-
Posts
9255 -
Joined
-
Last visited
-
Days Won
370
Everything posted by anyweb
-

XP install from WDS fails
anyweb replied to beernerd's question in Windows Deployment Services (WDS)
as it's XP, its most likely related to your HAL or storage so checkout the SATA settings in the bios and change them to ATA (compatible) cheers niall -

Installation Forefront Security
anyweb replied to Dom's question in Troubleshooting, Tools, Hints and Tips
could it be this ? Windows Installer Error 1623 This language of this installation package is not supported by your system. -
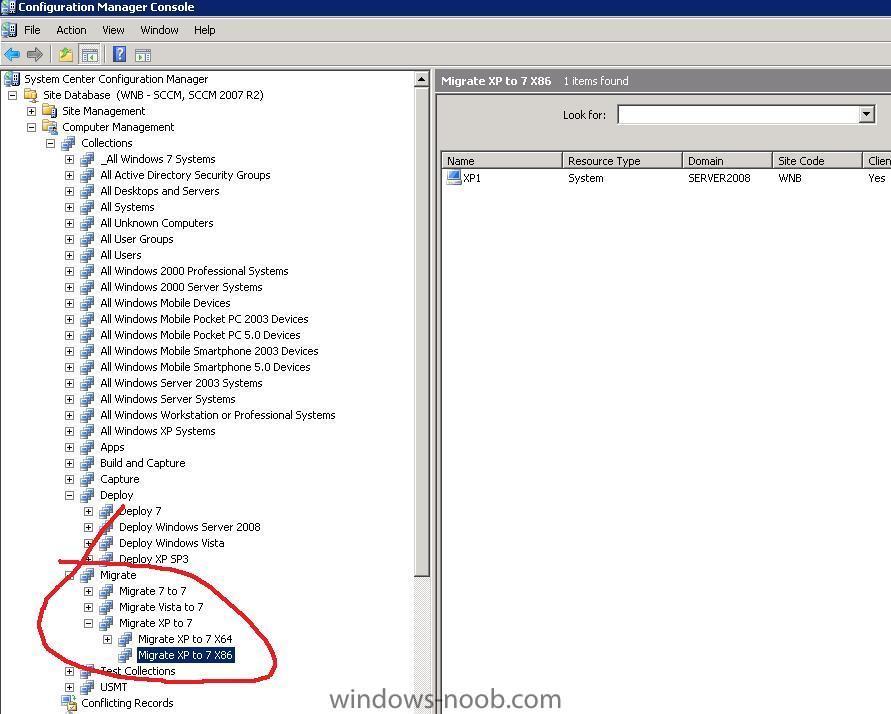
hi all, as this is a common requirement, here are two Task Sequences I use for demoing Windows XP migrations to Windows 7, Related Reading:- OSDMigrateAdditionalCaptureOptions on Technet OSDMigrateAdditionalRestoreOptions on Technet Before you can use these sample task sequences you must have done the following Steps. Using Computer Association add a computer to your Deploy XP collection, and then Deploy Windows XP to that computer. Once Deployed with XP you can use Direct Membership to add that computer to the Migrate XP to 7 Collection described below. XP to Windows 7 Demo - X86 using Hardlinking The first task sequence XP to Windows 7 Demo - X86 using Hardlinking.xml will migrate XP to Windows 7 using hardlinking XP to Windows 7 Demo - X86 using Hardlinking.xml XP to Windows 7 Demo - X86 using SMP The second one uses a SMP *State Migration Point* XP to W7 Demo - X86 using SMP.xml simply import these task sequences into ConfigMgr, and replace the missing package references (configmgr X86 boot images, microsoft deployment 2010 settings, mdt2010 files, windows 7 autologin enable package, usmt4 package and the Windows 7 X86 WIM file itself). See below screenshots to help you with that Task Sequence References with hardlinking Task Sequence References with SMP and then advertise the task sequences to a migrate XP to Windows 7 collection add computers to the Migrate XP to Windows 7 collection and kick off the appropriate TS via RAP.
-
because it cant find the script to run, create it as a package instead, with a program. and the program shall be the vbs script or cmd file
-
did you update collection membership and press F5 to refresh ?
-
i'm lost at your description of the problem, so let's simplify it Dom. are you saying that your TS is failing the three tasks ? if so, which of the three is it failing on ? why do you have a boot image attached to this TS, why is there a reboot ?
-

Setting computername during deployment
anyweb replied to anyweb's question in Troubleshooting, Tools, Hints and Tips
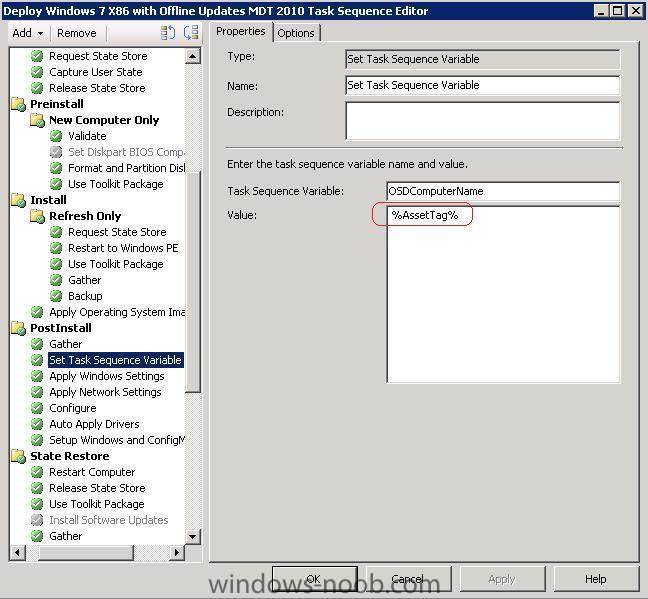
did you Add a "Set Task Sequence Variable" to the postinstall phase before the "Apply Windows Settings" step ? see the following screenshot, however in this screenshot i'm making the computername=the Asset Tag of the computer all you have to do is to leave the assettag value empty -

Office 2k3 Problems
anyweb replied to CPS_TECH_DTAFT's question in Deploy software, applications and drivers
maybe office 2007 is being installed to a collection you are in ? -
yes this still on target however i'm lacking two things at this point: 1. some software for making Webcasts, any recommendations ? 2. time do do the webcasts cheers niall
-
Reports have surfaced about a new security hole that has been in Windows since the release of Windows NT 3.1 on July 27, 1993. The vulnerability is present in all 32-bit versions of Windows released since then, including all supported versions: Windows 2000, Windows XP, Windows Server 2003, Windows Vista, Windows Server 2008, and Windows 7. Microsoft has issued Security Advisory (979682) to address the elevation of privilege vulnerability in the Windows kernel, making sure to note that 64-bit versions of Windows, including Windows Server 2008 R2, are not affected. ... Despite the fact that there is no patch available from Microsoft, Ormandy decided to publish the information because he believes the workaround is simple enough: disable the MS-DOS subsystem. via > http://arstechnica.com/microsoft/news/2010/01/microsoft-investigates-17-year-old-windows-flaw.ars
-
As promised, Microsoft released the patch that fixes the Google attack vulnerability. Seven other holes are closed off as well. "Microsoft on Thursday issued a cumulative critical patch for Internet Explorer that fixes eight vulnerabilities, including a hole targeted in the China-based attacks on Google and other U.S. companies. The security update is rated critical for all supported releases of IE 5, 6, 7, and 8, according to the advisory. The more severe vulnerabilities could allow remote code execution if a user views a malicious Web page using IE, it said." via > http://www.osnews.com/story/22774/Microsoft_Fixes_8_IE_Holes_Including_One_Used_in_Attacks
-

Best way to reinstall software following PC rebuild
anyweb replied to MED1975's question in Deploy software, applications and drivers
well lots of ways but most commonly discovery methods as they are what puts your computer or user in a collection in the first place (unless you add them using direct membership queries or such like), and you are most likely basing your application installs on what collection a user/computer is a member of, so... you could tweak your discovery methods to go more often, and for the collection update to update itself within a time period that corresponds to the discovery methods so lets say you do some AD discoverys every 3 hours, well then you might want some application collections refreshing themselves every 4 hours, I would strongly suggest testing this backwards in a lab, here are some good pointers Deploy software through AD Groups linked to Collections in SCCM, AD Group for deployments everyone needs software eventually Fully automated Application Groups One of the best ways of using AD groups for deploying software in addition to the above, the user (and computer if used) policy updates on the CLIENT will need to be tweaked cheers -

Best way to reinstall software following PC rebuild
anyweb replied to MED1975's question in Deploy software, applications and drivers
hi Matt a simple alternative would be to have a thick image (your base os plus vital apps like office, adobe reader, winzip, whatever...) and let the other less commonly used apps install as normal via SCCM let's see what the others have to say about it cheers niall -
it's this
-
i think proxy settings have to be configured via the Internet Explorer Administration Kit, have you checked that out ? of course if you find out differently post it here
-
can't you increase the hdd size/partition size/storage of the vm ?
-
Posted by Ed Bott @ 12:05 pm I just spoke with George Stathakopoulos, General Manager of Trustworthy Computing Security at Microsoft, regarding the ongoing security issue affecting Internet Explorer. (For background, see my earlier post, It’s time to stop using IE6. For an update on the vulnerability and its impact, see this Zero Day blog post from ZDNet’s Ryan Naraine.) According to Stathakopoulos, a security update for all versions of Internet Explorer will be released “out of band” - that is, earlier than the next regularly scheduled update cycle on Patch Tuesday, February 9. The update is currently undergoing testing, and Microsoft expects to announce a release schedule tomorrow, January 19. Separately, Gregg Keizer at ComputerWorld reports that French security researchers claim to have circumvented the Data Execution Prevention security feature and executed their own exploit code on Internet Explorer 8 with DEP enabled. A Microsoft spokesperson says they are investigating those claims and “will take appropriate action to help protect customers.” Stathakopoulos reiterated that Microsoft so far has seen only “very limited and targeted attacks” and confirmed that the only successful attacks have been against IE6. via > http://blogs.zdnet.com/Bott/?p=1651
-

Updating SCCM 2007 SP2 RC (or beta) to SP2 Final
anyweb replied to anyweb's topic in Configuration Manager 2007
if you reinstall sp2 on this box does it change the version of the boot image ? -

Updating SCCM 2007 SP2 RC (or beta) to SP2 Final
anyweb replied to anyweb's topic in Configuration Manager 2007
sorry, i meant the Windows PE tab, it lists the drivers -

Updating SCCM 2007 SP2 RC (or beta) to SP2 Final
anyweb replied to anyweb's topic in Configuration Manager 2007
if you click on the drivers tab of that boot image are any listed ? -

Updating SCCM 2007 SP2 RC (or beta) to SP2 Final
anyweb replied to anyweb's topic in Configuration Manager 2007
well the sp2 update wont update custom images, the boot images (both those that get updated and those that fail to update) are listed in the ConfigMgrSetup.log -
can you show a screenshot(s) of what you did so others will know ? cheers niall
-
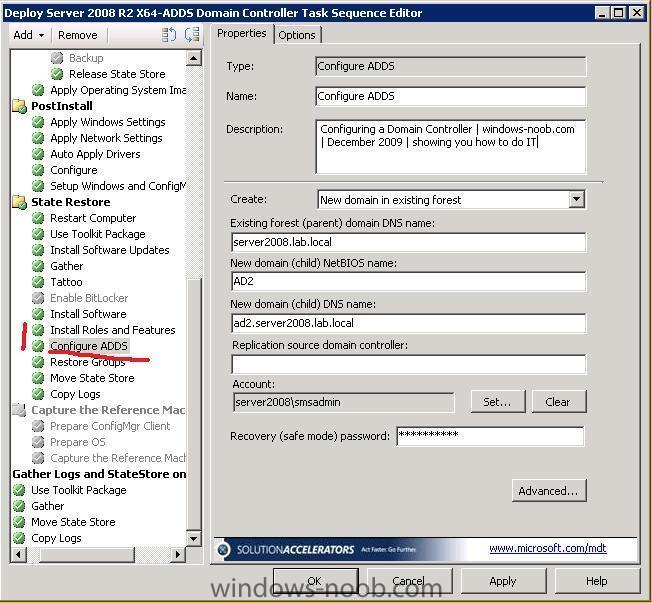
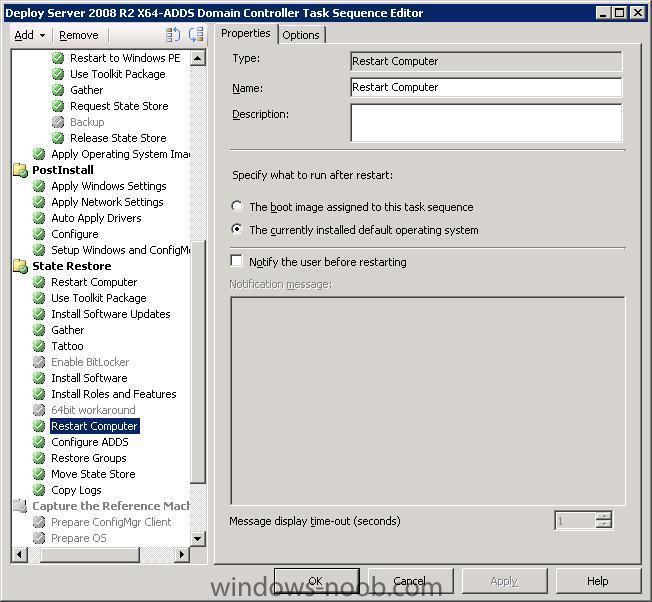
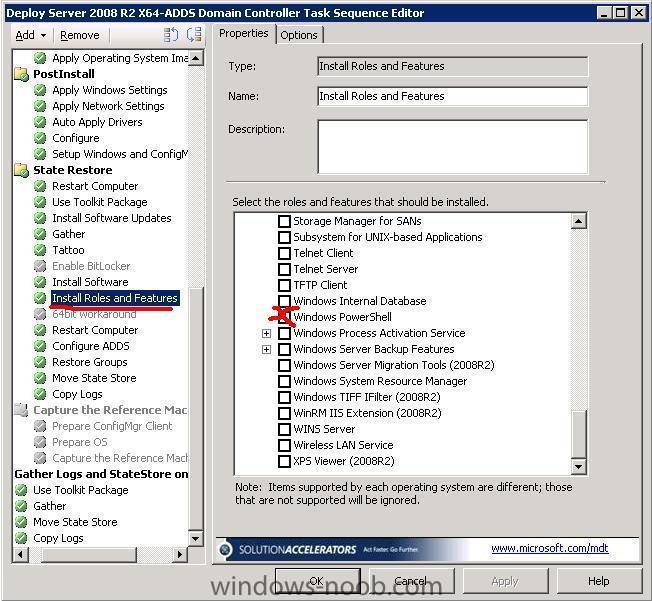
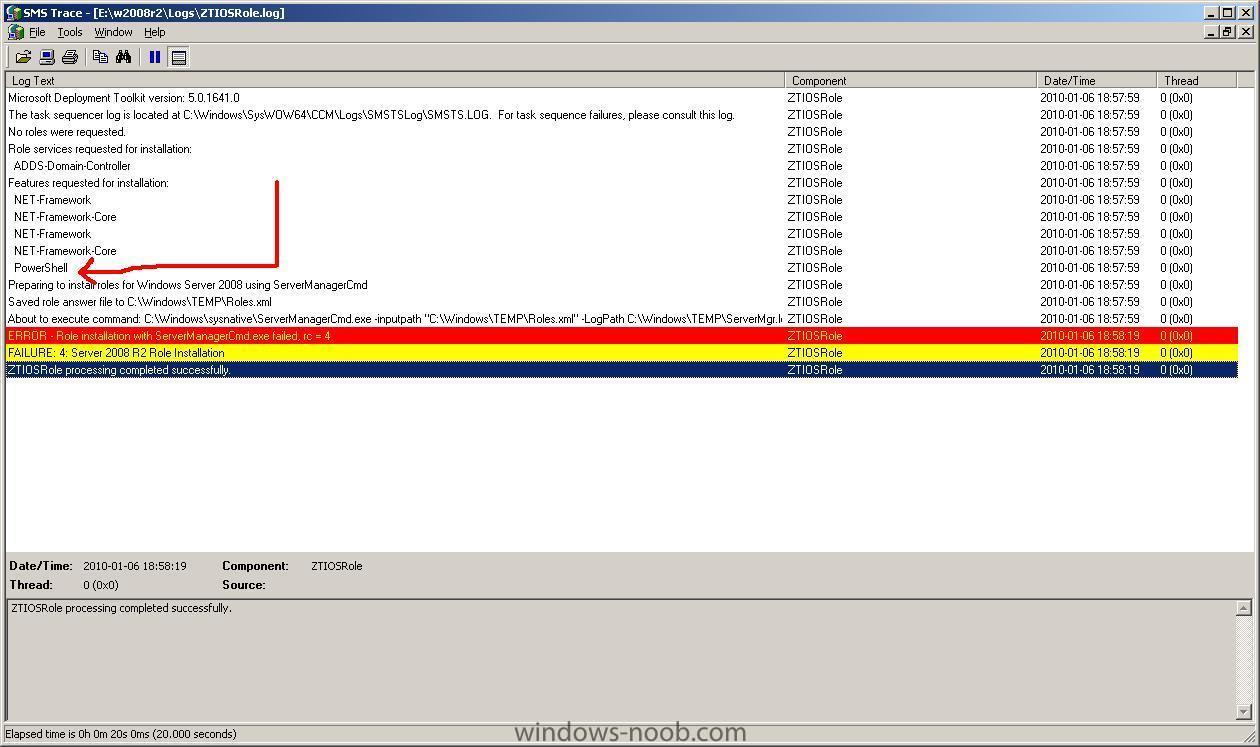
This post is not finished yet, work in progress... The following task sequence can be used to deploy Server 2008 R2 with ADDS, deploy server 2008r2.xml note: leave out Windows Powershell from the TS otherwise Roles and Features will be ignored.
-
The German government has warned web users to find an alternative browser to Internet Explorer to protect security. The warning from the Federal Office for Information Security comes after Microsoft admitted IE was the weak link in recent attacks on Google's systems. Microsoft rejected the warning, saying that the risk to users was low and that the browsers' increased security setting would prevent any serious risk. However, German authorities say that even this would not make IE fully safe. Thomas Baumgaertner, a spokesman for Microsoft in Germany, said that while they were aware of the warning, they did not agree with it, saying that the attacks on Google were by "highly motivated people with a very specific agenda". "These were not attacks against general users or consumers," said Mr Baumgaertner. "There is no threat to the general user, consequently we do not support this warning," he added. Microsoft says the security hole can be shut by setting the browser's security zone to "high", although this limits functionality and blocks many websites. However, Graham Cluley of anti-virus firm Sophos, told BBC News that not only did the warning apply to 6, 7 and 8 of the browser, but the instructions on how to exploit the flaw had been posted on the internet. "This is a vulnerability that was announced in the last couple of days. Microsoft have no patch yet and the implication is that this is the same one that exploited on the attacks on Google earlier this week," he said. Computer expert Alan Stevens: "It's like having a window left open in your house" "The way to exploit this flaw has now appeared on the internet, so it is quite possible that everyone is now going to have a go." Microsoft traditionally release a security update once a month - the next scheduled patch is the 9th of February. However, a spokesman for Microsoft told BBC News that developers for the firm were trying to fix the problem. "We are working on an update on this issue and this may well involve an out of cycle security update," he said. full story > http://news.bbc.co.uk/2/hi/technology/8463516.stm
-
The Cumulative Update 974144 is available at the following URL It resolves the following issues: # The Product Knowledge tab is displayed as the Company Knowledge tab after you import a language pack for System Center Operations Manager 2007 R2. # An agent cannot be removed successfully from a Windows Cluster service node. # The Heathservice.exe process on a Windows Cluster service passive node may have excessive CPU utilization. # The Healthservice.exe process may crash when it uses the OLE DB module. # The workflows that use the OLE DB data source may unload themselves if the underlying provider returns a null string or an empty string. # An instance of the MonitoringHost.exe process may cause a memory leak in nonpaged pool memory. # The notification subscriptions do not work if they are configured to parse a CustomField field or an AlertOwner field. # The Operations console loses the status as the current object that is in focus when a search filter is applied. # The SRSUpdateTool.exe process returns an error that states “Failed while updating registry entry for reporting code MSI component” when you try to upgrade SQL Reporting Services 2005 to SQL Reporting Services 2008. # The Operations Manager UI may crash when the Connector column and the Forwarding Status column are added to an Alert view. # The agents may re-process old Windows event log entries and then incorrectly generate alerts for these events that are not new. # Health state reliability fixes and improvements. # The Operations Manager Audit Collection Service (ADTServer.exe) does not start on an ACS Collector if the operating system is upgraded to Windows Server 2008 R2. # In a performance report that is exported, the list of object instances is not displayed. Support for Windows Server 2008 R2 and Windows 7 is also included in this CU. Here is the recommended installation order : 1. Root Management Server (RMS) 2. Manual update of the Operations Manager database together with the included stored procedure file that is discussed later 3. Manual import of the Management Pack library that is discussed later 4. Secondary Management Servers 5. Gateway Servers 6. Deploy the agent update to the agents that used a discovery-based installation 7. Operations console role computers 8. Web Console server role computers 9. Audit Collection Service role computers 10. Apply the agent update to manually installed agents via > http://myitforum.com/cs2/blogs/fdufour/archive/2010/01/17/cumulative-update-1-for-system-center-operations-manager-2007-r2-kb974144.aspx