-
Posts
9194 -
Joined
-
Last visited
-
Days Won
367
Everything posted by anyweb
-

Autopilot deployment profile get not assigned
anyweb replied to maikwhat's topic in Microsoft Intune
what have you assigned the deployment profile to, and is the device in that group ? -
here's the guide
-

Issues with WinPE.
anyweb replied to triston1434's topic in System Center Configuration Manager (Current Branch)
which version of mdt ? -

Issues with WinPE.
anyweb replied to triston1434's topic in System Center Configuration Manager (Current Branch)
is this an MDT enabled environment or pure SCCM, if so what version of SCCM ? -

Issues with WinPE.
anyweb replied to triston1434's topic in System Center Configuration Manager (Current Branch)
if you can grab the smsts.log from a machine that has the problem and attach it here that would be great -

Install Custom SCCM Client
anyweb replied to coolsport00's topic in System Center Configuration Manager (Current Branch)
as these are servers you could create a network logon script targeted only to the servers to do exactly what you want, install your 'custom' package, have you tried that ? -
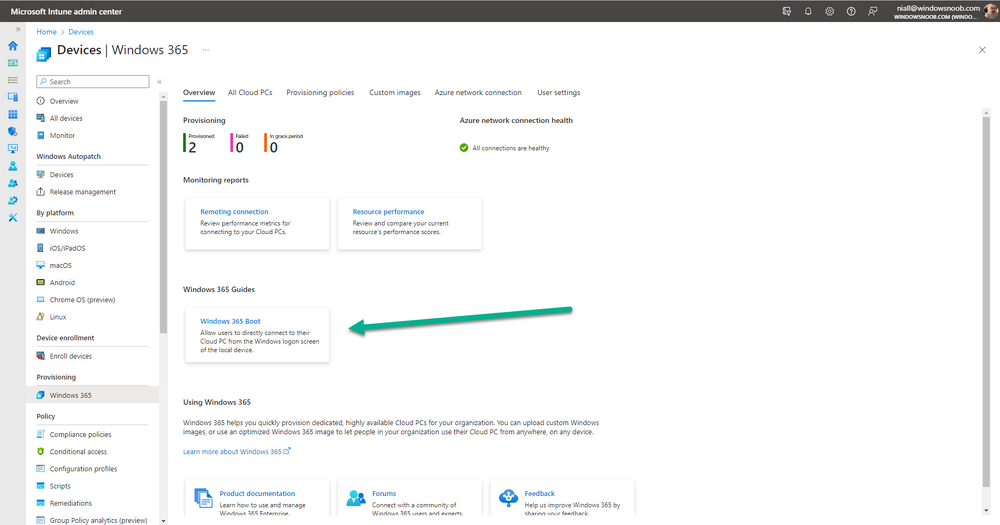
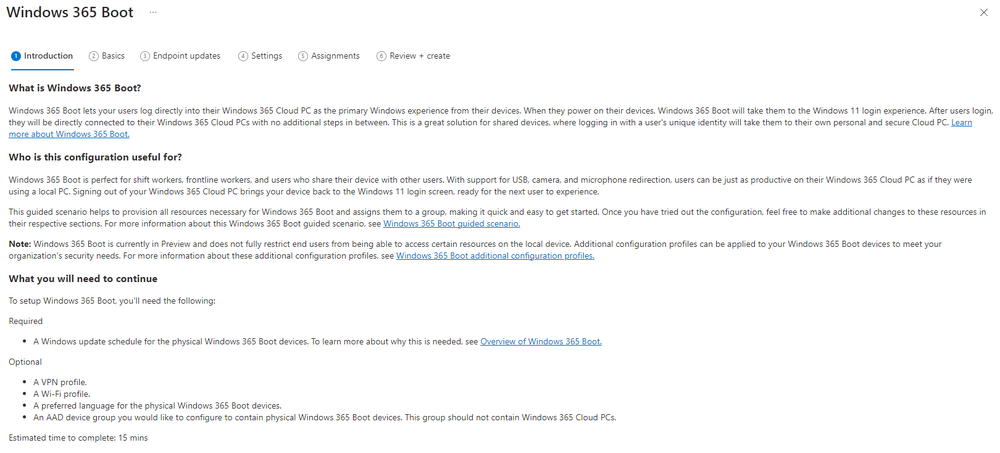
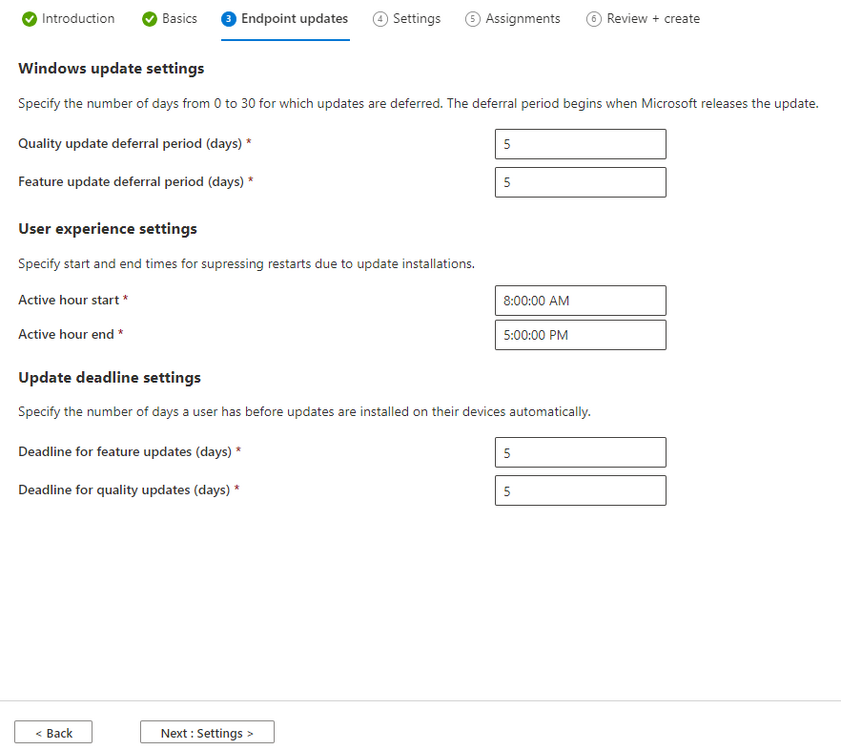
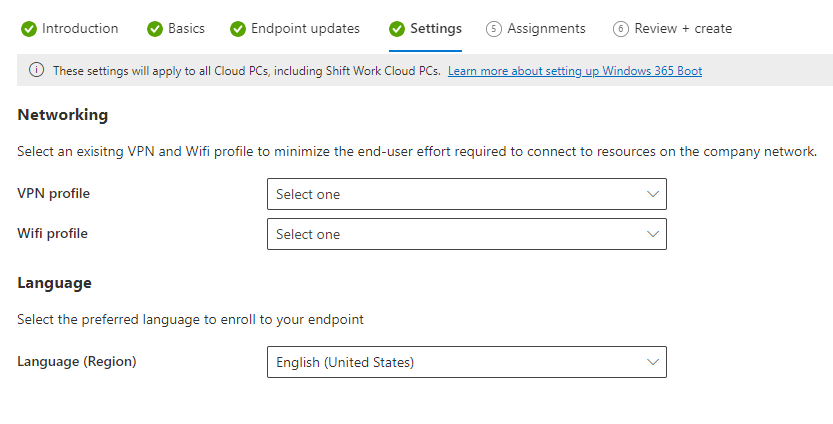
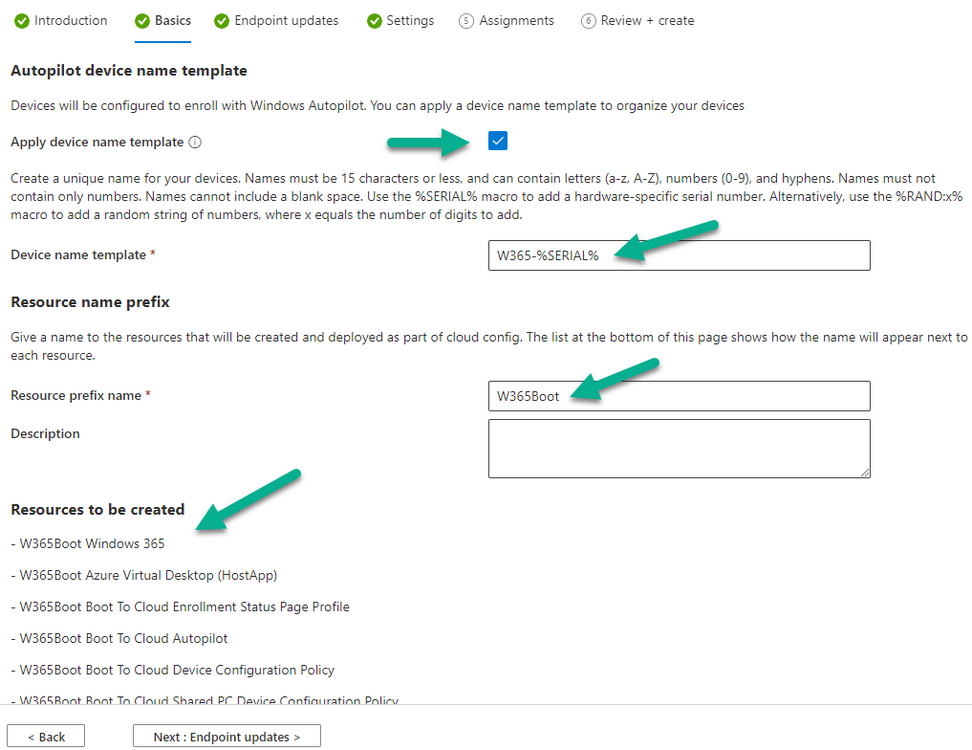
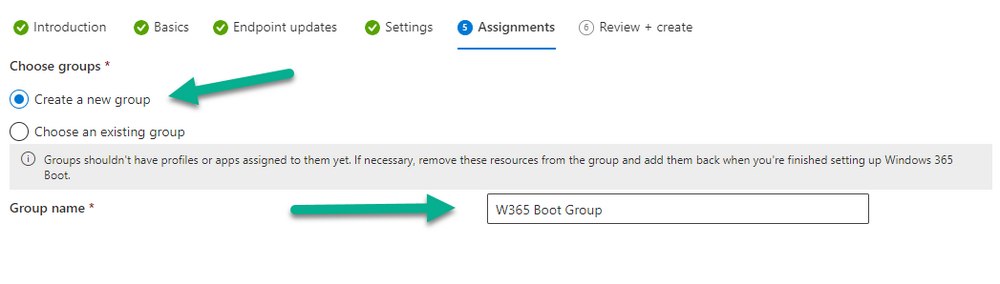
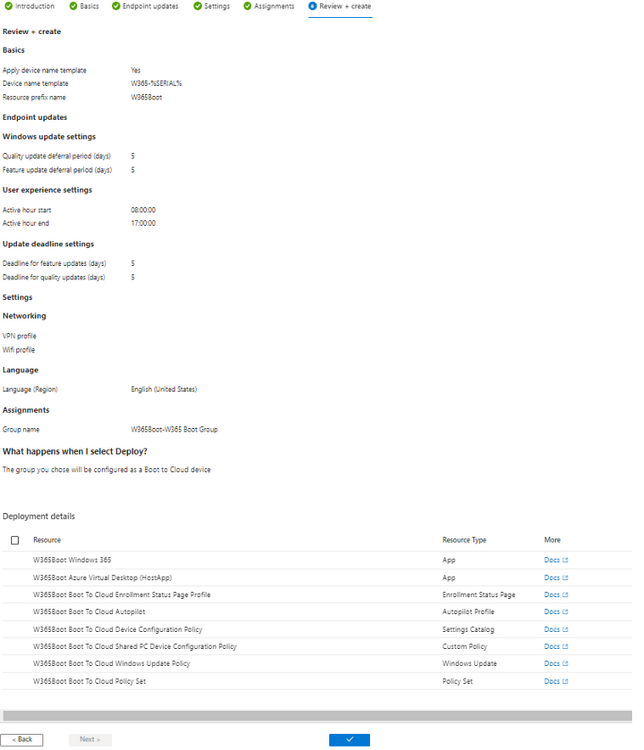
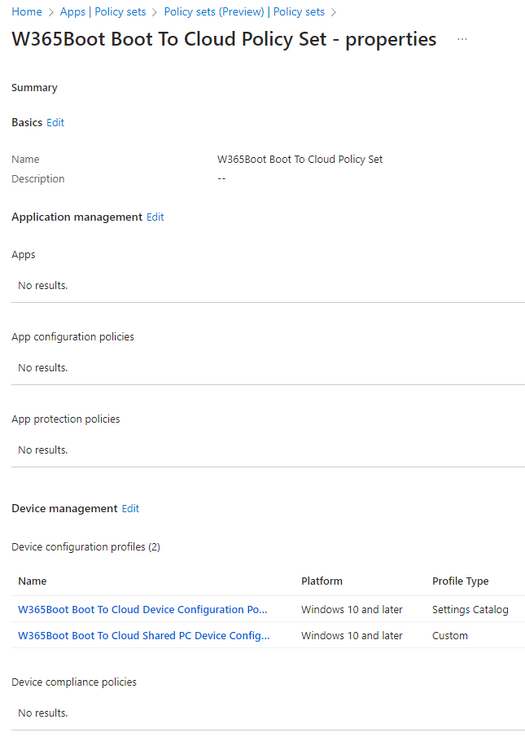
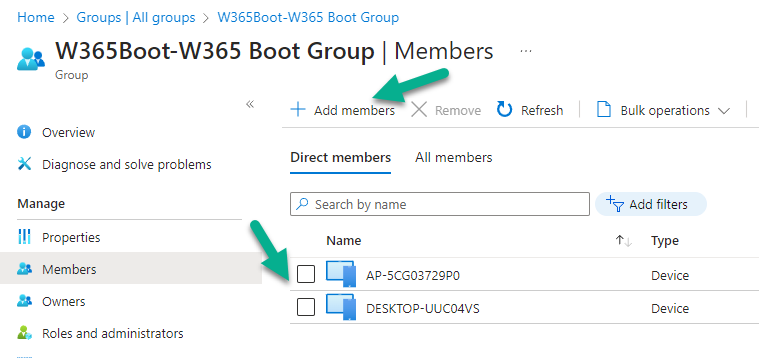
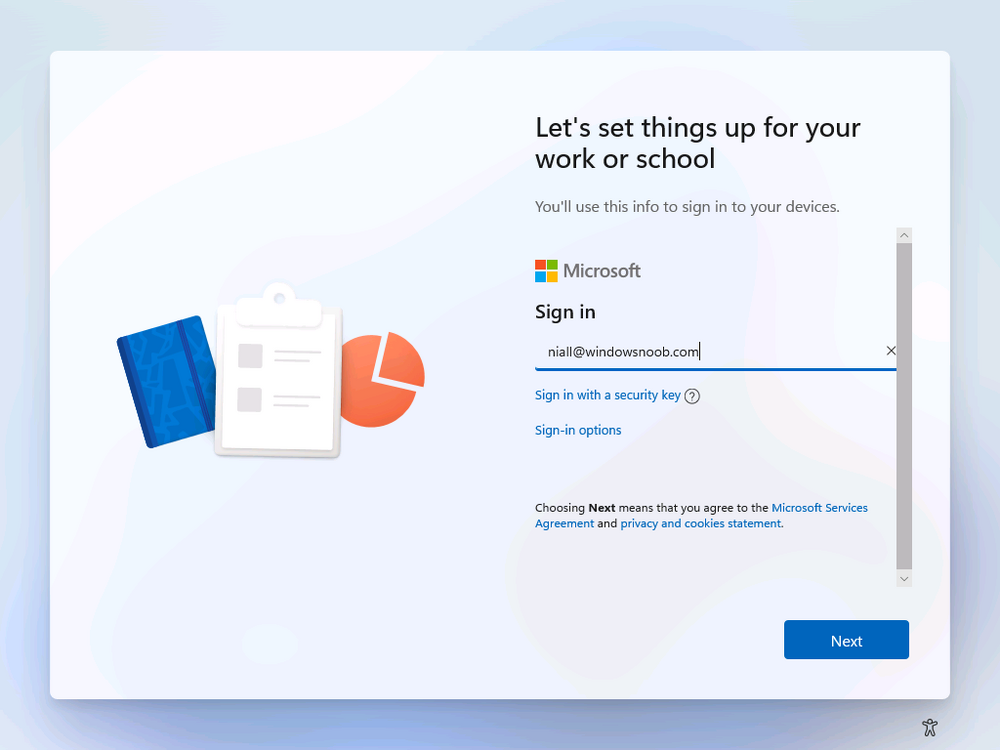
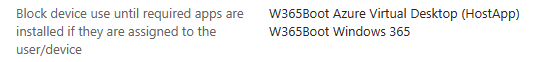
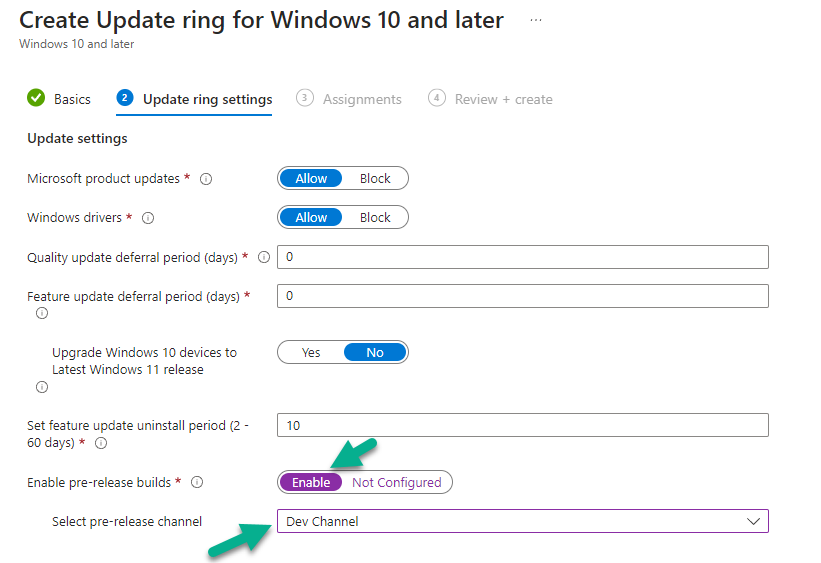
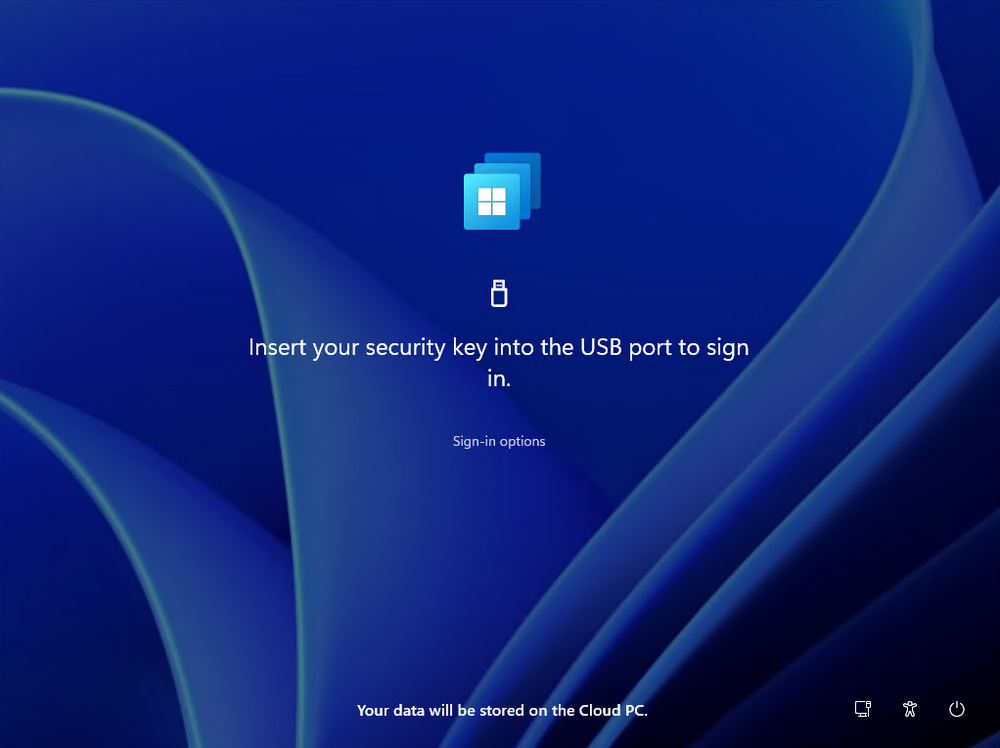
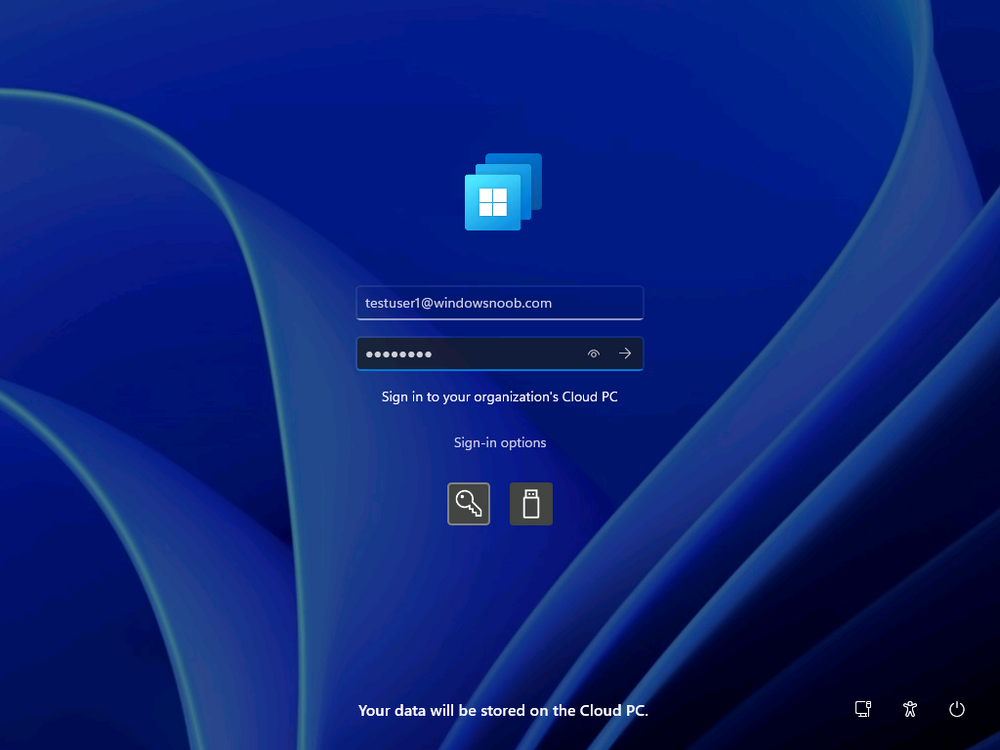
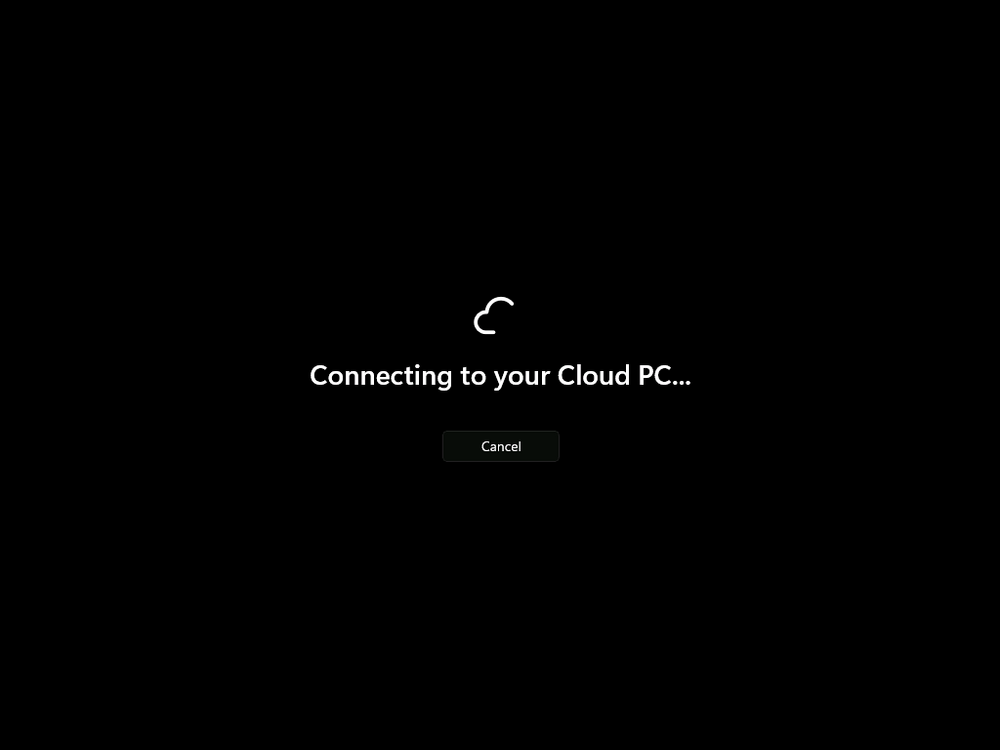
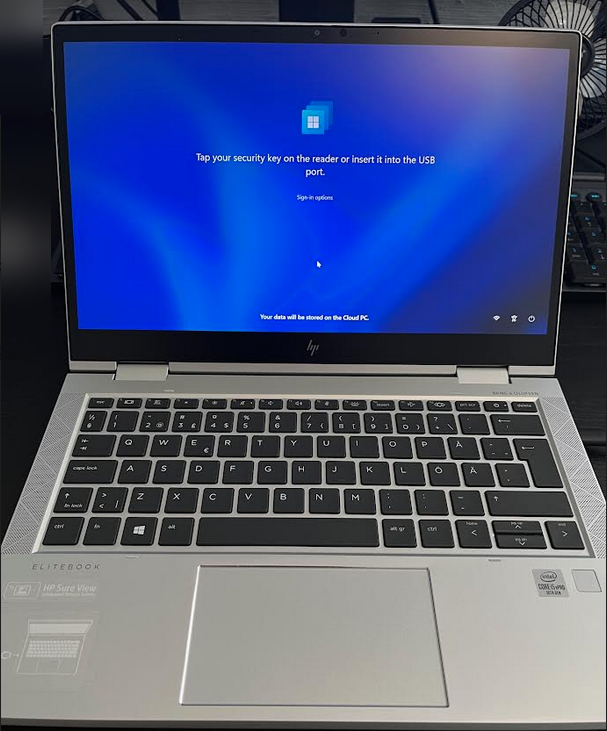
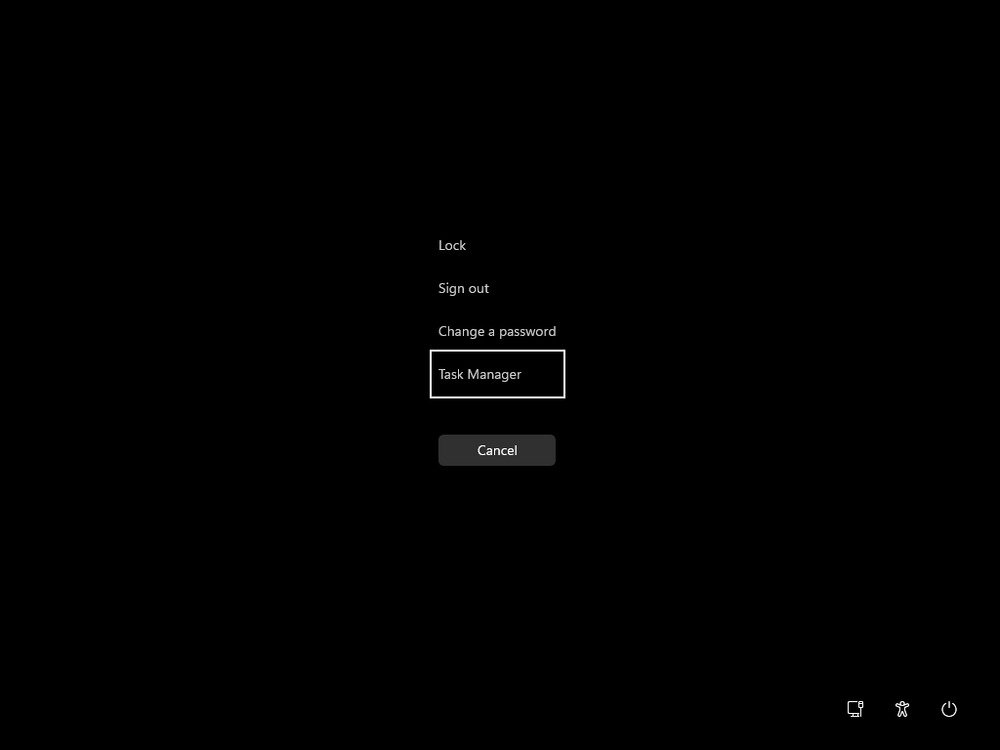
Introduction This is Part 8 in a new series of guides about getting started with Windows 365. This series of guides will help you to learn all about Windows 365 in a clear and insightful way. This series is co-written by Niall & Paul, both of whom are Enterprise Mobility MVP’s with broad experience in the area of modern management. At the time of writing, Paul is a 6 times Enterprise Mobility MVP based in the UK and Niall is a 12 times Enterprise Mobility MVP based in Sweden. In this series we aim to cover everything we learn about Windows 365 and share it with you to help you to deploy it safely and securely within your own organization. In Part 1 we introduced you to Windows 365, selecting the right edition with the level of management that you need, choosing the plan that suits your users needs at a cost you can afford, or modifying the configuration to make it more suited to your individual needs, purchasing licenses and saving money for your organization via the Windows Hybrid Benefit. In Part 2 you learned how to provision an Azure Ad joined Cloud PC and take a look at the different network options available when provisioning an Azure Ad joined Cloud PC. In Part 3 you learned about the steps needed to successfully provision a Hybrid Azure Ad Joined Cloud PC. In Part 4 you saw the many different ways you can connect to your Cloud PC from many device be it Android, Mac, Windows, Linux or iPhone and you learned that not all connection options have the same abilities. In Part 5 we covered the management capabilities of your Cloud PCs and explained the different options available depending on which version (Business versus Enterprise) that you purchase. In Part 6 we looked at the built in configurable backup technology in Windows 365 which is known as Point-in-time restore, which gives the admin (or user) the ability to restore Cloud PC's to an earlier time before a problem such as a Ransomware incident occurred. In Part 7 we looked at the ability to use Windows Autopatch to patch your Cloud PC's with ease and covered how to allow access to admins without licenses, enrolling into Windows Autopatch, the Readiness assessment tool, device registration and moving devices between deployment rings. Finally we looked at Windows Autopatch reports and the overall User Experience. In this part we'll take a look at the long awaited Windows 365 Boot feature and learn all about it. Below you can find all parts in this series: Getting started with Windows 365 - Part 1. Introduction Getting started with Windows 365 - Part 2. Provisioning an Azure Ad Joined Cloud PC Getting started with Windows 365 - Part 3. Provisioning a Hybrid Azure Ad Joined Cloud PC Getting started with Windows 365 - Part 4. Connecting to your Cloud PC Getting started with Windows 365 - Part 5. Managing your Cloud PC Getting started with Windows 365 - Part 6. Point in time restore Getting started with Windows 365 - Part 7. Patching your Cloud PCs with Windows Autopatch Getting started with Windows 365 - Part 8. Windows 365 boot <- you are here Getting started with Windows 365 - Part 9. Windows 365 switch Getting started with Windows 365 - Part 10. Windows 365 offline In this part we'll cover the following: Introduction to Windows 365 Boot Prerequisites Enabling Windows 365 Boot Preparing devices for Windows 365 Boot Using Windows 365 Boot Recommended reading Summary Introduction to Windows 365 Boot Update: Windows 365 Boot and Switch became Generally Available 26th September, 2023, so as long as you are using Windows 11 22H2 with build 2361 or later (or natively in Windows 11 23H2 later in Q4), then there should be no need to use the Windows Insider Preview steps mentioned below. Windows 365 Boot lets admins configure Windows 11 physical devices so that users can: Avoid signing in to their physical device. Sign in directly to their Windows 365 Cloud PC on their physical device. If that's confusing, then keep in mind that Windows 365 Boot is defined by Microsoft as follows: Prerequisites To setup Windows 365 Boot the following prerequisites need to be met on the physical devices: Enroll each physical device into Windows Autopilot. Assign the physical device to the Windows 365 Boot Enrollment Status Page (for Windows Autopilot) Assign the physical device to the Windows 365 Boot Azure AD group you created in the guided scenario wizard. Enabling Windows 365 Boot To enable Windows 365 Boot in your tenant do as follows. Navigate to the Windows 365 provisioning node and you should see a Windows 365 Boot guide as shown in the screenshot below. You need to click on that to start the guided scenario. And here it is, the Introduction screen of the guided scenario for Windows 365 Boot. Clicking Next gathers the basic info, including whether or not you want to use a device name template (as you do for Windows Autopilot devices...). Once you've confirmed the resource name prefix, it'll list a list of resources that will be created using that naming convention. Even though you can use Windows Autopatch to patch your Windows 365 Boot devices, there's no easy way to do that (yet) in this wizard, we've provided that feedback already to the Product Group. For now, configure the settings as appropriate. On the next screen (Settings) you get to choose an option VPN and Wi-Fi setup, and to decide which language to use. On the next screen you add your assignments. We chose to create a new group and gave it a suitable name. Finally you'll get a summary of the settings you've chosen along with a list of resources it will create. Note that the guided scenario creates several things as part of the setup including an Enrollment Status Page profile, a Windows Autopilot deployment profile, and some apps which must be installed before the device can be logged on to. These and other configuration profiles are listed/defined in the policy set created during the wizard. You can find the Windows 365 Boot policy set in Apps, Policy Sets. Also to note, when the Windows 365 Boot ESP is created, it's at the lowest priority so if you want your shared devices/hosts to get that profile, make sure to increase the priority or change the assignments. Preparing devices for Windows 365 Boot Now you are ready to test Windows 365 Boot, and to do so you'll need a device that matches the prerequisites mentioned earlier. You can use Intune Update Rings to target Windows 11 devices with that Windows 11 version. Each physical device (and Cloud PC) must be running one of the following, version 22621.2361 or later: Windows 11 Enterprise Windows 11 Professional Windows IoT Enterprise Once those devices are upgraded then add them to the Windows 365 boot group that you defined during the wizard. After the device is running the correct version of Windows 11, use Windows Autopilot to enroll as normal and make sure it's in the Azure Ad group targeted with the Windows 365 Boot policy Using Windows 365 Boot After Windows Autopilot enrollment is complete on your shared physical device it will be ready for Windows 365 Boot and that will become obvious as the logon screen changes. You'll get the following login screen, which is the new Windows 365 Boot login UI with a cool Windows 365 logo. Note how it clearly states that your data will be stored on your Cloud PC. To login, click Sign-in options and enter the credentials of a user with a Windows 365 license. It'll state "preparing Windows" for a moment followed more excitingly by this. However, we are using a hybrid azure ad joined Cloud PC the next part is less exiting as their is no possibility to configure single sign on (SSO) yet. After signing in again (and completing MFA) it will show your Cloud PC ! And here's where the fun starts, as this is a shared PC scenario, multiple users can login (after the other users logs off...) as long as they are assigned a Cloud PC. So here for example is another user logged on to the same Windows 365 Boot device, however their Cloud PC is running Windows 10. As the physical device is connected directly to your Cloud PC, resources such as the MIC, Camera are shared with the Cloud PC allowing you to use them in Teams calls etc. One thing to be aware of however is that once Windows 365 Boot 'takes over' a physical device you can no longer get back to the main UI on that device without first removing the physical device from the targeted device configuration profiles in Intune. You can however bring up task manager to run Explorer.exe and browse your local files on the physical device if needed. Note that Microsoft will most likely remove the ability to start the Task Manager on physical devices once Windows 365 Boot exits from Preview. Recommended reading Deploy the public preview today - Windows 365 Boot What is Windows 365 Boot? | Microsoft Learn Windows 365 Boot guided scenario Windows 365 Boot physical device requirements. Restrict user access to Windows 365 Boot physical device. Troubleshoot Windows 365 Boot. Visit the Microsoft tech community blog Restrict user access to Windows 365 Boot physical device. | Microsoft Learn Windows 365 Boot guided scenario | Microsoft Learn Summary Windows 365 Boot in its current form (preview) allows shared PC's to be used for connecting straight to a Windows 365 Cloud PC, you could say booting to the Cloud PC but in reality the host device must boot up first. It is seamless however, and very well executed. You simply prepare the device, hand it over to the user and they logon to their Cloud PC. Once they are done, they can hand the physical device back and another user can use it to connect to their Cloud PC. This is a great way of simplifying this scenario, and having all the back end bits created by the wizard makes it a breeze to setup. The downside is that once you've targeted a device with this policy, there's not a whole lot you can do on it other than connect to Cloud PC's, but all you have to do to restore it's former glory is to remove it from the device configuration profiles targeted to it.
-
hi Alex can you verify that you meet these requirements when creating the ANC ? as you are just doing AAD the first line is what you need Intune Administrator, Windows 365 Administrator, or Global Administrator role. and... once created, if you need to edit it... you'll also need > to have the Subscription Reader role in the Azure Subscription where the VNET associated with the ANC was located. for more info > Azure network connection overview | Microsoft Learn cheers niall Permissions required for Azure network connections The ANC wizard requires access to Azure and, optionally, on-premises domain resources. The following permissions are required for the ANC: Intune Administrator, Windows 365 Administrator, or Global Administrator role. An Active Directory user account with sufficient permissions to join the AD domain into this Organizational Unit( (Hybrid Azure AD Join ANCs only). To create or edit an ANC, you must also have the Subscription Reader role in the Azure Subscription where the VNET associated with the ANC was located. For a full list of requirements, see Windows 365 requirements.
-
IT compliance is a critical aspect of modern business as it refers to the adherence to policies, regulations, and government laws protecting IT systems and processes. IT compliance ensures businesses and organizations operate under strict security requirements, guidelines, and industry best practices for data protection and governance. IT business leaders, CIOs/CTOs/CISOs, MSPs, system administrators, and other roles within IT must understand the importance of implementing stricter compliance requirements to protect valuable data. Here are a few reasons why modern businesses and organizations must become IT-compliant: Ensuring Data Privacy and Security Businesses that handle sensitive information, such as customer data and financial and medical information, must comply with industry-specific frameworks like HIPAA, PCI-DSS, GDPR, and others. These frameworks provide guidelines for protecting the most sensitive of information a business handles, including data encryption, access controls, and vulnerability assessments. Mitigating Security Risks IT Compliance standards, such as ISO 27001, NIST, and CIS, provide guidelines for identifying, assessing, and mitigating security risks. These standards enable businesses to implement best practices for security and ensure that their IT infrastructure is secure against cyber threats. Avoiding Legal and Financial Fines IT compliance can help businesses avoid legal and financial penalties. However, non-compliance with industry-specific regulations can result in hefty fines, legal suits, and loss of reputation in case of data breaches and general loss of sensitive information. Providing Competitive Advantage Compliance with industry-specific regulations demonstrates to customers the willingness and seriousness businesses take toward data privacy and information security. Compliance can also help businesses improve their reputation, build customer trust, and enhance brand value. Take the Hornetsecurity IT Compliance Survey now! Feel free to participate and get a chance to win!
-
can you show me how you originally configured SCCM other sources ? maybe that was the issue
-
hi Joe, do you still have this problem ?
-

Migrate to the cloud - Part 1. Setup
anyweb replied to anyweb's topic in System Center Configuration Manager (Current Branch)
ok i've shared the new code with you @TomBlack please read the instructions in the ZIP (7zip) -

Migrate to the cloud - Part 1. Setup
anyweb replied to anyweb's topic in System Center Configuration Manager (Current Branch)
hi TomBlack, i have a new version (not released yet) with several fixes/changes/enhancements, if you want to try it, pm me and i'll make it available to you, blog coming later... -

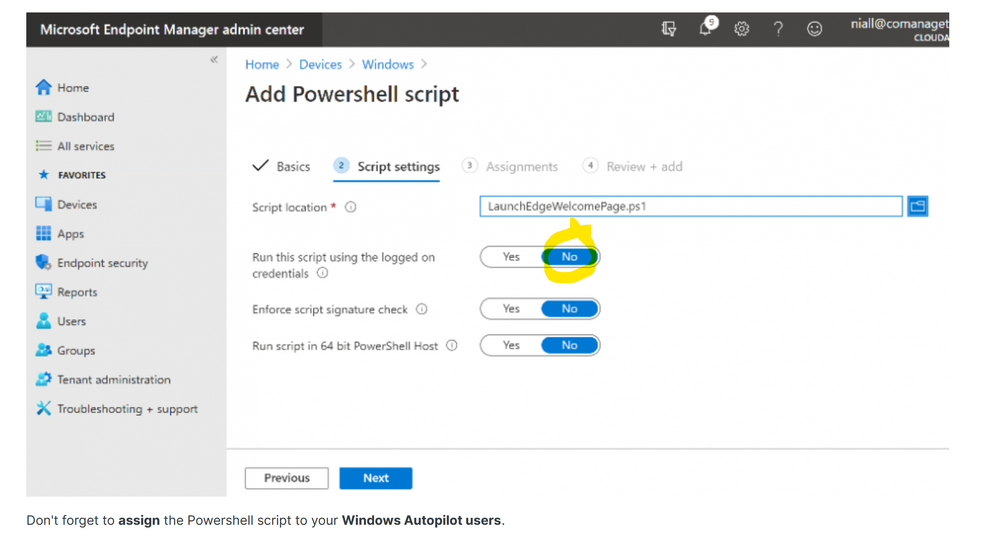
Displaying a welcome page after Windows Autopilot completes
anyweb replied to anyweb's topic in Microsoft Intune
did you assign this to your Windows Autopilot users or ? -

Displaying a welcome page after Windows Autopilot completes
anyweb replied to anyweb's topic in Microsoft Intune
-
do you know what software is installed on this cloud pc, probably one or more apps are slowing things down, that's my guess, but it's hard to tell without more info about whats running on the cloud pc, do you know ?
- 3 replies
-
- remote desktop
- remote
-
(and 1 more)
Tagged with:
-
this looks like a Windows 365 Cloud PC (business), based on the 'please wait' I wonder is it getting updated by any chance, it looks like it needs a restart, if you browse to https://www.windows365.com do you see an option to restart your Cloud PC there ? if that doesn't help when you see 'please wait' then you'll need to troubleshoot on the Cloud PC itself to see what is causing it to be in this state,
- 3 replies
-
- 1
-

-
- remote desktop
- remote
-
(and 1 more)
Tagged with:
-

Migrate to the cloud - Part 1. Setup
anyweb replied to anyweb's topic in System Center Configuration Manager (Current Branch)
hi @Wizu I've now finished updating the changes and testing to the new release (1.5.28) I plan on blogging about the changes shortly, if you'd like to try it before I blog it then please pm me and i'll make the code available,