-
Posts
9182 -
Joined
-
Last visited
-
Days Won
366
Everything posted by anyweb
-
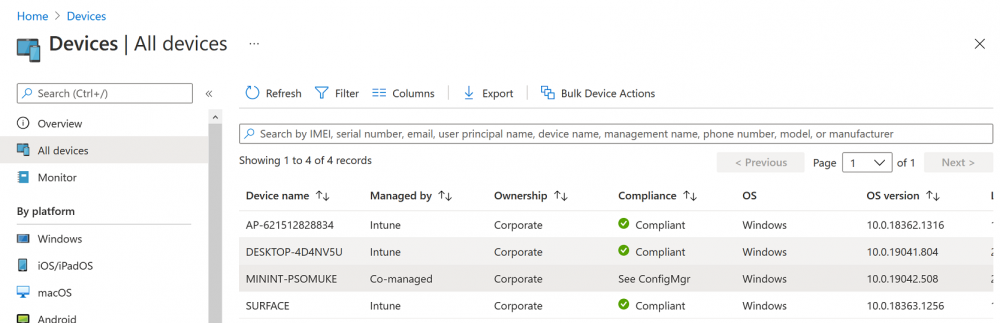
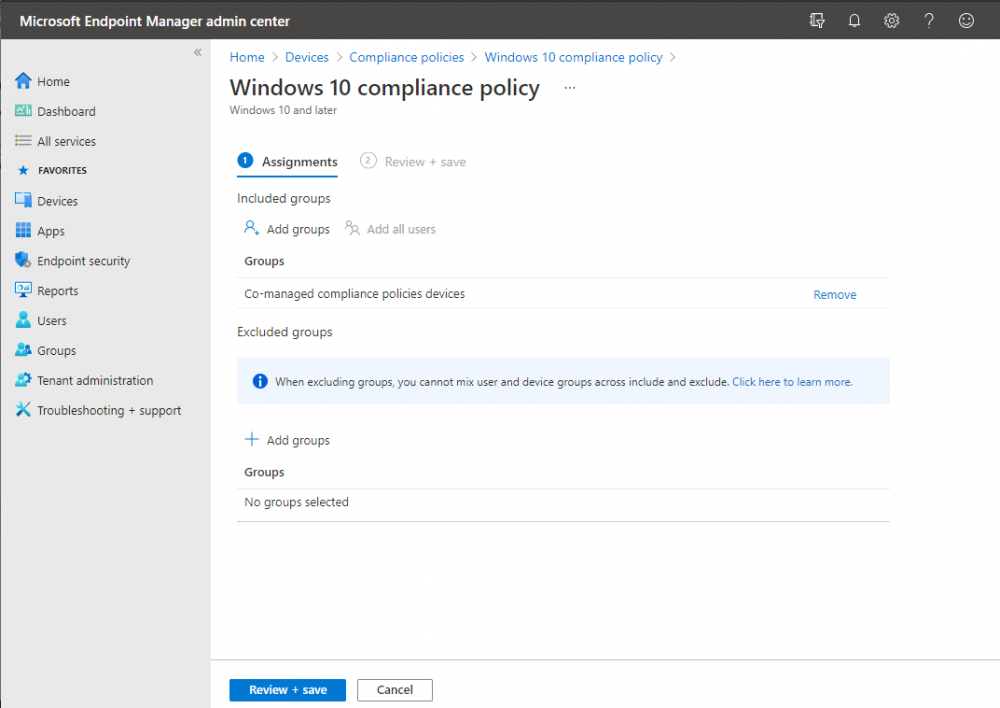
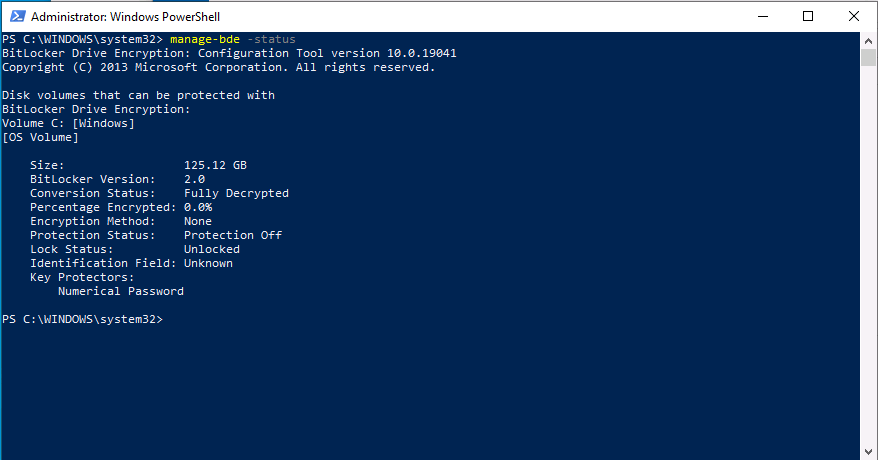
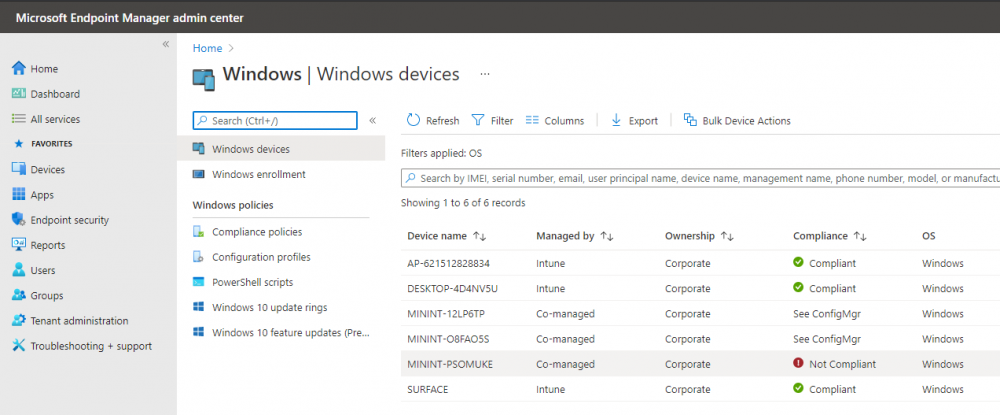
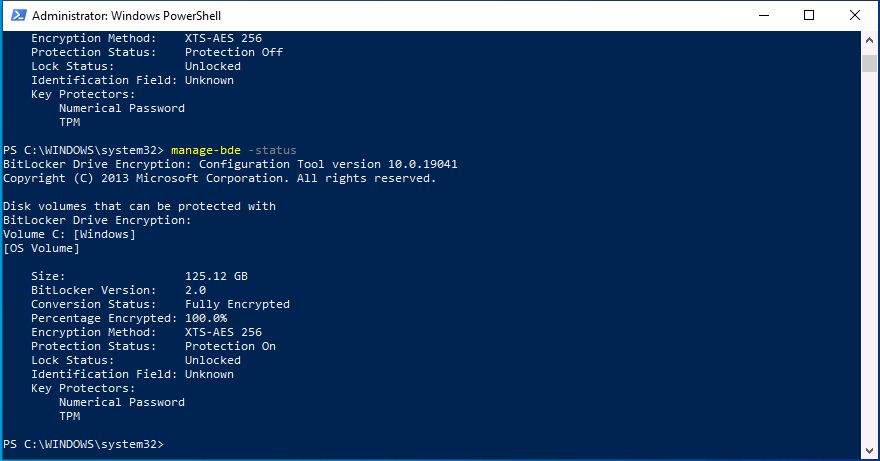
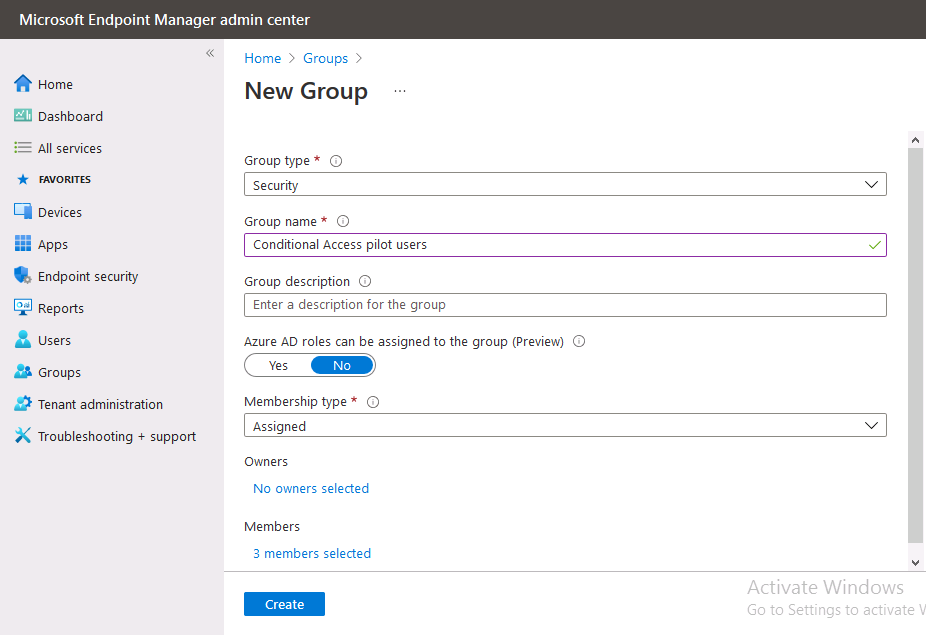
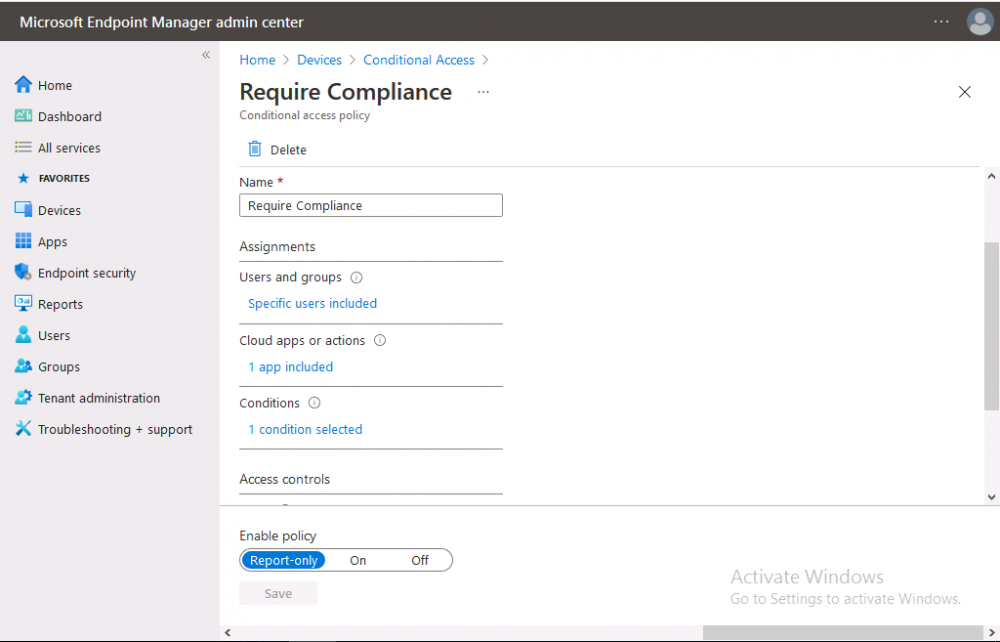
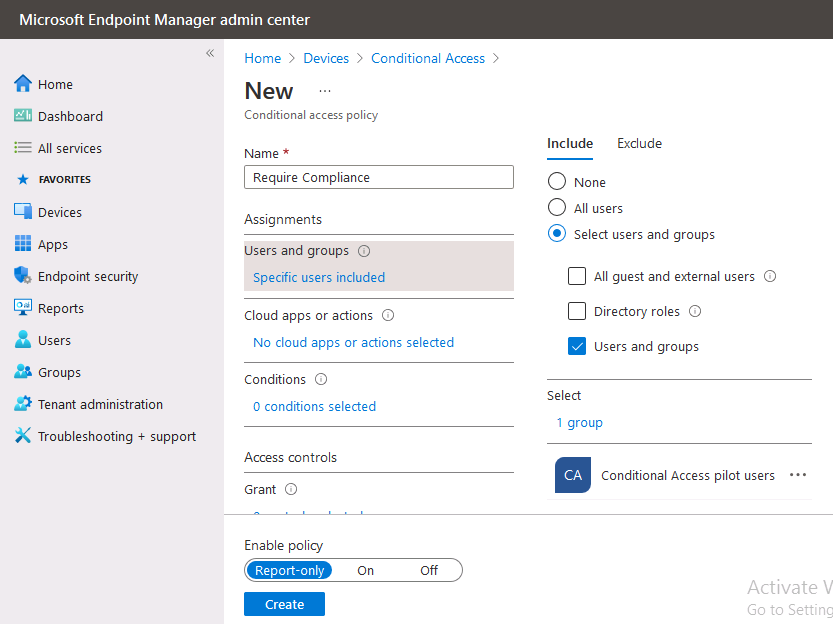
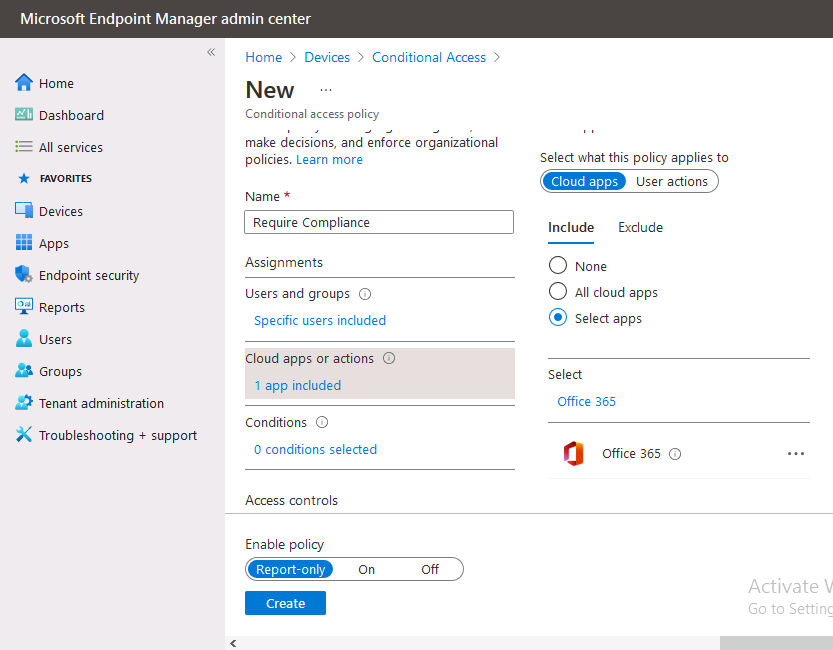
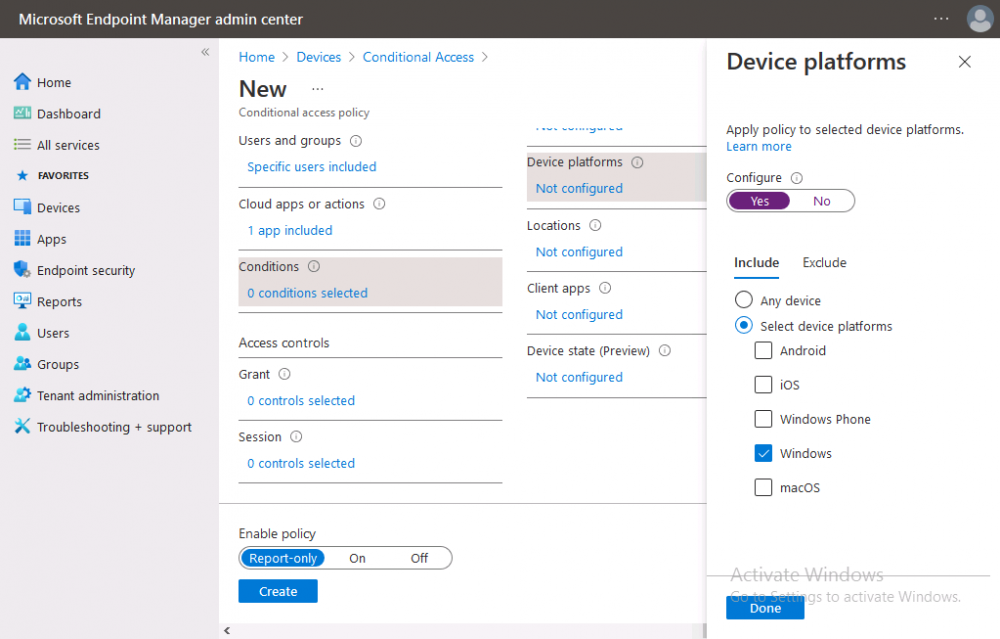
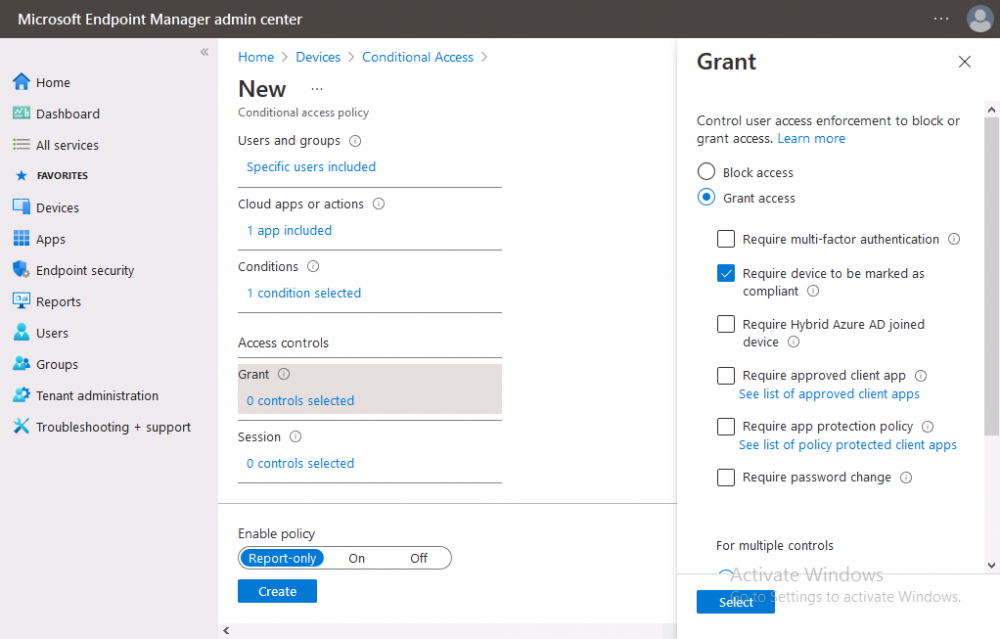
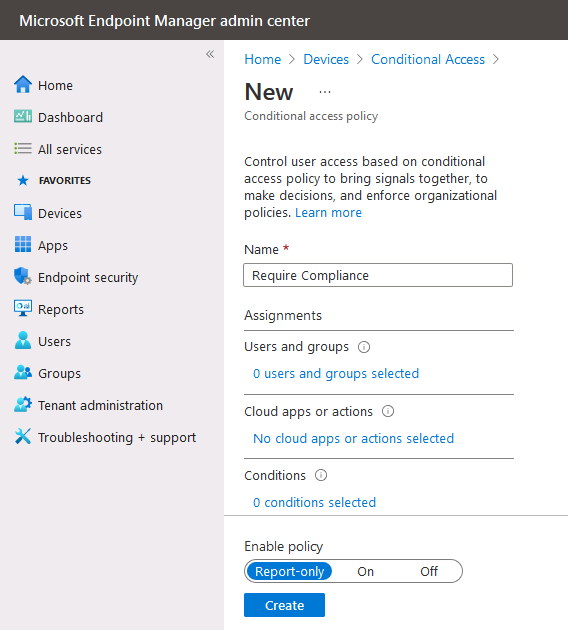
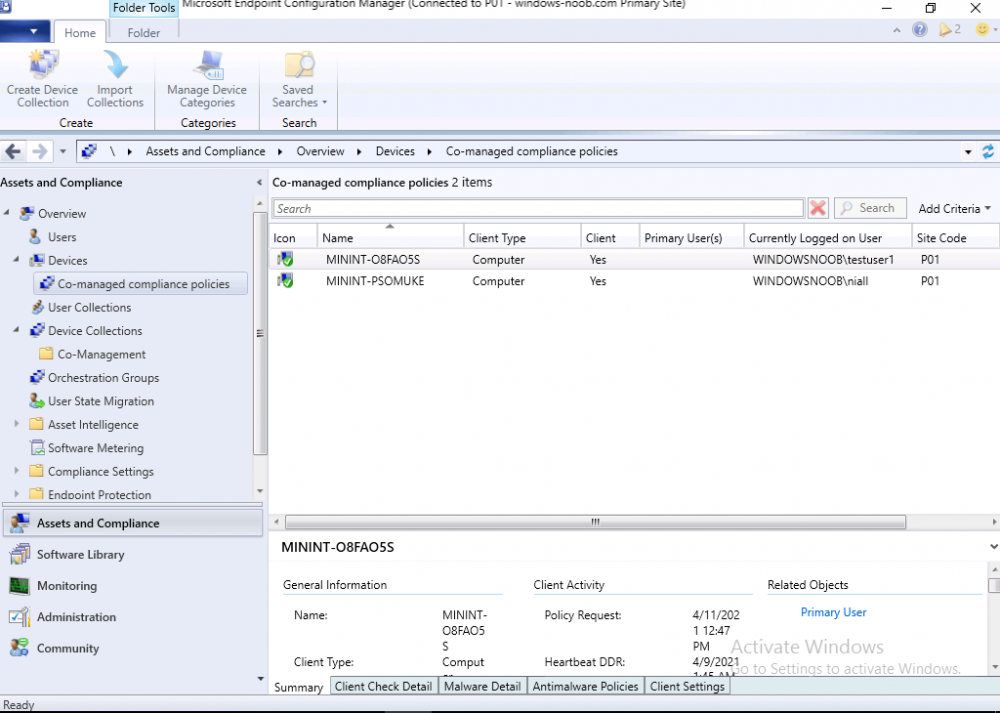
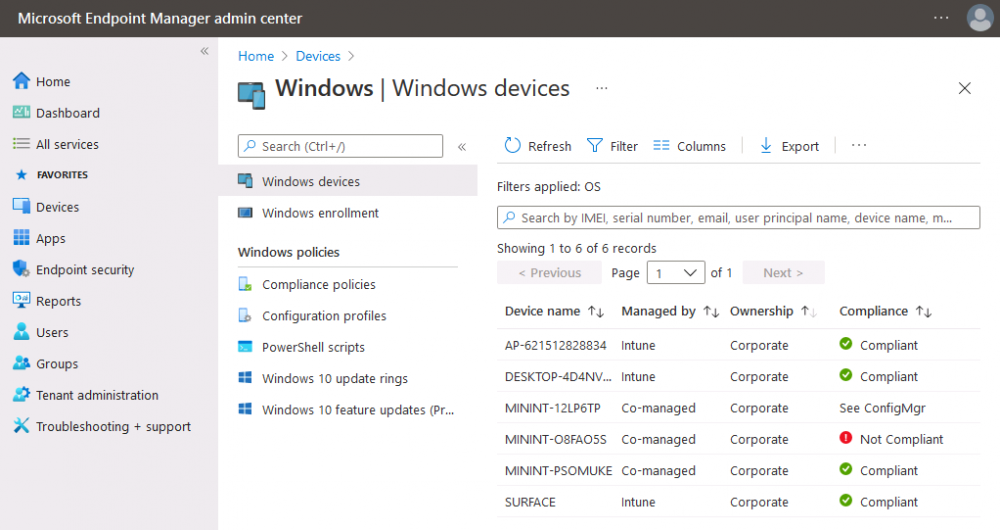
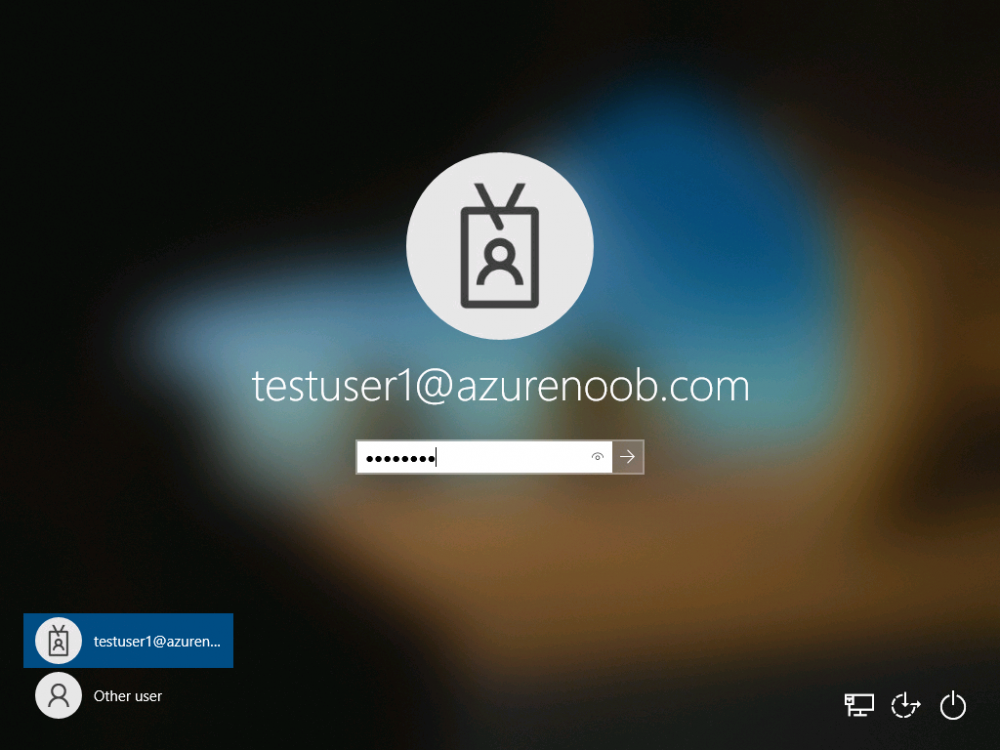
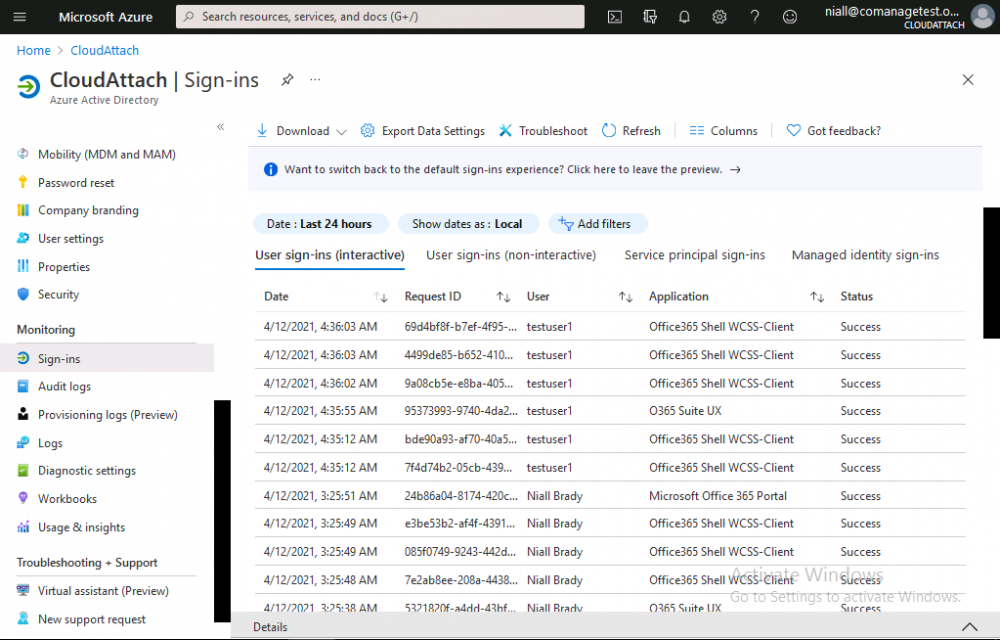
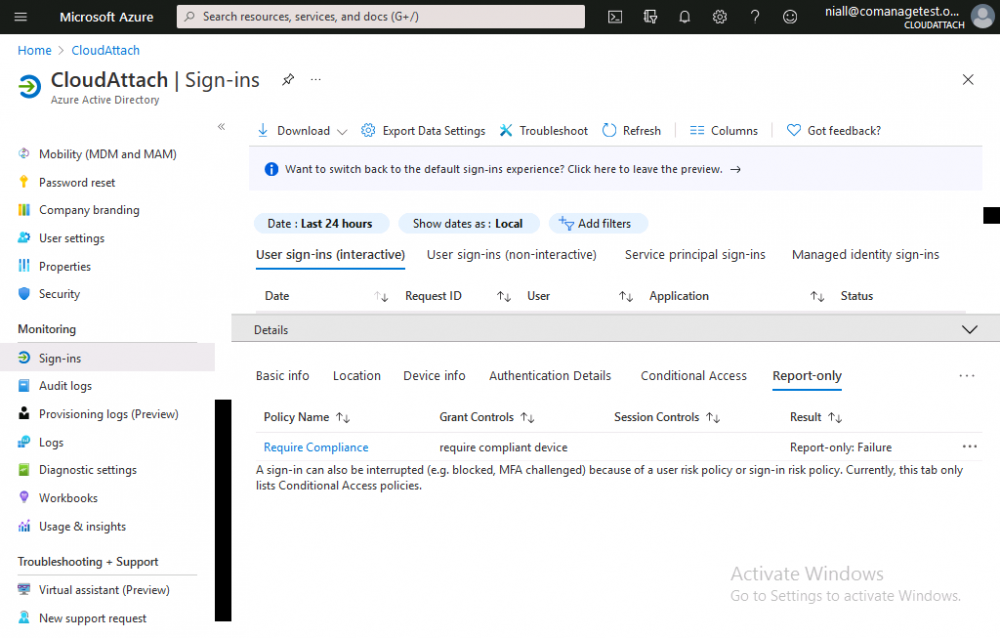
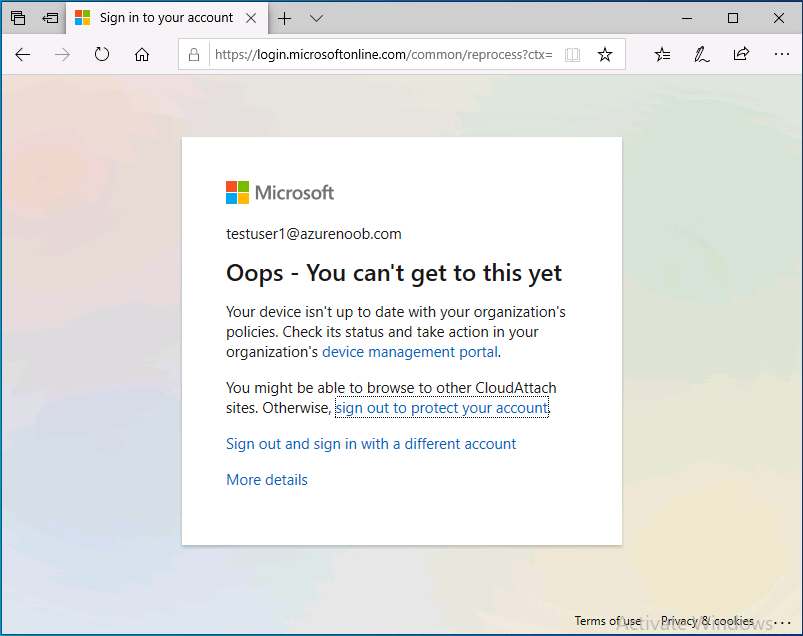
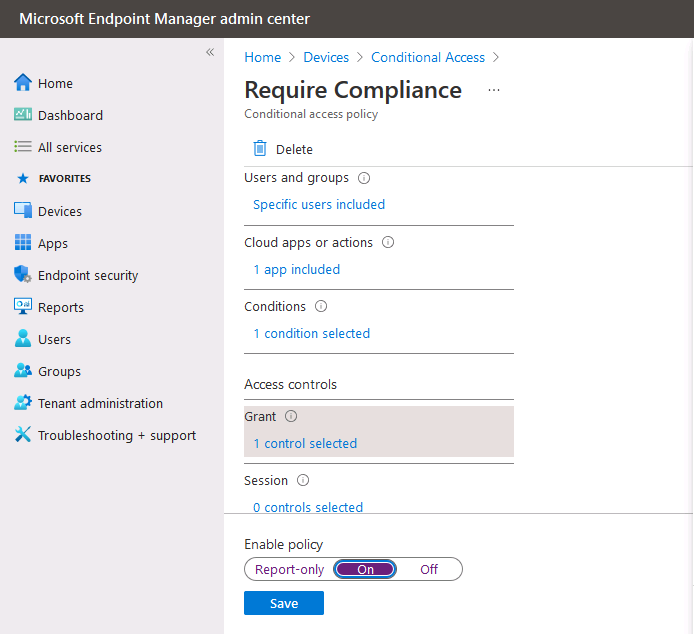
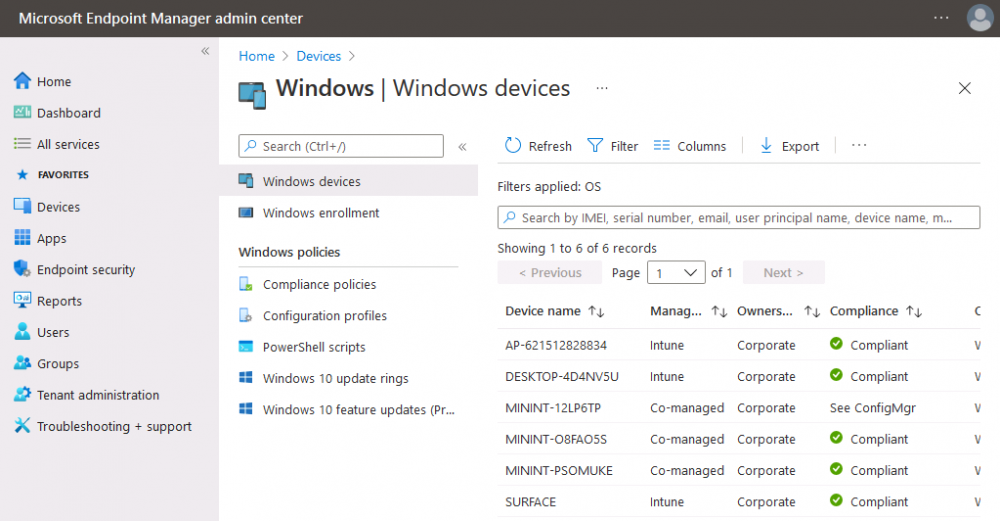
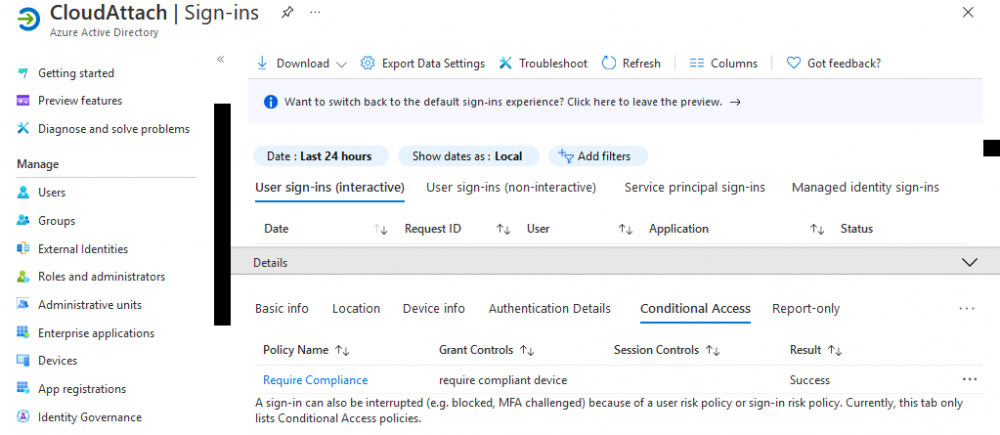
Introduction This is part 6 in a series of guides about cloud attach in Microsoft Endpoint Manager, with the aim of getting you up and running with all things cloud attach. This part will focus on enabling the compliance policies workload. This series is co-written by Niall & Paul, both of whom are Enterprise Mobility MVP’s with broad experience in the area of modern management. Paul is 4 times Enterprise Mobility MVP based in the UK and Niall is 10 times Enterprise Mobility MVP based in Sweden. In part 1 we configured Azure AD connect to sync accounts from the on premise infrastructure to the cloud. In part 2, we prepared Azure resources for the Cloud Management Gateway, in part 3 we created the cloud management gateway and verified that everything was running smoothly. In part 4 we enabled co-management. With co-management, you retain your existing processes for using Configuration Manager to manage PCs in your organization and you gain the additional advantage of being able to transfer workloads to the cloud via Endpoint Manager (Intune). In part 5 we enabled the compliance policies workload and reviewed how that affected a co-managed computer. In this part we will enable conditional access and see how that can be used to deny access to company resources. Conditional access is easy to use when you enable co-management. It requires moving the Compliance Policies workload to Intune. We've already completed both of those activities in the previous 2 parts. Now we will configure conditional access and we'll use it to deny access to company resources unless the device is encrypted with BitLocker. Conditional Access makes sure that only trusted users can access organizational resources on trusted devices using trusted apps. It's built from scratch in the cloud. Whether you're managing devices with Intune or extending your Configuration Manager deployment with co-management, it works the same way. Source: https://docs.microsoft.com/en-us/mem/configmgr/comanage/quickstart-conditional-access Below you can find all parts in this series. Cloud attach - Endpoint Managers silver lining - part 1 Configuring Azure AD connect Cloud attach - Endpoint Managers silver lining - part 2 Prepare for a Cloud Management Gateway Cloud attach - Endpoint Managers silver lining - part 3 Creating a Cloud Management Gateway Cloud attach - Endpoint Managers silver lining - part 4 Enabling co-management Cloud attach - Endpoint Managers silver lining - part 5 Enabling compliance policies workload Cloud attach - Endpoint Managers silver lining - part 6 Enabling conditional access <- you are here Cloud attach - Endpoint Managers silver lining - part 7 Co-managing Azure AD devices Cloud attach - Endpoint Managers silver lining - part 8 Enabling tenant attach Cloud attach - Endpoint Managers silver lining - part 9 Renewing expiring certificates Cloud attach - Endpoint Managers silver lining - part 10 Using apps with tenant attach License requirements Using this feature requires an Azure AD Premium P1 license. To find the right license for your requirements, see Comparing generally available features of the Free, Basic, and Premium editions. Customers with Microsoft 365 Business Premium licenses also have access to Conditional Access features. Sign-in Risk requires access to Identity Protection Step 1. Add some users to an Azure AD group To test conditional access we'll first create an Azure AD group and populate it with some test users. In Microsoft Endpoint Manager, select Groups, then select + New Group, give it a suitable name such as Conditional Access pilot users. Add some test users by clicking on No members selected, select the users you want to test conditional access with and then click on Create. Step 2. Configure conditional access Now you'll create your first conditional access policy, to do so in Microsoft Endpoint Manager, select devices and then select Conditional Access from the Policy node (shown below). In the Conditional Access pane, click on + New Policy, give it a suitable name such as Require Compliance In the Assignments section click on 0 users and groups selected, in the pane that appears select Include, and select select users and groups and add the Azure ad group created in step 1. For the Cloud apps or actions selection, select No cloud apps or actions selected and then choose select apps and select a suitable app such as Office 365. For the Conditions selection, select 0 conditions selected and select the following conditions, Device platforms, select select device platforms and select Windows as shown here and then select Done. Note: You could use other conditions to fine grain the conditional access rules such as trusted locations, use modern authentication only etc but this is just an example. Next, select the Access controls you wish to apply to this policy. For Grant select that the device is marked as Require device to be marked as compliant. Click Select when done. Finally, we will set the policy to Report-only for now so we can test the rule in case we have negative impact on the targeted users which can later be remedied before switching the policy On. Finally, click on Create. For more details on the Report-only setting see https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/concept-conditional-access-report-only Step 3. Testing conditional access Note: Make sure that the devices you use for testing are targeted with the compliance policy created in Part 5 before continuing by adding them to that Configuration Manager collection which we enabled for sync to the cloud (co-managed compliance policy devices) or targeting the assignment to those devices. Below you can see our test devices. And here you can see that the device in question MININT-08FAO5S is Co-managed and with a compliance state of not compliant. On a computer that is not encrypted with BitLocker encryption and therefore not compliant, login as a user that is in the group created in step 1. Once done, open a web browser and browse to https://www.office.com In portal.azure.com select Azure Active directory and scroll down to Sign-ins. This will list all sign-ins for that tenant. Select the latest sign-in for the test user testuser1 (which is added to the azure ad group we created in step 1). As this conditional access policy is in report-only mode, select the Report-only tab and you'll see a report of what happened and it's status as shown here: Now that we've verified it works, let's flip the compliance policy to On and click Save. On the test computer, sign out of office and once again try and browse to https://www.office.com you should see that conditional access blocks access to that resource ! And back in Azure AD, if you check the sign-ins and this time select the Conditional Access tab... you can see that it's correctly reported as a failure. At this point, you can go ahead and encrypt the device with BitLocker, so that it becomes Compliant in Intune. Here we can see the device is listed now as Compliant. Now that it is compliant, verify that it can access Office while using Conditional Access. It should work just fine. And you can verify that too, in the Azure AD sign-ins, using the Conditional Access tab, here you can see that for the policy named Require compliance, with a grant controls of require compliant device it has a result of Success. Job done, you've successfully enabled your first Conditional Access policy and reviewed how it functions on a co-managed device. Please join us in the part 7 where we'll take an Azure AD joined device and add make it co-managed. Related reading Quick start conditional access - https://docs.microsoft.com/en-us/mem/configmgr/comanage/quickstart-conditional-access What is Conditional Access in Azure Active Directory - https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
-

No Site System Listed in Boundary
anyweb replied to wudevr's topic in System Center Configuration Manager (Current Branch)
great stuff, you should definitely check out the posts here, there are plenty to get you up and running again -
As World Backup Day approaches, we're reminded of all the mishaps, backup scares, and near- catastrophes that we've experienced over the years – and how grateful we were to have backup during those times! If you use Microsoft 365/Office 365, Hyper-V or VMware, celebrate with us. All you have to do is sign up for a 30-day free trial of either Altaro VM Backup or Altaro Office 365 Backup – it's your choice! What can you win? Receive a guaranteed €20 Amazon voucher when you sign up for and use the trial of Altaro Office 365 Backup or Altaro VM Backup Get a chance to WIN one of our Grand Prizes when you tell us about your funniest IT catastrophe! Grand Prizes include: What are you waiting for? Sign up now!
-

Windows updates failure
anyweb replied to rob343's topic in System Center Configuration Manager (Current Branch)
can you zip up your CBS logs from C:\Windows\logs\cbs and attach the zip here, feel free to remove any personal info from them first -

Windows updates failure
anyweb replied to rob343's topic in System Center Configuration Manager (Current Branch)
how are your boundaries configured and did you configure a boundary for the cmg, if you did, why ? -

BitLocker Azure, upload removable drive recovery key to Azure AD
anyweb replied to super_aaa's topic in Microsoft Intune
I haven't tried that scenario myself but i'd imagine that anything is possible if you can script something in Powershell, you could write a script to upload the key to the users OneDrive and execute it as a scheduled task (that checks for the drives presence etc...) -

Intune Autopilot
anyweb replied to jkjk12's topic in System Center Configuration Manager (Current Branch)
hi there when you say 'integrated sccm with intune' can you be more specific ? also what version of ConfigMgr are you using ? what licenses are applied to your users in Azure/Intune, and have you configured anything in relation to Autopilot in Intune ? -
thanks a lot for clearing that up @Alex Shumilin, I've modified step 6, part 5 with a link to your comments, much appreciated !
-
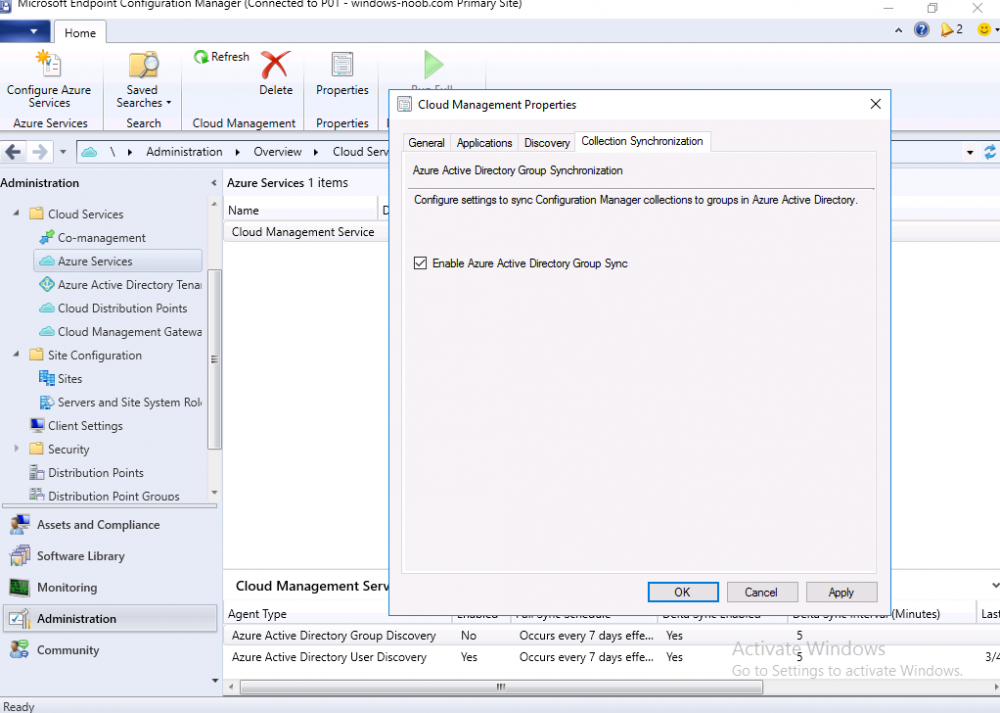
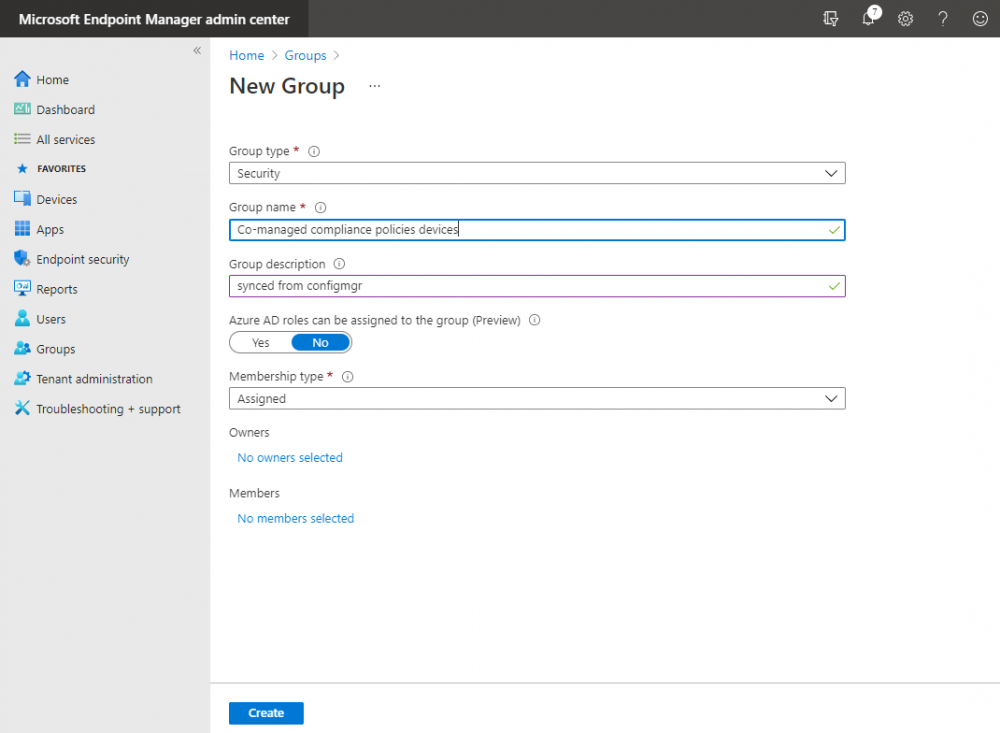
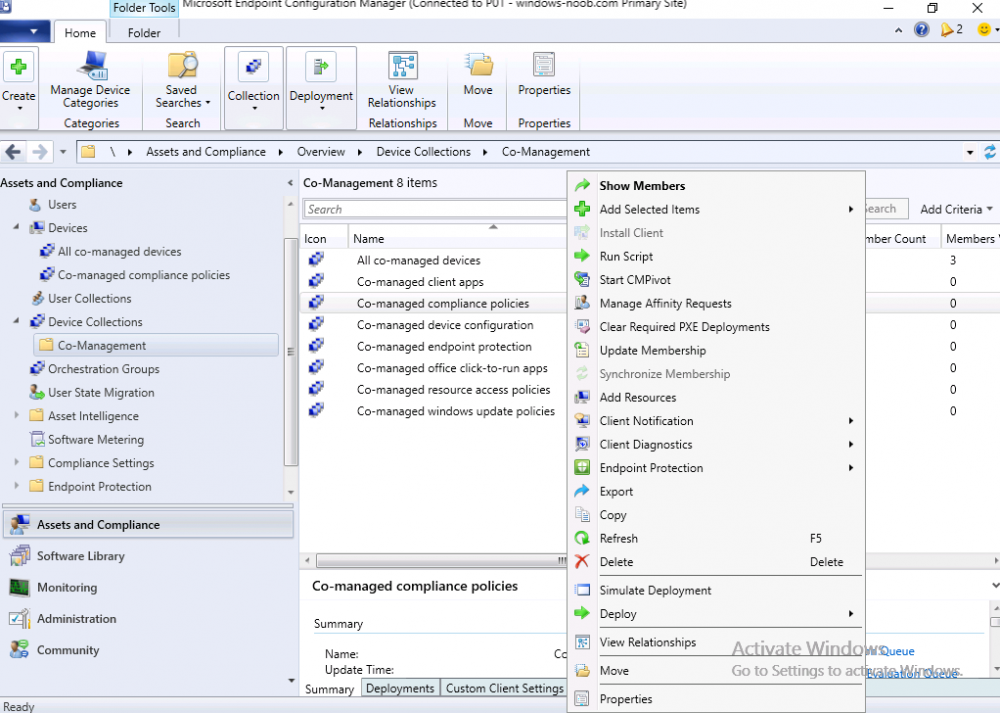
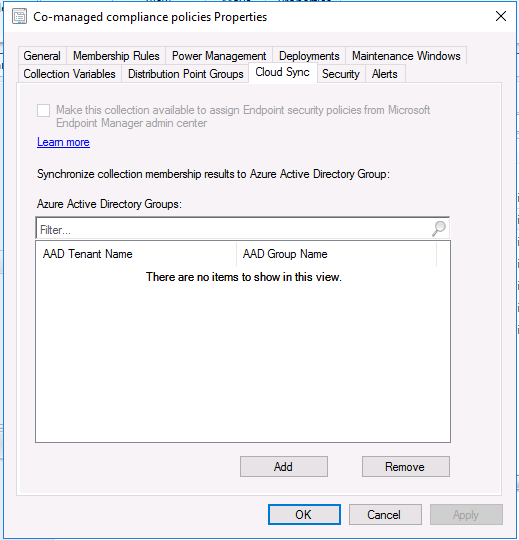
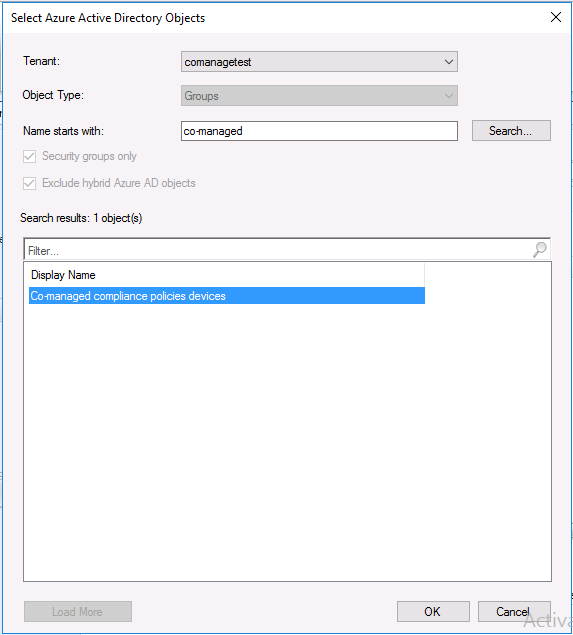
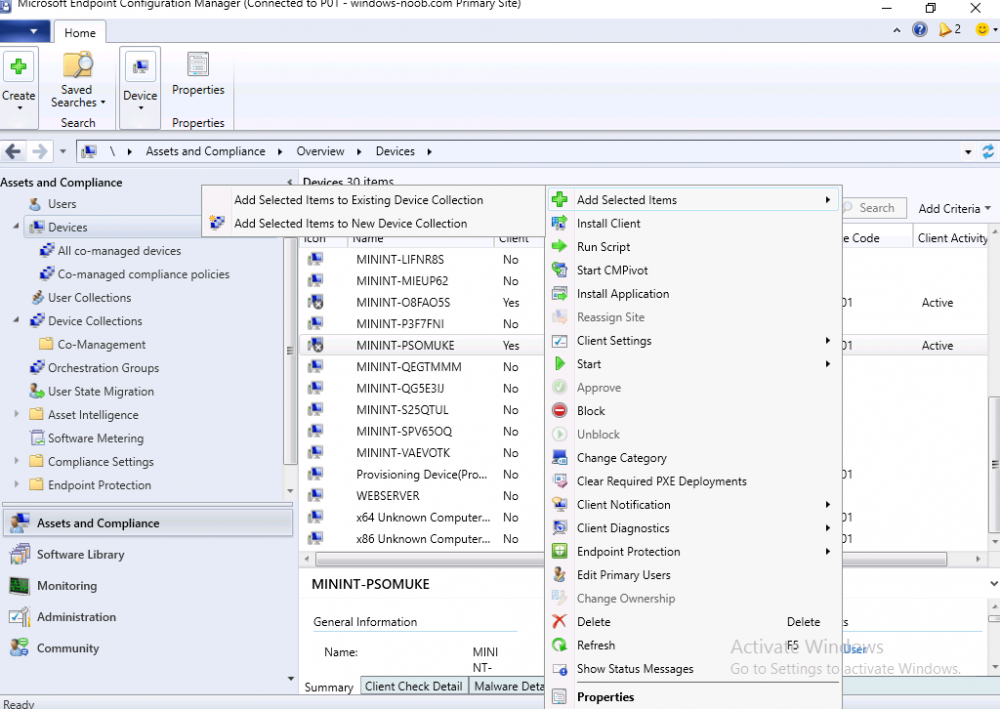
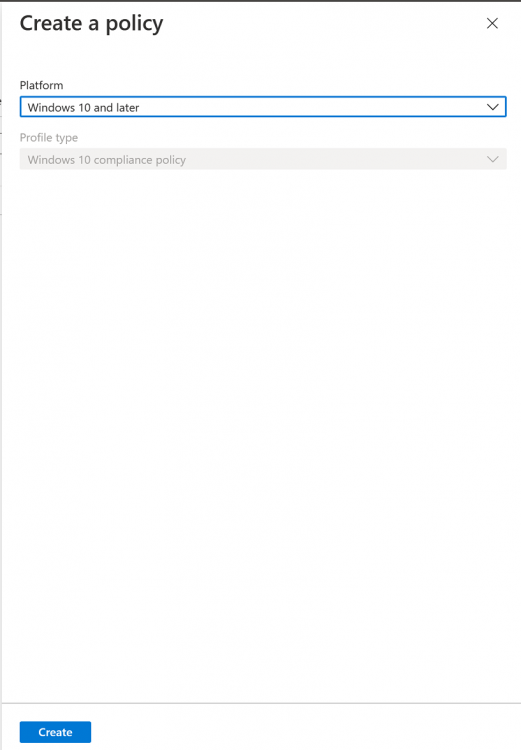
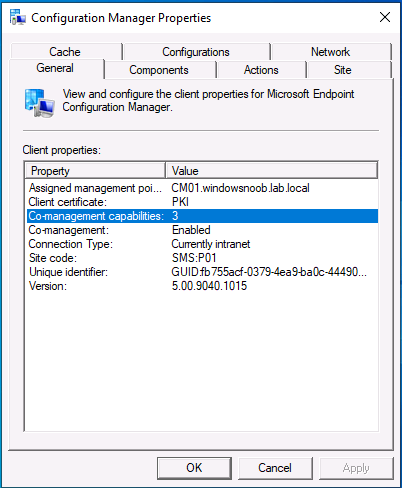
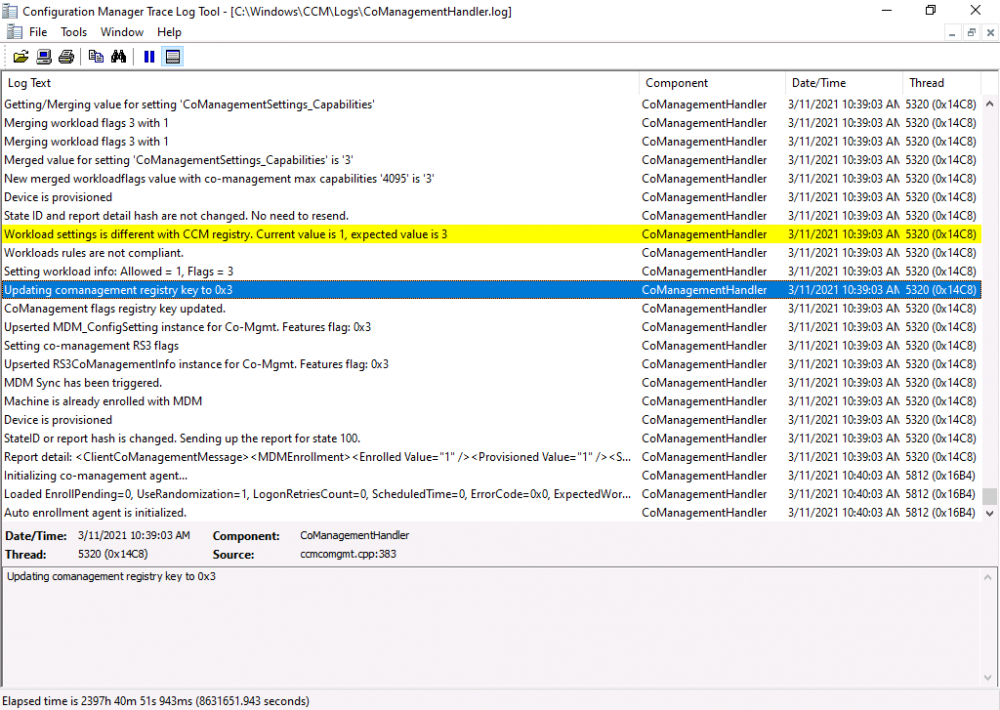
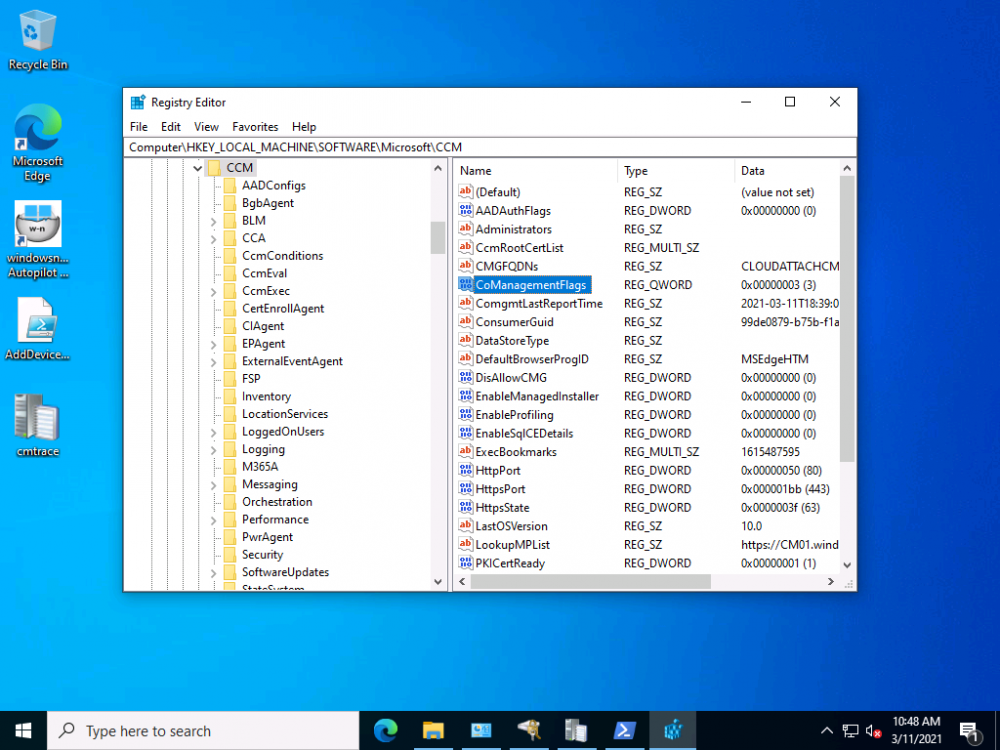
Introduction This is part 5 in a series of guides about cloud attach in Microsoft Endpoint Manager, with the aim of getting you up and running with all things cloud attach. This part will focus on enabling the compliance policies workload. This series is co-written by Niall & Paul, both of whom are Enterprise Mobility MVP’s with broad experience in the area of modern management. Paul is 4 times Enterprise Mobility MVP based in the UK and Niall is 10 times Enterprise Mobility MVP based in Sweden. In part 1 we configured Azure AD connect to sync accounts from the on premise infrastructure to the cloud. In part 2, we prepared Azure resources for the Cloud Management Gateway, in part 3 we created the cloud management gateway and verified that everything was running smoothly. In part 4 we enabled co-management. With co-management, you retain your existing processes for using Configuration Manager to manage PCs in your organization and you gain the additional advantage of being able to transfer workloads to the cloud via Endpoint Manager (Intune). In this part we'll enable the compliance policies workload and see how that affects a co-managed computer. Below you can find all parts in this series. Cloud attach - Endpoint Managers silver lining - part 1 Configuring Azure AD connect Cloud attach - Endpoint Managers silver lining - part 2 Prepare for a Cloud Management Gateway Cloud attach - Endpoint Managers silver lining - part 3 Creating a Cloud Management Gateway Cloud attach - Endpoint Managers silver lining - part 4 Enabling co-management Cloud attach - Endpoint Managers silver lining - part 5 Enabling compliance policies workload <- you are here Cloud attach - Endpoint Managers silver lining - part 6 Enabling conditional access Cloud attach - Endpoint Managers silver lining - part 7 Co-managing Azure AD devices Cloud attach - Endpoint Managers silver lining - part 8 Enabling tenant attach Cloud attach - Endpoint Managers silver lining - part 9 Renewing expiring certificates Cloud attach - Endpoint Managers silver lining - part 10 Using apps with tenant attach Step 1. Verify compliance status in Endpoint Manager Before making any changes to workloads, on a co-managed device, open devices in Microsoft Endpoint Manager and locate that device, you should see that the compliance state is in a status of See ConfigMgr. Step 2. Create an Azure AD group In Endpoint Manager, create a new Azure Ad group which you'll use in the next step. Give it a suitable name like Co-managed compliance policies devices, this group should have a membership of Assigned. Step 3. Add some devices to the workload collection Next, add one or more devices to the collection that you will use when piloting a compliance workload. You can add the device(s) by selecting them and right clicking, choose Add selected items to Existing Device Collection and then point them to the relevant collection corresponding to that workload. The collection you will add device(s) to in this case is the Co-managed compliance policies collection. Step 4. Enable Azure Active Directory group sync In this step you'll enable synchronization of a collections membership to an Azure Active Directory group. This allows you to easily sync the membership of a collection in your on-premises environment to Endpoint Manager. In this step you'll sync one collection but you could add multiple collections depending on your needs. The sync takes place every 5 minutes. To enable this, expand Cloud Services in the Administration node of ConfigMgr, select Azure Services, select Cloud Management service properties and on the Collection Synchronization tab, place a check in Enable Azure Active Directory Group Sync. Next, right click the collection you want to sync and choose Properties. In this example you'll right click on the previously created Co-managed compliance policies collection as shown below. In the properties of that collection, select the Cloud Sync tab. Next, click on Add, then enter a search term such as co-managed to add the Azure AD groups you will sync to from Configuration Manager. Click on OK when done. After 5 minutes, you can browse the Azure AD group created in step 2 and you should see the co-managed devices have synced. Step 5. Create a Compliance policy In Microsoft Endpoint Manager, select Devices in the left pane, select Windows, select Compliance Policies and click on + Create Policy, in the Create a policy window, select Windows 10 and later for the Platform. Then click on Create. select Windows 10 Compliance Policy, enter a name for it and click Next. select Require for the Require Encryption of data storage on device section and then click Next. Set Actions for noncompliance to mark the device as non compliant immediately. You can set a grace period for non-compliance however we want to force this the device to be non compliant quickly for this blog post. Next, assign the compliance policy to the previously created Azure ad group, then don't forget to click on Review+Save. Step 6. Check the client Logon to the client computer that you added to the compliance policy workload collection, and open the ConfigMgr agent. Once the Configmgr client agent receives the policy it will flip the co-management capabilities value from 1 to 3 as shown here. You can get details about what those capability values can be in Ben's blog post here. And this switch is revealed in the CoManagementHandler.log and the registry key it's referring to is this one. Next, we decrypted the device to ensure that it didn't match the compliance policy. If you now check in Endpoint Manager, under devices, the device will show up as Not Compliant. You can drill deeper in the Device Compliance node of the device itself. and click on the Error Next, we allowed BitLocker to Encrypt the device After the device has checked-in with MEM and reported it's compliance state, the change will be updated in Endpoint Manager as Compliant. finally, you can look at the individual compliance settings on the device itself. that's it for this part, see you in Part 6 where we'll enable Conditional Access.
-
These guides explain to you how to setup PKI in a 2 tier setup, after you've completed these 8 detailed guides you are then ready to configure SCCM in https/pki mode as explained here. How can I configure System Center Configuration Manager in HTTPS mode (PKI) - Part 1 How can I configure System Center Configuration Manager in HTTPS mode (PKI) - Part 2 And after that, you are ready to configure BitLocker Management in PKI mode. if you choose to set it up using other guides then please understand that problems you may face may be directly as a result of that choice
-
I don't understand why you are saying things are not working in your lab when you are not following the guide exactly as I've explained it, I've done this guide multiple times, and it works every time. Do it right in your lab so that you get a better understanding of how it all fits together, then once it's working in your lab, try and implement something similar in production with the help of professional consultants in the PKI and/or SCCM area.
-
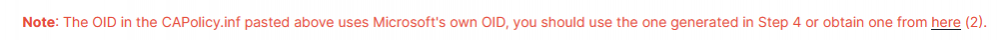
hi Imraz, the scripts available on the internet allow you to create an OID for use in your lab for free, if you want one for production then as explained in the note in step 5 and I quote... I hope that clears it up
-

Missing Intune Subscription
anyweb replied to jkjk12's topic in System Center Configuration Manager (Current Branch)
That used to be the way it was when SCCM had a hybrid mode, that has been depreciated and now, it uses cloud attach. Please see our series of blog posts on the subject here. Parts 2 and 3 will help you setup a CMG which can also function as a CDP (cloud distribution point). -

Issues re-imaging PCs currently on legacy BIOS to UEFI
anyweb replied to stevecrossin's question in Troubleshooting, Tools, Hints and Tips
so are you converting the computer from legacy to UEFI and also converting the file system > if not it won't work -

Bitlocker management on SCCM 2002
anyweb replied to Imraz's topic in System Center Configuration Manager (Current Branch)
IIS doesn't host the recovery keys, they are stored in the ConfigMgr database. The recovery service runs on IIS and that's probably what you are thinking about. The following guides should cover everything you need including HTTPS (pki) which is listed at the bottom of the blog post. If you don't want to go all https (and i'd recommend you do...) then simply add the HTTPS cert to IIS as explained in https://www.niallbrady.com/2019/11/13/want-to-learn-about-the-new-bitlocker-management-in-microsoft-endpoint-manager-configuration-manager/ why are you testing with ConfigMgr 2002, 2010 is out already cheers niall -
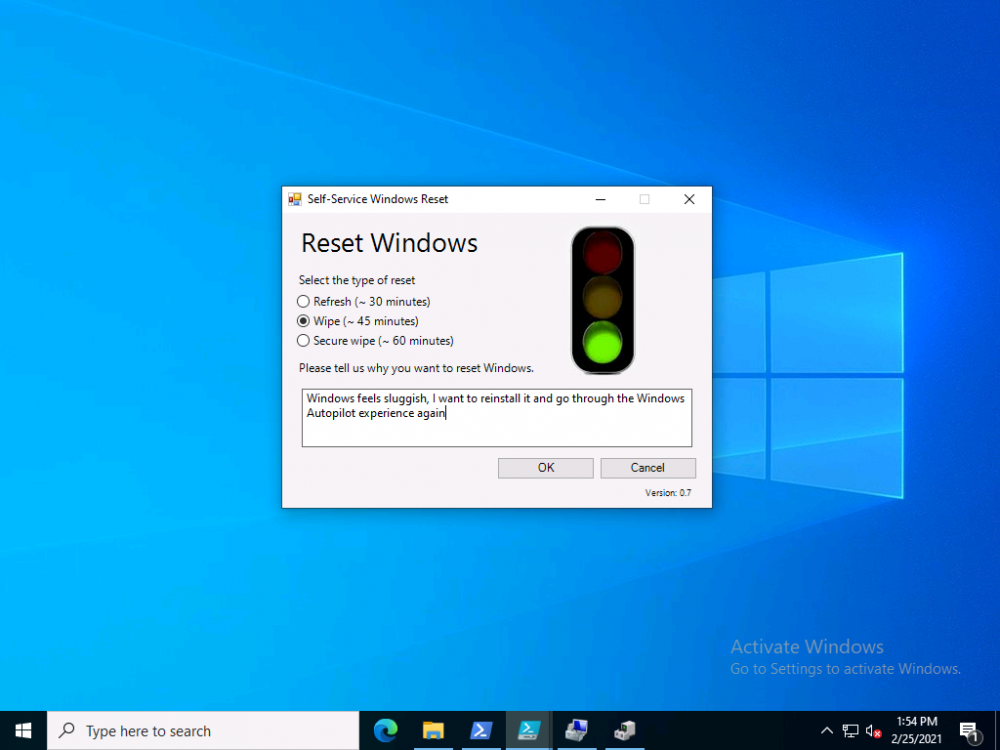
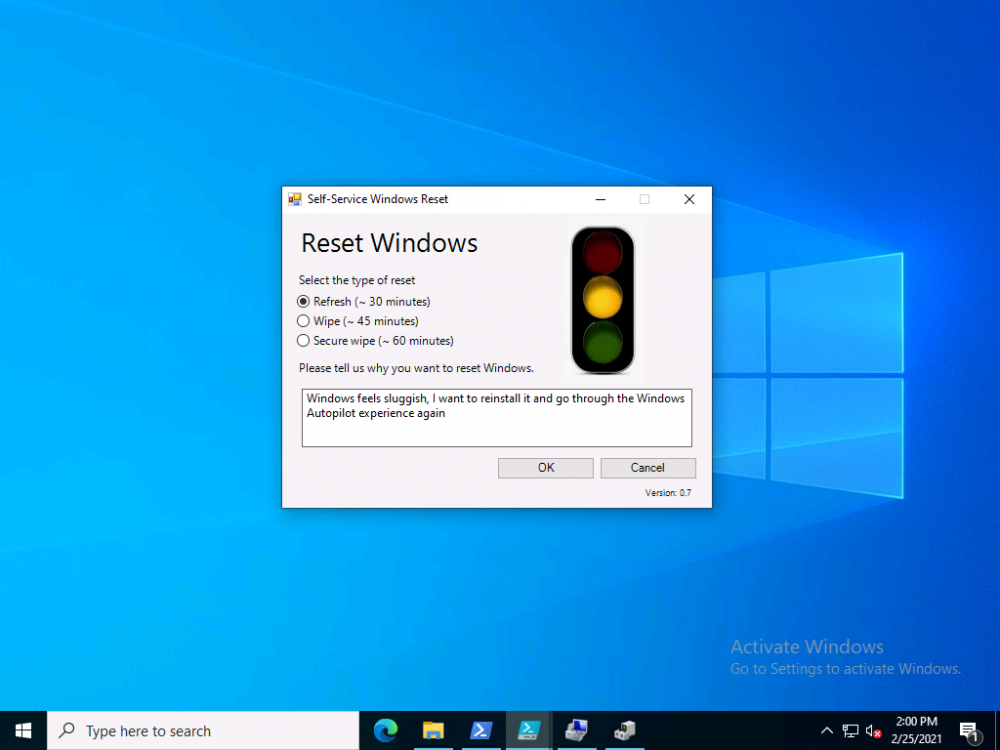
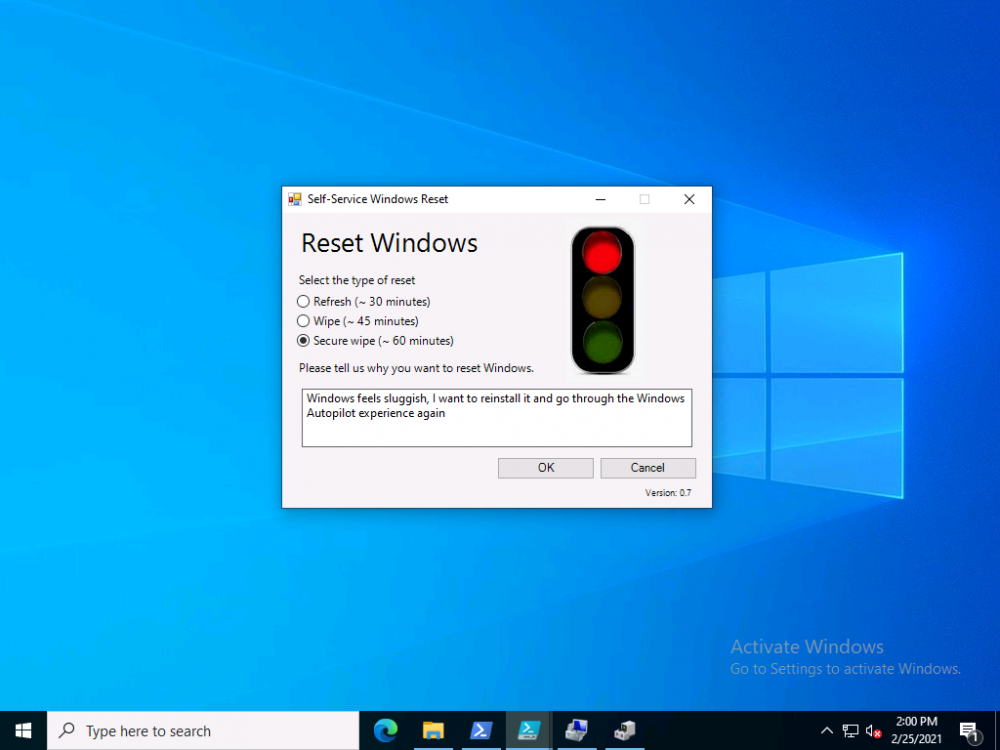
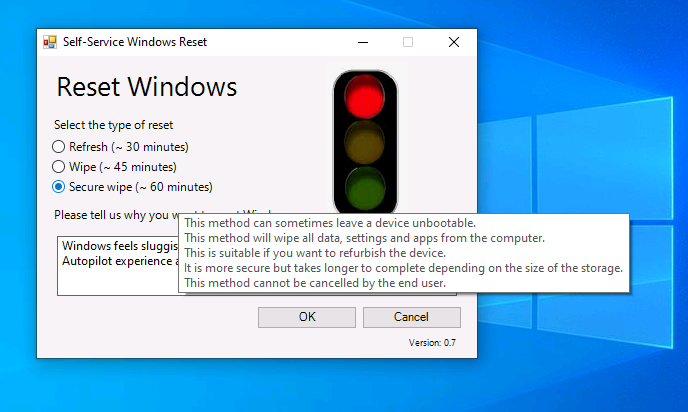
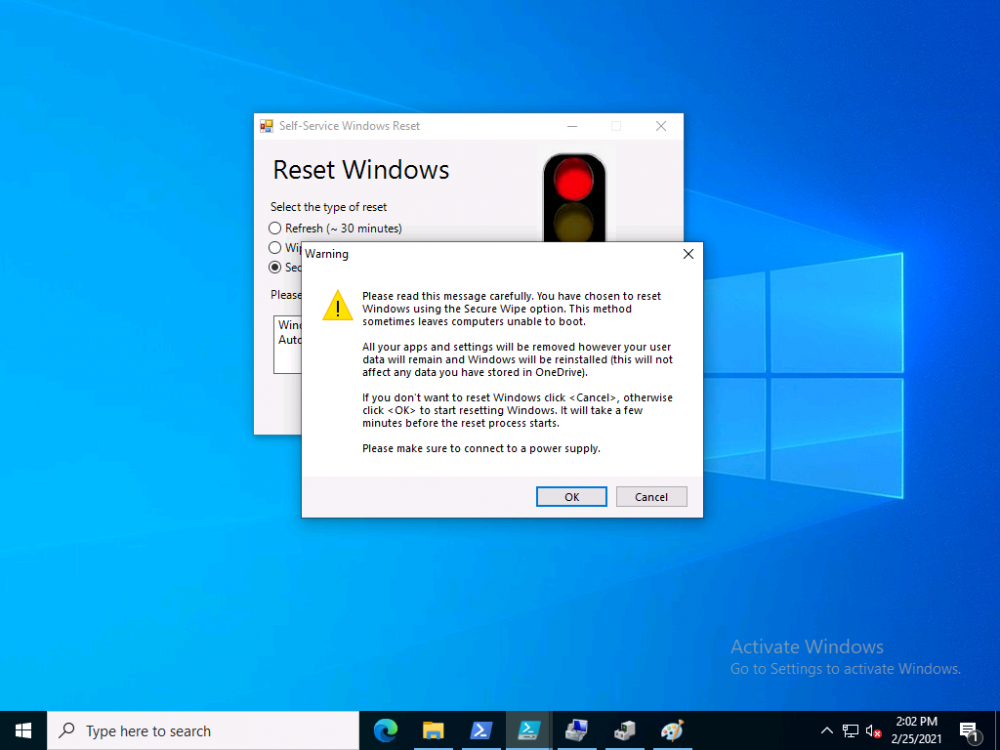
Introduction In a previous blog post I explained how you could use the SendGrid resource in Azure to send emails, and with a PowerShell script create an Intune app to give end users additional options when resetting their Windows Autopilot provisioned pc. This app would gather the Autopilot diagnostic logs (and other relevant logs) and send an email to your support inbox prior to resetting the pc. I've now updated the code quite a few times with the following changes. modified text boxes to 'read' better modified warnings to make it clear when a device might become unbootable added visual clues (traffic lights) to show which method is recommended changed the default method to Wipe added code to check for missing WindowsRE environment and to attempt to repair it if missing modified reg keys so you can reinstall from the company portal if you click cancel bug fixes Well that's it, so let's take a look at some of the changes. When it launches, by default the Wipe method is highlighted with a Green traffic light. This is the recommended Windows reset option for most users. the Refresh option is shown as follows... and the Secure Wipe option is shown with a red stop light, this visual clue should hopefully get the users to think before continuing with this method... If the user hovers over a method they'll get tooltips about what it does And if they decide to continue they'll get more info about the possible choice made (it's a dynamic message) If the user proceeds with the reset then the Windows Autopilot (and other related logs) are gathered, zipped up and emailed to your inbox, and other actions can be taken within the reset-windows.ps1 script, such as a payload of your choice (hint: remove device from an azure ad group) before finally resetting Windows using the method you specified. that's it ! please test this new release and give me your feedback for instructions to set this up, use the new scripts in this blog post but see how here. Downloads You can download the new solution here: resest-windows_ver_07_windowsnoob.zip cheers niall
-

Task Sequence not working
anyweb replied to ITMick's question in Deploy software, applications and drivers
the best thing for you to do for now is to create a lab environment, three or four virtual machines, where you can learn SCCM and understand how it works and practice things before doing them in 'production'. Start with this guide.




.thumb.png.36643d9e609e42af58a97897bb695d5b.png)