-
Posts
9257 -
Joined
-
Last visited
-
Days Won
371
Everything posted by anyweb
-

Install drivers via task sequence
anyweb replied to kesh's topic in System Center Configuration Manager (Current Branch)
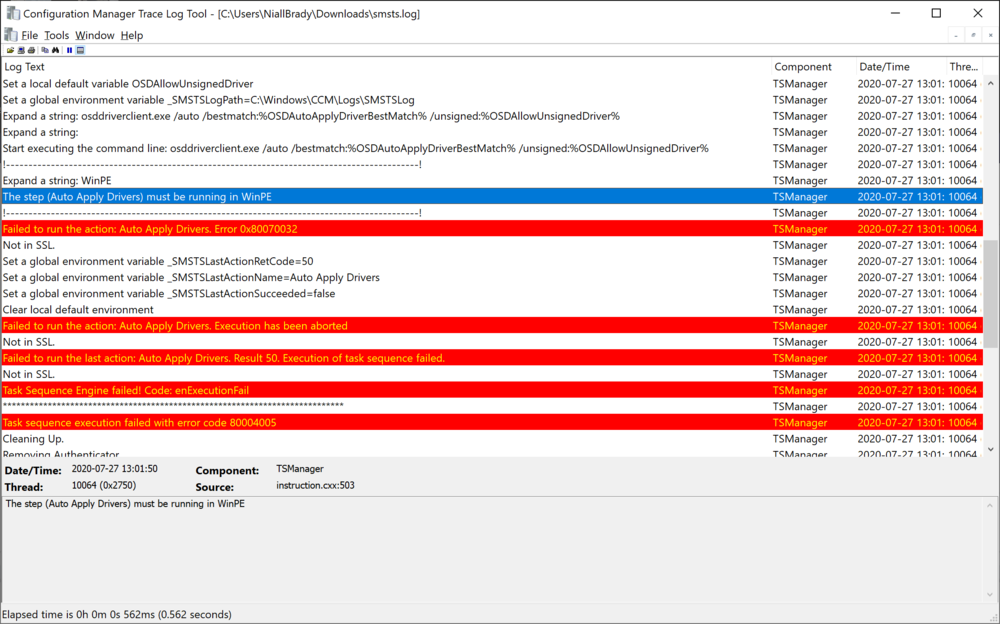
the 00000032 error translates to The process cannot access the file because it is being used by another process. Source: Windows ----- but the true error 80070032 from your smsts.log is The request is not supported. Source: Windows ----- and the real reason for that is revealed in the text above that, you are trying to install these drivers in Windows and it needs to do it in the WinPE phase you should probably convert the driver packages to apps and deploy them as applications to the affected computers (in Windows) -
did you follow the guide 100% as it works every time I've tried it, and I've implemented multiple labs successfully with this, I'd double check what you've entered and take a look at this blog post to see if it gives you some ideas of where you may have gone wrong.
-
I will do up a guide for installing the smoothwall VM soon, and thanks for the thanks, as regards the scripts, all of them are available for download for any logged in member of windows-noob.com if you encounter any missing script please point me to it and i'll fix it cheers niall
-

Management Point issue
anyweb replied to SHASHIDUBEY01's topic in System Center Configuration Manager (Current Branch)
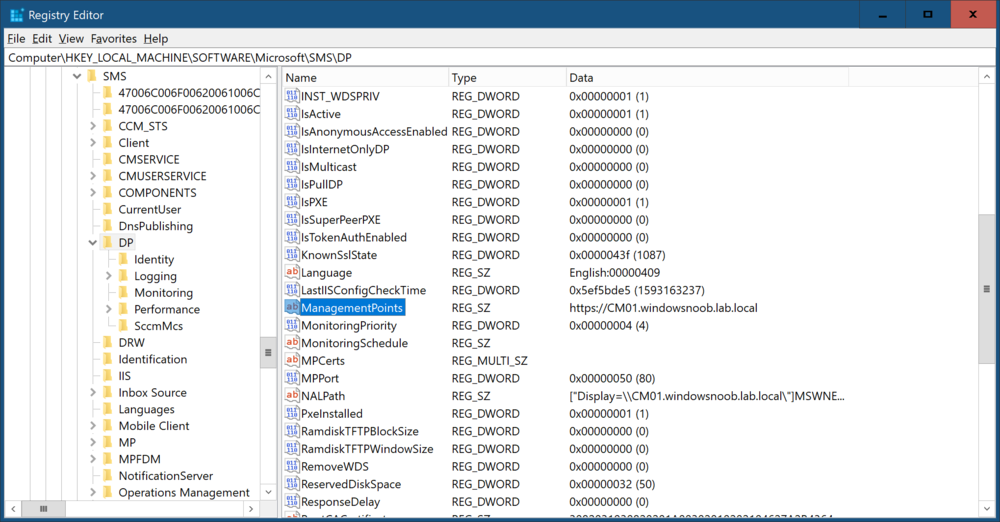
You could try hiring a consultant to remote in and troubleshoot it for you ? I'm on vacation now so don't have that much time to troubleshoot problems, also, have you taken a look at https://docs.microsoft.com/en-us/mem/configmgr/core/servers/deploy/configure/boundary-groups#fallback in WinPE, the client gets the list of possible MPs from a regkey that is set on the Distribution Point HKLM\Software\Microsoft\SMS\DP\ManagementPoints This key contains information about which MPs are available and in what order it will try to reach them. That order is determined by the order in which you installed the management points...You can change this key (on the distribution point) but it will be overwritten again soon by ConfigMgr. One workaround is to either run a schedule task that sets the "correct" value you want or use Configuration Items to set it instead... -
As the old adage goes: fail to prepare, prepare to fail. It’s the perfect description for backup yet to this day so many companies don’t have an adequate backup & disaster strategy in place for when the worst-case scenario happens. Just how well are you protecting your vital data? The Backup Bible, a free eBook from Altaro, guides you through the stages of preparing for, responding to, and recovering from a substantial data loss event, which can otherwise be disastrous for a company of any size. This eBook is the first installment of a 3-part series comprising the complete guide to data protection. It covers how to get started with disaster recovery planning; how to set recovery objectives and loss tolerances; how to translate your business plan into a technically oriented outlook; how to create a customized agenda for obtaining key stakeholder support; and the essentials to setting up a critical backup checklist. The second and third parts in the series will be released later this year but by downloading the first part, you’ll automatically receive the other eBooks in your inbox as soon as they become available! Whether you’re just starting to put together a backup and disaster strategy or you want to make sure your current plan is up to scratch, every IT admin needs to read The Backup Bible. Download your free copy today
-
I recently did a presentation for a Belgian User Group where I talked about a bunch of cool features in Microsoft Endpoint Manager like Tenant Attach, the ability to install applications, run scripts, use CMPivot, cloud OSD and more. Details Here are the details about the session 20h30 – 21h15: What’s new with cloud features in Microsoft Endpoint Configuration Manager Technical Preview by Niall C. Brady (Microsoft MVP Enterprise Mobility + windowsnoob.com). In this session you’ll get to see new Tenant attach features coming soon to Microsoft Endpoint Manager, Configuration Manager. These features are already available to try out in the Technical Preview releases. You’ll see how to install applications from the admin center, what the device timeline is and how to use it, CMPivot actions, Run scripts. In addition, you’ll look at other cloud friendly features such as VPN boundary type, Task sequence media support for cloud-based content. Downloads You can download the PowerPoint I used and watch a recording of the presentation in full below. I demo some cool features so I’d recommend you watch it in full. ppt – A look at the new cloud features in Configuration Manager Technical Preview video – https://1drv.ms/u/s!ApUuxMbRp9Jge_z66VXDKbnl0AU?e=csDRN7 cheers niall
-

Side by Side Migration
anyweb replied to DJ2016's topic in System Center Configuration Manager (Current Branch)
you can always upgrade the OS and SQL using an inplace upgrade, and that's the method I would choose and have done in the past. You need to get SCCM up to the latest version though before upgrading the operating system, here are my old notes and this does not include the operating system upgrade (which you can do after upgrading SCCM/SQL) -

Management Point issue
anyweb replied to SHASHIDUBEY01's topic in System Center Configuration Manager (Current Branch)
I think you are confusing application download and sending/receiving machine policy or state messages to the management point, i assume you have a local distribution point that resides in the IP Address range boundary that this computer is being image in, is that correct ? is the application in question also on this local DP ? -

Side by Side Migration
anyweb replied to DJ2016's topic in System Center Configuration Manager (Current Branch)
first things first why do you want to setup a new site maybe there's a better option like upgrade your existing infrastructure to Current Branch. -
did you install CM2002 in the slow ring or fast ring ? have you seen any update appear in updates and servicing for PXE boot issues (amongst other things) ?
-

Management Point issue
anyweb replied to SHASHIDUBEY01's topic in System Center Configuration Manager (Current Branch)
thanks, does that ip range over lap with any other subnet (as Garth already mentioned) ? -
if you are using https then are you sure you have no issues with your certs ? for example on your issuingCA run pkiview.msc and verify everything looks healthy as this can impact PXE booting.
-
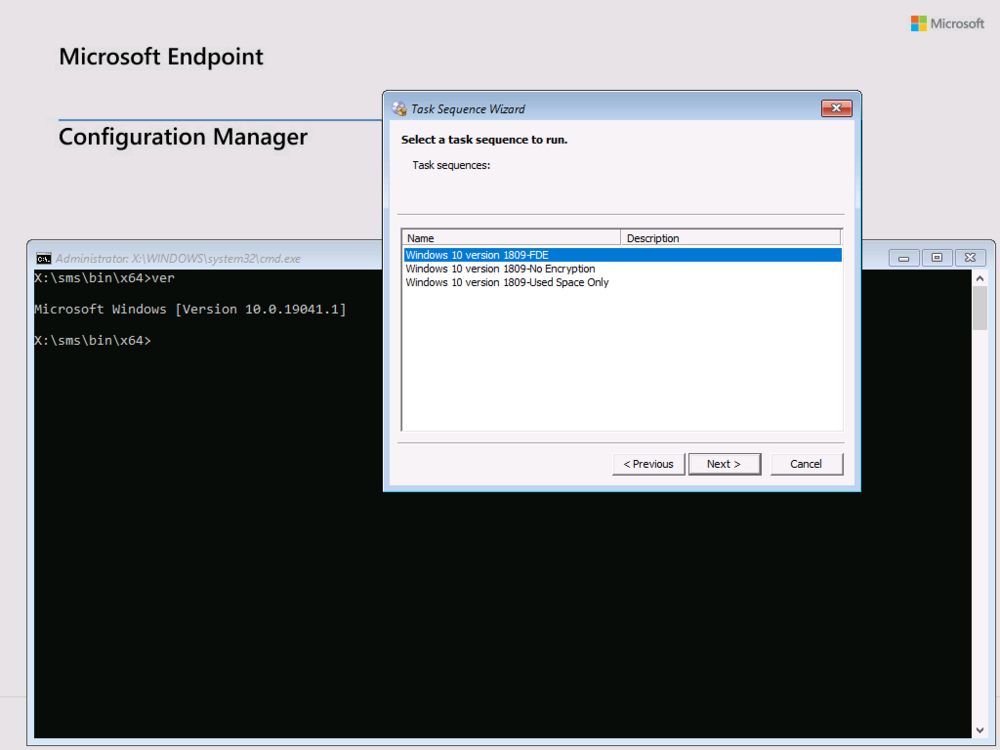
so i uninstalled both my Windows ADK's, rebooted, downloaded and installed both for ADK 2004 and rebooted, then reloaded my boot images with the new adk then tested pxe, works fine...
-
and the boot image is definitely distributed to your DP with the right source version ? i'm updating my lab to adk 2004 now....
-
very odd, i don't have adk 2004 in my cm2002 lab but i can upgrade it this evening to observe the behaviour did you verify from the boot package Id that it's pulling down the boot image you set the settings on ?
-
are you sure you upgraded Windows ADK properly then ? there are two components to it this time...



.thumb.png.fb1e761ef46559e3e40c344c8f9fe25e.png)