-
Posts
9175 -
Joined
-
Last visited
-
Days Won
366
Everything posted by anyweb
-
or... md c:\somedir net share someshare=c:\somedir /UNLIMITED /REMARK:"someshare" /GRANT:Everyone,FULL cacls c:\someshare /E /T /C /G "%USERDNSDOMAIN%\Administrators:f
-

OS deployment and Lenovo computers
anyweb replied to jeaostro's question in Deploy software, applications and drivers
nice info, thanks for sharing -
take a look at this post to see why
-

Add multiple machines to a single collection in SCCM 2007
anyweb replied to minor22's question in Deploy software, applications and drivers
many ways of doing it, easiest way is to create a query to check for members of an active directory security group, and if found in there, they'll be automatically added to the collection you can see how to do that here -
A new hole in Microsoft’s Internet Explorer browser has been identified. The flaw, reported by security firm Vupen, allows remote attackers to take complete control of a vulnerable system. The issue is caused by a use-after-free error within the mshtml.dll library when processing webpages featuring CSS that use “@import” rules. Attacks can exploit the flaw by executing arbitary code via a specially crafted web page. The vulnerability affects Internet Explorer 8 on Windows 7, Windows Vista SP2 and Windows XP SP3. Internet Explorer 6 and 7 are also affected on Windows XP SP3. The flaw is currently un-patched and example code is available. It’s unclear whether the vulnerability is being actively exploited in the wild. Microsoft announced last week that it’s planning a bumper Patch Tuesday on December 14. The software giant plans to patch a 0-day flaw in all supported versions of Internet Explorer. Researchers warned last week that they had successfully bypassed Protected Mode on both Internet Explorer 7 and 8. Microsoft responded to the findings by claiming that the bypass is not a vulnerability and that Protected Mode is not a full security boundary. WinRumors has reached out to Microsoft for clarification on the latest vulnerability. At the time of writing we have not yet received a response. via > http://www.winrumors.com/new-critical-un-patched-internet-explorer-css-vulnerability-discovered/#ixzz17zd3SH9U
-

Bare metal install/PXE Issues
anyweb replied to Gareth's question in Troubleshooting, Tools, Hints and Tips
well if it's abortpxe then the computer is known to SCCM (ie: it's in the sccm database), and it's doing what it's suppsed to, have you tried the fix mentioned here ? how to get rid of abortpxe.com or to be clear, are you getting this issue below ? The details below show the information relating to the PXE boot request for this computer Please provide these details to your Windows Deployment Services Administrator so the this request can be approved. -

Monitoring Forefront Endpoint Protection 2010 – the FEP Dashboard
anyweb posted a question in Endpoint Protection
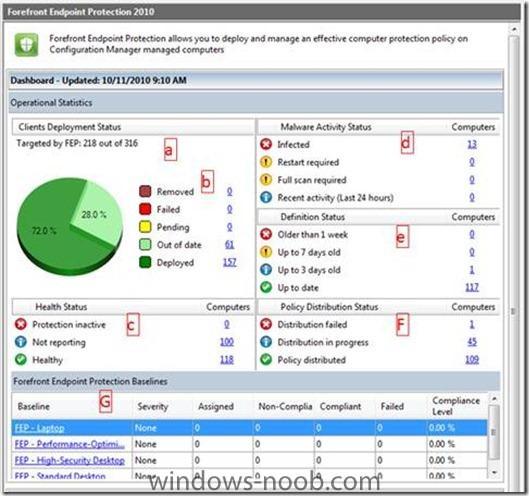
Forefront Endpoint Security 2010 (FEP) Release Candidate was released. In this post, we will discuss ways for administrators to monitor FEP. There are several monitoring features provided with FEP2010 - this is the first in a series of posts about these monitoring features. One of the key architecture changes from FCS is FEP’s alignment with System Center Configuration Manager. Configuration Manager provides the platform for client distribution and policy settings, as well as data collection to and from clients. The FEP Dashboard is an extension to the Configuration Manager console. After deploying the FEP console extension to Configuration Manager (either on the server or on administrator’s laptop), a new node appears in the navigation tree called “Forefront Endpoint Protection” (see Figure 1). Goals: * Provide a single pane of information to an administrator who needs to know how FEP is doing, as well as a starting point for drill down into FEP features and troubleshooting. * Serves as a Launchpad for the administrator to drill down to troubleshooting or other day to day tasks. Figure 1 - FEP Dashboard Capabilities of the FEP dashboard (see the labeled figure above): 1. Computers targeted by FEP: Unlike other security suites, FEP does not require a new discovery mechanism for computers in the organization. Instead, it queries the Configuration Manager database for workstations, laptops and servers (dropping mobile devices). Once discovered, the administrator may decide to protect the clients by creating a software distribution advertisement for collections containing all the clients. * Tip: Administrators can open the FEP collections and drill down to the “Deployment\Not Targeted” collection to identify those computers that are going to be unprotected without manual intervention (e.g. creating an advertisement). * Tip: The only way to capture administrator’s intention is to have the FEP related advertisement to active (never expire). Make sure you have this checked when creating your own. 2. Deployment status: Once an administrator starts to deploy FEP on clients, the clients are moved from the “not targeted” collection to one of the following deployment states: * Locally Removed - Computers where the FEP client was locally removed either by a user with local administrator permission or by another software (e.g. malware). * Failed - Computers for which the FEP client setup program reported a failure. * Pending – Computers for which an active Configuration Manager software distribution advertisement is trying to install the FEP client. * Out of date – Computers for which the reported FEP version is older than the one installed at the server. * Deployed – Computers with FEP client deployed. 3. Health status: For those computers either in “deployed” or “out of date” state, the FEP dashboard provides additional health information: * Protection inactive – The FEP service is reported to be turned off. * Not responding – Computers which have not reported for the last 14 days. * Healthy – Neither of the above. 4. Malware activity status: Shows computers with malware activity. FEP surfaces computers with the following infection states: * Infected – Computers where FEP could not fully mitigate a malware instance. * Restart\Full scan required – Computers where FEP mitigated a malware incident but requires additional action in order to complete the mitigation. * Recent activity – Computers where malware was detected and successfully mitigated (within the last 24 hours). 5. Definition status: Enables administrators to drill down into computers which failed to update their FEP definitions. 6. Policy distribution: Enables administrators to drill down into computers where Configuration Manager failed to distribute FEP policy. 7. FEP baselines: Presents administrators with a quick compliance view into the FEP baselines. * Tip: Administrators may create their own DCM baselines and use FEP Configuration Items (CIs). In order to add (or remove) baselines to the FEP dashboard, a “FEP” category should be added (or removed) to the baseline. * Note: The FEP dashboard is built on top of Configuration Manager collections. Each of the hyperlinks in the FEP dashboard leads to a collection which holds the actual computers sharing the same symptom. via > http://blogs.technet.com/b/clientsecurity/archive/2010/11/09/monitoring-forefront-endpoint-protection-2010-the-fep-dashboard.aspx -
of course, the answer is obvious nice catch ! still I think they are hiding sub-collections for a reason, (server load perhaps ?)
-

Prestaging with MDT 2010U1
anyweb replied to Thorsten's question in Microsoft Deployment Toolkit (MDT)
i believe it's possible with mdt 2010 but there are issues, far better to utilise sccm 2007 sp2 R3 for doing this, are you using SCCM ? -
Microsoft’s Windows operating system is now the most valuable software franchise in the world. Windows, now valued at $110 billion, has surpassed IBM’s Middleware ($107 billion). The figures come courtesy of Trefis, a financial analysis firm who track the most popular stocks in the US. Trefis has been tracking Microsoft’s Windows sales over the past year and has published its results for all to see. “While most of the businesses continued to retain their position, Microsoft’s Windows Operating System emerged as the single most valuable software business segment in 2010. Microsoft Windows Operating System (at $110 billion) surpassed IBM’s Middleware, which at $107 billion now stands at a comfortable second,” states Trefis. Windows isn’t the only software that’s doing well at Microsoft. The software giant’s other cash cow, Microsoft Office, now dominates the third position of most valuable software worldwide. Microsoft Office accounts for $86 billion compared to fourth place Oracle database software at $69 billion. Microsoft’s Windows operating system makes up about 41% of the company’s stock value. Microsoft Office contributes 32% to the company value. Trefis attributes the dominance of Windows to an increase in PC shipments in 2010 and the phenomenal success of Windows 7. Worldwide PC shipments will reach 352.4 million units in 2010, a 14% increase from 2009, according to Gartner research. Windows sales have improved over the past year as a result of the increased PC shipments. Windows has also dominated the netbook market with 68% now running Windows. It has been an incredibly successful year for Windows 7. Microsoft has confirmed that it has now sold over 240 million licenses of Windows 7 and that figure is expected to hit 300 million before the end of the year. Windows 7 now accounts for 25% of operating system market share. Microsoft’s success with Windows 7 began before the product was even widely available. Released in October 2009, the operating system has received praise from consumers, businesses and the media. In November 2009, Windows 7 managed to surpass Apple’s Snow Leopard market share in just two weeks. In early February it was revealed that Windows 7 had reached 10% market share in just three months. Microsoft is currently in the planning and preparation stage for Windows 8. The software giant is expected to share more information and beta bits next year. Steve Ballmer has described the next release of Windows as the company’s “riskiest product bet”. Company officials are keeping any Windows 8 plans close to their chest. According to company insiders that have spoken to WinRumors, Microsoft is currently readying Windows 8 and is betting big on cloud computing. Microsoft is expected to build a ‘Windows Store‘ app store into Windows 8 and Kinect-like functionality. The software maker will also integrate social networking and cloud features into the heart of Windows to finally realize its vision of software+services. A number of cloud related Windows adverts will air over the next year to seek consumer awareness on the cloud. Microsoft is currently readying its first Service Pack for Windows 7. A Release Candidate (RC) build was made available in October and a final version is expected in early 2011. Read more: http://www.winrumors.com/microsoft-windows-is-the-most-valuable-software-business-at-110-billion/#ixzz17uZjRjgT
-
the use of subcollections is being discouraged in sccm2012 from what i've heard, but creating them (and finding them) is possible, have a look at Jamitupya's post here
-
when it fails, bring up a command prompt (f8) and do ipconfig, do you have an ip address ?
-

Bare metal install/PXE Issues
anyweb replied to Gareth's question in Troubleshooting, Tools, Hints and Tips
are you still geting abortpxe errors or something else ? -
in between your tests make sure to delete the usmtbits and usmtoffline folders, i didn't build in any error detection for seeing if they existed in the sample task sequences so it will generate an error the second (and subsequent) time you run the ts. easy to test, just manually delete the dirs before running the task sequence
-
it's greyed out because you havent added a boot image to your task sequence, check your task sequence advanced properties again
-

Deploy Software Applications Zero Touch
anyweb replied to joshjohnson's question in Deploy software, applications and drivers
well the last place I was at had approx 700 applications, most were standard Microsoft apps but others were using all sorts of weird and wonderful installers, this meant that the packages themselves had to be installed in various ways, to standardise this process all apps (whether msi or other) were wrapped in a vbs script which contained many functions for doing various things during the install. so, even an Office 2007 MSI would be wrapped in a vbs, the msi's themselves could be run through Wise Installation studio to generate the needed mst's or whatever you prefer, but ultimately wrapping them in a vbs gave better control of how the application was installed. -
ok well i'm on gmail too anyweb @ ...
-
what about this one ? '©2008 Rick Bennett {rick-bennett@uiowa.edu} 'DISCLAIMER: This script is provided "as is" with all faults. The author cannot be held liable for any indirect, special, incidental, consequential, or exemplary damages arising out of or in any way relating to the use of this script, including without limitation damages for loss of goodwill, work stoppage, lost profits, loss of data, and computer failure or malfunction. You bear the entire risk as to the quality and performance of this script. '~$~----------------------------------------~$~ Option Explicit Dim objWshShell, strSiteCode, strSCCMServerFQDN, strUserName, strPassword Dim objLocator, objSMS, returnValue, strMessage, StartProcess Dim Collection, objCollection, strCollectionCheck, newCollection, strCollectionID, newCollectionRelation, Token, objNewCollection, objNewRight Dim strParentCollectionID, strNewCollectionName, strCollectionComment, strSecurityUserName, intSecurityPermissions, intHourlyMembershipRefreshTime Set objWshShell = WScript.CreateObject("WScript.Shell") ' Provide the needed configuration information here. strSiteCode = "XXX" :'Site code for the SCCM environment strSCCMServerFQDN = "XXXXXXX.XXXXX.XXXX.XXX" :'Name of the SCCM server strNewCollectionName = "XXXXXXXXXX" : 'Name of the collection to be created strCollectionComment = "XXXXXXXXXXXXXXXXX" : 'Comment field shown in the collection strParentCollectionID = "XXXXXXX" : 'ID of the collection to contain the collection to be created strSecurityUserName = "YourDomain\XXXXXXXX" : 'Name of the domain group or user to be granted access intSecurityPermissions = "6887" : 'Permission setting to be granted to the domain group or user intHourlyMembershipRefreshTime = "2" :'Amount of time in hours that the collection should update its membership strUserName = "XXXXXXXXXXXXXXXXXXXXXXX" :'Domain user account that has rights to the SCCM environment strPassword = "XXXXXXXXXXXXXXXXXXXXXXXX" :'Accompanying password to the domain user account strMessage = "This script will attempt to create the " & strNewCollectionName & " collection with the information provided within the script." + (Chr(13)& Chr(13)& Chr(13)) + "Do you wish to continue with this process now?" StartProcess=objWshShell.Popup(strMessage,, "SCCM Collection Creation Script . . .", 4 + 32) If StartProcess = 7 Then ' Clicked the NO button. Wscript.Quit End If ' Attempts to connect to the SCCM environment. returnValue = ConnectToSCCM If returnValue = "NoAccess" Then wscript.echo "Unable to connect to the SCCM provider. Either the user credentials entered are incorrect, or else this account does not have the needed rights and permissions to access the SCCM environment." End If ' Attempts to check if the collection already exists. Set Collection = objSMS.ExecQuery ("select * from SMS_Collection where Name='" & strNewCollectionName & "'") For Each objCollection in Collection strCollectionCheck = "This collection already appears to exist with the collection ID of: " & objCollection.CollectionID Wscript.Echo strCollectionCheck Next If strCollectionCheck = "" Then ' Attempts to create the new collection Set newCollection = objSMS.Get("SMS_Collection").SpawnInstance_() newCollection.Name = strNewCollectionName newCollection.OwnedByThisSite = True newCollection.Comment = strCollectionComment newCollection.Put_ Else Wscript.Quit End If ' Attempts to obtain the collection ID of the newly created collection. Set Collection = objSMS.ExecQuery ("select * from SMS_Collection where Name='" & strNewCollectionName & "'") For each objCollection in Collection strCollectionID=objCollection.CollectionID Next If strCollectionID = "" Then Wscript.Echo "Unable to obtian a collection ID for the newly created collection." Else ' Attempts to move the newly created collection into the desired parent collection. Set newCollectionRelation = objSMS.Get("SMS_CollectToSubCollect").SpawnInstance_() newCollectionRelation.parentCollectionID = strParentCollectionID newCollectionRelation.subCollectionID = strCollectionID newCollectionRelation.Put_ ' Attempts to set the membership update schedule on the collection. Set Token = objSMS.Get("SMS_ST_RecurInterval") Token.HourSpan = intHourlyMembershipRefreshTime Token.StartTime = ConvertToWMIdate(Now()) Set objNewCollection = objSMS.Get ("SMS_Collection.CollectionID='" & strCollectionID & "'") objNewCollection.RefreshSchedule = Array(Token) objNewCollection.RefreshType = 2 objNewCollection.Put_ ' Attempts to set the needed security permissions on the newly created collection. Set objNewRight = objSMS.Get ("SMS_UserInstancePermissions").SpawnInstance_() objNewRight.UserName = strSecurityUserName objNewRight.ObjectKey = 1 objNewRight.InstanceKey = strCollectionID objNewRight.InstancePermissions = intSecurityPermissions objNewRight.Put_ End If Wscript.Echo "Finished creating the " & strNewCollectionName & " collection. Please use the Configuration Manager console and create any needed membership queries that may be required." Wscript.Quit ' ~$~----------------------------------------~$~ ' FUNCTIONS & SUBROUTINES ' ~$~----------------------------------------~$~ Function ConnectToSCCM ' Attempts to use the provided information to connect to the SCCM environment. On Error Resume Next Set objLocator = CreateObject("WbemScripting.SWbemLocator") Set objSMS = objLocator.ConnectServer(strSCCMServerFQDN, "root\sms\site_" & strSiteCode, strUserName, strPassword) If Err then Err.Clear ConnectToSCCM = "NoAccess" Exit Function End If objSMS.Security_.ImpersonationLevel = 3 objSMS.Security_.AuthenticationLevel = 6 ConnectToSCCM = "Accessed" End Function ' ~$~----------------------------------------~$~ Function ConvertToWMIdate(strDate) ' Attempts to convert the date into a WMI date-time. Dim strYear, strMonth, strDay, strHour, strMinute strYear=year(strDate) strMonth=month(strDate) strDay=day(strDate) strHour=hour(strDate) strMinute=minute(strDate) If len(strMonth) = 1 Then strMonth = "0" & strMonth End If If len(strDay) = 1 Then strDay = "0" & strDay End If If len(strHour) = 1 Then strHour = "0" & strHour End If If len(strMinute) = 1 Then strMinute = "0" & strMinute End If ConvertToWMIdate = strYear & strMonth & strDay & strHour & strMinute & "00.000000+***" End Function tell me what are you busy with (i'm on office communicator if you want to chat) cheers niall
-
System Center Configuration Manager 2007 SP1, SP2 and R2 now support Microsoft SQL Server 2008 SP2 as a Configuration Manager 2007 site database. The site system role of Reporting Services Point and the client status reporting feature of System Center Configuration Manager 2007 R2 are supported. No software updates are required. --Harini Muralidharan This posting is provided "AS IS" with no warranties, and confers no rights. via > http://blogs.technet.com/b/configmgrteam/archive/2010/12/08/configuration-manager-support-announcements-for-november-2010.aspx
-
as Eswar says, plus see > http://www.microsoft.com/downloads/details.aspx?FamilyID=b9fb478a-ec98-47f2-b31e-57443a8ae88f in addition to testing out what is covered in the SCCM guides here Interviewrs will want to gauge how much you know about SCCM and some areas that you should have good knowledge on would include:- Collections Operating System Deployment Software Distribution Software Updates Reporting good luck ! cheers niall
-
It’s always telling to hear what Charles Songhurst, Micrsosoft’s General Manager of Corporate Strategy, is focused on. Songhurst, an eight-year Microsoft veteran, has held various strategy and mergers and acquisitions posts at Microsoft. According to his bio, Songhurst was instrumental in helping to kill the acquisition of Yahoo, saving the company $48 billion, and subsequently negotiating the Microsoft-Yahoo search partnership. These days, Songhurst is spending most of his time on two areas — the economics of the cloud and piracy — he told attendees of the NASDAQ OMX Investor Program on December 7. (I listened to the Webcast.) Microsoft recently issued a white paper entitled “The Economics of the Cloud,” which Microsoft envisioned as “help(ing) build a framework that allows IT leaders to plan for the cloud transition. (My ZDNet colleague Larry Dignan wrote about Microsoft cloud economics paper last month.) Among the takeaways: Larger clouds save users more money than smaller clouds. Songhurst talked up the economies of scale that can be realized via day-parting to drive up server utilization and other ways of taking advantage of both supply-side and demand-side factors. He noted (not surprisingly) that second-tier, non-mission-critical apps are what’s going to the cloud first. And he claimed that Microsoft wouldn’t cannibalize its business by moving more and more to the cloud because moving enterprise IT does not “somehow turn (things) into a simple, homogeneous mass.” The one new tidbit Songhurst shared was a connection I hadn’t made before. He said that Microsoft is counting on the movement of more of its assets to the cloud as helping to reduce piracy. “As products become services, piracy naturally disappears,” Songhurst said. “It is hard to pirate when the experience is coming from a server.” Songhurst said piracy reduction due to the cloud was a long-term phenomenon, which might not have much impact until the next decade, but that it was “a very positive trend.” One other question from an attendee of the NASDAQ event which I thought was interesting was how Microsoft could be both a good consumer and good enterprise company. Songhurst acknowledged that it was very hard to do both well, but the “rewards” of managing to were “very high.” Like CEO Steve Ballmer has said recently, Songhurst claimed that the synergies between the two parts of the business are tightly intertwined and interdependent. He didn’t say much else on the topic. Songhurst also declined to answer a quesetion about when and if Microsoft would port Windows to ARM, noting “we don’t talk about anything about Windows beyond official announcements.” He also deflected questions about what’s coming next on the Office front and how/when Kinect-like capabilities might come to PCs. Still, I found it interesting just how much attention (and at what levels) the company is paying to the economics around the cloud these days…. via > http://www.zdnet.com/blog/microsoft/microsoft-moving-more-assets-to-the-cloud-may-curb-piracy/8139?tag=mantle_skin;content
-
Microsoft is introducing a new feature, “Tracking Protection,” to Internet Explorer (IE) 9 “to help consumers be in control of potential online tracking as they move around the Web,” according to company officials. Microsoft officials said to expect the new feature to be part of the Release Candidate (RC) test build of IE 9, which is due out in early 2011. Microsoft execs have not said when to expect the final version of IE 9 to be released, but I continue to hear April 2011 is the internal target. Tracking Protection will be an opt-in mechanism. Microsoft officials said “Tracking Protection Lists” will enable consumers to control what third-party site content can track them when they’re online. The new feature is meant to complement other privacy features in IE, including InPrivate Browsing, a k a porn mode. From the IE Blog, here’s an explanation of how those lists will work: Microsoft has posted some slides and videos detailing how the Tracking Protection feature will work. Microsoft announced its plans to add Tracking Protection to IE on December 7, the same day (and the same time) that Google is holding a webcast on its Chrome 9 browser and is expected to announce more details of its Chrome OS operating system for netbooks. via > http://www.zdnet.com/blog/microsoft/microsoft-to-add-privacy-tracking-to-ie-9-test-build-in-2011/8142
-
is this a question ? can you be more specific please..