Rob Key, Senior Solutions Engineer at 1E), and some of the customers he talks to, it’s common to see them using the following methods for change control, either by sending the change to IT so they can test it on one or more machines, and then after doing that test, sending out a survey to the users involved asking how did that affect your machine, but depending on that change, IT might not dig in as deep as we’d like or using an UAT (user acceptance testing) group to look at it. Capturing pre-change data Let’s take a different approach using Tachyon Experience. Not only can we do monitoring but we can check health and compliance policies on a group of test machines to make sure that we can see that those machines stay healthy both before and after the change is completed. For that we’d want to capture pre-change health and compliance information. In this particular example there are two control groups, manufacturing and marketing. These are two different parts of the organization and they have different needs, so they should be good target groups for the data that we need. In the screenshot below we can dig down and see that services are healthy and all of the numbers are looking good. Next we can verify the version (in real-time) of the target software we intend to change, and below we can see it’s not yet upgraded. We can also see the services running, or in the example below, that a Zoom sharing Service is both stopped and disabled. It was disabled as a policy was created to not allow that service to run in the manufacturing group, for security reasons, to stop the release of important and confidential information. For the marketing group another policy was created to allow it to run. Post-change rules to guarantee state Any area of a business that goes down due to change management processes that go wrong costs that business money, so to avoid that, policies are created in Tachyon in Guaranteed State. You can see two policies in the drop down menu below, one for marketing, and one for the manufacturing group. Here’s a closeup of those policies. These policies are created using one or more rules in Tachyon Guaranteed State. This is post-change, and here we can see a rule from our policy targeting the marketing department, pay attention to the Not Applicable slice. Clicking on that reveals the following, and here we can see that there is a check to ensure that the Zoom sharing service is enabled, however this new version of Zoom doesn’t use this as Zoom changed the way they structure their software. So how were these Guaranteed State policies created? Each rule can check for various things, such as checking for free disk space or whether or not the Zoom Sharing Service is enabled or that the 1E Client service is in a correct state. Below you can see a list of some of those rules. If we take a closer look at a rule, in this case a rule to Ensure the DNS service is in a correct state, you can see from the screenshot below that the rule looks at optional Pre-conditions, Triggers, the Check itself and an optional Fix. What about non-compliance post-change ? Seeing real-time results that reveal non-compliance post-change is a great ability. That can be revealed by our Guaranteed State policies. To test this, killing a service which is checked for (one of the rules above) reveals this in real-time. Below a service is stopped… and reviewing the rules results, you can straight away see that there is non-compliance and drill down to find out more information. This is instantaneous, which means you can see how to control the change management process with ease by gathering data and responding effectively. “So how quick is quick ?” This really depends on what you are looking at, for example disk space might be polled every minute or 30 seconds. But when you are talking about registry changes or config file changes or services, that is real-time. Conclusion Change happens all the time in business and while most companies have their own change management processes to deal with that change, they are very likely contributing to their own workloads by the way they do it. Remember, internal changes that are not correctly monitored pre and post change can cause major problems. Using Tachyon Experience and Tachyon Guaranteed State gives your admins the power to see those results in real-time and allows them to easily tweak the change management process to increase their success rate. DISCLAIMER: The contents of this article are the opinion of the author and have been written from an impartial standpoint; however, 1E may have reimbursed the author for time and expenses for undertaking the findings and conclusions detailed in the article.
-

CMG boundaries and Fallback
anyweb replied to Tommy75's topic in System Center Configuration Manager (Current Branch)
over time it will switch MP, now whether it'll do that during the task sequence I don't know, you want to save time so.. my point with the variable, is why not set the variable after the reboot to the CMG MP, have you tried that ? -

CMG boundaries and Fallback
anyweb replied to Tommy75's topic in System Center Configuration Manager (Current Branch)
you should be able to see from the client based logs which MP it's currently attached to and when it switches... -

CMG boundaries and Fallback
anyweb replied to Tommy75's topic in System Center Configuration Manager (Current Branch)
interesting problem, are you setting this variable to true as a matter of interest ? SMSTSDisableStatusRetry In disconnected scenarios, the task sequence engine repeatedly tries to send status messages to the management point. This behavior in this scenario causes delays in task sequence processing. Set this variable to true and the task sequence engine doesn't attempt to send status messages after the first message fails to send. This first attempt includes multiple retries. When the task sequence restarts, the value of this variable persists. However, the task sequence tries sending an initial status message. This first attempt includes multiple retries. If successful, the task sequence continues sending status regardless of the value of this variable. If status fails to send, the task sequence uses the value of this variable. and have you tried setting this variable after the reboot ? SMSTSMP Use this variable to specify the URL or IP address of the Configuration Manager management point. https://docs.microsoft.com/en-us/mem/configmgr/osd/understand/task-sequence-variables -
recovery partitions are needed by the OS to recover the os in case of boot failure, you do need them, chances are your disk 0 is the system, boot disk and disk 1 is data or something else you need to make disk 1 your system disk and then you'll be able to remove the partitions on disk 0.... like so... diskpart sel disk 0 clean exit then recreate whatever partition you want on it in
-
are you absolutely sure you've configured it as we've explained ? to find out if the firewall is causing you issues, as a test, temporarily disable it, try adding the CMG connection point role again, any difference ? don't forget to re-enable the firewall after the test. If there's no change, then it's not your firewall or blocked ports but more than likely a mis-configuration or certifcate issue
-
It’s that time of the year again: SysAdmin Day has arrived, and with it comes infinite gratitude for the men and women who support us 24/7. For all the times you’ve prevented catastrophes and saved our skins, for all the long hours and patience, Hornetsecurity want to say thank you! If you’re a Microsoft 365 administrator, celebrate with them. All you have to do is sign up for free to 365 Threat Monitor and set up your account! How does it work? - Sign up to 365 Threat Monitor - Receive a guaranteed $20 Amazon voucher and a chance to win one of the Grand Prizes! What are you waiting for? Get your free 365 Threat Monitor App & Win!
-
remote sql is not recommended, but if you are using it, see here https://docs.microsoft.com/en-us/mem/configmgr/core/plan-design/network/pki-certificate-requirements Site system servers that run Microsoft SQL Server This certificate is used for server-to-server authentication. Certificate requirements: Certificate purpose: Server authentication Microsoft certificate template: Web Server The Enhanced Key Usage value must contain Server Authentication (1.3.6.1.5.5.7.3.1) The Subject Name must contain the intranet fully qualified domain name (FQDN) Maximum supported key length is 2,048 bits. This certificate must be in the Personal store in the Computer certificate store. Configuration Manager automatically copies it to the Trusted People Store for servers in the Configuration Manager hierarchy that might have to establish trust with the server.
-
the only way I've found is to script around it on the client and get that script onto your autopilot images somehow..., or get your proxy guys to add a transparent proxy for it, or use Wi-fi connections that bypass the proxy, there probably are some other abilities but for now that's what we have
-

Secondary Site Clients Site Code
anyweb replied to gokhan76's topic in System Center Configuration Manager (Current Branch)
you mentioned subnets, and that's not advisable, have a read of Jason's old blog post here to get some ideas https://home.memftw.com/ip-subnet-boundaries-are-evil/ -
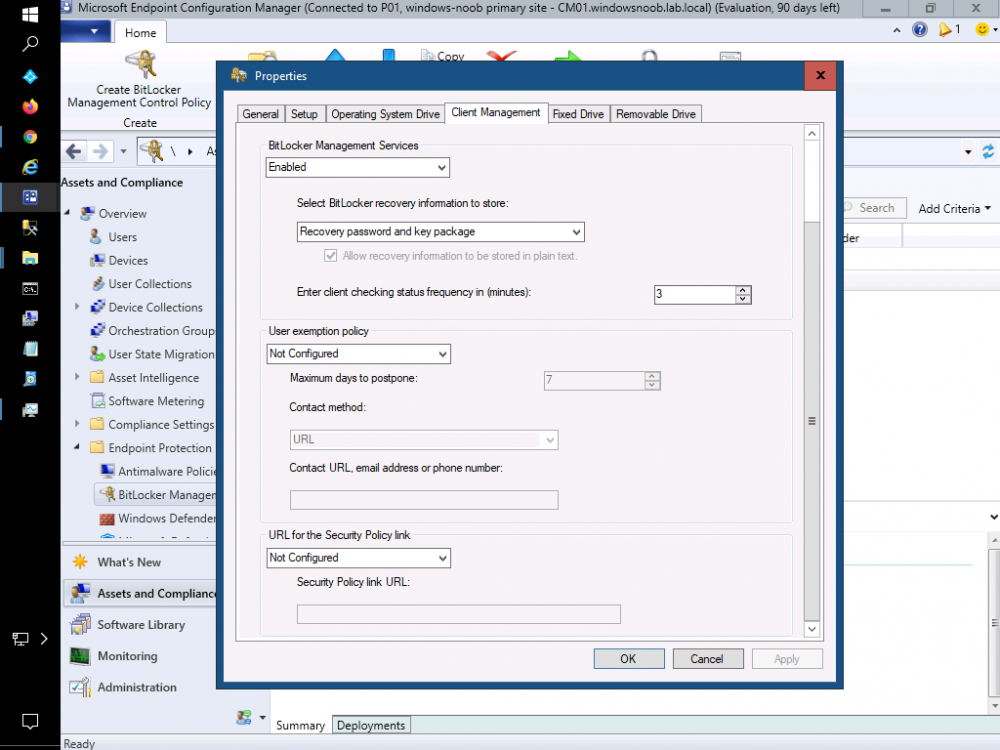
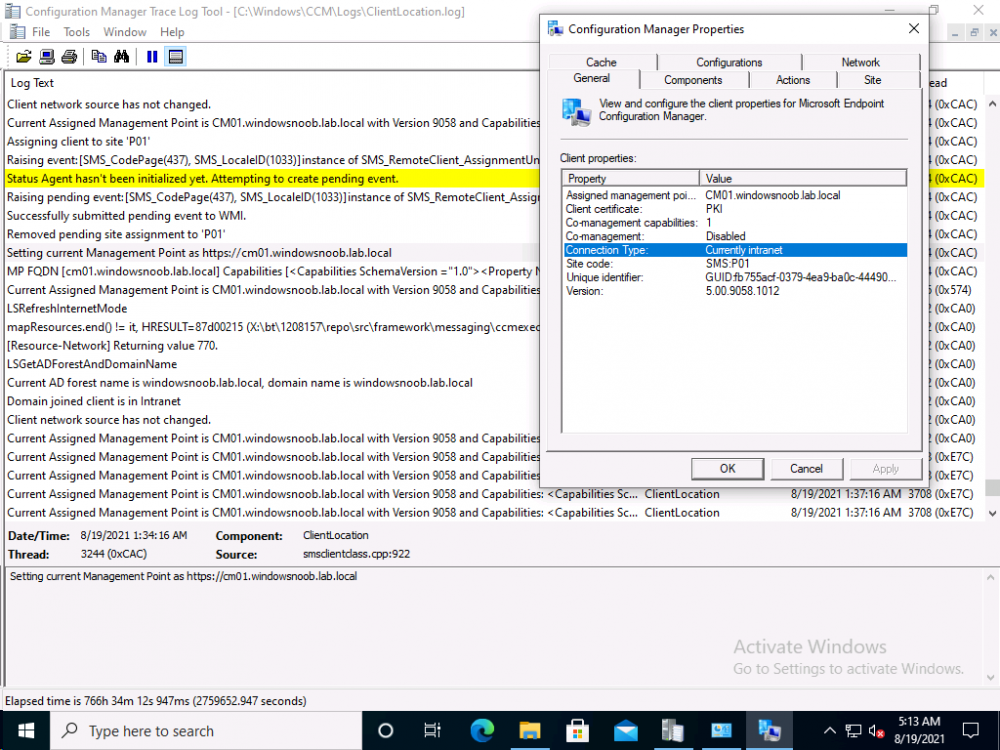
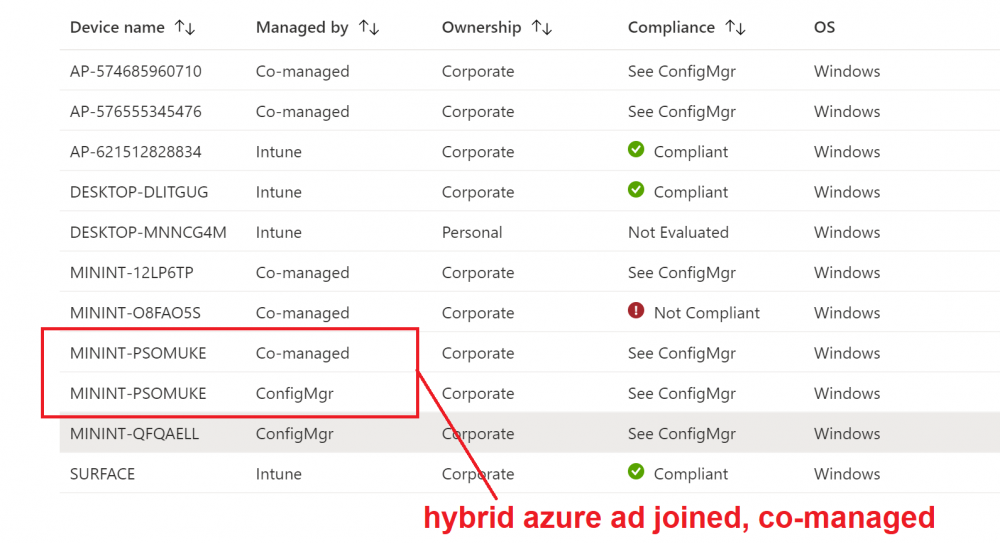
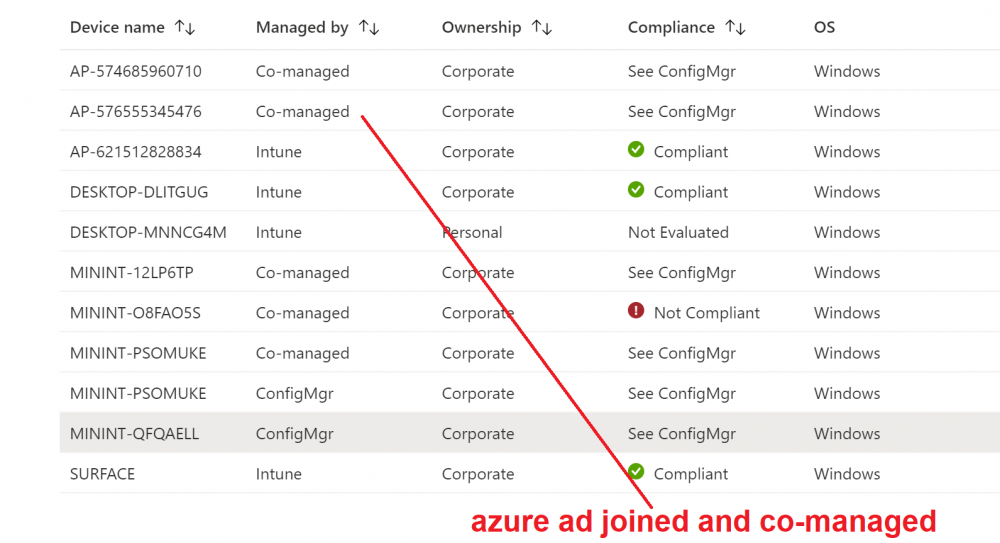
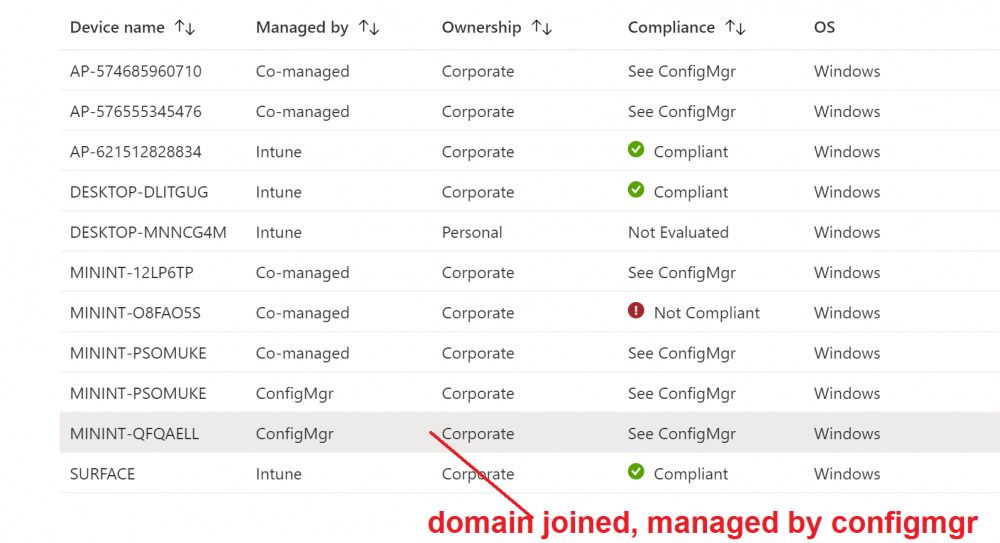
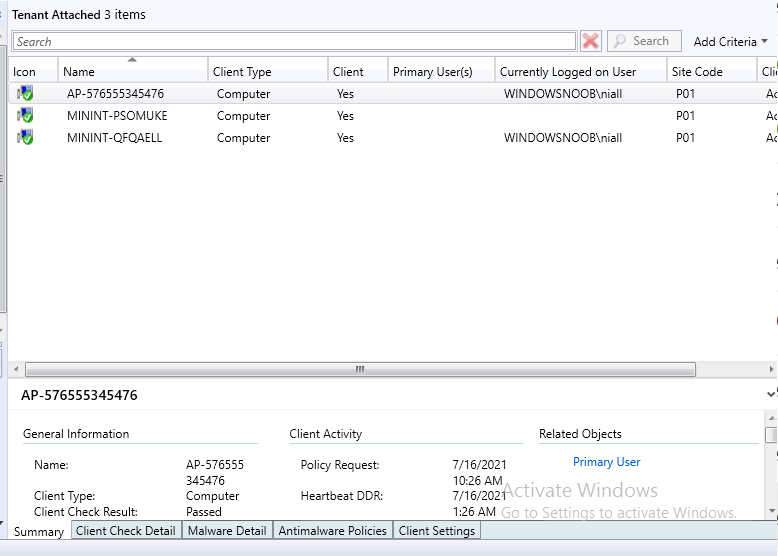
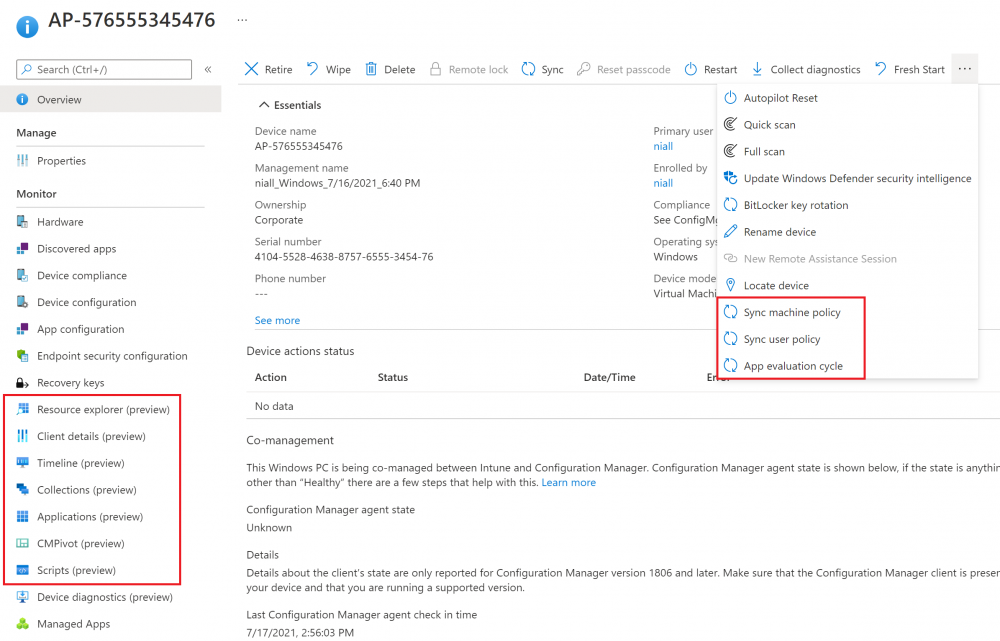
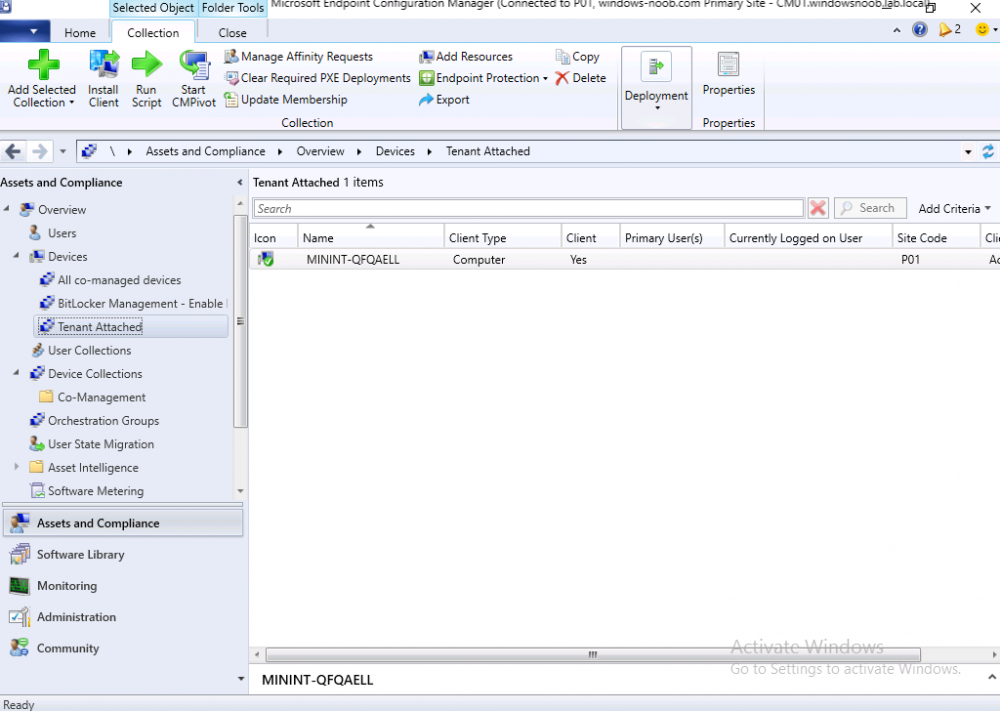
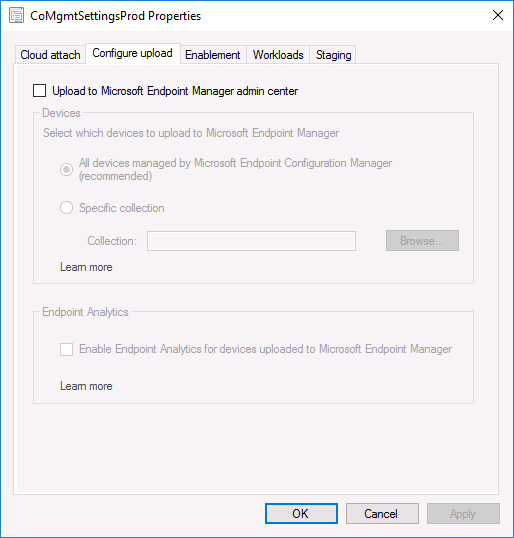
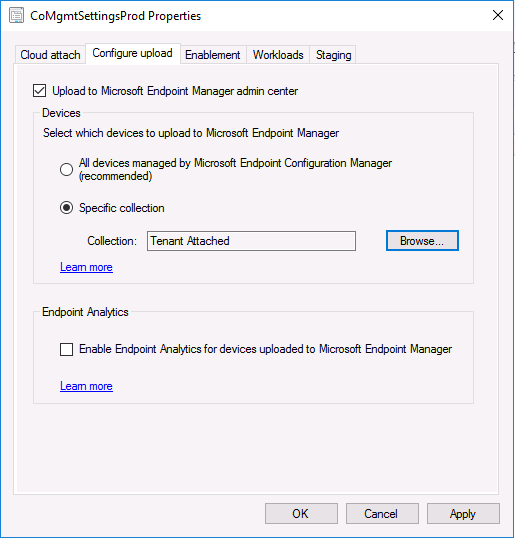
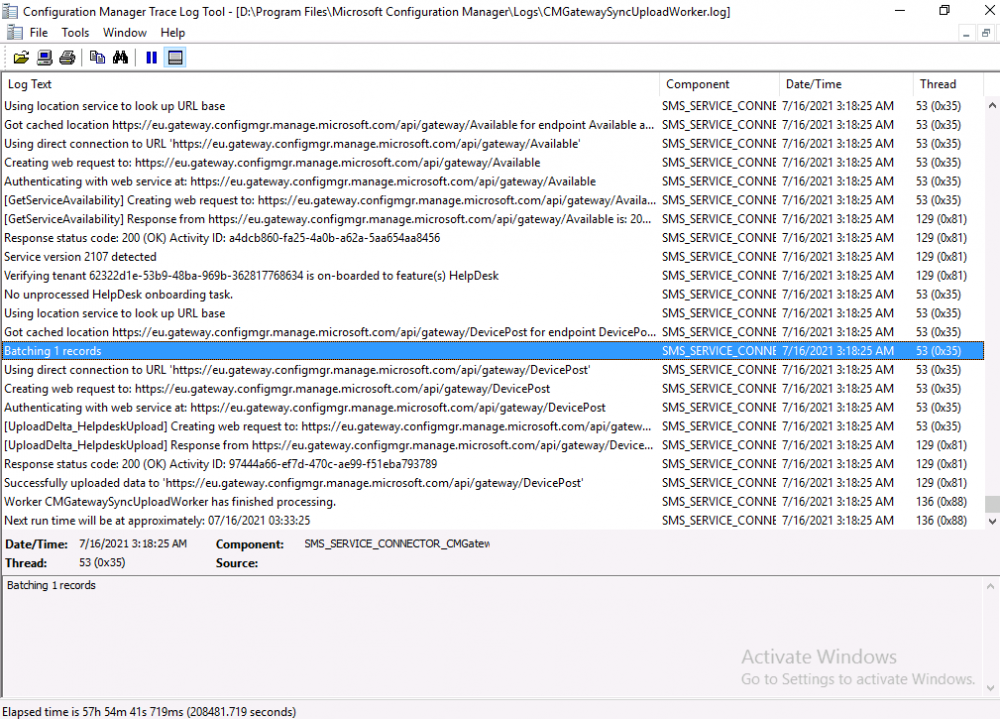
Introduction This is part 8 in a series of guides about cloud attach in Microsoft Endpoint Manager, with the aim of getting you up and running with all things cloud attach. This part will focus on enabling tenant attach. This series is co-written by Niall & Paul, both of whom are Enterprise Mobility MVP’s with broad experience in the area of modern management. Paul is 5 times Enterprise Mobility MVP based in the UK and Niall is 11 times Enterprise Mobility MVP based in Sweden. In part 1 we configured Azure AD connect to sync accounts from the on premise infrastructure to the cloud. In part 2, we prepared Azure resources for the Cloud Management Gateway, in part 3 we created the cloud management gateway and verified that everything was running smoothly. In part 4 we enabled co-management. With co-management, you retain your existing processes for using Configuration Manager to manage PCs in your organization and you gain the additional advantage of being able to transfer workloads to the cloud via Endpoint Manager (Intune). In part 5 we enabled the compliance policies workload and reviewed how that affected a co-managed computer. In this part we will enable conditional access and see how that can be used to deny access to company resources. In part 6 we configured conditional access and used it to deny access to company resources unless the device was encrypted with BitLocker. In part 7 we showed you how to co-manage Azure AD devices. In this part we'll enable Tenant Attach and take a brief look at it's features. Below you can find all parts in this series. Cloud attach - Endpoint Managers silver lining - part 1 Configuring Azure AD connect Cloud attach - Endpoint Managers silver lining - part 2 Prepare for a Cloud Management Gateway Cloud attach - Endpoint Managers silver lining - part 3 Creating a Cloud Management Gateway Cloud attach - Endpoint Managers silver lining - part 4 Enabling co-management Cloud attach - Endpoint Managers silver lining - part 5 Enabling compliance policies workload Cloud attach - Endpoint Managers silver lining - part 6 Enabling conditional access Cloud attach - Endpoint Managers silver lining - part 7 Co-managing Azure AD devices Cloud attach - Endpoint Managers silver lining - part 8 Enabling tenant attach <- you are here Cloud attach - Endpoint Managers silver lining - part 9 Renewing expiring certificates Cloud attach - Endpoint Managers silver lining - part 10 Using apps with tenant attach Tenant attach first showed up in Technical Preview 2002.2, but was released in ConfigMgr 2002 which you can read about here. You can think of tenant attach as being a way to give your Endpoint Manager admins access to ConfigMgr actions/data via the MEM console (login to your tenant at https://aka.ms/memac) without needing to do it via the ConfigMgr console. The prerequisites The user account needs to be a synced user object in Azure AD (hybrid identity). This means that the user is synced to Azure Active Directory from Active Directory. For Configuration Manager version 2103, and later: Has been discovered with either Azure Active Directory user discovery or Active Directory user discovery. For Configuration Manager version 2010, and earlier: Has been discovered with both Azure Active Directory user discovery and Active Directory user discovery. The Initiate Configuration Manager action permission under Remote tasks in the Microsoft Endpoint Manager admin center. For more information about adding or verifying permissions in the admin center, see Role-based access control (RBAC) with Microsoft Intune. Note: In case it’s not clear above, you need to configure Azure AD Connect to sync your on-premise users to the cloud for the user actions to succeed. You also need to go through the Azure services in ConfigMgr and configure cloud management to sync Azure Active Directory User Discovery. During this blog post we used a user that satisfies the above, namely niall@azurenoob.com to perform the tenant attach related actions in MEM. Step 1. Create a collection This is an optional step, but helps you to keep track of which devices are Tenant Attached. Create a collection called Tenant Attached, you will use that collection to populate your tenant attached devices. Once created, place one or more devices into the collection. Step 2. Enable tenant attach In the ConfigMgr console, select the Administration node and expand cloud services, select Co-management (2103 or earlier) or based on what we saw in the recent technical preview (Technical Preview 2106) select Cloud Attach (2107 or later). Select CoMgmgtSettingsProd, right click and bring up the properties. In Co-management properties, click on the Configure upload tab. Next, place a check in the Upload to Microsoft Endpoint Manager admin center checkbox, and select a collection, for example use the Tenant Attached collection we created in step 1, Note: If you select All devices managed by Microsoft Endpoint Configuration Manager then all devices (including servers) will show up in the MEM console. Next, deselect the Enable Endpoint Analytics for devices upload to Microsoft Endpoint Manager. And finally click Apply. When prompted to authenticate to Azure services, enter the credentials of your Global Admin account for the applicable tenant. After correctly entering your credentials, the changes will be applied and you can review the success or failure of your actions via the CMGatewaySyncUploadWorker.log Step 3. Verify upload of data After a device is added to the target collection, you can look at the CMGatewaySyncUploadWorker.log to verify that it uploads data for the number of records you added. So if for example you add one computer to the Tenant Attached collection, then it'll state "Batching 1 records" as shown below. This will only happen when it detects a new device, in the next upload (15 minutes later) it'll return to Batching 0 records and so on unless of course new devices are detected in the collection. This upload of data occurs every 15 minutes. In the below screenshots, all highlighted devices are tenant attached and are in the Tenant Attached collection. Next, login to your tenant at https://aka.ms/memac this will display your devices. After the data is uploaded from ConfigMgr, check devices in Microsoft Endpoint Manager and depending on the type of device you'll see one or more devices matching that device name. In the first example, we have a device that is shown with two records, one is listed as co-managed and the other record as ConfigMgr. That record is tenant attached. The Managed by column will denote how the device is managed and tenant attached co-managed devices (hybrid azure ad joined) may have a second record where it states managed by ConfigMgr. We saw this repeatedly with this specific client, even after clean installing Windows 10 on it...the client version in this particular case was CM2103. If it's an Azure AD joined device that is also co-managed (as we described in Part 7) then the managed by column will state Co-managed and yet this device will have only one record. Lastly if the device is merely managed by ConfigMgr (not co-managed, not azure ad joined) then it will show up with one record. Step 4. Looking into tenant attach features Now that we can identify the different types of devices that are tenant attached, let's take a look at the power of tenant attach. If we look at the Azure AD joined, co-managed device which we deployed in part 7, we can see that the following additional capabilities are now available by enabling tenant attach and adding this computer to that collection so that the device becomes tenant attached. The following are available (in preview): Resource explorer Client details Timeline Collections Applications CMPivot Scripts in addition, you can now trigger the following actions Sync machine policy Sync user policy App evaluation cycle In the MEM console, the tenant attach abilities are highlighted below in red. Below you can see the Timeline feature and some of the data it can provide. To grab more data, click the Sync button and then refresh the screen. And here's a quick look at CMPivot Resource explorer is chock full of data Conclusion Using Tenant attach gives your admins more power to do ConfigMgr actions via the MEM console without needing to even install the ConfigMgr console.
-
- memcm
- endpoint manager
-
(and 1 more)
Tagged with:
-

Secondary Site Clients Site Code
anyweb replied to gokhan76's topic in System Center Configuration Manager (Current Branch)
1. that's normal see https://docs.microsoft.com/en-us/mem/configmgr/core/clients/deploy/assign-clients-to-a-site 2. I wouldn't setup boundaries using subnet, that's probably going to cause you issues, use IP ranges instead for your boundary definitions. Clients should download content from the distribution point closest to them (based on boundaries) or from fallback dp's if you have configured that. -
what have you tried and did it fail ? why not raise your own topic and explain what you've tried and what you want to achieve...
-
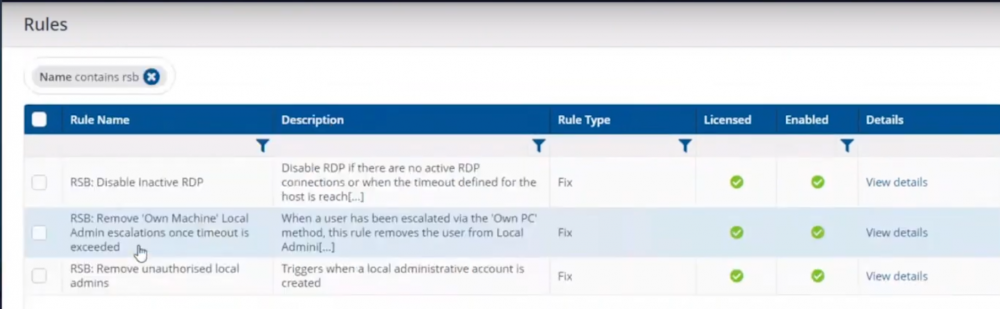
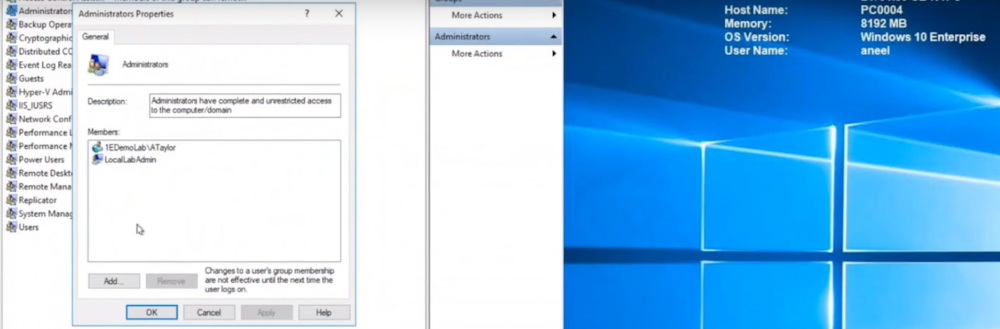
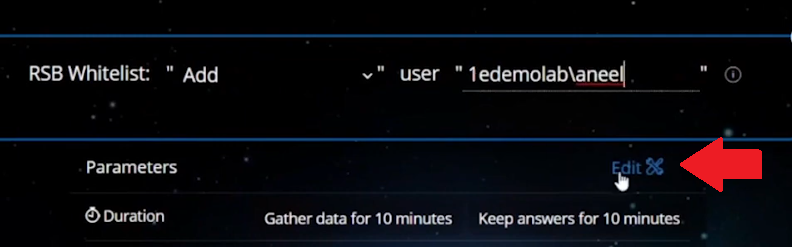
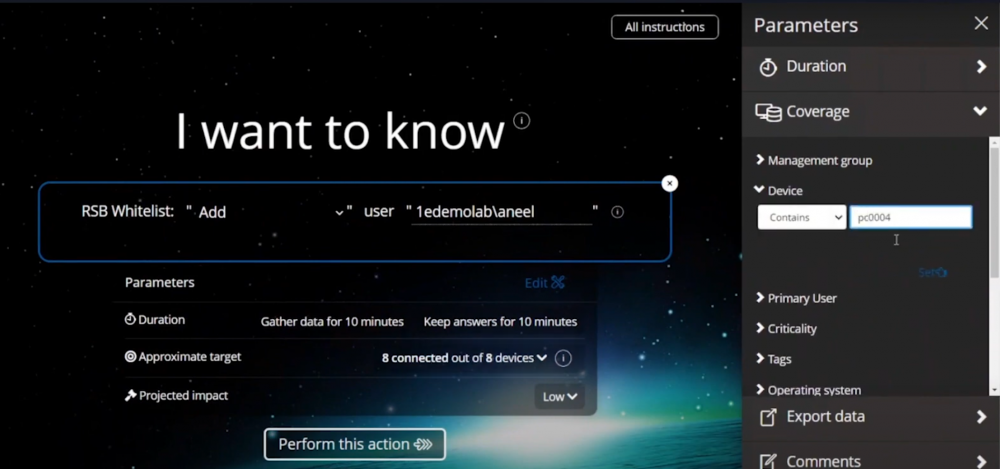
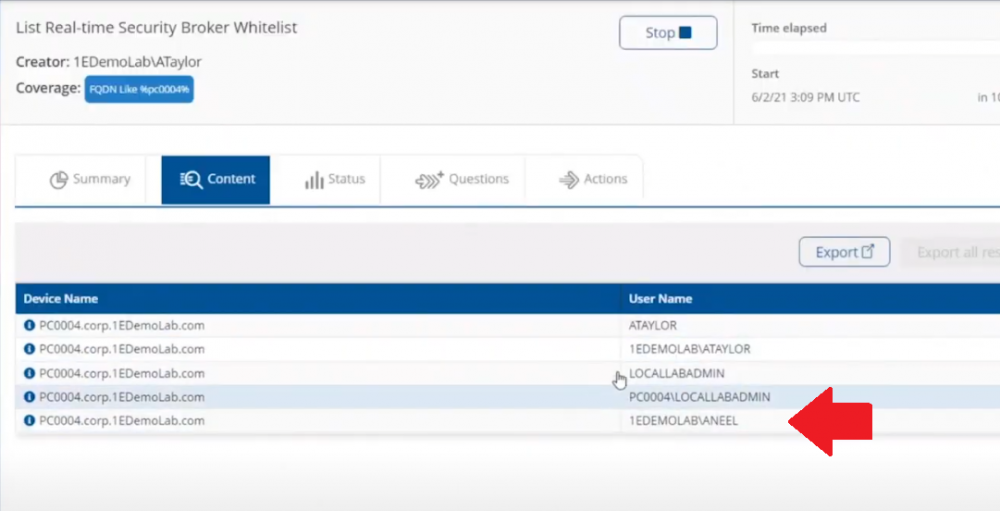
Introduction In a previous blog post I explained how to sign up for a webinar series and by doing so, learn from industry experts and Microsoft MVP’s about how and why they use tools like Tachyon from 1E to make things work better for your users, including how to deal with slow endpoints, or how to deal with apps that crash or for todays blog post, how to deal with those annoying admin requests. I will blog about each episode in the webinar series and link them here for your perusal. Episode 1. How to find and fix Slow Endpoints Episode 2. That crashy app Episode 3. Dealing with annoying admin requests Security. Love it or hate it, without it we’d all be in a worse situation. However security mandates as a best practice that the user logged on to Windows should be a standard user and not a local administrator. Why ? because that helps thwart the spread of damage to the operating system from running files that could overwrite operating system kernel files for example, or simply to keep root kits or viruses in check. Bad software can do bad things especially if you are a local administrator. That said, most users will need to be able to install legitimate software or configure things that require local administrator permissions on their computer, so how can we deal with that in a seamless, automated way with Tachyon. “Maybe you need an application for a demo, in 30 minutes.” Software Installation Requests are the probably the most common reason why people request admin elevation. Here are some ways that people typically deal with local admin rights requests. Group Policy – It’s a bit of a legacy dinosaur. Not that granular. The downside is knowing did it apply to the right group, did you clean it up after wards. Local Admin Password solution – LAPS, giving out a password for the local admin account and risks associated with it, able to add others to the local admin group, security team not so happy about that. How does Tachyon deal with this problem ? Tachyon deals with this seamlessly and fast, but it doesn’t sacrifice security to enable this ability. It’s part of the Guaranteed state module, specifically the real time security broker (RSB) shown below. This is made up of three rules listed here. RSB: Disable Inactive RDP RSB: Remove ‘Own Machine’ Local Admin escalations once timeout is exceeded. RSB: Remove unauthorised local admins. Here’s an example of it how Tachyon deals with this from start to finish. This is broken down into a couple of actions which are security focused, in that the user must be whitelisted in order to be allowed local administrative privileges. Whitelisting an account/Verifying whitelisted account Adding that whitelisted account to the local admins group Whitelisting an account Below we can see a user (aneel) is logged on to PC0004 and we can clearly see that the user is not a member of the Local Admins group on that PC. In the Tachyon Explorer console, you can search for RSB and then select RSB Whitelist: <Action> user <UserName> to add (or remove) a user. Next, click on Edit (shown below with the red arrow) to add Parameters to your action. In the parameters section on the right side of the console, select the device name that you want that user to have local admin permissions on. Adding a user to local admin on PC0004 in Tachyon After clicking Perform this action the request is then validated and any alternative accounts needed to approve the request will be informed to approve it. After the instruction was approved you can see that the user has been whitelisted and all of this is in real time. Verifying whitelisted account To verify that the whitelist request has succeeded you can use the List Real-time Security Broker Whitelist action in Tachyon Explorer. and in an instant you can see that the user has been added to the whitelist. Adding the user to the Local Admins group Next, you actually add the user (aneel) to the Local Admins Group. In Tachyon Explorer use the RSB Command: Add user <UserName> to the Local Administrators group, ONLY ON HOST: <hostname>. After performing the action you can see that the user is added to the Local Admins group. The entire process took less than a minute to whitelist and then add the user to the local admins group including the secondary approvals. You can also set the amount of time needed, for example give the user 30 minutes of Local Admin time. What about Self service for the end user ? If you want to allow your users to do this on their own, to elevate on demand using self-service, it’s possible as long as they’ve been given the correct permissions/ability. We can deploy an app called “Escalate to local admin” via Tacyhon to a small subset of users whom we trust to use appropriately. Below we can see another user (Ataylor) is logged on to PC0005 and this user is not a member of the Local admins group. This user launches the “Escalate to local admin” app so that they can self-service (with 2FA) the action themselves. and after clicking Go and satisfying the security prompts, the user is now added to the local admins group. Users behaving badly What about users adding other accounts without permission, below we can see a user that was granted local admin permissions has decided to add another user (sneakyadmin) to the local admins group. But no sooner than they click Apply, they are informed that the unauthorized action was denied. This is because the user added was not authorized via the Tachyon platform, and was instantly denied, not only that but the action has been logged and undone. going back into the Local Admins group you can see that the sneakyadmin account is not listed any more. Reporting on actions If you look in the Guaranteed State rules which drive this you can see that the action has been remediated, this is revealed under Report, Remediations. Conclusion Using Tachyon to provide admin credentials using security focused methods is easy and painless, yet retains useful features such as auditing, whitelisting and the ability to deny unapproved users. That’s it for this blog post, I hope to see you in the next one. In the meantime, I’d suggest that you sign up for the next DEM webinar, it’s free, tell them Niall sent you . And for those of you who want to see previously published episodes on youtube please click here. DISCLAIMER: The contents of this article are the opinion of the author and have been written from an impartial standpoint; however, 1E may have reimbursed the author for time and expenses for undertaking the findings and conclusions detailed in the article.