-
Posts
9257 -
Joined
-
Last visited
-
Days Won
371
Everything posted by anyweb
-

New SCCM 1702 Setup Issue
anyweb replied to day79's topic in System Center Configuration Manager (Current Branch)
what does mpMSI.log say ? -

SCCM 1702 bug to be aware of
anyweb replied to Config Mangler's topic in System Center Configuration Manager (Current Branch)
i'm not sure if this weekends hotfix will fix this problem but check your Updates and Servicing node.... -
heh, interesting observation, but to be honest, this is in the interest of protection your details, your info, your account, so you should understand that it's important that your password is a decent one, security today, is very important as the recent ransomware news made all to clear
-

Deployment for computers with no monitors
anyweb replied to Glowbeard's question in Windows Deployment Services (WDS)
id personally use MDT (with WDS) to install those machines easily, and then the machines themselves would be hyperv VM's, there's a bunch of guides right here to start setting that up, such as this one. -
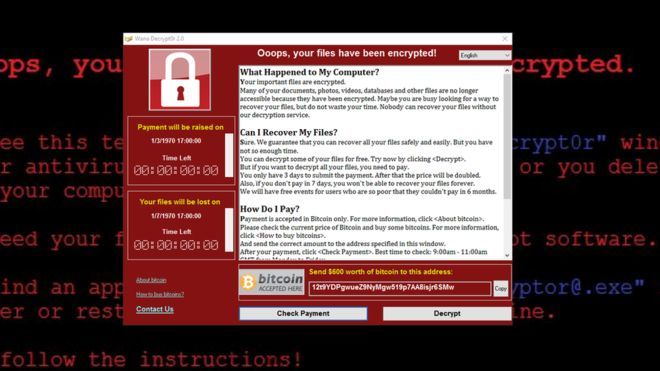
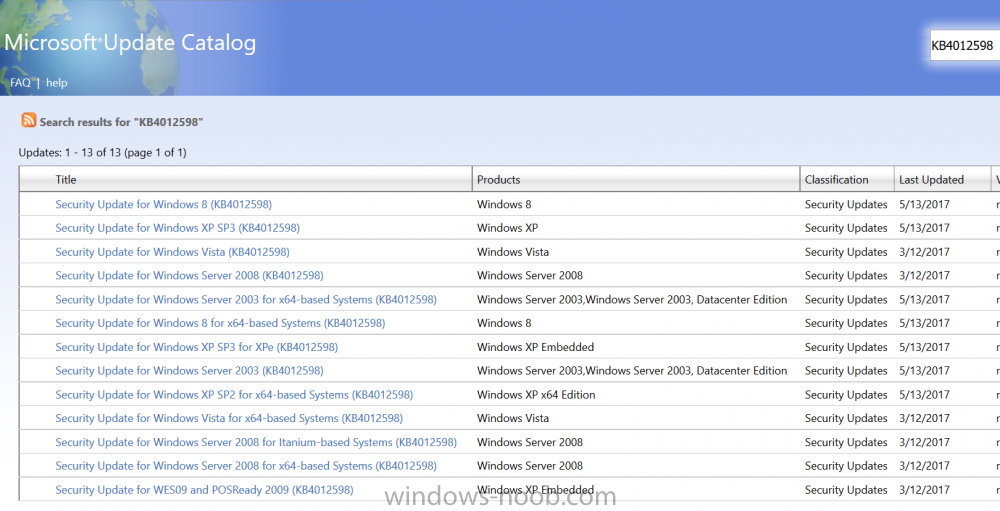
Ransomware has been around for a few years now but up until yesterday, it wasn't that well known about. This latest RansomWare called WannaCry has changed that for ever. Ransomware encrypted data on at least 75,000 systems in 99 countries on Friday. Payments were demanded for access to be restored. European countries, including Russia, were among the worst hit. Companies around Europe were hit and investigations are underway to see who was responsible. This was such a big attack that Microsoft released patches for unsupported operating systems (such as Windows XP) to allow those businesses still running them, a chance to protect themselves. Guidance available In addition to making patches available, Microsoft has published guidance to explain what is necessary in protecting yourself against this Ransomware and any others based on the same vulnerabilities (SMBv1). These vulnerabilities were patched by Microsoft in March of this year, but of course there were no patches (at that time) for unsupported operating systems such as Windows XP. Download Patches for unsupported Operating Systems To patch your unsupported operating systems, get over to this url and download the available patches. WannaCry has multiple vectors, but you should remove one vector, SMBv1. Do as follows 1. Block 445 inbound 2. Install MS17-010 3. Remove SMB1
-

Client Install Issues
anyweb replied to Jordanwaller's topic in System Center Configuration Manager (Current Branch)
what does the ccm.log tell you (on the server), attach it here if you want us to look at it -
hi Eric, what does your execmgr.log reveal ? also, if you find tsagent.log does that have errors ? can you also attach the 3 logs generated by the script in C:\ProgramData
- 242 replies
-
- 1
-

-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-

SCCM Content Library Cleanup
anyweb replied to Scottpowers82's topic in System Center Configuration Manager (Current Branch)
if you create a log file using this switch does it reveal anything ? /log <log file directory> (optional) — the directory to place log files in. Can be a network share. If not specified, the temp folder is used. https://www.niallbrady.com/2017/01/24/what-is-the-contentlibrarycleanup-tool-and-how-can-i-use-it/ -

SCCM 1702 bug to be aware of
anyweb replied to Config Mangler's topic in System Center Configuration Manager (Current Branch)
does the problem only occur when importing Via PowerShell ? if so what's the problem, it will be fixed.. I've pinged Adam to ask when the rollup is coming.... -
so disable it in your lab, does the problem go away in the lab ?
- 13 replies
-
- servicing plan
- windows10
-
(and 2 more)
Tagged with:
-
if you disable the gpo does the problem go away ?
- 13 replies
-
- servicing plan
- windows10
-
(and 2 more)
Tagged with:
-
is the console installed on the computer that you are running the script on ?
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
hi there, it's still supported but i'd consider upgrading now rather than later https://docs.microsoft.com/en-us/sccm/core/plan-design/configs/support-for-sql-server-versions SQL Server 2012 SP2: Standard, Enterprise You can use this version of SQL Server with no minimum cumulative update version for the following: A central administration site A primary site A secondary site
-
where were these programs pinned exactly ? start menu or taskbar ? we are using the Upgrade task sequence and not servicing currently
- 13 replies
-
- servicing plan
- windows10
-
(and 2 more)
Tagged with:
-
every time you upgrade from one version of Windows 10 to the next, you loose access to RSAT as it is not compatible with the new version.
- 13 replies
-
- servicing plan
- windows10
-
(and 2 more)
Tagged with:
-
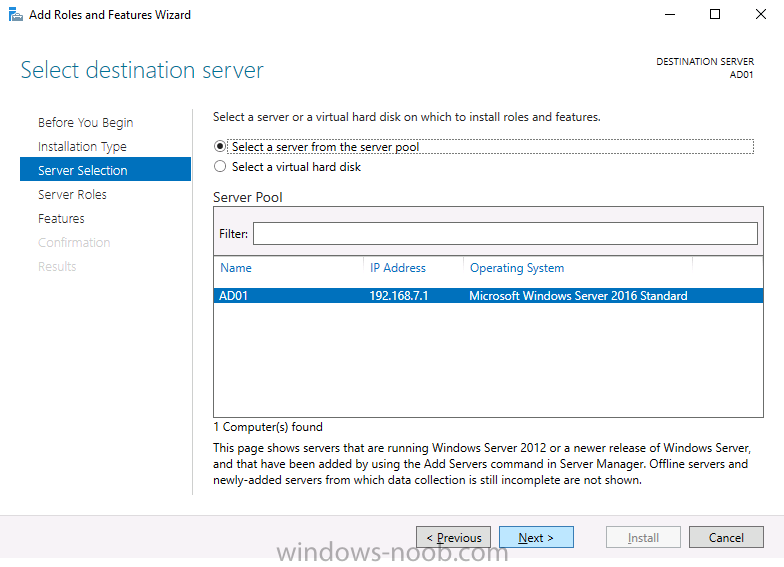
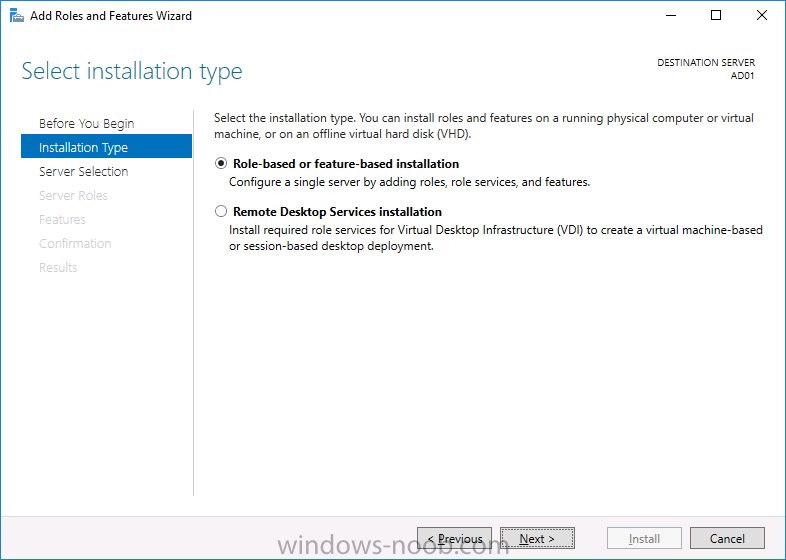
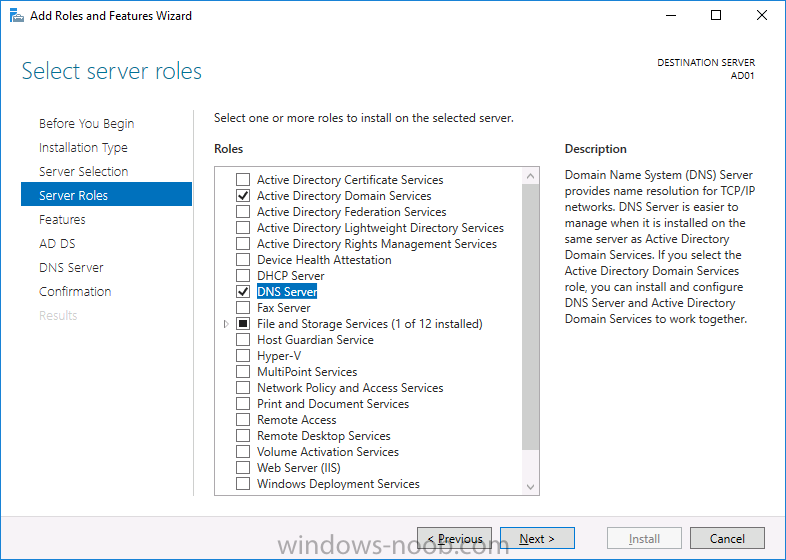
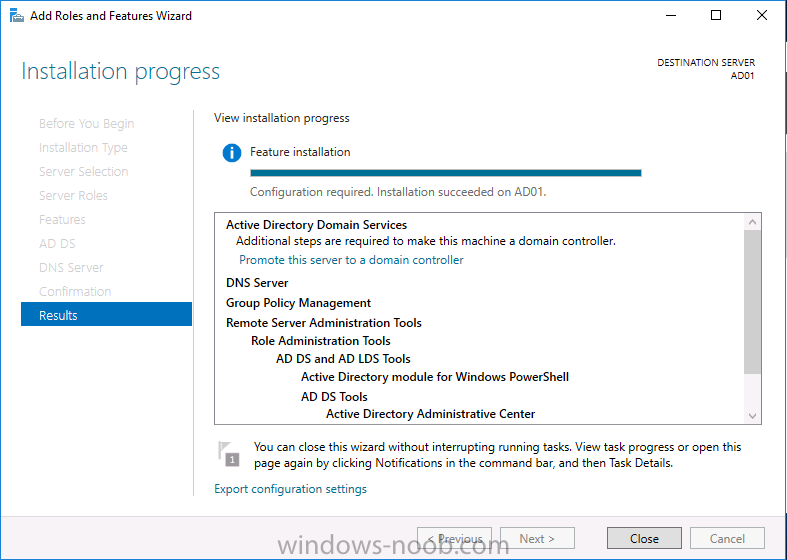
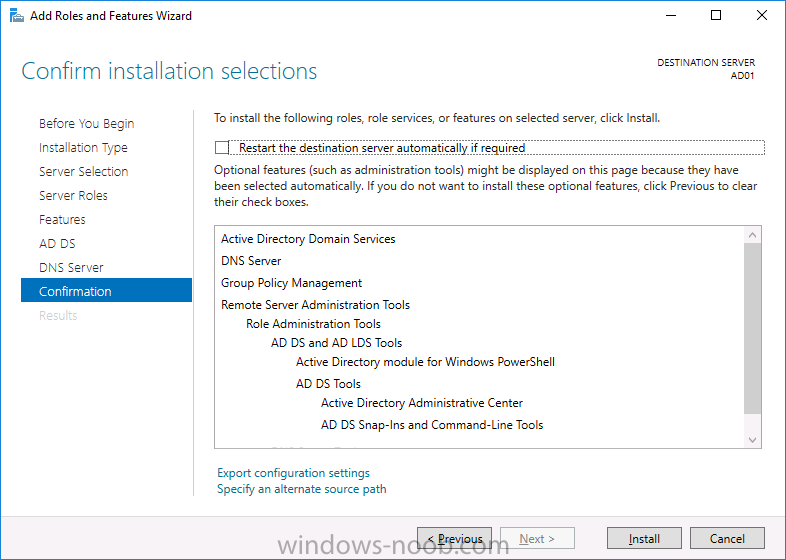
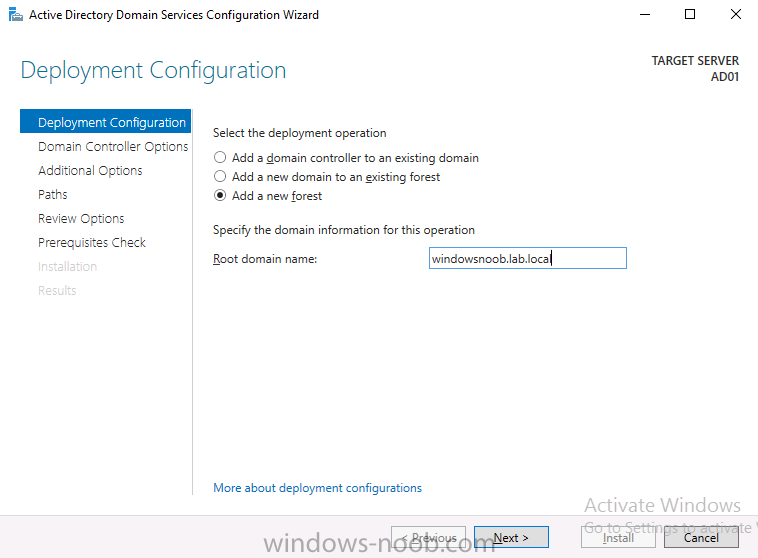
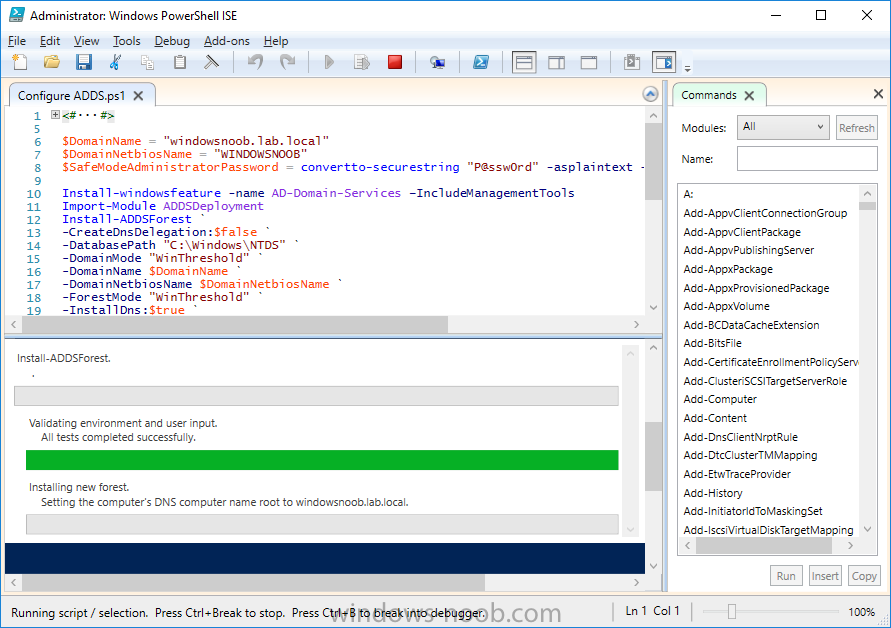
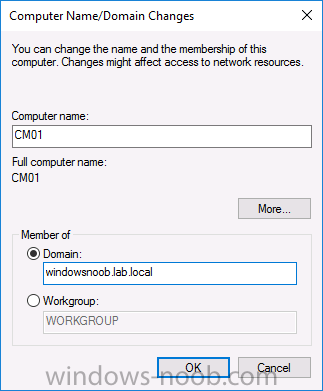
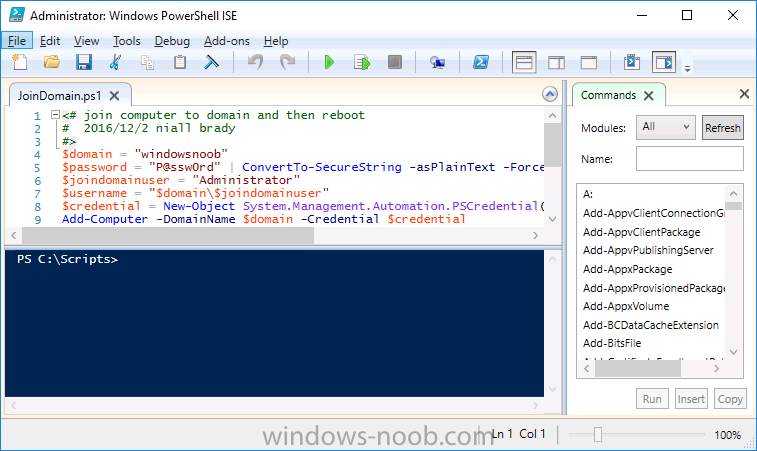
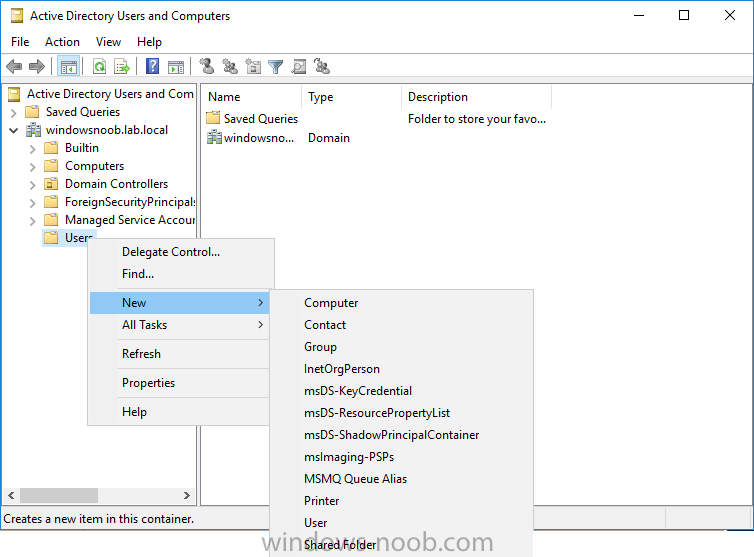
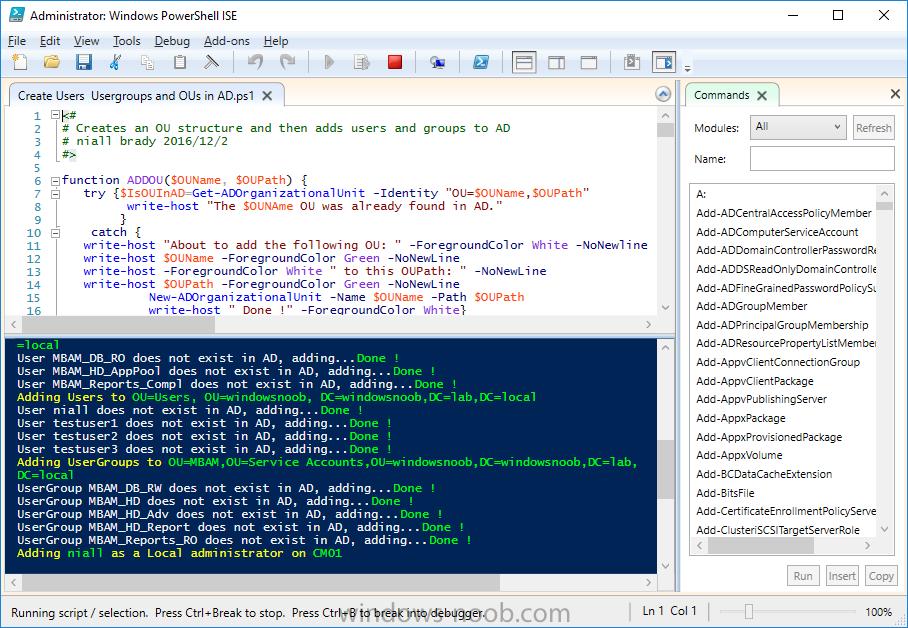
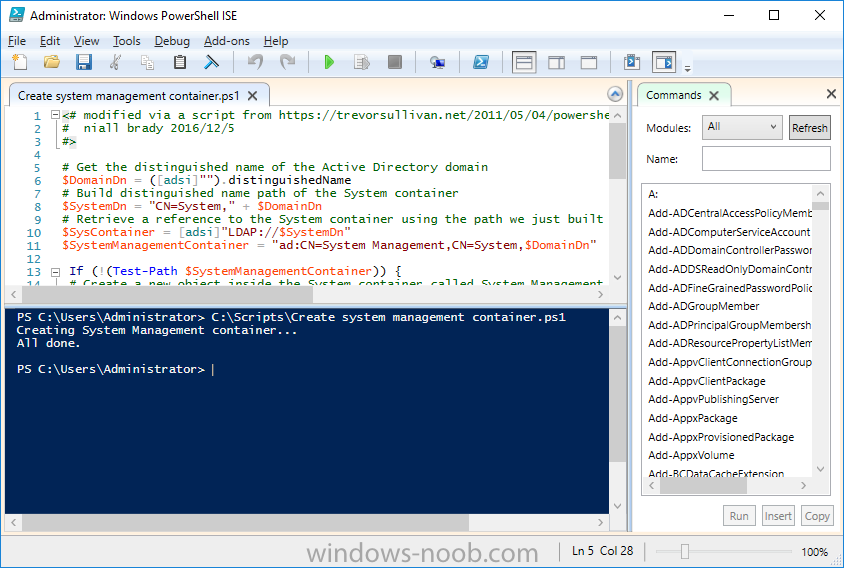
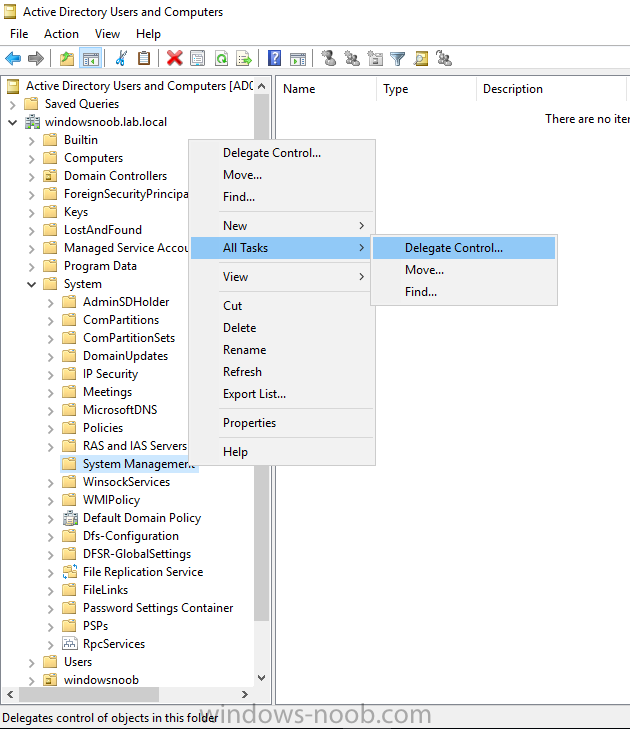
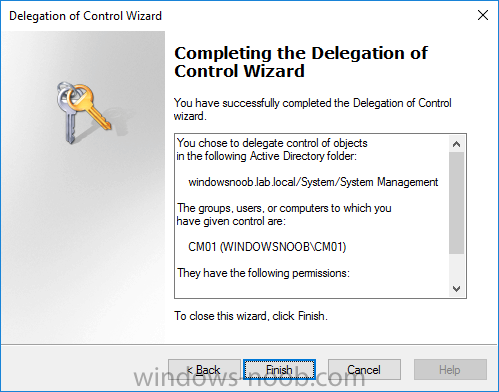
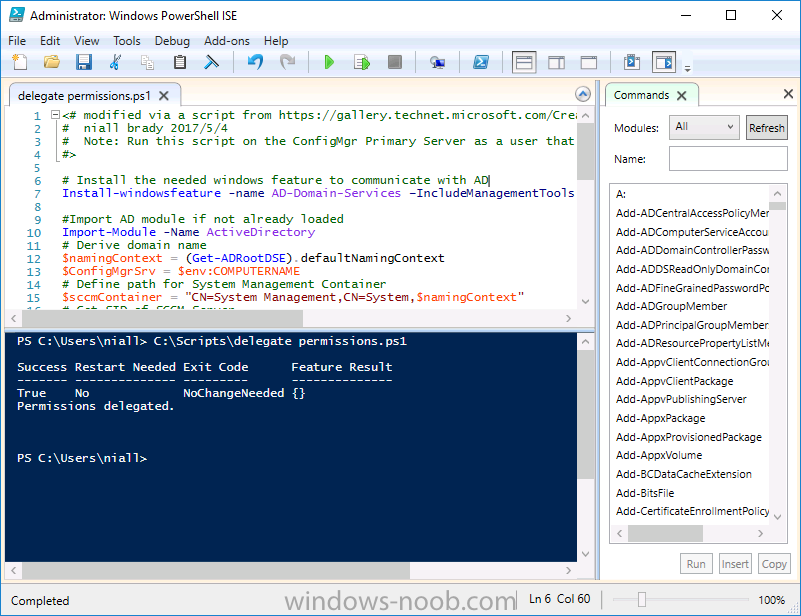
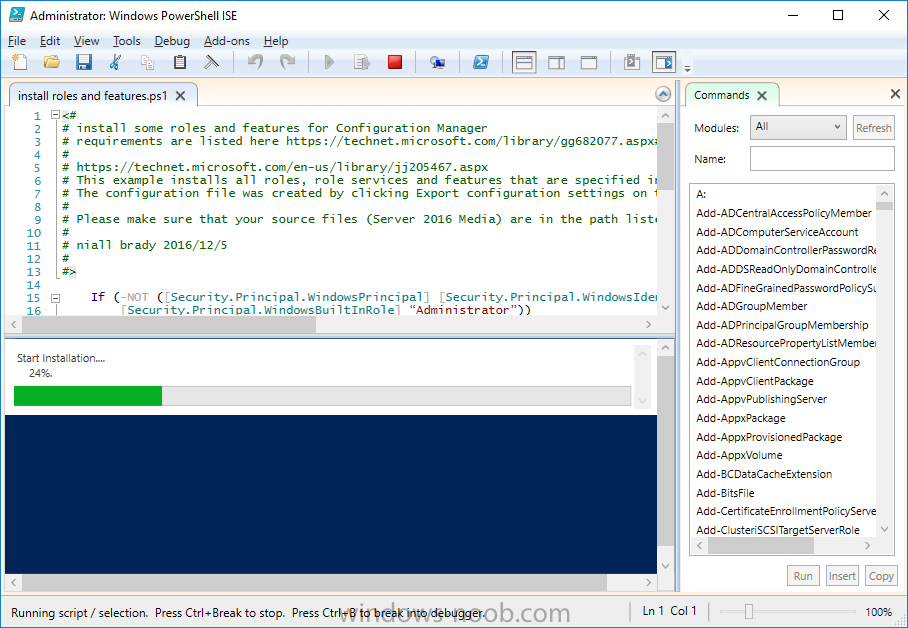
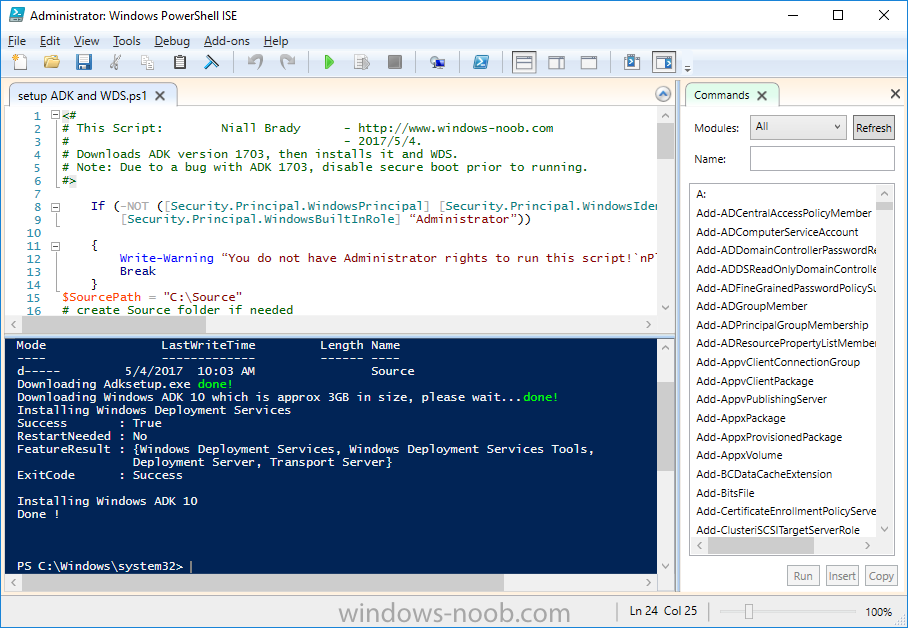
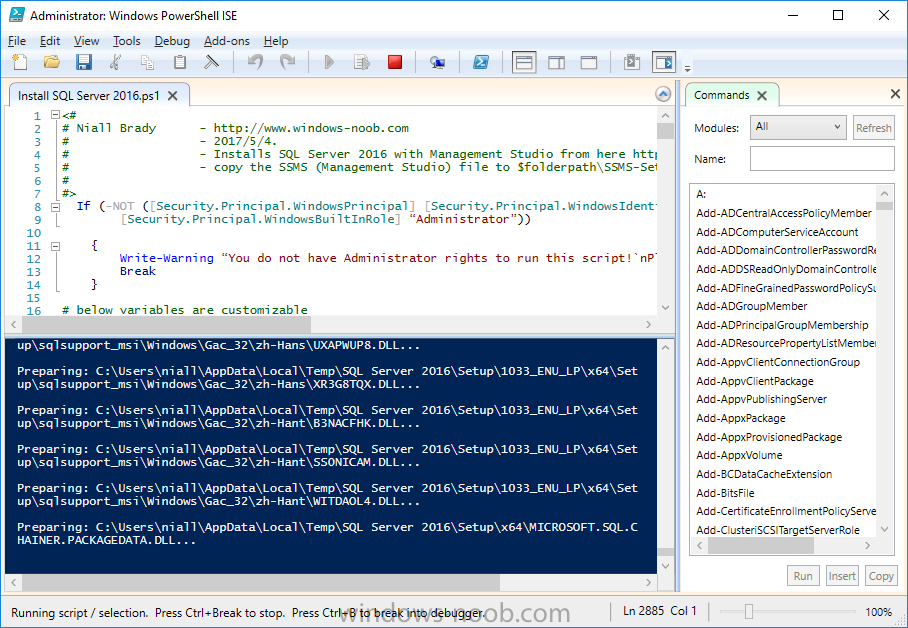
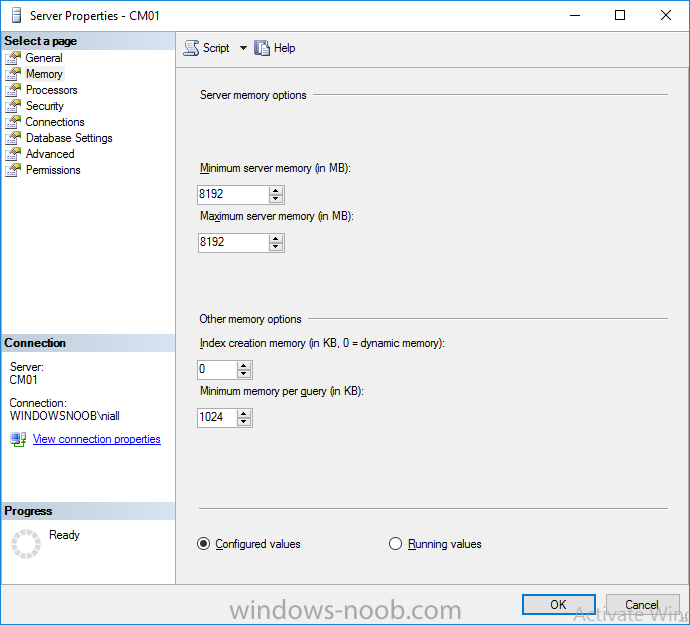
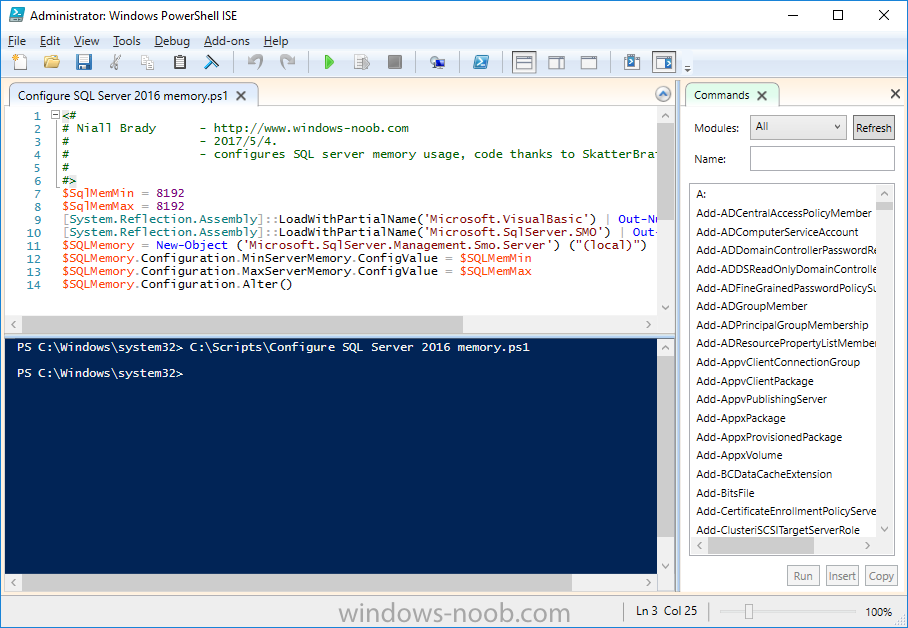
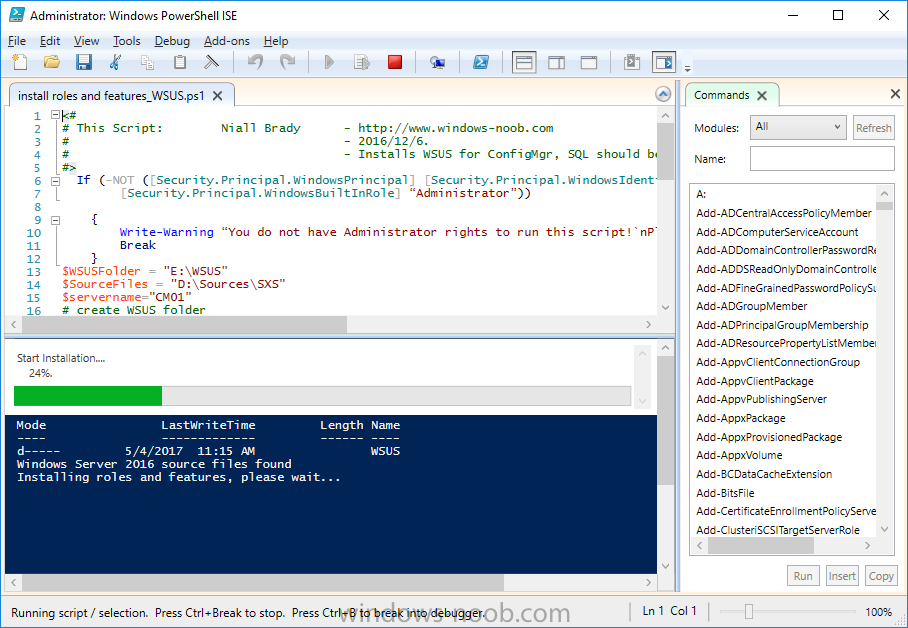
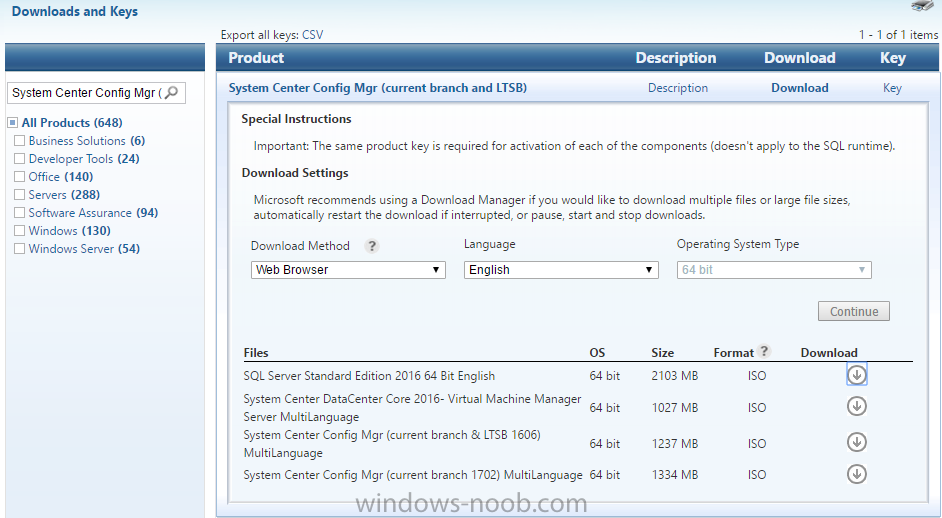
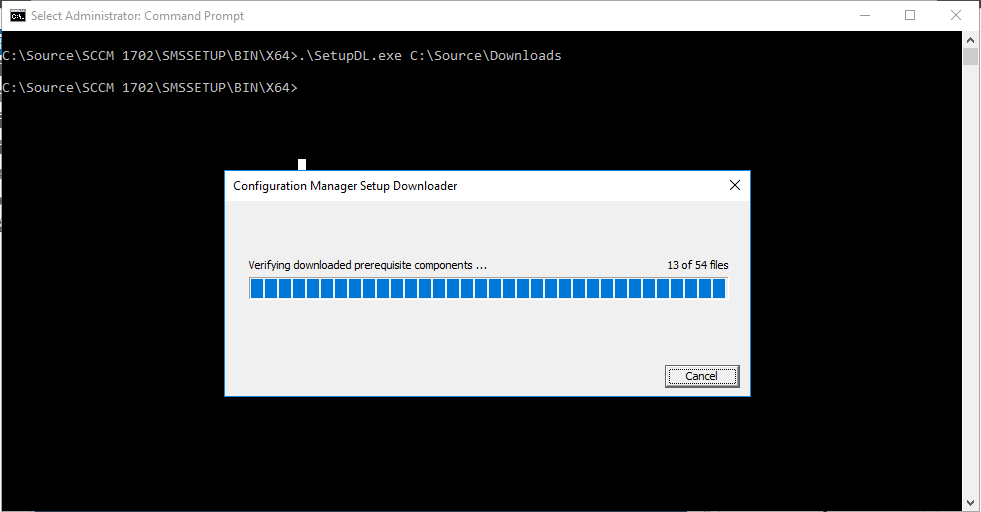
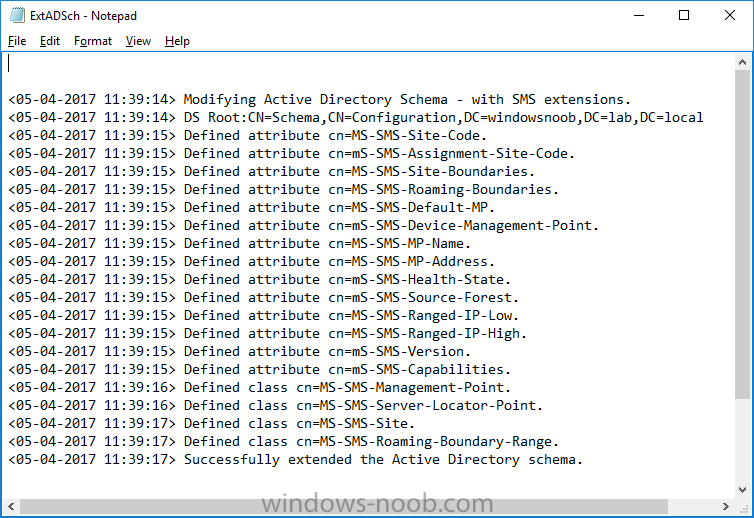
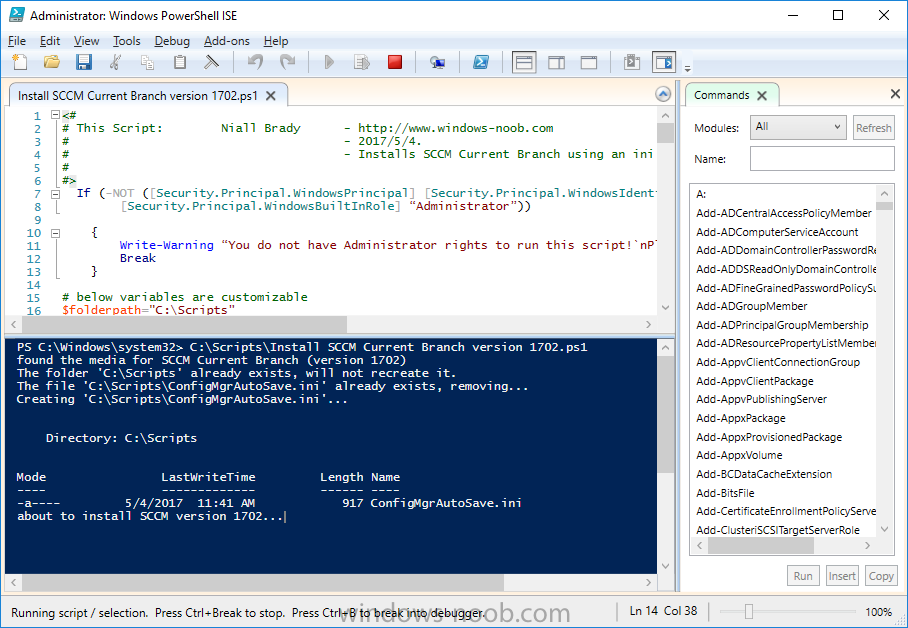
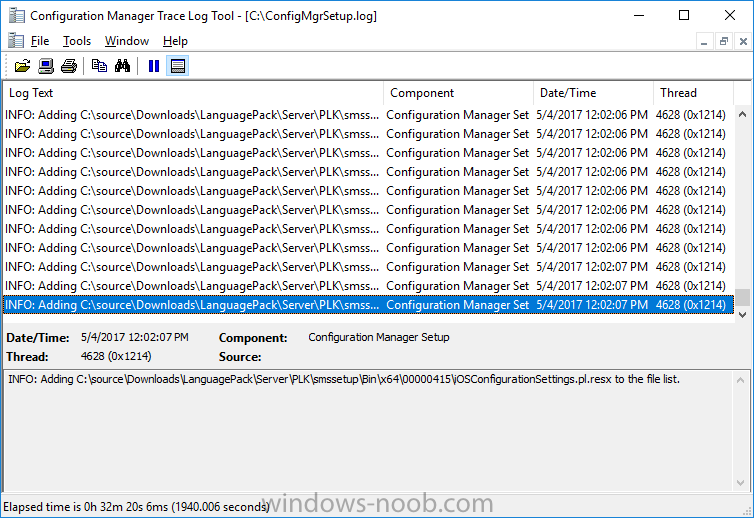
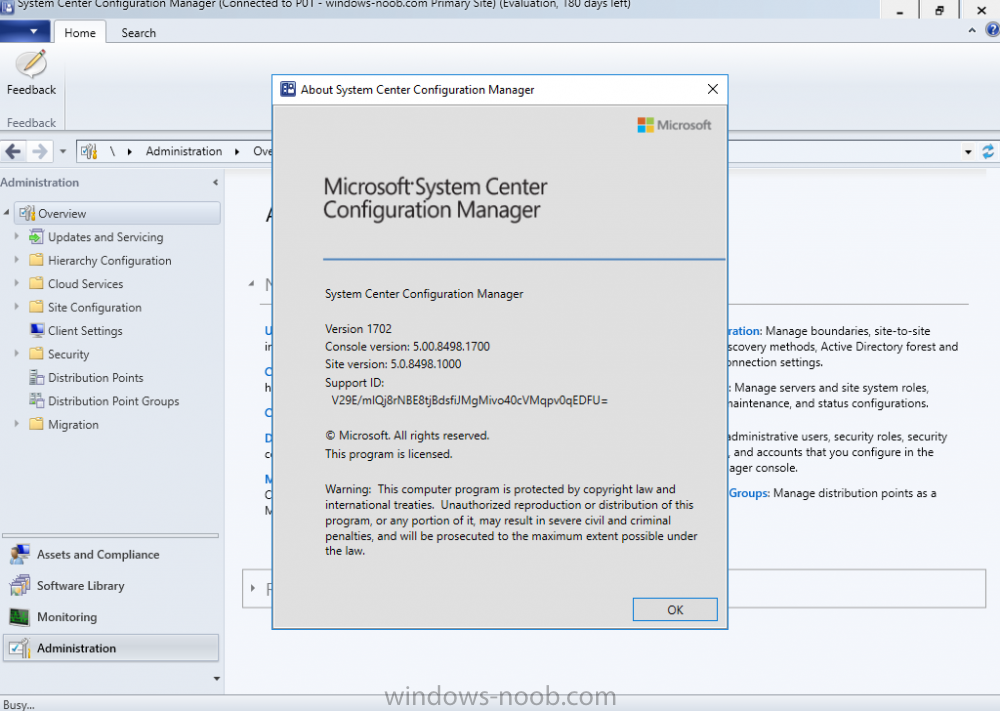
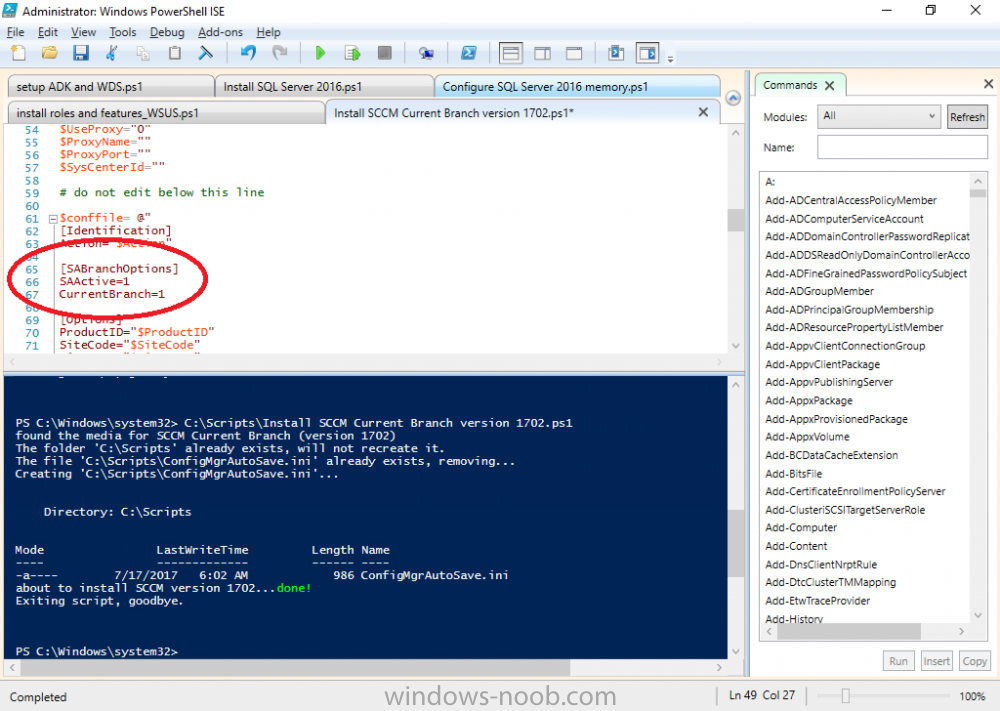
Introduction In a previous guide I showed you how to install System Center Configuration Manager version 1606 (Current Branch) on Windows Server 2016. This guide will show you how to quickly install the latest and greatest baseline version, System Center Configuration Manager version 1702 (Current Branch) on Windows Server 2016 using SQL Server 2016. The concept behind this long and detailed post is to guide you through all the steps necessary to get a working ConfigMgr Primary site installed using manual methods or automated using PowerShell. This is not necessarily a hydration kit, there are many examples out there. Take a look at Johans excellent hydration kits for example. This, on the other hand gives you the power to automate the bits that you want to automate, and manually do other tasks if deemed appropriate. PowerShell knowledge is desired and dare I say it required (if you are in any way serious about ConfigMgr).I will show you how to do most steps via two methods shown below, it's up to you to choose which method suits you best but I highly recommend using PowerShell. Method #1 - Do it manually Method #2 - Automate it with PowerShell Assumptions In this guide I assume you have already installed two workgroup joined servers running Windows Server 2016 (choose Windows Server 2016 Standard (Desktop Experience)) as listed below, and that you've configured the network settings. The network settings I am using for this lab are shown below. Server name: AD01 Server function: Domain Controller Server status: Workgroup joined IPv4 Address: 192.168.7.1 Subnet Mask: 255.255.255.0 Default Gateway: 192.168.7.199 DNS: 192.168.7.1 Server name: CM01 Server function: Configuration Manager Primary site Server status: Workgroup joined IPv4 Address: 192.168.7.2 Subnet Mask: 255.255.255.0 Default Gateway: 192.168.7.199 DNS: 192.168.7.1 Server name: Smoothwall Server function:Linux firewall Server status: 2 legacy nics eth0: 192.168.7.199 eth1: x.x.x.x (internet facing ip) Scripts used in this guide The scripts used in this guide are available at the bottom of the guide in the Downloads section, download them before beginning and extract them to C:\scripts on your destination server(s). Step 1. Configure Active Directory Domain Services (ADDS) Note: Perform the following on the AD01 server as Local Administrator. To setup Active Directory Domain Services you could manually click your way through the appropriate wizard in Server Manager or automate it using PowerShell. For your benefit I'll show you both methods below, all you have to do is choose which one suits you. Method #1 - Do it manually 1. To manually setup ADDS, in the start screen search for Server Manager. Click on Add roles and features 2. For Installation Type choose Role-based or Feature-based installation 3. For Server Selection choose the local server (AD01) 4. For Server Roles select Active Directory Domain Services and DNS Server, when prompted to install any packages accept the changes. 5. Continue the the wizard and click Install 6. Click Close to complete the wizard. 7. After it's finished, perform the Post Deployment Configuration by clicking on Promote this server to a domain controller select the Add a new forest option, give it a root domain name such as windowsnoob.lab.local and click through the wizard, when prompted for a password use P@ssw0rd. and click your way through to completion. Method #2 - Automate it with PowerShell To configure ADDS and DNS automatically, use the ConfigureADDS.ps1 PowerShell script. 1. Copy the script to C:\scripts. 2. Edit the variables as desired before running. 3. Start Windows PowerShell ISE as Administrator and run the script by clicking on the green triangle. Step 2. Join CM01 to the domain Note: Perform the following on the ConfigMgr server (CM01) as Local Administrator Method #1 - Do it manually To join the domain manually, bring up the computer system properties. Click on Change settings beside the computer name, click Change and enter the appropriate domain join details, reboot when done. Method #2 - Automate it with PowerShell To join the domain automatically, use the joindomain.ps1 PowerShell script. 1. Copy the script to C:\scripts. 2. Edit the variables as desired before running. 3. Start Windows PowerShell ISE as Administrator and run the script by clicking on the green triangle. TIP: If DNS is not set correctly on the CM01 Network Properties, then Domain Join will fail, in addition the script currently doesn't check for sucess/failure and will reboot, I'll amend that in the next version. Step 3. Create users Note: Perform the following on the Active Directory Domain Controller server (AD01) as Local Administrator Note: The PowerShell script creates users and makes a user a local admin on the CM01 server. To facilitate the local administrator creation, you'll need to create a GPO on AD01 called Allow Inbound File and Printer sharing exception which sets Windows Firewall: Allow inbound file and printer sharing exception to Enabled. Method #1 - Do it manually To create users manually, add the following users in AD using Active Directory Users and Computers: <your user name>, a domain user, this user will become a local administrator on CM01 Testuser, a domain user CM_BA, used for building ConfigMgr created images CM_JD, used for joining computers to the domain CM_SR used for reporting services. CM_CP, a domain user used when installing the Configuration Manager Client for Client Push. CM_NAA, a domain user, (Network Access Account) used during OSD Step 4. Create the System Management Container Note: Perform the following on the Active Directory Domain Controller server (AD01) as Local Administrator For details of why you are doing this see https://technet.microsoft.com/en-us/library/gg712264.aspx. Method #1 - Do it manually Open ADSI Edit, click on Action, Connect To and click Ok, Double Click on Default Naming Context and the DC= that appears below it. Click on the + and scroll down to CN=System. Right Click on CN=System and choose New, Object, choose Container from the options, click Next and enter System Management as the value. Method #2 - Automate it with PowerShell To create the System Management container automatically, use the Create System Management container.ps1 PowerShell script. Step 5. Delegate Permission Note: Perform the following on the Active Directory Domain Controller server (AD01) as Local Administrator Method #1 - Do it manually Open Active Directory Users and Computers. Click on view, select Advanced Features. Select the System Management Container, and right click it, choose All Tasks and Delegate Control. When the Welcome to Delegation of Control Wizard appears click next, then click Add. click on Object Types, select Computers. Type in your Configuration Manager server name (CM01) and click on Check Names, it should resolve. Click Ok, then Next. Choose Create a Custom Task to Delegate, click next, make sure This folder, existing objects in this folder and creation of new objects in this folder is selected. Click next, select the 3 permissions General, Property-Specific and Creation-deletion of specific child objects are selected then place a check mark in Full Control. Tip: Repeat the above process for each site server that you install in a Hierarchy. Method #2 - Automate it with PowerShell To delegate permissions to the System Management container automatically, use the Delegate Permissions.ps1 PowerShell script on CM01. That's right, on the ConfigMgr server. Note: You need to start Windows PowerShell ISE as a user that has Administrative Permissions in AD. Step 6. Install Roles and Features on CM01 Note: Perform the following on the Configuration Manager server (CM01) as a Local Administrator To support various features in System Center Configuration Manager, the setup wizard requires some Server Roles and Features pre-installed. On CM01, login as the username you added to the Local Administrators group and navigate to C:\Scripts. The XML files within the Scripts Used in This Guide.zip were created using the Export Configuration File option in Server Manager after manually installing roles and features and the accompanying PowerShell script simply installs it. Note: Make sure your Server 2016 media is in the drive specified in the script or edit the script to point to the location of the media. Method #1 - Do it manually The role and feature requirements for ConfigMgr are listed here https://technet.microsoft.com/library/gg682077.aspx#BKMK_SiteSystemRolePrereqs Method #2 - Automate it with PowerShell To install the roles and features needed, start Windows Powershell ISE as Administrator and run the install roles and features.ps1 script. Step 7. Download and install Windows ADK 10 version 1703 and WDS Note: Perform the following on the Configuration Manager server (CM01) as a Local Administrator The ConfigMgr prerequisite checker will check for various things, including ADK components such as USMT and Windows Preinstallation Environment (amongst others), therefore you need to install Windows ADK on your server. To do so, either download ADKsetup from here and manually install it or run the setup ADK and WDS.ps1 PowerShell script to download and install the correct components for you. This script not only downloads the components needed, it's also installs ADK 10 and then installs Windows Deployment Services. The setup ADK and WDS.ps1 PowerShell script is available in the Scripts Used in this Guide zip file. Note: As of 2017/5/4 ADK 1703 has an installation issue that occurs if you have Secure Boot enabled. To workaround this, disable secure boot prior to installing it, you can re-enable secure boot after the installation. Update - Michael Niehaus has a regedit fix detailed here - https://blogs.technet.microsoft.com/mniehaus/2017/05/16/quick-workaround-for-adk-1703-issue/ Method #1 - Do it manually Go to this link and download ADK 1703, install it, then when done, install the Windows Deployment Services service. Method #2 - Automate it with PowerShell To download and then install Windows ADK 10 with the components needed, start Windows Powershell ISE as Administrator and run the setup ADK and WDS.ps1 script. Step 8. Install SQL Server 2016 Note: Perform the following on the Configuration Manager server (CM01) as a Local Administrator The following script will create a ConfigurationFile.ini used to automate the installation of SQL Server 2016, and after it's installed the script will download the SSMS executable (Management Studio) and install it. SQL Server no longer comes with the Management Studio built in, and it's offered as a separate download, don't worry though, my PowerShell script takes care of that for you. Note: Make sure your SQL Server 2016 media is in the drive specified in the script or edit the script to point to the location of the media. Method #1 - Do it manually Install SQL Server 2016 and download and then install SSMS. Method #2 - Automate it with PowerShell To install SQL Server2016 use the Install SQL Server 2016.ps1 script. Note: The script and accompanying INI file have the path pointing at E:\Program Files, please change the path as appropriate. 1. Copy the script to C:\scripts. 2. Edit the variables [lines 17-75] as desired before running. 3. Start Windows PowerShell ISE as Administrator and run the script by clicking on the green triangle. Step 9. SQL Memory Configuration Note: Perform the following on the Configuration Manager server (CM01) as a Local Administrator Depending on your memory configuration and server setup, you may also want to configure SQL memory limits as per the following guidance prior to installing ConfigMgr otherwise you'll get warnings in the Prerequisite checker when it runs the Server Readiness checks. Configuration Manager requires SQL Server to reserve a minimum of 8 gigabytes (GB) of memory for the central administration site and primary site and a minimum of 4 gigabytes (GB) for the secondary site. This memory is reserved by using the Minimum server memory setting under Server Memory Options and is configured by using SQL Server Management Studio. For more information about how to set a fixed amount of memory, see here. If your SQL Server is configured for unlimited memory usage, you should configure SQL Server memory to have a maximum limit. Method #1 - Do it manually Open Management Studio, select CM01, right click, choose Properties, select memory and configure the values as appropriate for your environment. Method #2 - Automate it with PowerShell Use the following PowerShell in ISE on the server that you installed SQL Server 2016 on, thanks go to SkatterBrainz for the code snippet, you might want to adjust the $SqlMemMin and $SqlMemMax variables to suit your environment. Step 10. Restart the ConfigMgr Primary Server Note: Perform the following on the Configuration Manager server (CM01) as a Local Administrator Open an administrative command prompt and issue the following command: shutdown /r Step 11. Install the WSUS role Note: Perform the following on the Configuration Manager server (CM01) as a Local Administrator Now that SQL server is installed, we can utilize SQL Server for the WSUS database. To install WSUS and configure it to use the SQL server database instead of the Windows Internal Database, do as follows: Method #1 - Do it manually Using Roles and Features in Server Manager, add WSUS. Method #2 - Automate it with PowerShell Browse to the location where you extracted the scripts, C:\scripts. Start Windows PowerShell ISE as administrator, open the Install roles and features_WSUS.ps1 script, edit the $servername variable and replace CM01 with the ServerName your are installing ConfigMgr on (SQL server). Note: Make sure to have your Windows Server 2016 SXS media in the path referred to by $Sourcefiles. Step 12. Download and extract the ConfigMgr content Note: Perform the following on the Configuration Manager server (CM01) as a Local Administrator To install System Center Configuration Manager version 1702 you'll need to download the content. You can download it from Microsoft's Volume licensing Service Center site for use in production or from MSDN for use in a lab. The VLSC download can be found be searching for Config and then selecting System Center Config Mgr (current branch and LTSB) as shown below. Method #1 - Do it manually For the purposes of this guide I used the 1702 release from VLSC. This iso is named: SW_DVD5_Sys_Ctr_ConfigMgrClt_ML_1702_MultiLang_ConfMgr_SCEP_MLF_X21-37386.ISO Once downloaded, I mounted the ISO in Windows File Explorer and copied the contents to C:\Source\SCCM 1702 on CM01. Step 13. Download the ConfigMgr Prerequisites Note: Perform the following on the Configuration Manager server (CM01) as a Local Administrator Method #1 - Do it manually You can download the prerequisites during ConfigMgr setup or in advance. As you'll probably want to install more than one copy of ConfigMgr (one lab, one production) it's nice to have the prerequisites downloaded in advance. To do that, open a PowerShell prompt with administrative permissions and navigate to the following folder: C:\Source\SCCM 1702\smssetup\bin\X64 Run the following line .\SetupDL.exe C:\Source\Downloads Tip: Browse to C:\source\SCCM 1702\SMSSETUP\TOOLS and double click on CMTrace.exe, answer Yes to the default logging question. Then, using Windows File Explorer, browse to C:\ and double click on ConfigMgrSetup.log which will open the log file in CMTrace. This will allow you to view any errors or problems with the download of the prerequisites in real time. Method #2 - Automate it with PowerShell Coming soon. Step 14. Extend the Schema Note: Perform the following on the Domain controller server (AD01) as Administrator. You do not have to extend the Active Directory schema if it was already extended for Configuration Manager previously. Method #1 - Do it manually 1. Using Windows File Explorer on the Active Directory Domain Controller, browse to \\<server>\c$\Source\SCCM 1702\SMSSETUP\BIN\X64 where <server> is your ConfigMgr server 2. Locate extadsch.exe, right click and choose Run As Administrator. 3. A command prompt window will appear briefly as the schema is extended, check in C:\ for a log file called ExtADSch.log it should look similar to this Method #2 - Automate it with PowerShell Coming soon. Step 15. Install SCCM Current Branch (version 1702) Note: Perform the following on the ConfigMgr server (CM01) as Administrator. Note: If you are NOT using an evaluation version of SCCM then you need to add the section below in blue to the configuration.ini file which is contained within the PowerShell script, and you need to change the ProductId open the script in Windows ISE, locate the line that reads $ProductID= and enter your ConfigMgr Product Key. [SABranchOptions] SAActive=1 CurrentBranch=1 Method #1 - Do it manually Install SCCM Current Branch using the wizard. Method #2 - Automate it with PowerShell You will need to edit the Install SCCM Current Branch version 1702.ps1 script and replace the variables inside with those that work in your environment. 1. Copy the script to C:\scripts. 2. Edit the variables [lines 16-17 & lines 32-57] as desired before running. 3. Start Windows PowerShell ISE as Administrator and run the script by clicking on the green triangle. Tip: Use CMTrace to open C:\ConfigMgrSetup.log to monitor the installation of ConfigMgr as it happens. Once the script completes successfully, System Center Configuration Manager Current Branch (version 1702) is installed. Success ! Summary In this guide you used quite a bit of PowerShell to automate pretty much most of Installing System Center Configuration Manager Current Branch (version 1702), including installing and configuring SQL Server 2016 on Windows Server 2016. Doing it this way means you can safely say that you've got a handle on Automation using PowerShell, heck, you could even call yourself a 'geek with an attitude'. I hope you learned a lot from doing it this way, and until next time, adios ! Downloads The scripts used above are available in the zip below. Scripts.zip