-
Posts
9257 -
Joined
-
Last visited
-
Days Won
371
Everything posted by anyweb
-

Surface Go 2 PXE Issues
anyweb replied to Damo's topic in System Center Configuration Manager (Current Branch)
it's probably sitting like that because it's a shared network dongle, you can try the advice here https://systemcenterdudes.com/sccm-duplicate-hardware-identifiers/ -
according to your log, this is why it failed, I'm curious though, did you read the log ? The execution of the group (PreChecks) has failed and the execution has been aborted. An action failed. Operation aborted (Error: 80004004; Source: Windows) TSManager 20/01/2021 15:39:16 9960 (0x26E8) Failed to run the last action: Foundation Application Check. Execution of task sequence failed. The line in question that you need to investigate is: Failed to run the last action: Foundation Application Check. Execution of task sequence failed.
-
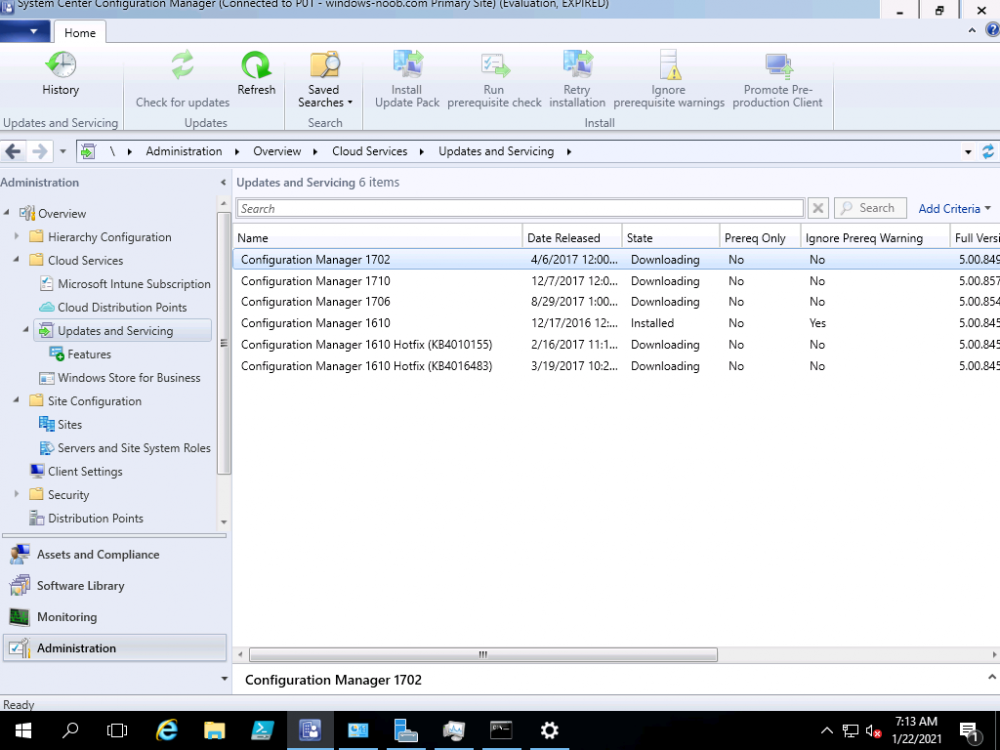
it's been a long time since i blogged about it (see here) but i think you'll have to go n+3, so probably offline upgrade from 1606 to 1706 or so and so on, 1606 has been unsupported for years now what took you so long you will definitely have your work cut out for you here...as you'll also need to upgrade SQL server more than likely, and maybe even the os of the server below is what an old lab of mine looks like (version 1610) after I triggered a sync, so in this case you can see that it can upgrade to 1710 (n+3) so that was... 1610 (n) 1702 1706 1710 based on this I'll guess that you can do the following... 1606 (n) 1610 1702 1706 (n+3) 1710 which would mean that you could theoretically upgrade from 1606 to CM2006 like so 1606>1706>1806>1906>2006
-
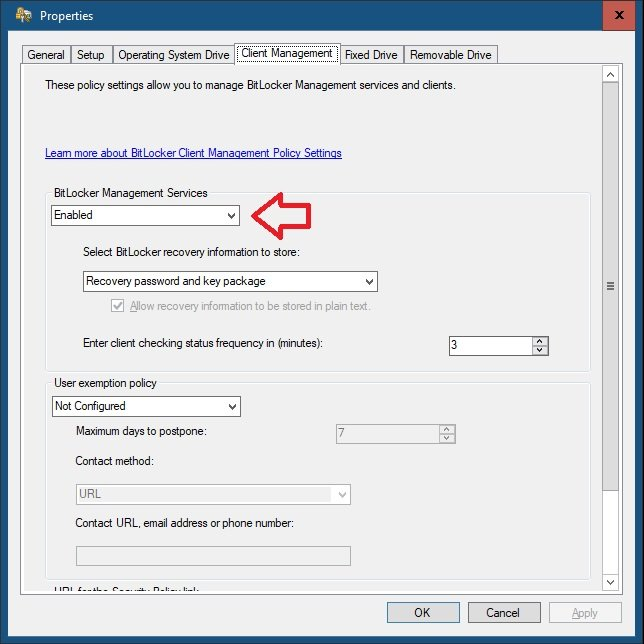
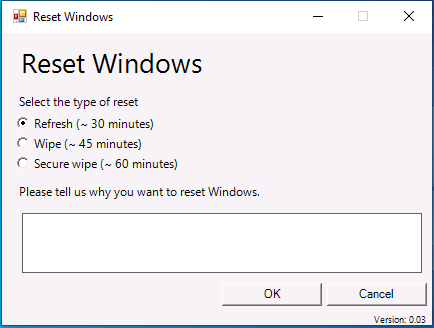
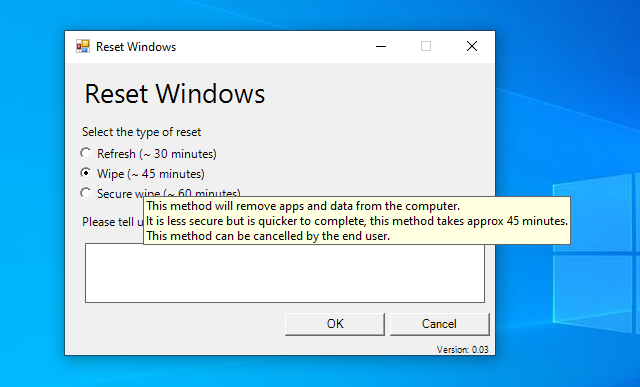
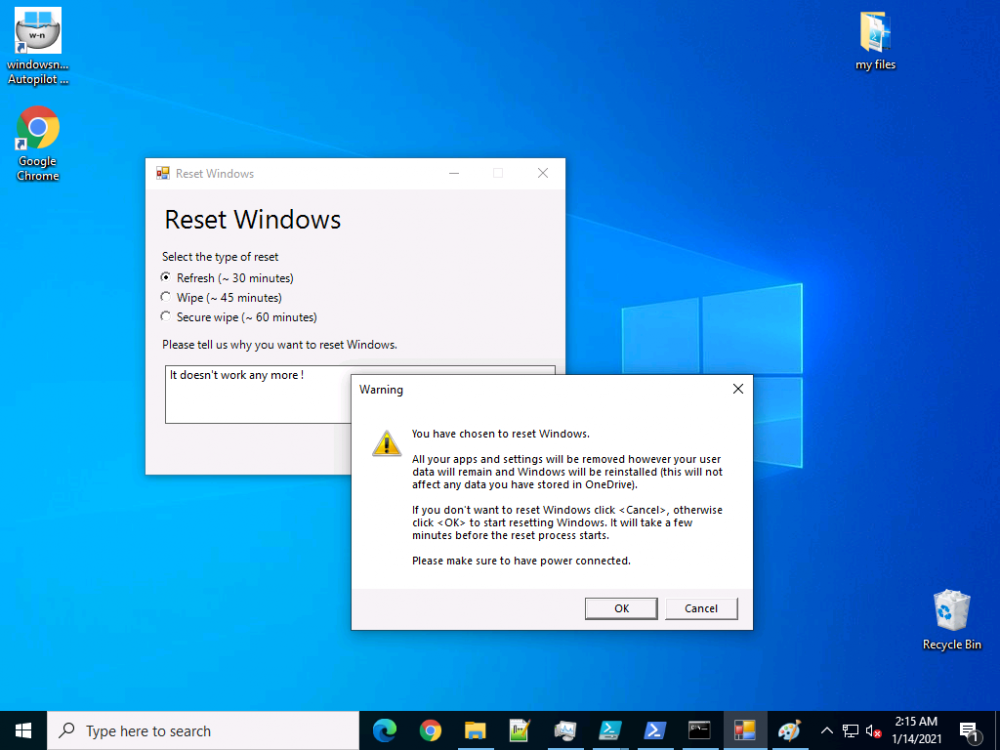
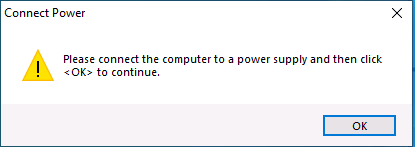
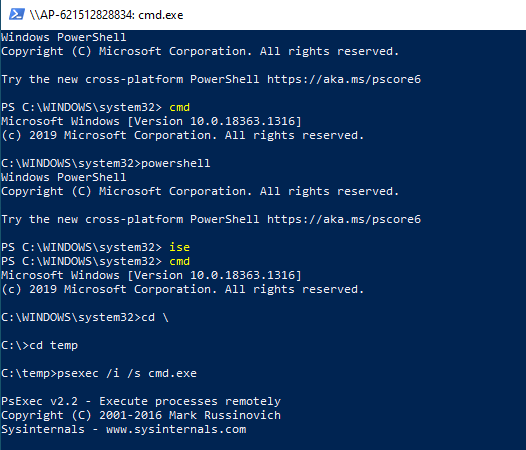
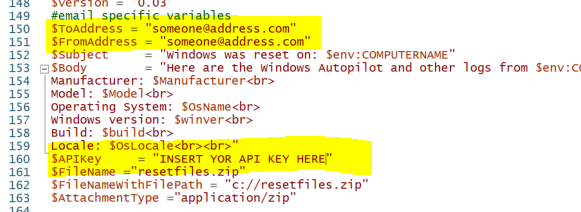
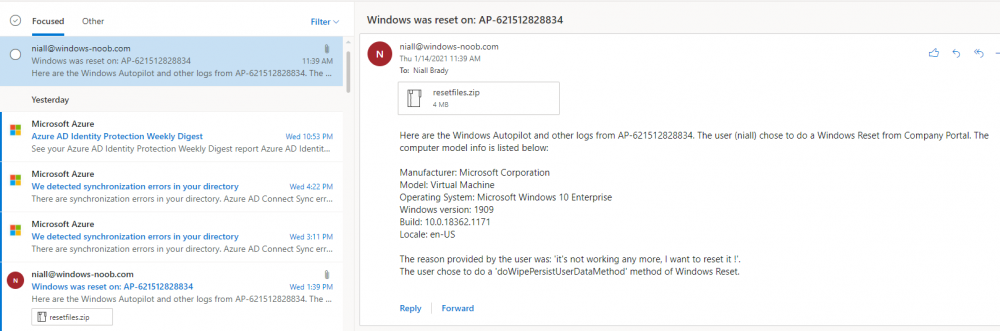
Introduction In a previous blog post I explained how you could use the SendGrid resource in Azure to send emails, and with a PowerShell script create an Intune app to give end users additional options when resetting their Windows Autopilot provisioned pc. This app would gather the Autopilot diagnostic logs (and other relevant logs) and send an email to your support inbox prior to resetting the pc. This was a very popular post so I updated the code to add some new features and to give more information to the end user. So let's take a look at the changes. New reset option In the new version (version .003) there's an additional reset option called Refresh, it's based on the doWipePersistUserData option here and this allows user account and data to be retained during the reset. In addition, I've added approximate estimations of how long each reset will take (I might adjust these later on with better estimations), this gives the end user a good idea of which option might be best for them. Tooltips I've added tooltips throughout the tool so if you hover the mouse over an option you'll get details about what it offers. You can customize the content of the tooltips in this section of the reset-windows.ps1 PowerShell script. Updated messages I've modified the messages to make them clearer to the end user. Below is one example. Check for Power The script now checks if a power source is connected, and prompts the end user to connect power if not. This check will only occur if the computer is not a virtual machine. Testing the script To test the script, you can use psexec to launch a cmd prompt in SYSTEM context. After doing that, you can launch the reset-windows.ps1 PowerShell script to see how it works after your changes. psexec /i /s cmd.exe and below I'm launching the script using SYSTEM context Don't forget to configure the to/from address and API key here After resetting, the email is sent and this is what it looks like Download the files Ok now you've seen the changes, give it a try ! follow the instructions in the previous part and use the updated script here. Note: you must be logged on to windows-noob.com to download scripts. reset-windows_ver_003.zip cheers ! niall
-
I imported your task sequence but that was as far as i got today, i have the day off tomorrow so i'll try and look into it, but first things first, why are you capturing an image in the first place, that's old school (now), most people just push out vanilla wim images and add apps in the task sequence
-

Remove Built in Apps from 20H2
anyweb replied to kesh's topic in System Center Configuration Manager (Current Branch)
what does the removeapps log file tell you, it's in c:\windows\temp (or the smstslog folder) -
ok thanks are there any odd ascii characters in that password ? can you please share a screenshot of your join domain step, i've contacted Microsoft PG and they don't believe there's any restrictions on password length, the join domain step should even accept 500 characters... i definitely need the log file from a failing domain join to get more understanding of this