-
Posts
9255 -
Joined
-
Last visited
-
Days Won
370
Everything posted by anyweb
-
personally I think those days are over and that it's better to deploy an up to date ISO/WIM of the latest OS version of Windows 11 available, how will you manage your clients ? how do you intend to get an 'image' on these clients ? will you use Windows Autopilot ? without knowing more it's hard to advise
-

Migrate to the cloud - Part 1. Setup
anyweb replied to anyweb's topic in System Center Configuration Manager (Current Branch)
hi @shintest, i'm working on it just now so plan on releasing yet another release soon, please stay tuned ! -
- 14 replies
-
in the blog post you'll see it's deployed to 'autopilot users' that can be whatever users you want, it's up to you who get's this behaviour (or not)
- 14 replies
-
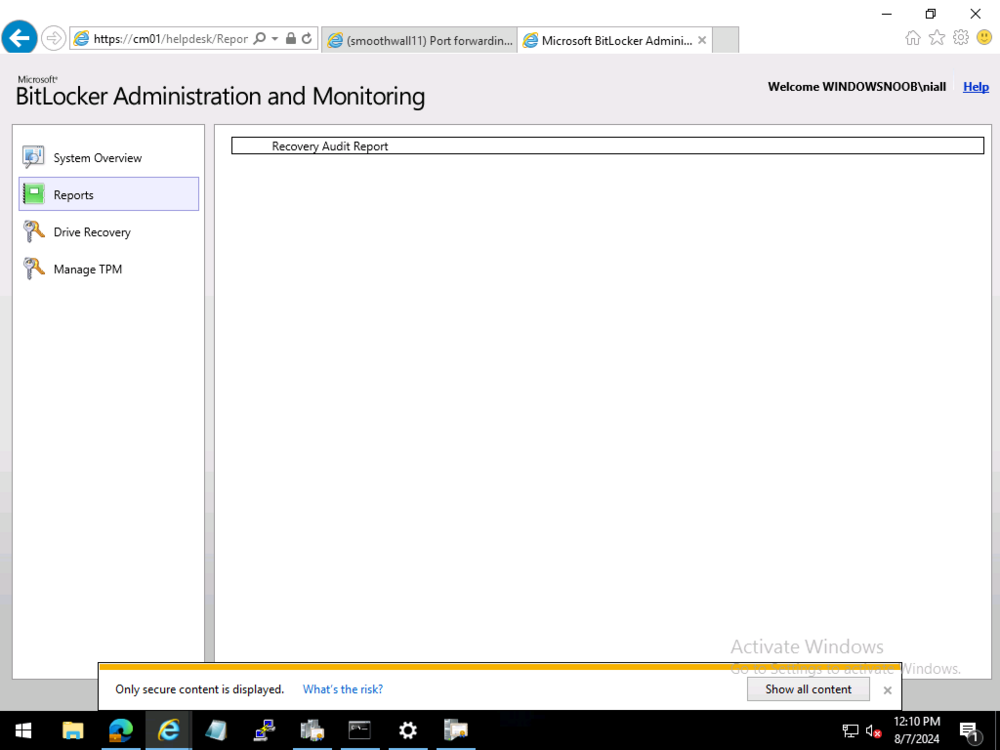
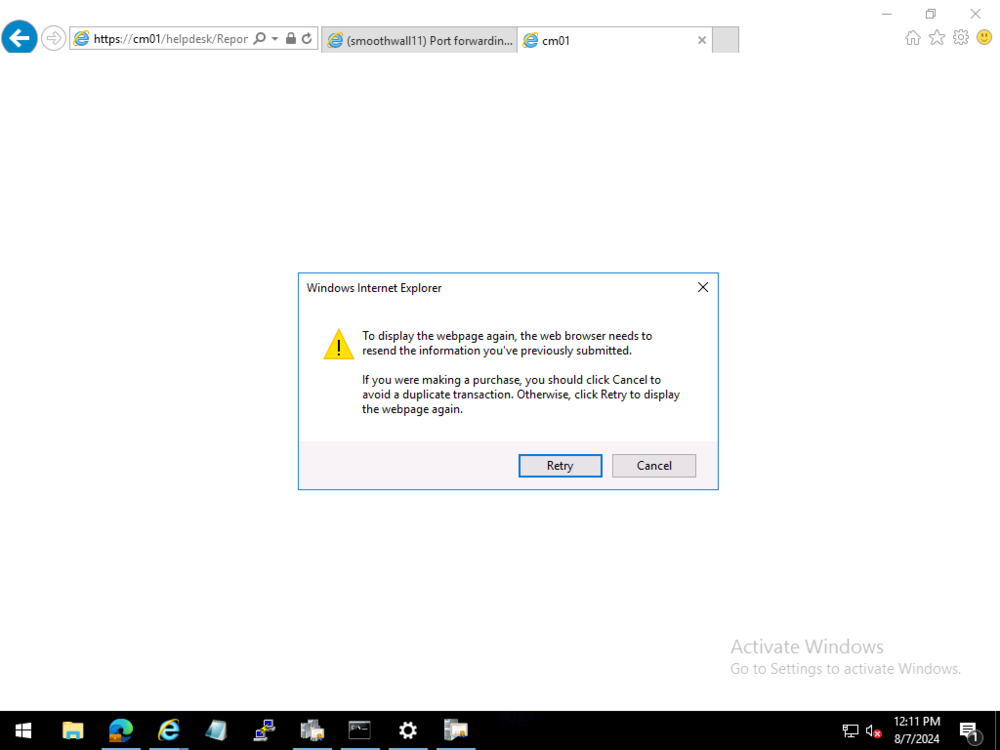
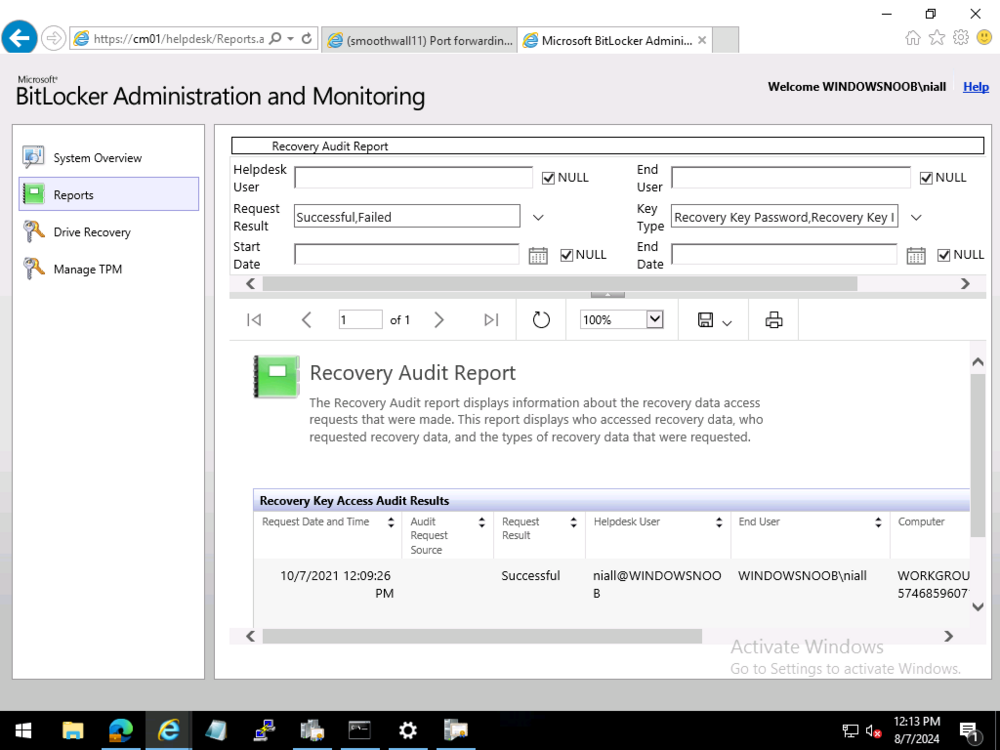
ok sorry for the delay in getting to the bottom of this, but after our Teams meeting I have a better understanding of your problem... first of all, in SCCM 2403 in my lab, i also do not see the Recovery Audit Report, and that is intentional as that report was moved out of SCCM in version 2002 see here > https://learn.microsoft.com/en-us/mem/configmgr/protect/deploy-use/bitlocker/view-reports#bkmk-audit and > https://www.reddit.com/r/SCCM/comments/pot0qu/bitlocker_management_recovery_audit_report_missing/?rdt=38888 so now that we know it shouldn't show up in SCCM versions greater than 2002, where do you find that report now ? the answer is below so go to your BitLocker Administration and Monitoring Website and click the Recovery Audit link, if that does nothing at all, then maybe we've found an issue. In my Technical Preview lab (2405) it does nothing. In my Current Branch 2403 lab, it does nothing in Edge, Chrome, Firefox, it looks like it trys but nada. So I tried IE. yeah I still have that installed on this server, and it prompted me with this > notice the 'only secure content is displayed' message ? after clicking Show all content I get this at this point, clicking Cancel, shows the actual report ! so i think this could be a bug, or at least an annoyance or a web browser setting that we need to 'change' to read the reports, i'll ping the Microsoft Product group and see what they say about it, if they reply i'll post back here cheers niall
-
did you look at part 2 of this blog series ? it's all there
- 14 replies
-
share the logs with me and i'll take a look are you sure you deployed this to the right group ?
- 14 replies
-

Server 2022 Network not Reconnecting after Restart
anyweb replied to ETx13's topic in Windows Server General
great to hear it's working now ? -

SCCM CB and Bitlocker
anyweb replied to wanderer's topic in System Center Configuration Manager (Current Branch)
see here, i explain how this happens (after 10:28...) and how to resolve it (after 13:00) -

Server 2022 Network not Reconnecting after Restart
anyweb replied to ETx13's topic in Windows Server General
i'm guessing it's your NIC (network) drivers, what are they shown as in device manager ? have you tried installing the latest drivers+bios version from dell ? -

SCCM 2403 and MDT and UDI Issue
anyweb replied to keywan's topic in System Center Configuration Manager (Current Branch)
thanks for the update @keywan -
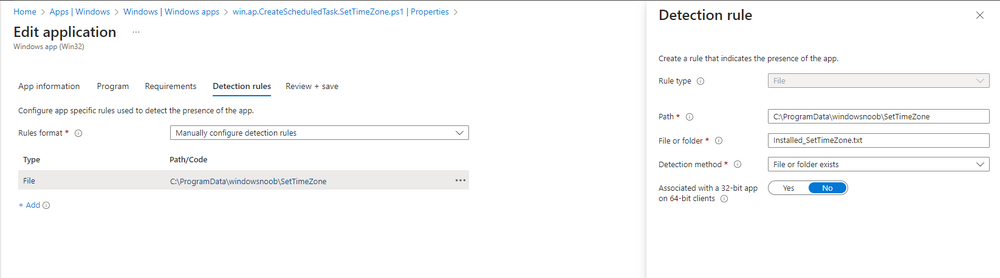
i tested it on an already enrolled device (not preprovisioned) and the log file is below, if you want it to detect your devices as preprovisioned then it'll need the whiteglove reg keys created from this solution I've uploaded yet another copy with slight changes above. the files below are what's left after a successful installation and run. win.ap.CreateScheduledTask.SetTimeZone.log Installed_SetTimeZone.txt win.ap.SetTimeZone-GUI.log