-
Posts
9182 -
Joined
-
Last visited
-
Days Won
366
Everything posted by anyweb
-
the script works for me every time in a lab, did you edit it in any way ?
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-

CB 1706 PXE boot
anyweb replied to khawkins's topic in System Center Configuration Manager (Current Branch)
the error above translates to " A network error interrupted the operation. Source: Windows ----- " do you get an ip in WinPE ? did you try adding network drivers for the hardware involved to your boot image ? this script will help you identify if you have missing drivers in the boot image and will inform you if so -
no problem, if you still have issues then please post the exact error message you get so we can try and help
-
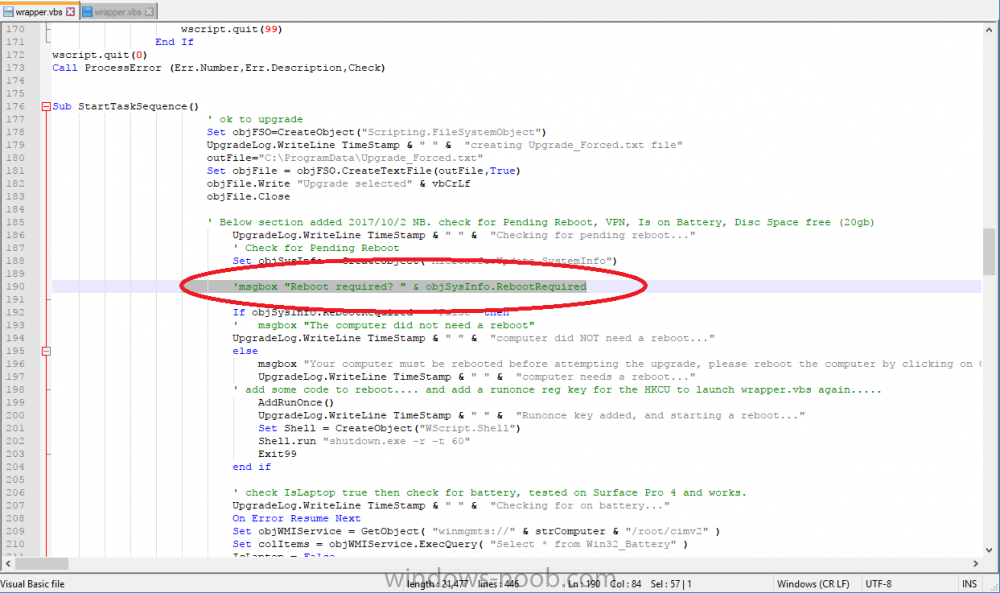
1. the 4 hours is to give the user time to finish their PowerPoint or meeting, and then start the upgrade with loads of time to spare, but at the same time to give them a sense of urgency 2. set them whatever way you want 3. VPN's can cause upgrade's to fail (lack of connection), hence the vpn check, it's better to do the upgrade in the office to force it to run quickly I open a powershell cmd prompt on a vm, and start the powershell start... command to kick off the hta, that's a manual process but it allows you to test the flow so that you are happy with it cheers niall
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
heh well good luck with that, if you want to manage servers then most people do that with SCCM, by installing the client agent on the servers to do tasks (application install, gathering data etc) and software update management, there's a whole bunch of guides here on windows-noob to get you started with that, here for example
-
hi and welcome, what is your goal here ? to manage a few desktops or image them, or what ?
-

Configuring BitLocker in Intune - Part 2. Automating Encryption
anyweb replied to anyweb's topic in Microsoft Intune
really ? it worked for me when I tested it, what does the log tell you ? -
it's documented here, have you seen this yet ? Trivial FTP (TFTP) Daemon: The Trivial FTP (TFTP) Daemon system service does not require a user name or password and is an integral part of Windows Deployment Services (WDS). The Trivial FTP Daemon service implements support for the TFTP protocol that's defined by the following RFCs: RFC 350: TFTP RFC 2347: Option extension RFC 2348: Block size option RFC 2349: Time-out interval and transfer size options Trivial File Transfer Protocol is designed to support diskless boot environments. TFTP Daemons listen on UDP port 69 but respond from a dynamically allocated high port. Therefore, enabling this port allows the TFTP service to receive incoming TFTP requests but doesn't allow the selected server to respond to those requests. You can't enable the selected server to respond to inbound TFTP requests unless the TFTP server is configured to respond from port 69. https://docs.microsoft.com/en-us/sccm/core/plan-design/hierarchy/ports
-
Great guide, thanks so much for making this available to everyone this resource is the best by far on the web. hi and thanks for your comments Do I need to amend the computer name and server name that's mentioned in the DeploymentConfigTemplate at all? not in my testing, but please verify first in a LAB I don't plan on using Config Manager for WSUS at the moment so should i still install the role? We currently already have a WSUS server which is looking after updates. if you don't intend to use SCCM for software updates, then you don't need to install WSUS. Is it best practice to use the default local SQL accounts for the SQL services or should I apply domain accounts for those services? I mentioned in a previous post about having to re-install Config Manager from scratch as the whole thing was a mess when I took it on, I have managed to uninstall most of the clients on the domain but as I will be using the same site names going forward as before am I likely to run into trouble after following this setup guide? Use SQL accounts that work with your enterprise, here are some tips, and as regards your current setup and installing configmgr again, i'd suggest you verify everything in a lab first, it's easy to do so.
-
the 0.0.0.0 is only for the vpn i tested with, you should customize that function to detect your own VPN solution, or just skip it
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
yeah there were some bug fixes on the scripts, but what is there now should do what it supposed to
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
once the threshold completes, it will close the HTA so yes, that is as per design, I initially wanted to move the window to the center of the screen and flash it on top of all other windows but didn't find a reliable way of doing it, and i'm not going to use third party tools to do so if you use teamviewer I can remote in and have a look and see what's wrong with yours...
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
when testing the HTA I copy the package to a virtual machine desktop, then cd to that folder, then start powershell, then start the powershell script from the powershell prompt, that should kick off the wrapper and launch the HTA, you can then close the hta or defer and the values should be updated in the registry, try multiple times and each time it's launched the value should decrease by 1
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
hi, I can't share it sorry, but I can give you an idea of what it contains, via these pointers *below*, you'll have to go and create one yourself for your Company cheers Niall <- Known software Incompatibilities Hardware requirements Preparation Required upgrade to the latest Windows 10 version 1709 What to do when the upgrade is completed Windows 10 features Incidents and issues
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
you just need to add the model to the model supported check, or rem out that group entirely and move it to the task sequence, it's up to you
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
please download the scripts again, i can see you are using an older version, and the version i have has improvements/corrections and does not have that issue
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
what do you mean it failed, do you get an error, if so what error and what functions did you add to the hta ?
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
I was just about to create a similar script and found this, great work. thanks, also, I just checked the script, seems fine, those commands you mention are simply to help 'test' or 'debug' the script they don't change the functionality, look again at it.. so was it indeed this or something else you are referring to ? cheers niall
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
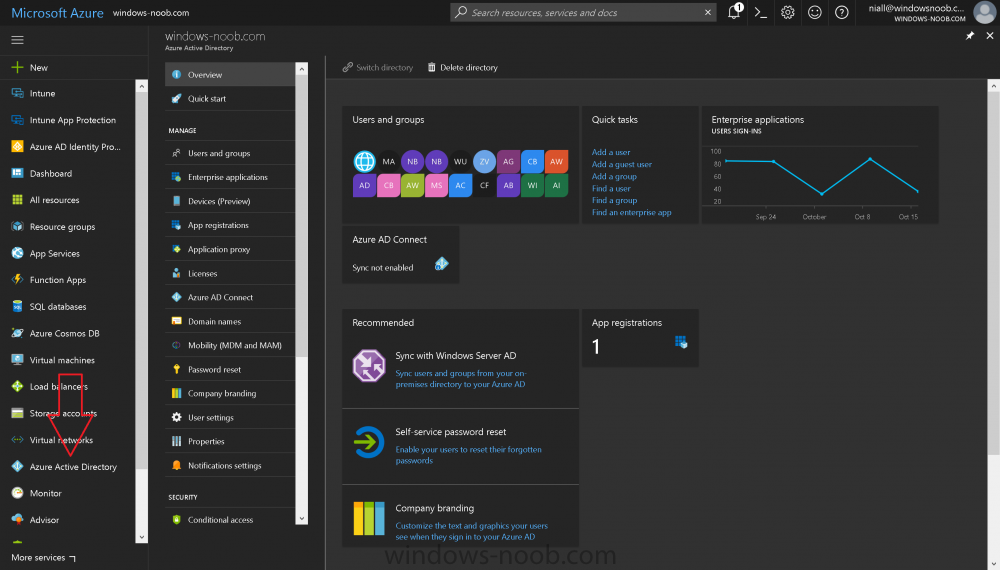
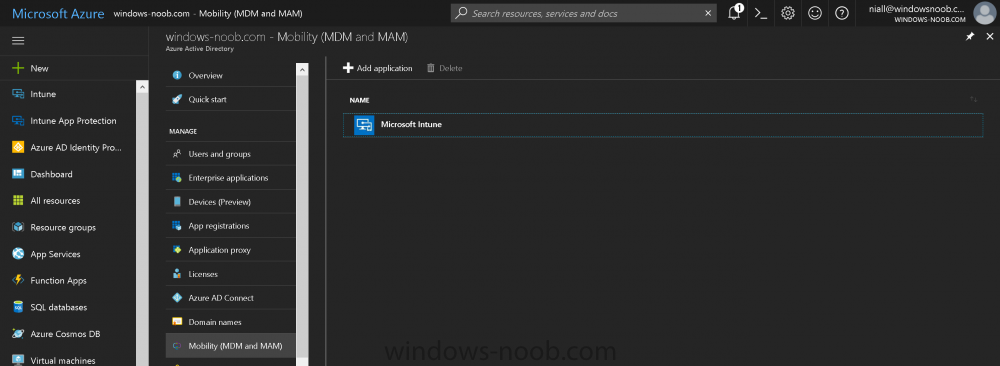
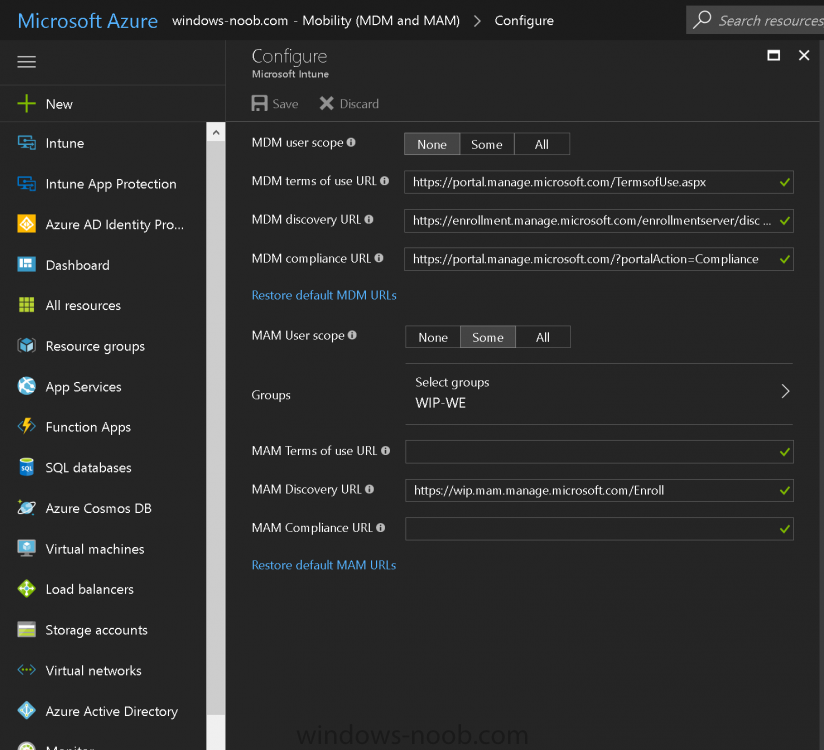
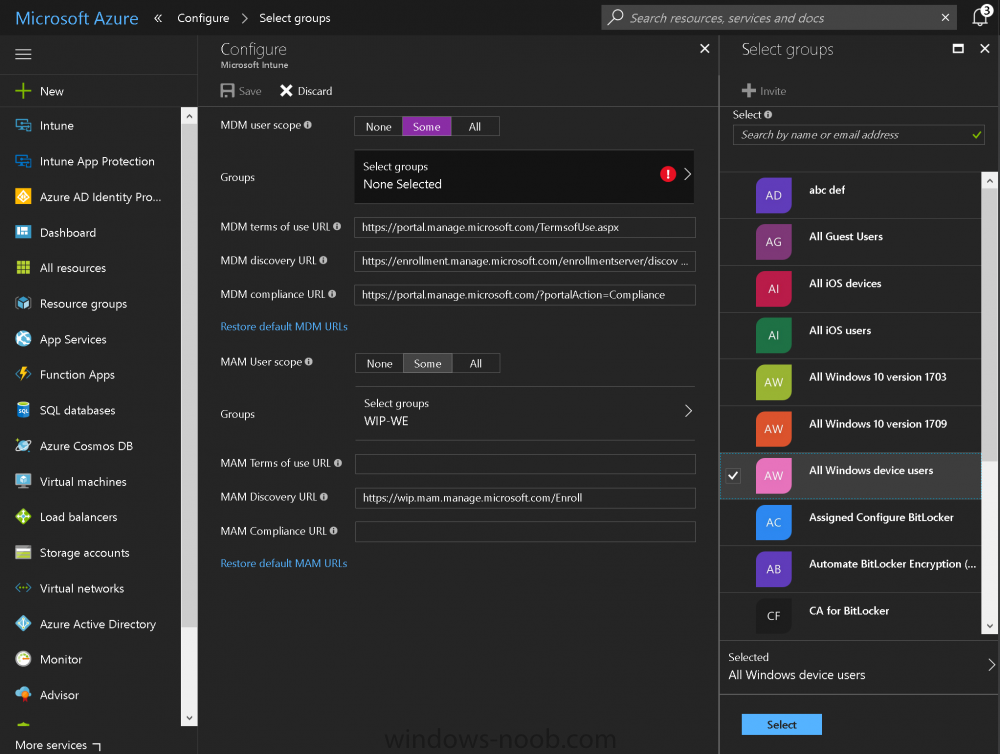
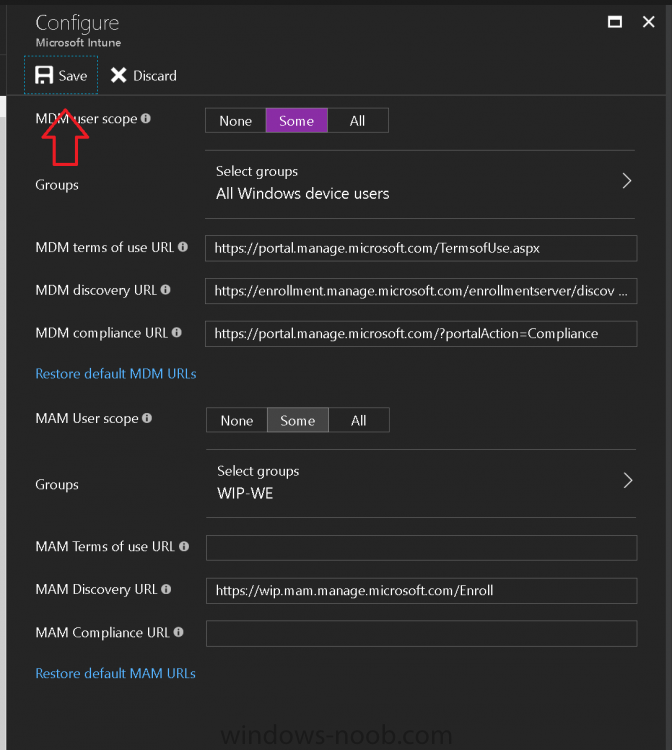
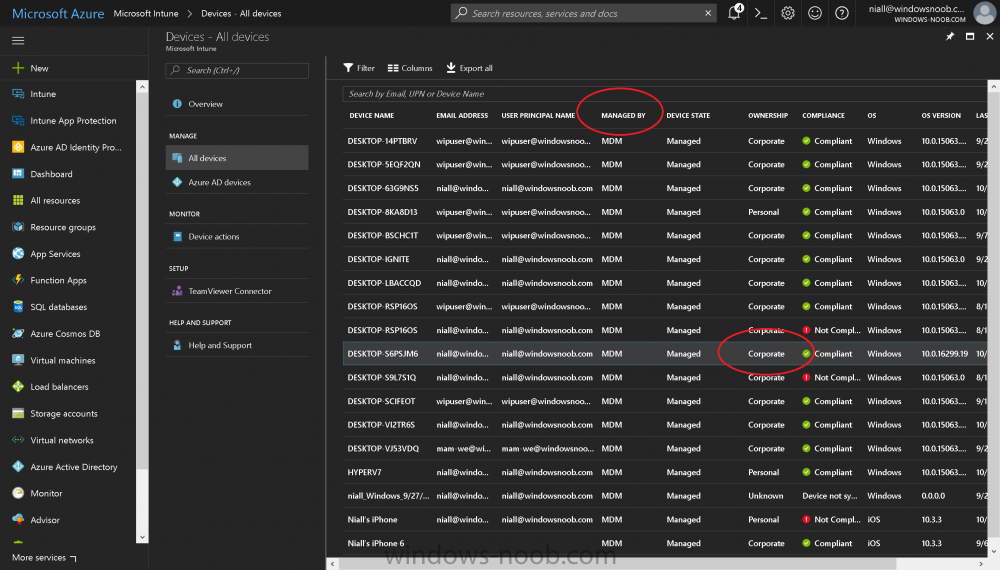
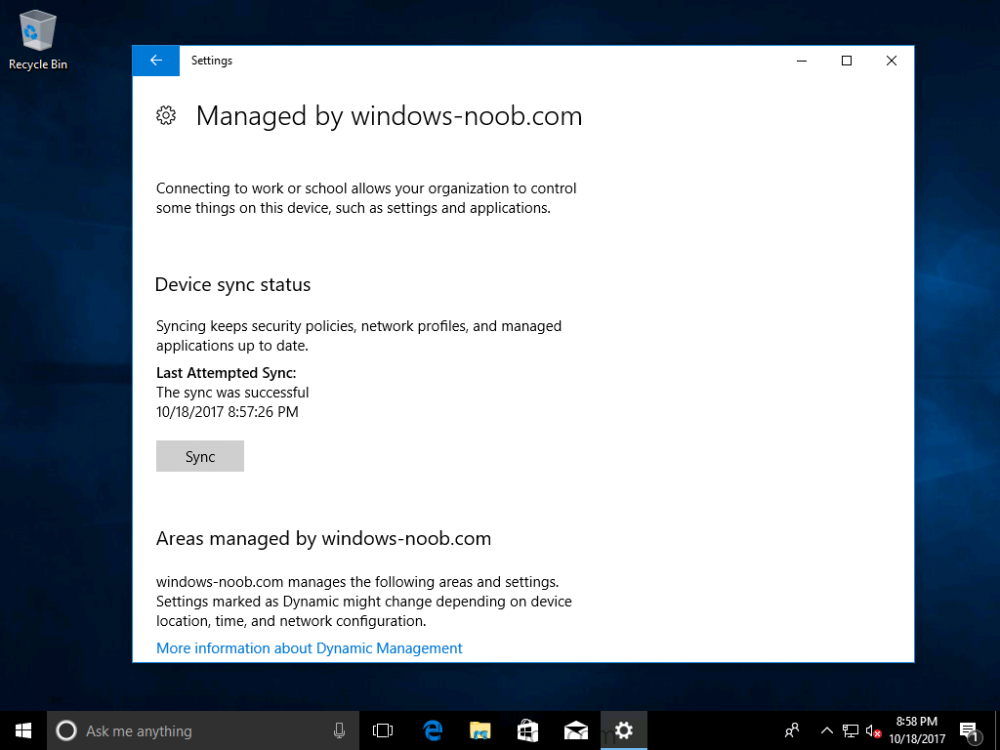
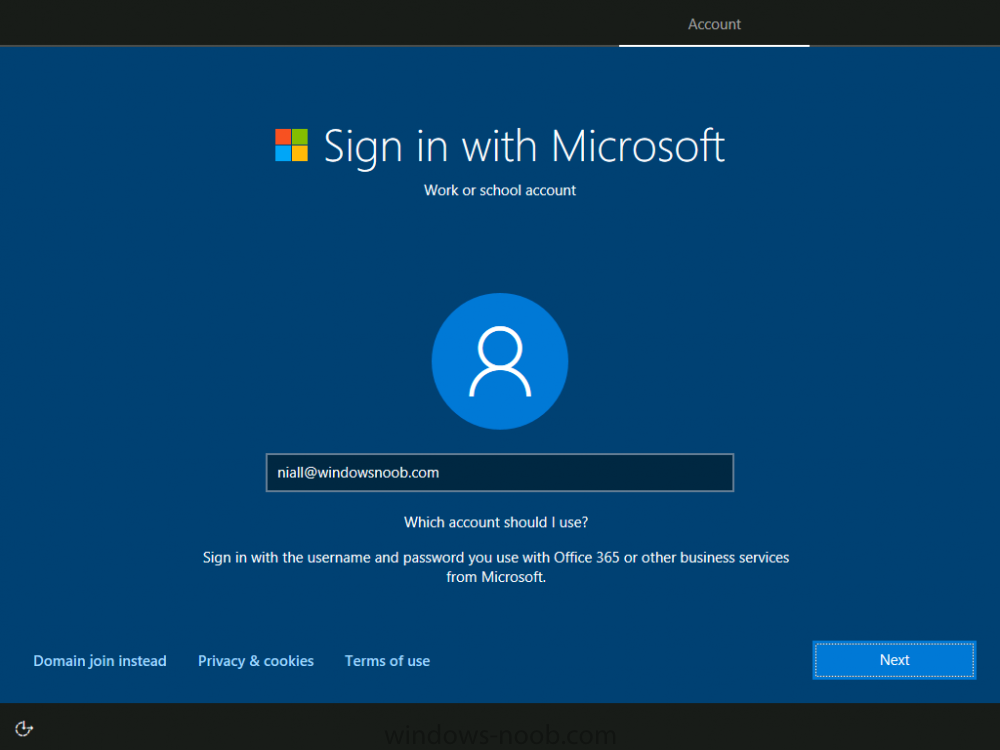
Introduction Devices can be enrolled into Microsoft Intune in many ways, the user can download the Microsoft Company Portal, and enroll the device using the wizard contained within that app, this would then mean the device shows up as Personal owned. Or, the admin can use Bulk Enrollment methods such as Apple Device Enrollment Program or Apple Configurator (which requires an Apple Mac to run the program) or for Windows devices, use Windows AutoPilot. Keep in mind that bulk enrollment is generally for new devices and not devices that have already been deployed. When you join new Windows desktop, mobile, holographic or Surface devices into Azure AD (Azure AD join as part of OOBE or Windows AutoPilot or via the options in the operating system) you can avail of a new MDM auto-enrollment capability which means that not only is the device Azure AD joined, but it will automatically become enrolled (and managed) by Microsoft Intune. This also means that the device will show up as Corporate owned and has the distinct advantage of not needing the end user (or admin) to have to download and use the Company Portal to enroll the device. To setup MDM auto-enrollment in Azure is fairly easy, and here's how to do it. You do need to have both Azure Active Directory Premium subscription and a Microsoft Intune tenant configured before doing this. Step 1. Login to Azure As a user with administrative permissions in Azure Active Directory, login to https://portal.azure.com and select the Azure Active Directory service highlighted here with the red arrow. Step 2. Configure MDM auto-enrollment Click on Mobility (MDM and MAM) and then select Microsoft Intune from the applications listed. The Configure Microsoft Intune blade opens. Notice the following text (by clicking on the information 'i' beside MDM User scope, which explains the capabilities. Use MDM auto-enrollment to manage enterprise data on your employees' Windows devices. MDM auto-enrollment will be configured for AAD joined devices and bring your own device scenarios. Click on Restore default MDM URLs and then select Some (to select one or more user groups you want to enable for MDM auto-enrollment), or All to apply to all users. In this example you will add a User Group (previously created, containing one or more Windows device users), so select Some, and then click on Select Groups to select the User groups you want this MDM auto-enrollment capability to apply to. When you are done with your selection, click on Select. Next click on Save to save your changes. You'll be notified in the top right corner of the success or failure of this action. That's it, job done, now go and Azure AD join a Windows device, using a user that is a member of the group you specified above. After joining Azure AD, it will also become MDM auto-enrolled by Microsoft Intune. You can verify this by going into Microsoft Intune service in Azure, and selecting Devices then All Devices, the device you just joined into Azure AD will now also be MDM Managed by Microsoft Intune (due to MDM auto-enrollment) and listed as a Corporate owned device. And on the device itself you can verify in All Settings, Accounts, Access work or school, and click on the username. For more info about this read https://docs.microsoft.com/en-us/intune/windows-enroll#enable-windows-10-automatic-enrollment
-
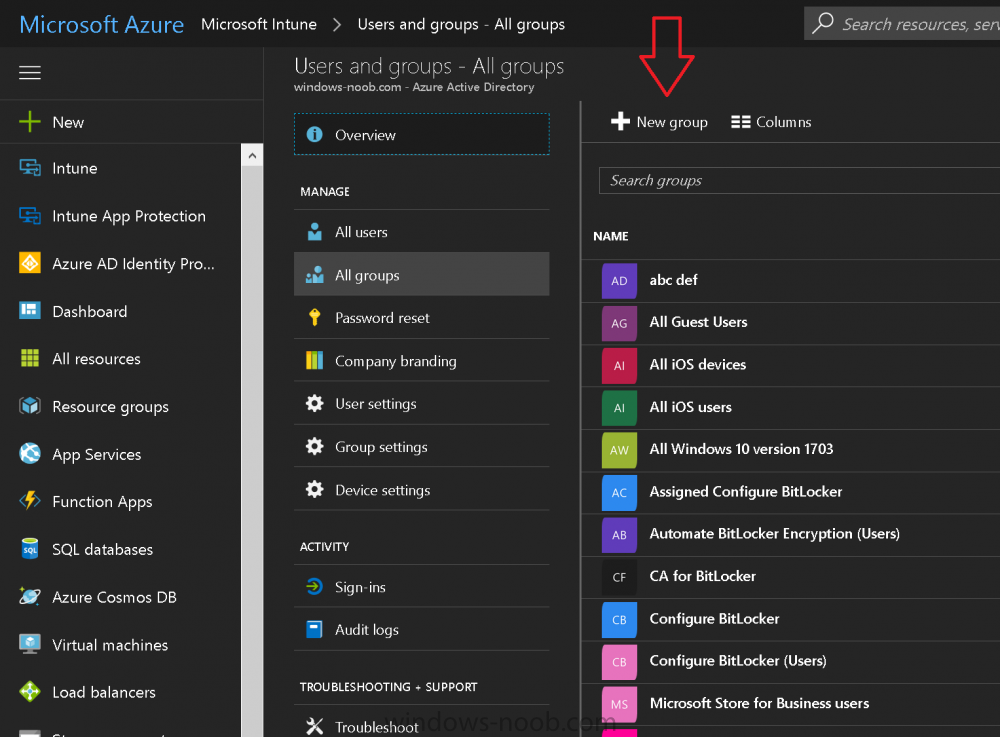
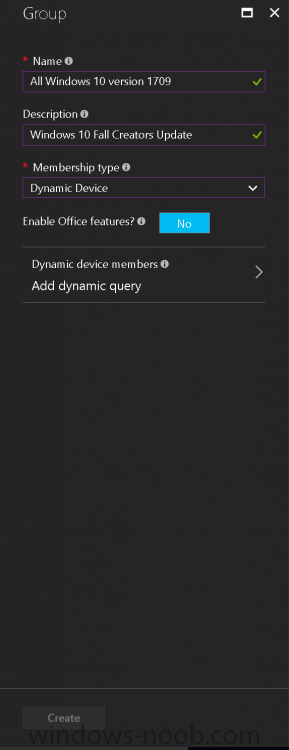
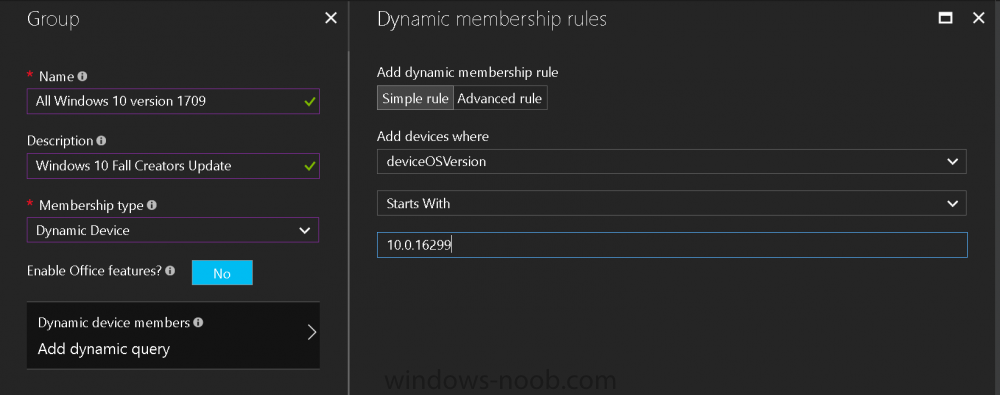
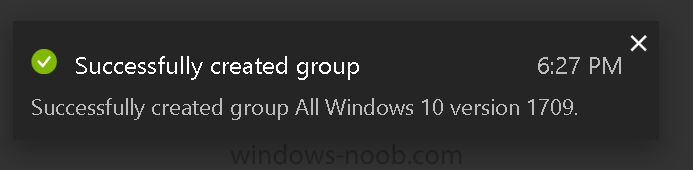
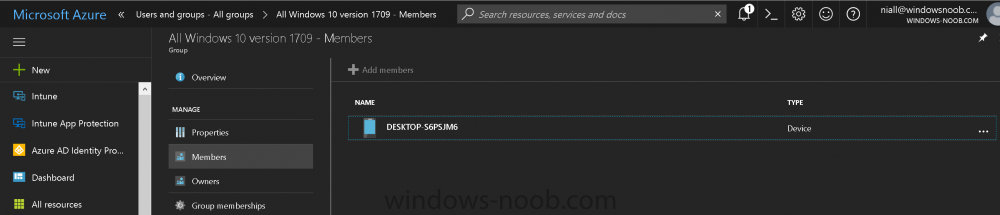
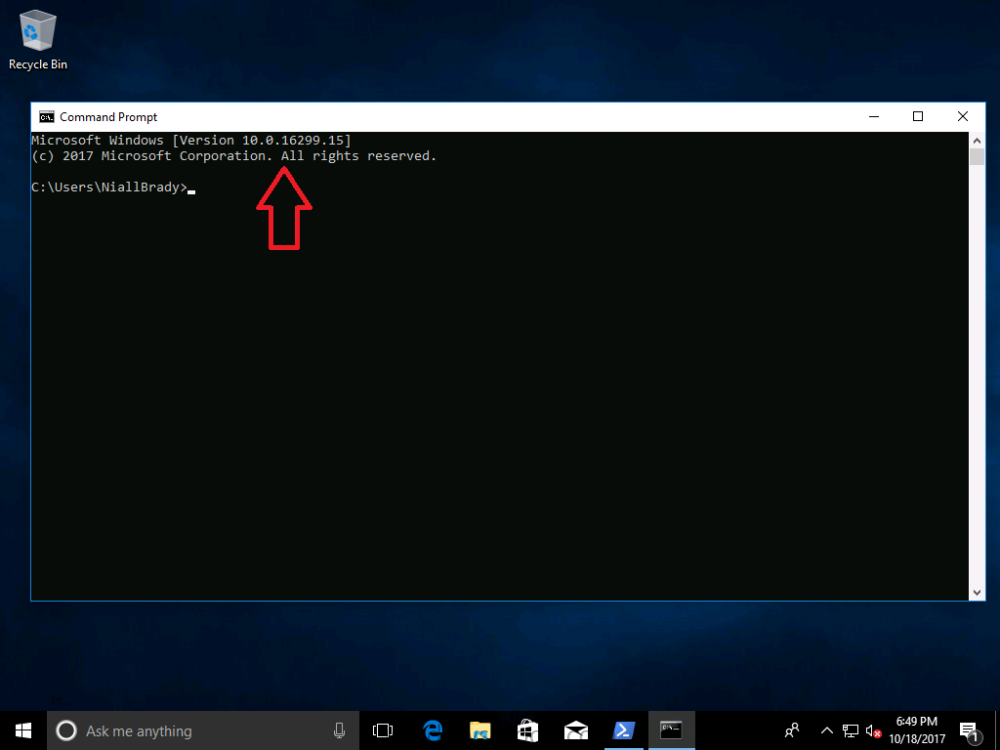
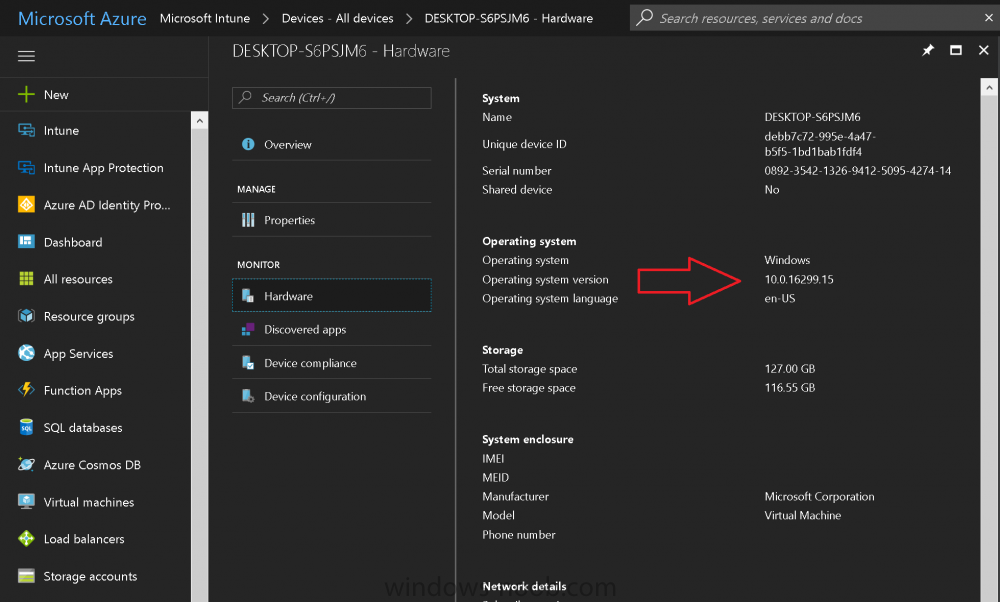
Introduction Microsoft released Windows 10 version 1709 to VLSC and MSDN yesterday, so of course people are deploying it and testing it in their environments. If you want to create a dynamic Group (that auto populates) of Windows 10 version 1709 in Microsoft Intune then do as follows. Note: In this blog post I assume you have configured MDM auto-enrollment in Azure. This isn't mandatory but makes enrollment into Microsoft Intune for Windows devices much easier. To see how to enable that functionality, click here. Step 1. Login to Azure Login to https://portal.azure.com and select the Intune service. Step 2. Create a dynamic devices group Click on Groups. Select New Group (highlighted with the Red Arrow). In the New Group blade, use the following options Name: All Windows 10 version 1709 Description: Windows 10 Fall Creators Update Membership Type: Dynamic Device In the Dynamic Device members Add Dynamic Query option, enter the following Add device membership rule: SimpleRule Add devices where DeviceOsVersion StartsWith 10.0.16299 Next, click on Add Query Followed by Create. You'll get a notification in the top right that the group was successfully created. Step 3. AzureAD join a Windows 10 version 1709 device Go through OOBE on a Windows 10 version 1709 device, at the account screen enter your Azure AD credentials. and after the device has joined Azure AD, it'll show up in Intune soon after in the correct Group. Job done ! You can verify the build number on a Windows 10 version 1709 device by opening a command prompt, in this screenshot it's 10.0.16299.15, the .15 at the end will increase as new cumulative updates are installed on this base build number. and that full string can be seen in Intune in Devices, select All Devices, select the device in question and click on Hardware. Note: If you'd like to create a collection in SCCM for Windows 10 version 1709 please see the following blog post. For a list of deployment resources for Windows 10 version 1709 please see here.
- 3 replies
-
- windows 10
- fall creators update
-
(and 2 more)
Tagged with:
-
Windows 10 version 1709 (Fall Creators Update) is finally available on Microsoft’s Volume Licensing Service Center and MSDN. To see what’s new in Windows 10 1709 see the following post https://blogs.technet.microsoft.com/windowsitpro/2017/10/10/see-whats-new-for-it-pros-in-windows-10-version-1709/ To find out how to get it, see https://blogs.windows.com/windowsexperience/2017/10/17/get-windows-10-fall-creators-update/ Windows 10 ADK version 1709 With the release of Windows 10 version 1709, along comes the Windows Assessment and Deployment Kit (ADK) version 1709. You can download it from: Windows 10 Assessment and Deployment Kit (ADK). RSAT for Windows 10 version 1709 You can download the Remote Server Administration tools for Windows 10 version 1709 here. https://www.microsoft.com/en-au/download/details.aspx?id=45520 Recommended reading What's new in Windows 10 version 1709 https://docs.microsoft.com/en-us/windows/whats-new/whats-new-windows-10-version-1709 Windows lifecycle facts page updated with Windows 10 1709, including tentative end of service date, March 2019 https://support.microsoft.com/en-us/help/13853/windows-lifecycle-fact-sheet Windows 10 version 1709 ADK Windows 10 Assessment and Deployment Kit (ADK)
-
you'd just have to add a delay function on the associated button, either in the wrapper or the HTA itself
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
Introduction Here’s some links with videos of all the Microsoft Intune and Configuration Manager, Windows 10 & Office 365 ProPlus content @ Microsoft Ignite in Florida last month. Intune/ConfigMgr: Mobile device and app management overview with Microsoft Intune System Center Configuration Manager overview and roadmap Conduct a successful pilot deployment of Microsoft Intune Manage and secure Android, iOS, and MacOS devices and apps with Microsoft Intune Learn how to use Microsoft Intune with the new admin console and Microsoft Graph API Secure access to Office 365, SaaS and on-premises apps with EMS Manage and protect Office 365 mobile apps with Microsoft Intune Deploying and using Outlook mobile in the Enterprise Manage mobile productivity with EMS Windows 10 & Office 365 ProPlus: Microsoft 365: Modern management and deployment (general session with Brad and Rob) Overview: Modern Windows 10 and Office 365 ProPlus management with EMS Transition to cloud-based management of Windows 10 and Office 365 ProPlus with EMS Modernize deployment & servicing of Windows 10 & Office 365 ProPlus with EMS Secure Windows 10 with Intune, Azure AD and System Center Configuration Manager