-
Posts
9253 -
Joined
-
Last visited
-
Days Won
369
Everything posted by anyweb
-

C:\ drive Full
anyweb replied to nhottinger's topic in System Center Configuration Manager (Current Branch)
pls try it, those figure don't really add up at first glance... -

C:\ drive Full
anyweb replied to nhottinger's topic in System Center Configuration Manager (Current Branch)
and the remaining 90gb is ? i prefer treesizefree to be honest. -

C:\ drive Full
anyweb replied to nhottinger's topic in System Center Configuration Manager (Current Branch)
start looking at logs and temp files, use Treesizefree to get a graphical overview of the damage, probably sql logs hogging everything don't delete stuff without knowing what you are doing, SQL log files can be compacted, see here -

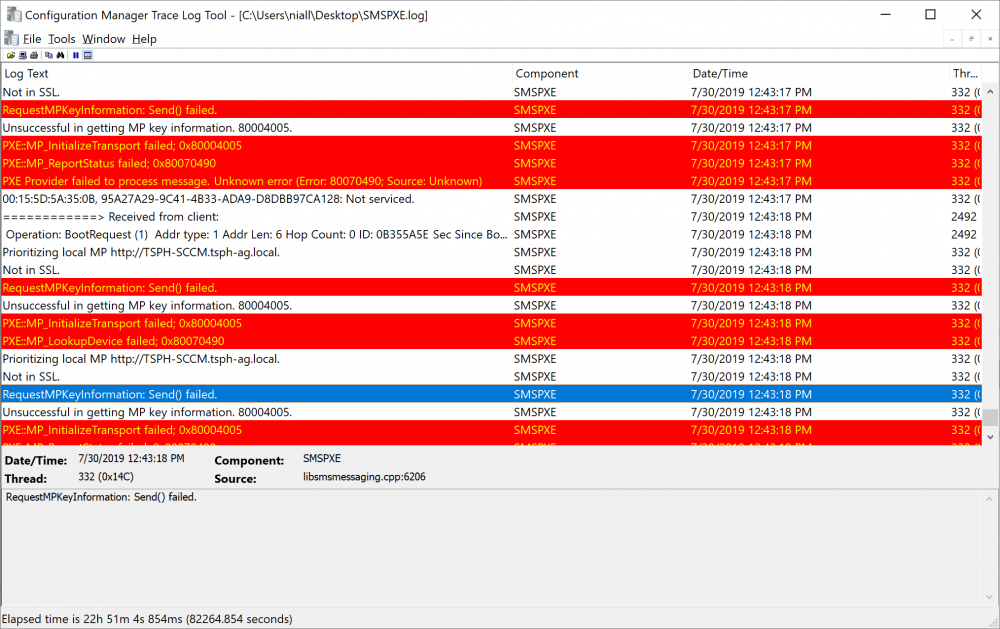
PXE Request Forwarding Possible
anyweb replied to YPCC's topic in System Center Configuration Manager (Current Branch)
try uninstalling the Management Point role, then reinstall it, then retest PXE on the dp. You've a lot of management point errors in that log RequestMPKeyInformation: Send() failed. -

PXE Request Forwarding Possible
anyweb replied to YPCC's topic in System Center Configuration Manager (Current Branch)
how are you boundaries setup ? did you configure two separate boundaries for these 2 offices ? -

MDT SCCM 1610 Integration
anyweb replied to terraj01's topic in System Center Configuration Manager (Current Branch)
looks like file permission errors, try running as administrator when doing the ConfigMgr MDT integration step. -
ok so you want to transfer data using USMT while in WinPE to a state store, you could use my prebuilt HTA to help with that, it even works with BitLocker if you have an MBAM back end. https://www.niallbrady.com/2016/05/17/introducing-the-windows-10-uefi-bitlocker-frontend-for-system-center-configuration-manager-current-branch/
-
it's just a lab so I did as follows:- ConfigMgr will always eat lots of RAM, so the more you have available for it, the better. CM01 = 16GB ram, 500gb hdd, 4x CPU, Hyper-v Gen 2 DC01 = 2GB ram, 128gb hdd, 4x CPU, Hyper-v Gen 2 Smoothwall = 256MBram, 128gb hdd, Hyper-v Gen 1
- 24 replies
-
hi and welcome i'd suggest you follow my guides index here and in particular focus on the following How can I install System Center Configuration Manager (Current Branch) version 1902 on Windows Server 2019 with SQL Server 2017 - Part 1 How can I install System Center Configuration Manager (Current Branch) version 1902 on Windows Server 2019 with SQL Server 2017 - Part 2 How can I install System Center Configuration Manager (Current Branch) version 1902 on Windows Server 2019 with SQL Server 2017 - Part 3 How can I install System Center Configuration Manager (Current Branch) version 1902 on Windows Server 2019 with SQL Server 2017 - Part 4 How can I install System Center Configuration Manager (Current Branch) version 1902 on Windows Server 2019 with SQL Server 2017 - Part 5 How can I install System Center Configuration Manager (Current Branch) version 1902 on Windows Server 2019 with SQL Server 2017 - Part 6 PKI and certificates are covered in this series.
-
you must be doing something different to my guide, as i've done the guide from start to finish over 6 times and every time it works 100% on both Server 2016 and Server 2019
-

Configuring BitLocker in Intune - Part 2. Automating Encryption
anyweb replied to anyweb's topic in Microsoft Intune
hi the msi attached to this blogpost is the latest i have available did you see my testing video here ? -
good point, thanks for sharing
-
ok well if you are not following my guide exactly then you may have issues, but at least you figured it out. I hope you understand that it's hard to support people when they don't follow my guide 100%.
-
where exactly are you seeing that is it being reset to it's default value, please explain. Are you following my guide 100% or are you doing your own thing ? if you are doing your own thing then I cannot guarantee your results. I've done this series 6 times using both Windows Server 2016 and Windows Server 2019 and have had zero issues with it.
-
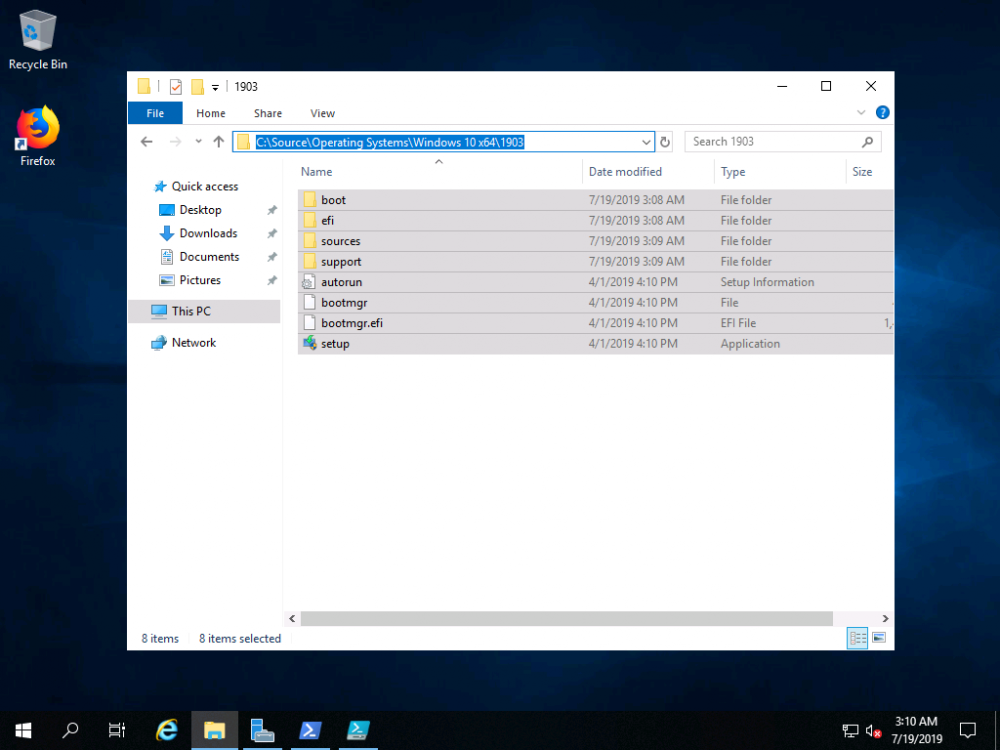
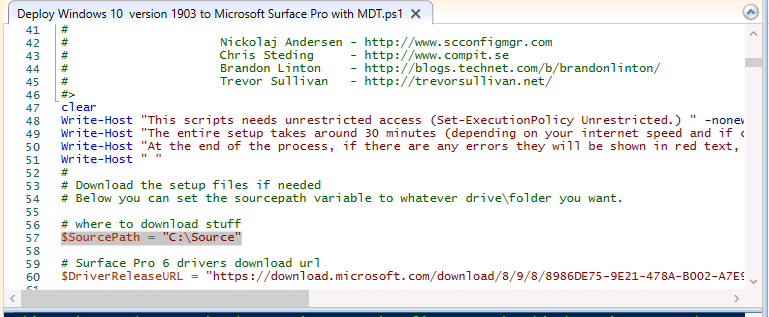
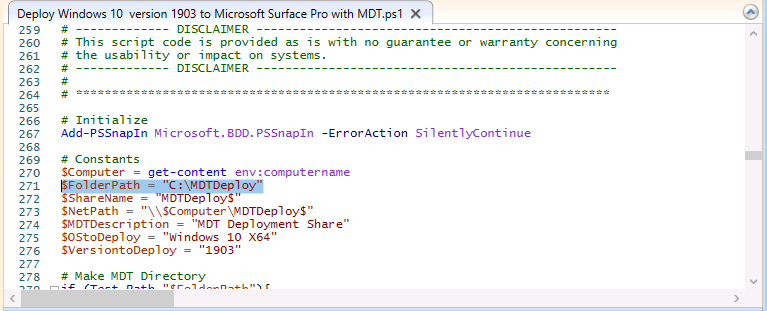
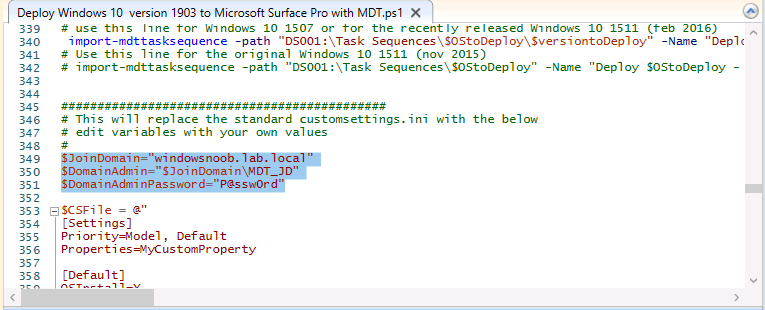
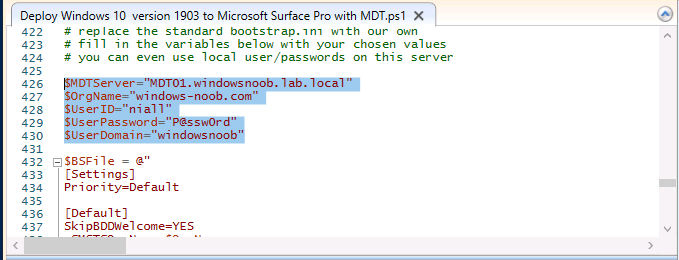
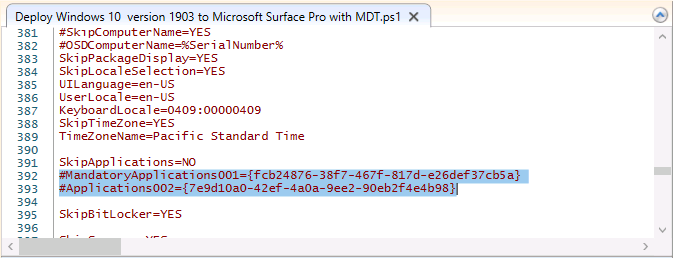
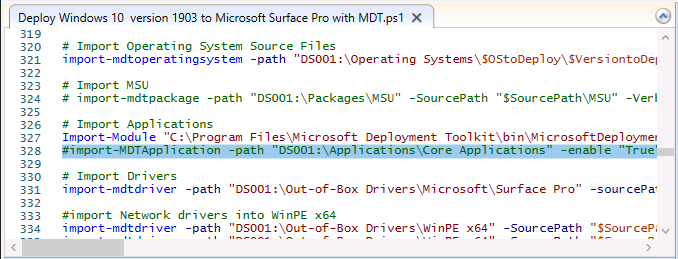
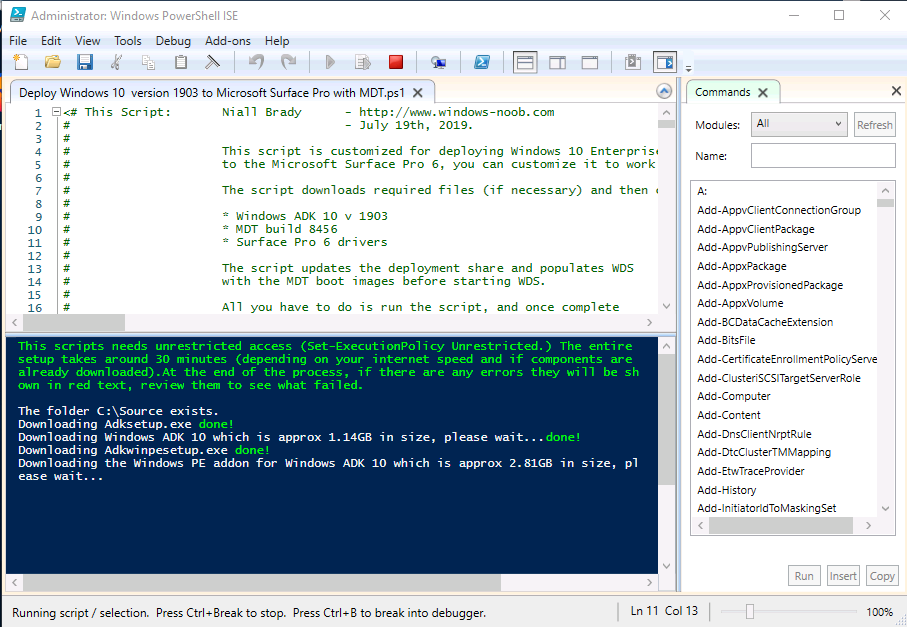
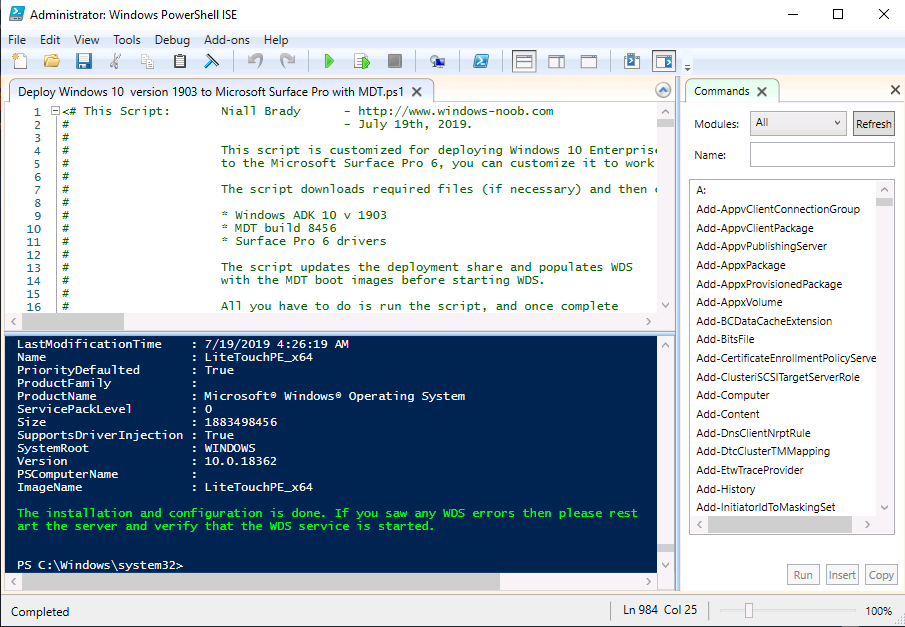
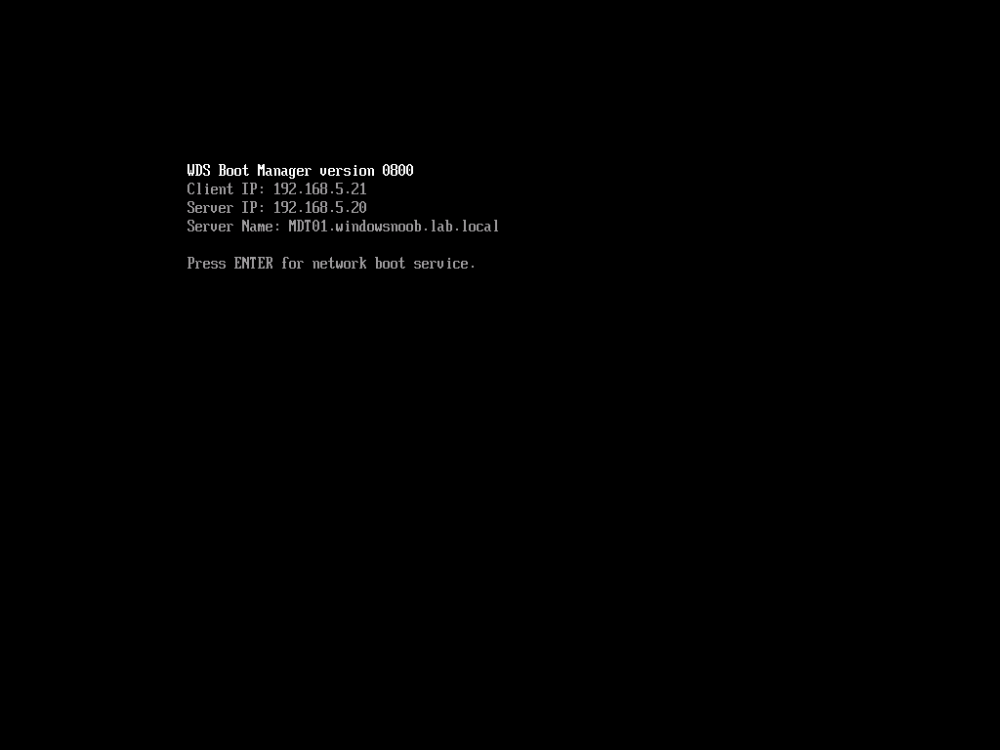
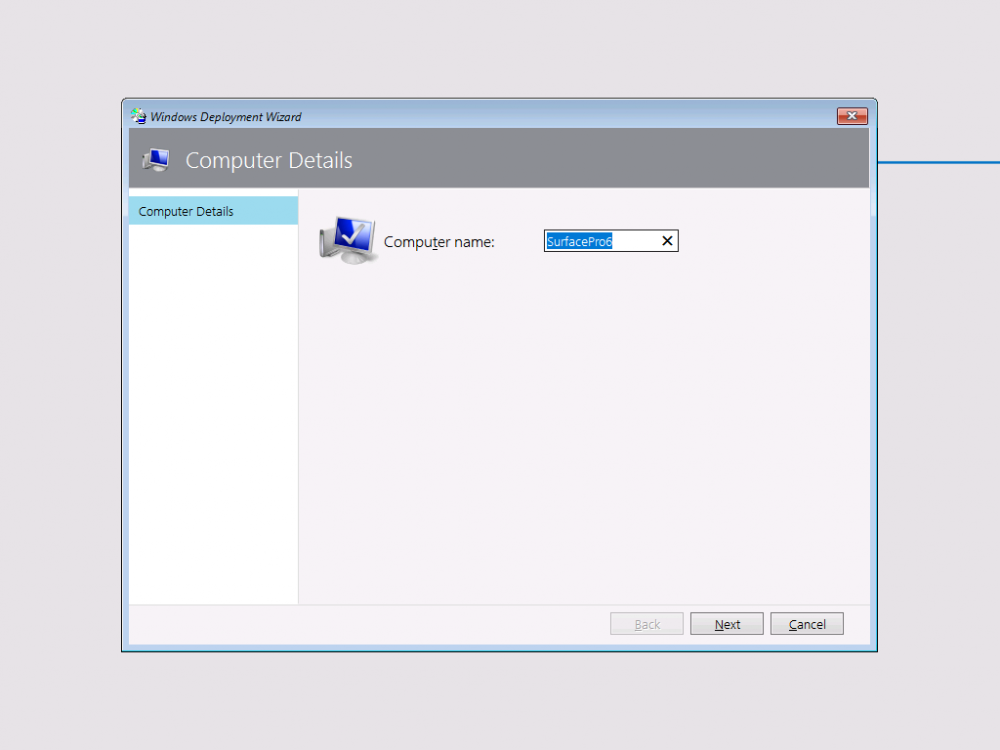
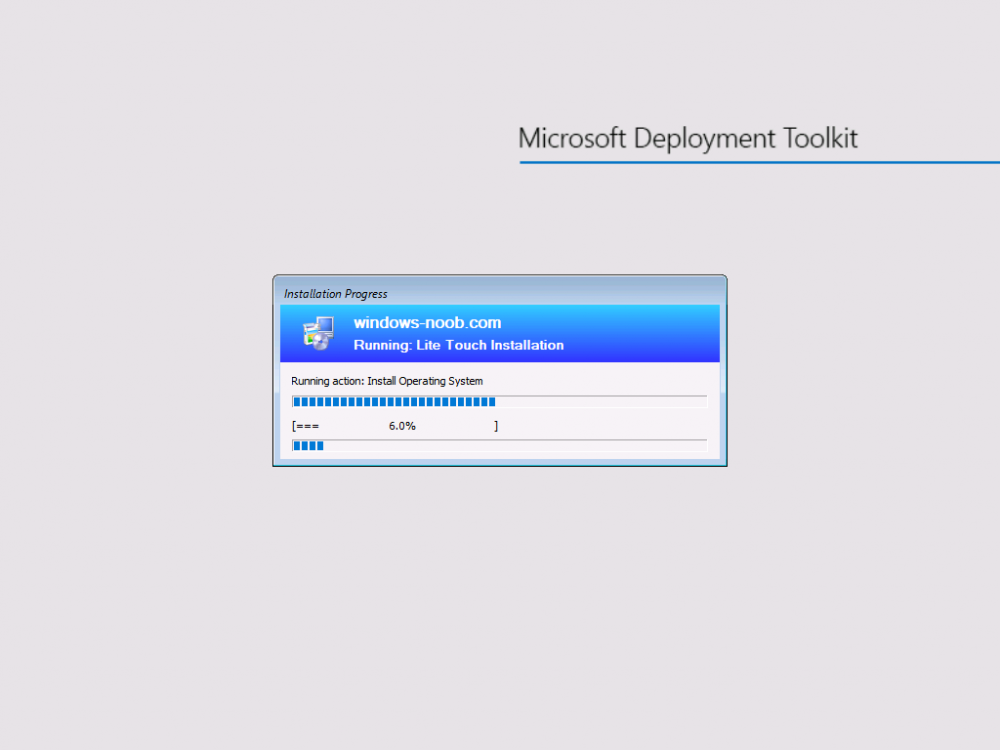
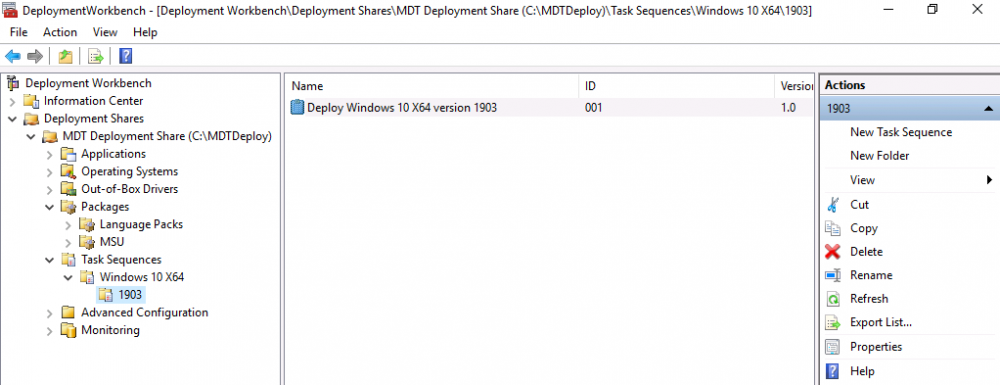
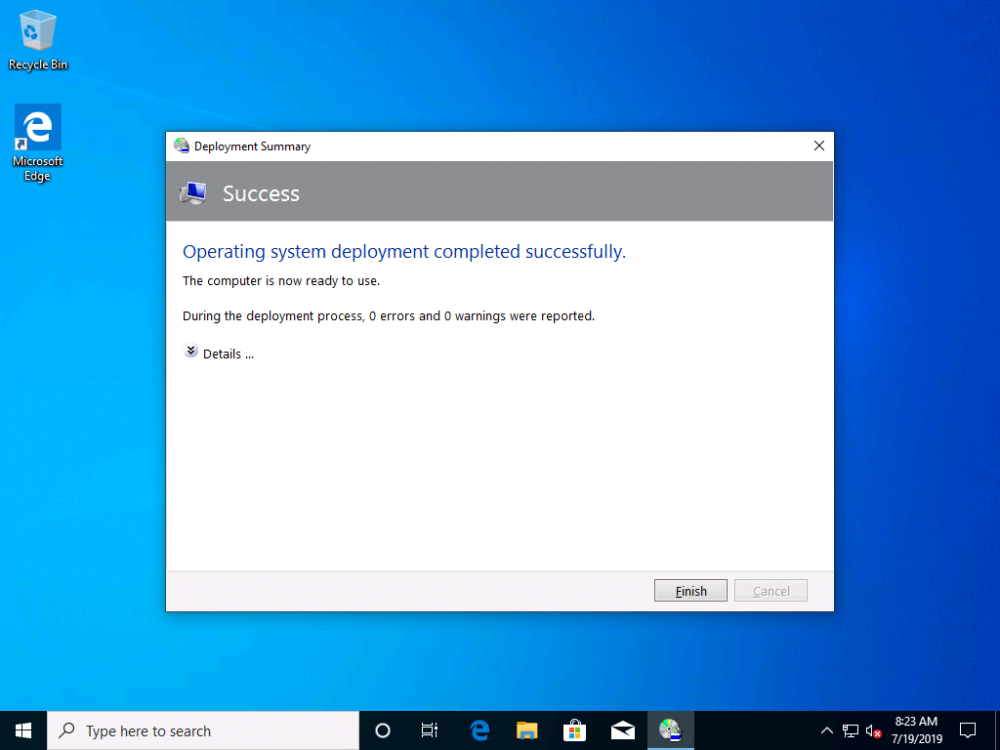
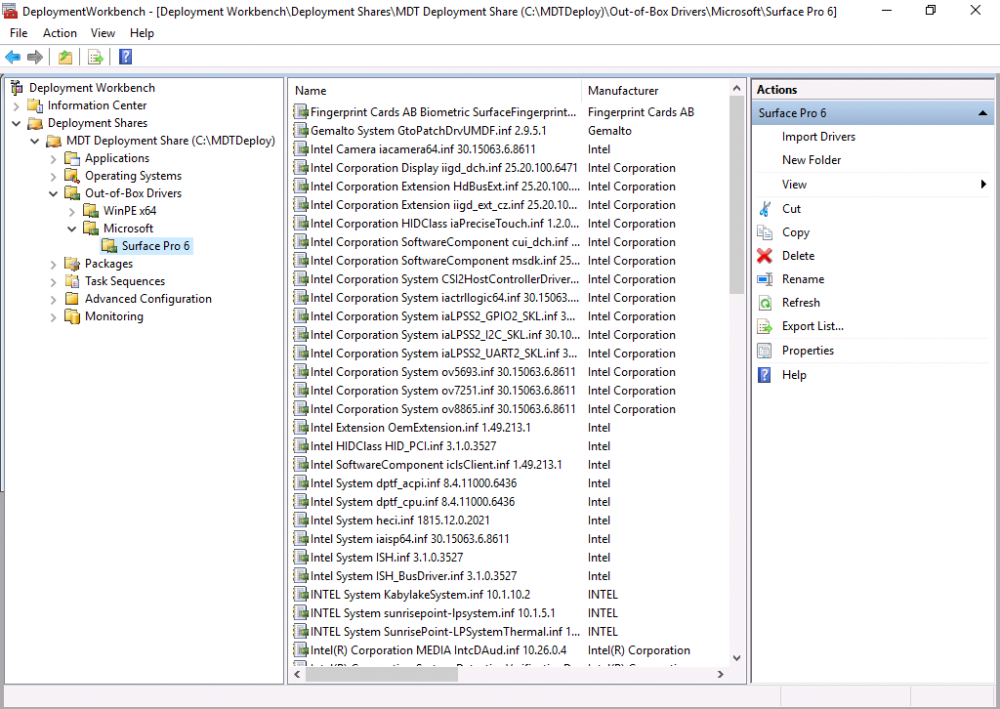
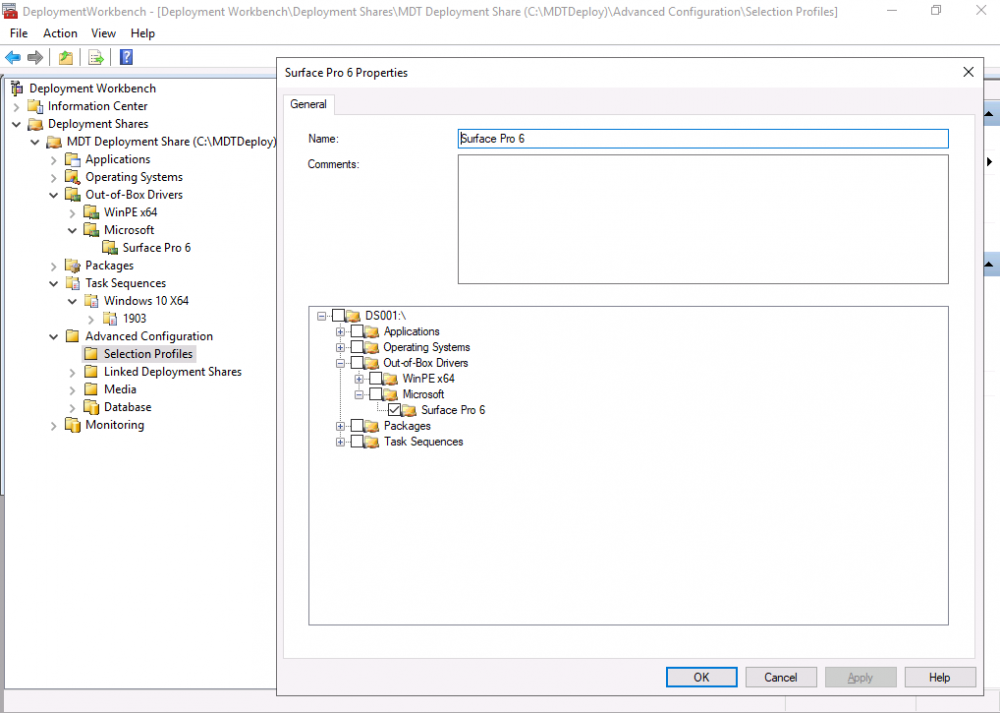
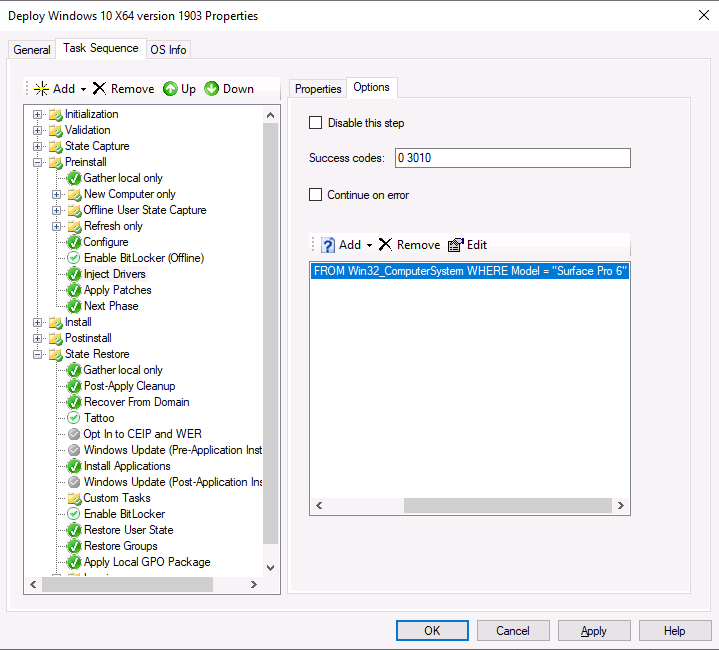
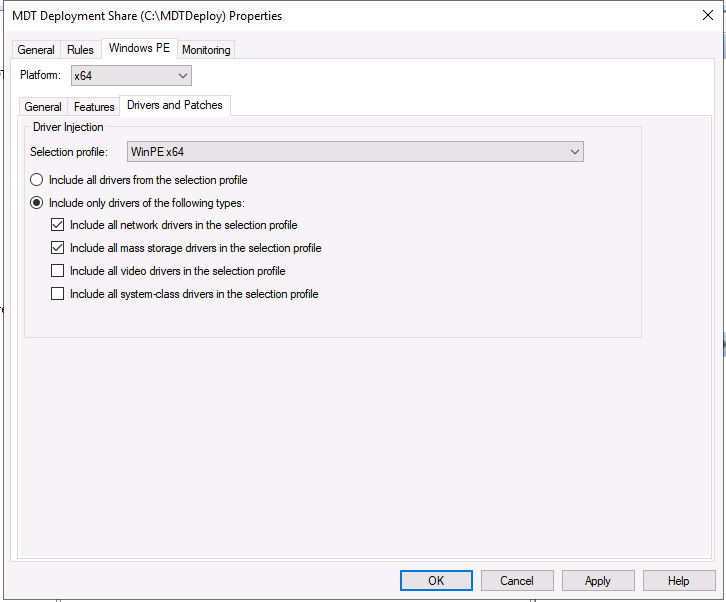
Introduction You are most likely familiar with the Microsoft Surface Pro 6 and the recently released version of Windows 10 version 1903 (May 2019 Update). Now you can automate the installation of Surface Pro 6 using PowerShell and MDT. This script has been written to allow you to automate the deployment Windows 10 version 1903 (May 2019 Update) using the latest available software including: Windows 10 x64 (version 1903) Microsoft Deployment Toolkit (MDT) build 8456 Latest available 2019 drivers for the Surface Pro 6 for Windows 10 version 1903 Windows 10 ADK (version 1903) Windows Server 2019 Note: This is fully automated, and as this does install a Windows Deployment Services server role hosting a boot image, you should modify the script accordingly and test it thoroughly in a lab first. This script is tailored for one thing only, deploying Windows 10 x64 version 1903 to the Microsoft Surface Pro 6 with all drivers loaded and MDT pre-configured. Download it and customize it to suit your needs for other hardware if you wish because what it does is pretty cool. This script performs the following actions:- Downloads and then Installs Windows ADK 10 (version 1903) if you have not done so already Downloads and then Installs MDT, if you have not done so already Downloads all required drivers for Microsoft Surface Pro6 if you have not done so already Imports the Windows 10 x64 (version 1903) operating system into MDT Imports the Microsoft Surface Pro drivers into MDT Creates Selection Profiles for Surface Pro 6 and WinPE x64 Creates a Deploy Windows 10 X64 version 1903 task sequence Edits the Deploy Windows 10 X64 version 1903 task sequence and adds an inject drivers step for Microsoft Surface Pro 6 Sets a WMI query for hardware detection for the Surface Pro 6 on the corresponding driver step Injects the Microsoft Surface Pro 6 network drivers into the LiteTouchPE_x64.wim Creates custom CustomSettings.ini and BootStrap.ini files Disables the X86 boot wim (as it is not needed for Surface Pro 6) Changes the Selection Profile for the X64 boot wim to use the WinPE x64 selection profile Installs the Windows Deployment Service role Configures the WDS role and adds the previously created LiteTouchPE_x64.wim Starts the WDS service so that you can PXE boot (UEFI network boot). All you have to do is provide a domain joined server (MDT01), then download the script below, modify some variables, then place certain files in the right place such as the Windows 10 x64 Enterprise (version 1903) media. Please ensure you have a working DHCP scope on your Active Directory domain controller, then PXE boot a Microsoft Surface Pro and sit back and enjoy the show. Step 1. Download the script The PowerShell script will do all the hard work for you, download it, unzip it and place it on the server that is designated to be the MDT server. Scripts.zip Step 2. Configure the variables in the script Once you have downloaded and extracted the script, you need to configure certain variables interspersed throughout the script. I'll highlight the ones you need to edit. The most important of them is the $SourcePath variable (line 57) as this decides where to get the content from and where to store it. This variable should point to a valid drive letter, the folder name will be created if it does not exist. The $FolderPath variable (line 271) specifies the MDT Deployment share root folder for example C:\MDTDeploy. There are other variables to configure, for joining the Domain (lines 349-351) and then you need to configure how you actually connect to the MDT server from WinPE (lines 426-430) Step 3. Copy the Windows 10 x64 (version 1903) operating system files Mount a Microsoft Windows 10 x64 Enterprise (version 1903) ISO and copy the contents to $SourcePath\Operating Systems\Windows 10 x64\1903 as shown below. Step 4. Optionally copy MDT, ADK 10, Surface Pro drivers This is an optional step. If you've already downloaded the above files then place them in the source folder, otherwise the script will automatically download them for you. Note: You do not have to do this as the script will download the content for you if it's not found. Step 5. Optionally copy your Applications to the respective folders This is an optional step. If you have apps like Office 365, copy them to their respective folders under Applications. If you do add any applications, you'll need to edit the corresponding section within the script for the CustomSettings.ini and replace the GUID for the App, these applications are remmed out with a #, as shown here (line 392-393) and in line 328 Step 6. Run the script On the server that will become your MDT server, start PowerShell ISE as Administrator. Click on the green triangle to run the script. This is how it looks while running... Below you can see the script has completed. Step 7. Deploy a Surface Pro 6 After the script is complete, you are ready to test deploying Windows 10 version 1903 (May 2019 Update) to a Microsoft Surface Pro 6. You can see that Windows Deployment Services is installed and that the ADK 1903 version of the MDT LiteTouch_X64 boot wim is already imported. This boot image also has the Surface Pro 6 network drivers added. After the Surface Pro 6 has PXE booted, you'll see the MDT computer Name screen, you can change that behavior in the UI itself (CustomSettings.ini on the Properties/Rules of the DeploymentShare) or automate it via the many methods available such as those that Mikael describes here. After clicking next the OS will get deployed. and after a while it's all complete. Step 8. Review the MDT Deployment Workbench After opening the Deployment Workbench, you can see the Deploy Windows 10 x64 version 1903 task sequence is created and in the task sequence you can see the inject drivers step that is customized with a wmi query for Surface Pro 6 drivers specific to the Surface Pro 6 are imported into MDT Surface Pro 6 specific selection profiles created drivers (network) are also added to the x64 boot image Troubleshooting If the script has issues starting WDS (and you see the error below) then restart the server, as you were asked to do at the end of the script ;-). If you cannot PXE boot, because WDS is not accepting connections (revealed by the PXE Response tab in WDS properties), then look for the following error in the scripts output: An error occurred while trying to execute the command. Error Code: 0x5 Error Description: Access is denied. If you see that error, then the user you are logged in as does not have sufficient permissions to configure WDS. To grant permissions to the Windows Deployment Server (MDT01) do as follows Open Active Directory Users and Computers. Right-click the OU where you are creating prestaged computer accounts, and then select Delegate Control. On the first screen of the wizard, click Next. Change the object type to include computers. Add the computer object of the Windows Deployment Services server, and then click Next. Select Create a Custom task to delegate. Select Only the following objects in the folder. Then select the Computer Objects check box, select Create selected objects in this folder, and click Next. In the Permissions box, select the Write all Properties check box, and click Finish. Next, open ADSIEdit.msc Browse to the Computer Account of the WDS Server. It will have a Child Object named something like "CN=MDT01-Remote-Installation-Services". The user that runs the the PowerShell script or the WDS Console needs Full Access permissions to this Child Object. Right click and choose Properties. Select the Security/Permissions tab and add the user/group in. Set them to have Full Permissions. Log out of the MDT Server and log back in again. AD replication may delay the result of this, but you should now no longer have Access Denied. Summary Automating the deployment of Windows 10 version 1903 (May 2019 Update) to the Microsoft Surface Pro 6 using PowerShell and MDT is easy when you know how.
- 1 reply
-
- 1
-