Search the Community
Showing results for tags 'Conditional Access'.
-
Are you planning to deploy Microsoft Intune and looking for straightforward technical guidance to help you accelerate this effort? Please join us as we share our deployment experience working with customers from all over the world, covering Intune pilot planning, deployment and management. At the en...
-
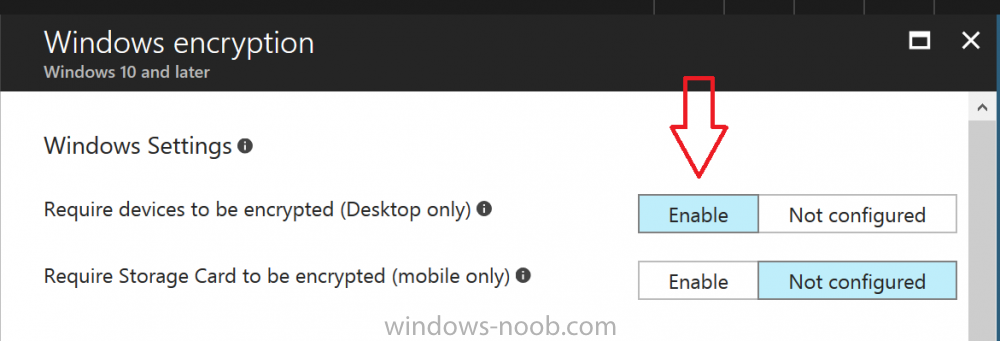
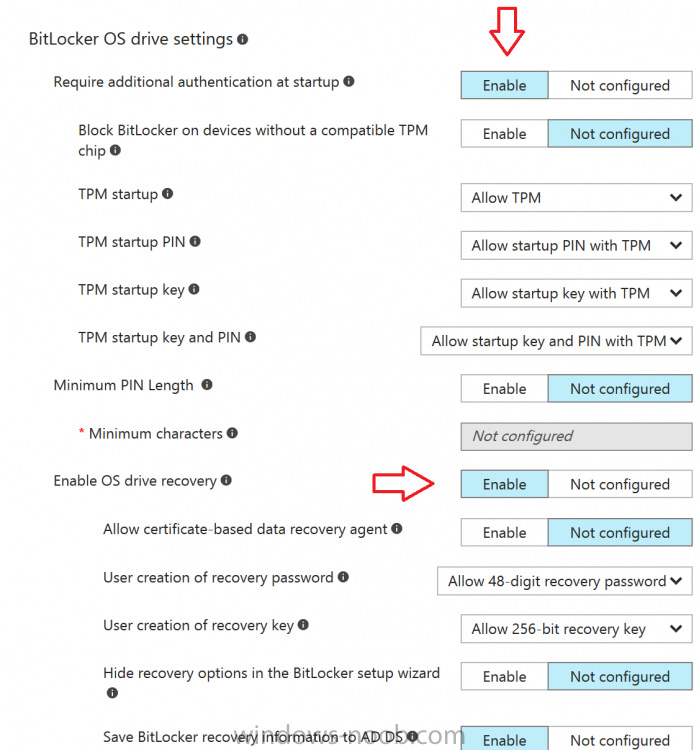
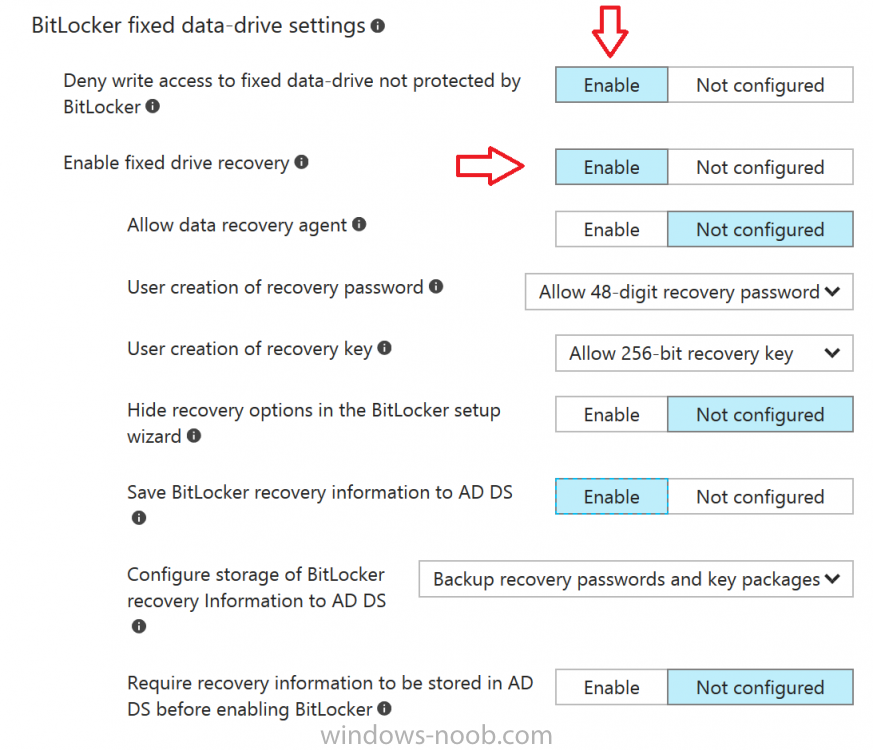
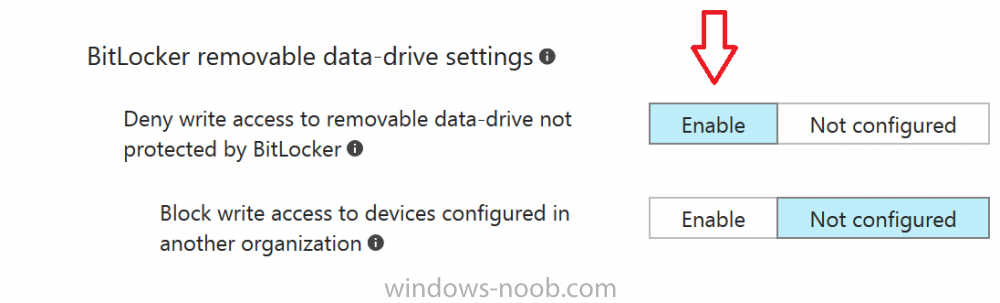
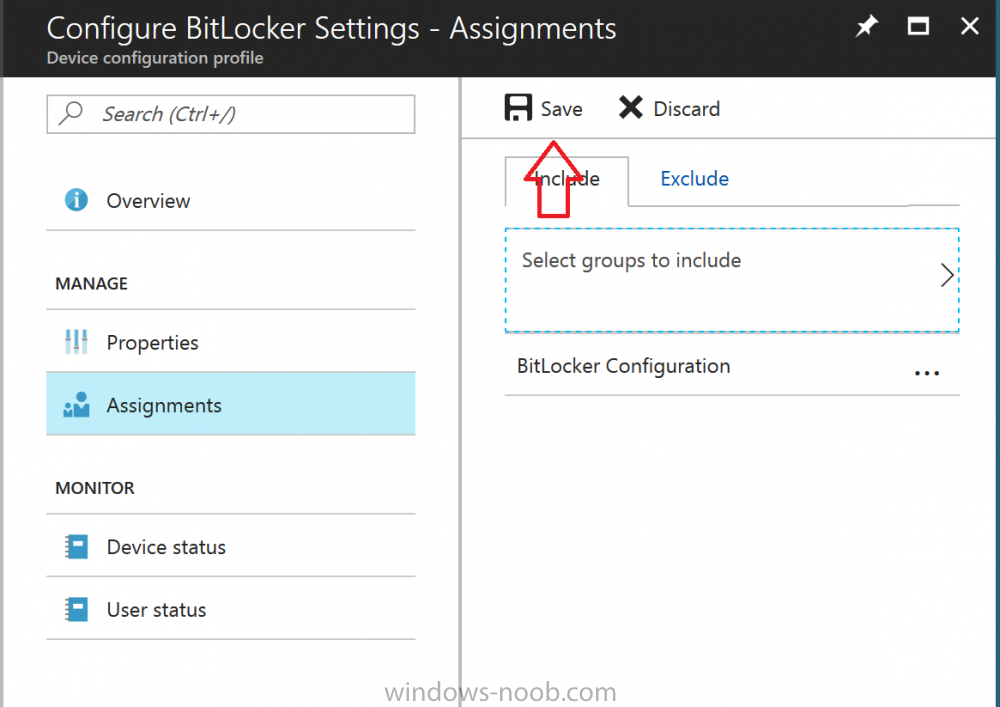
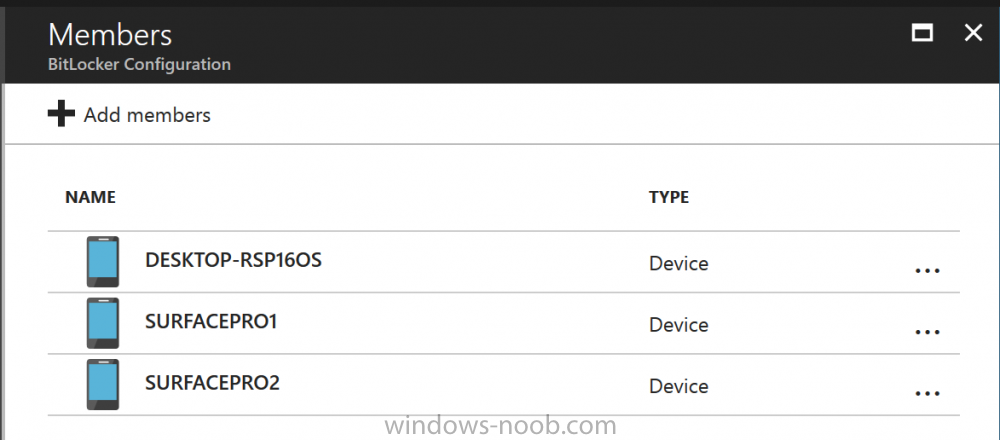
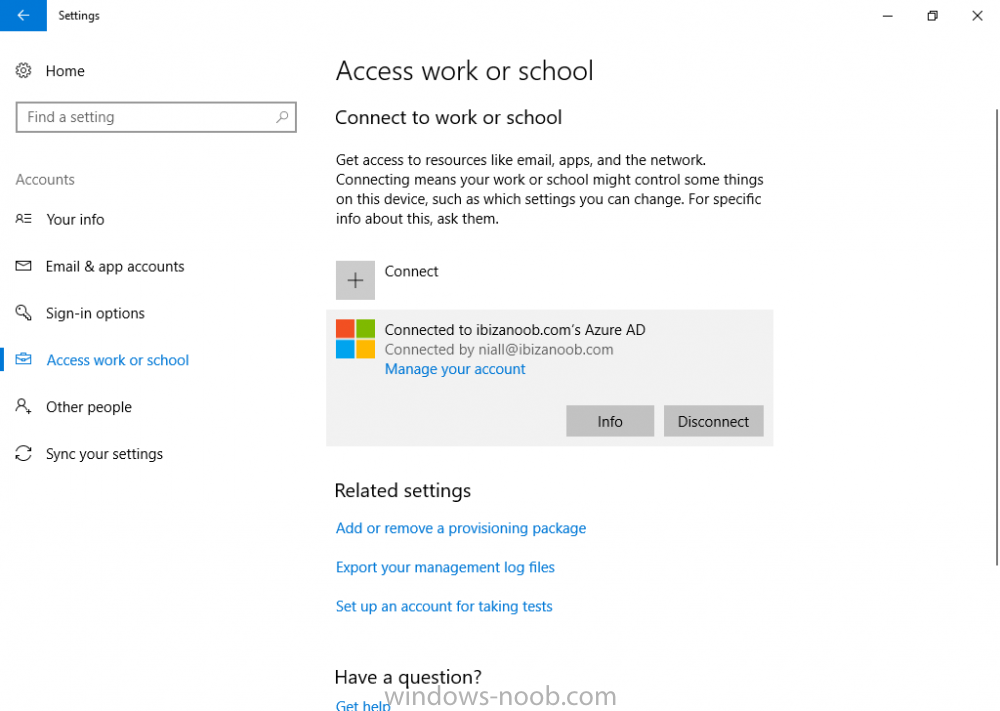
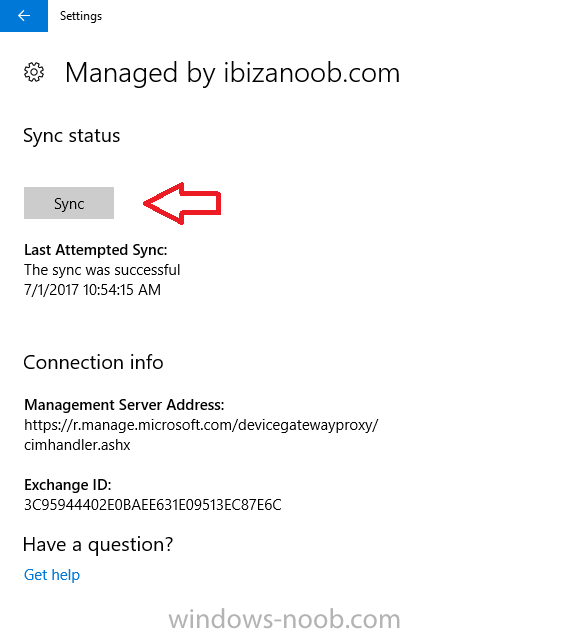
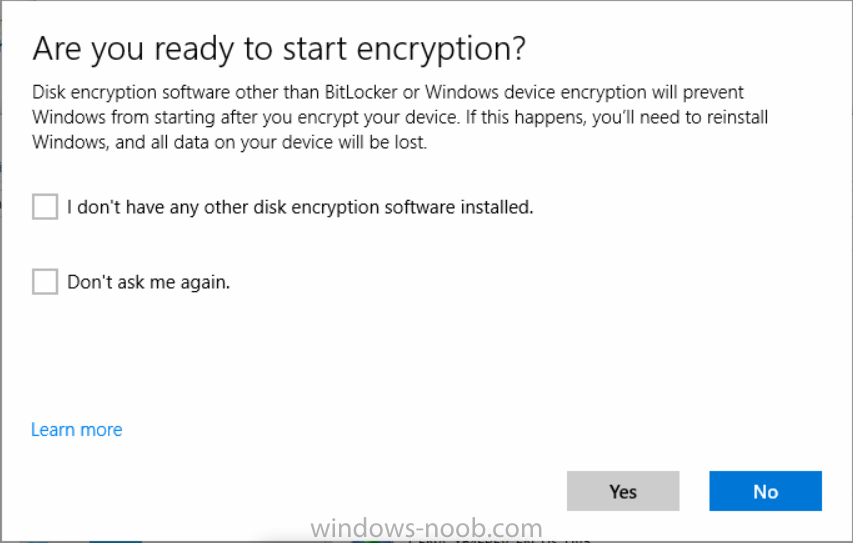
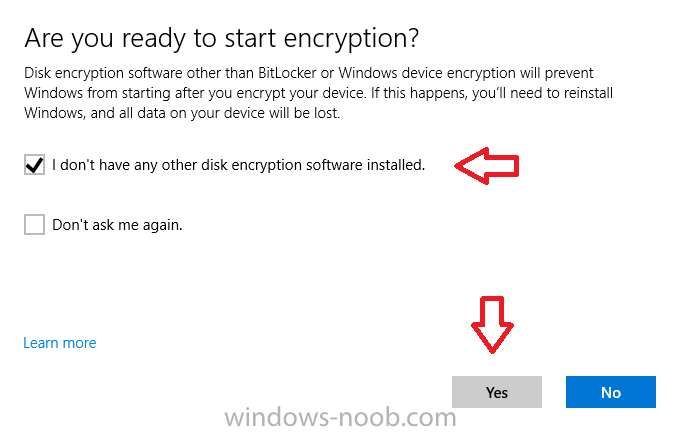
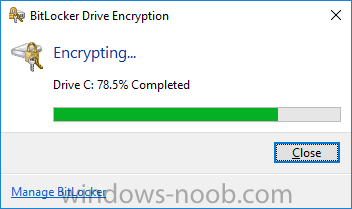
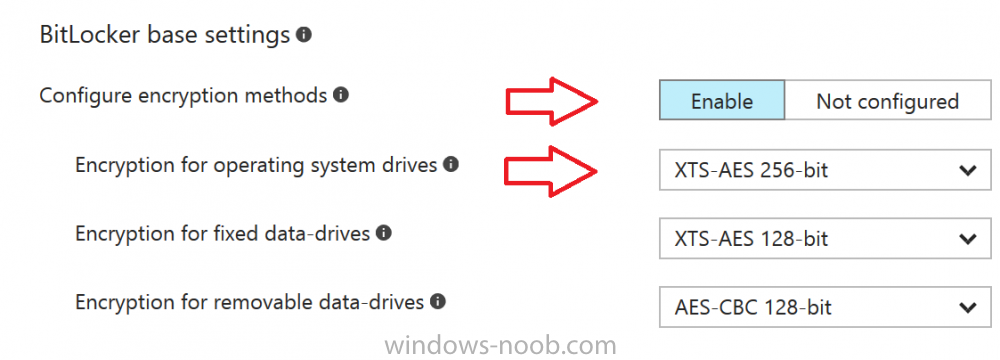
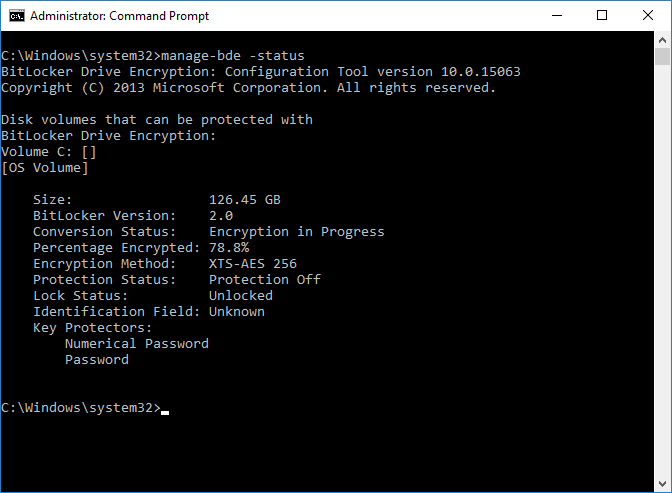
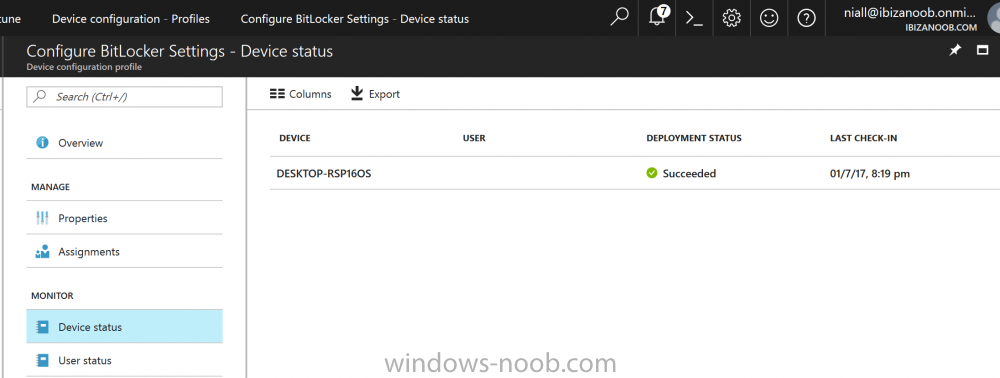
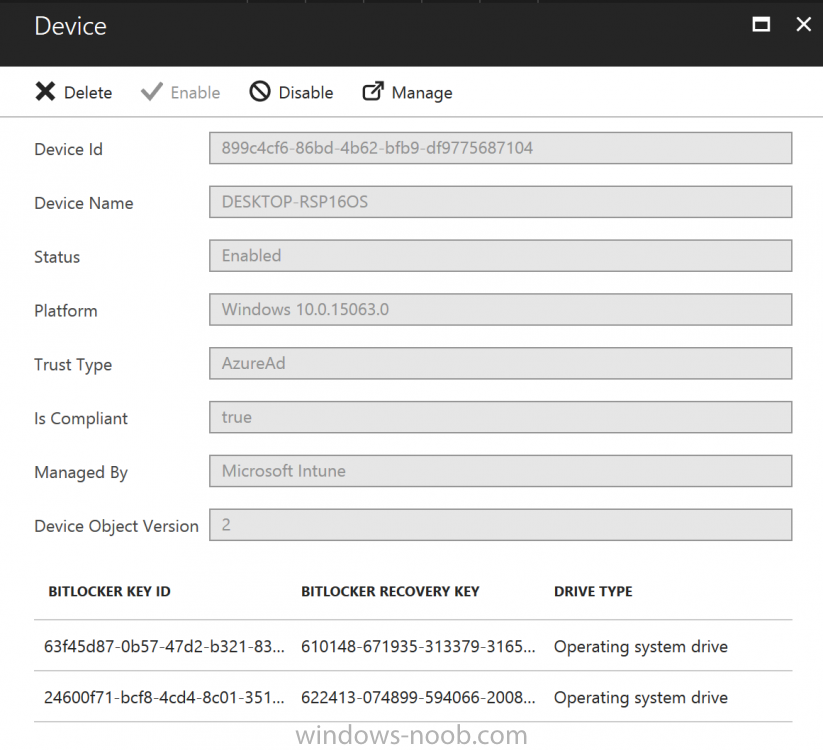
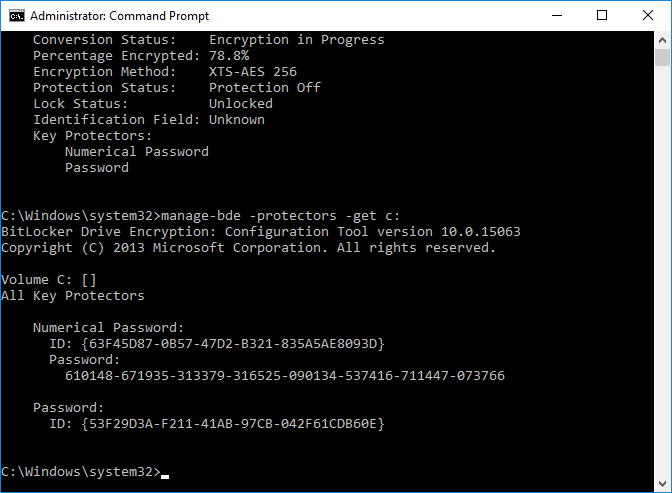
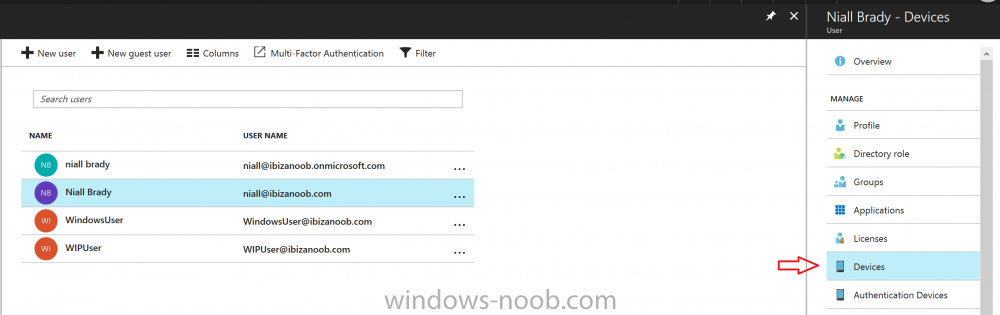
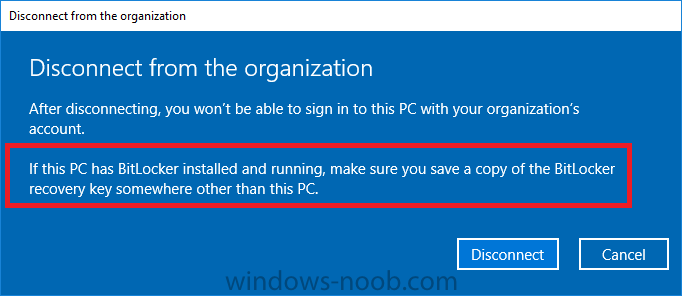
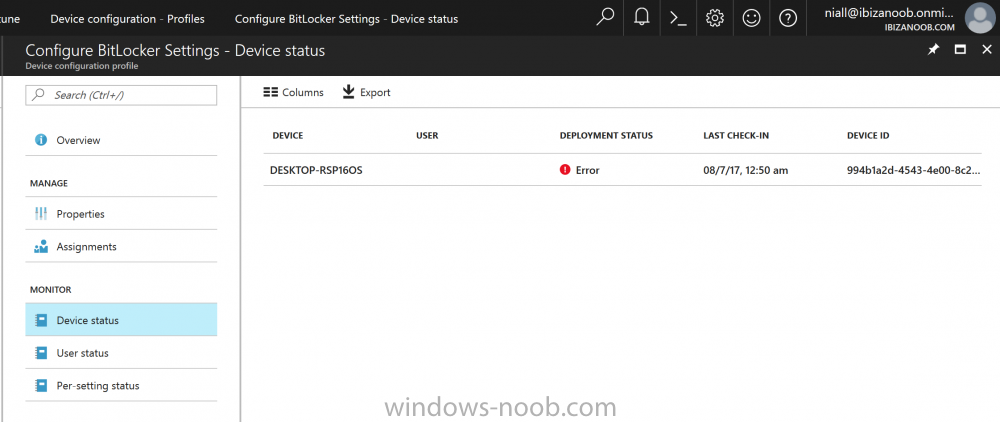
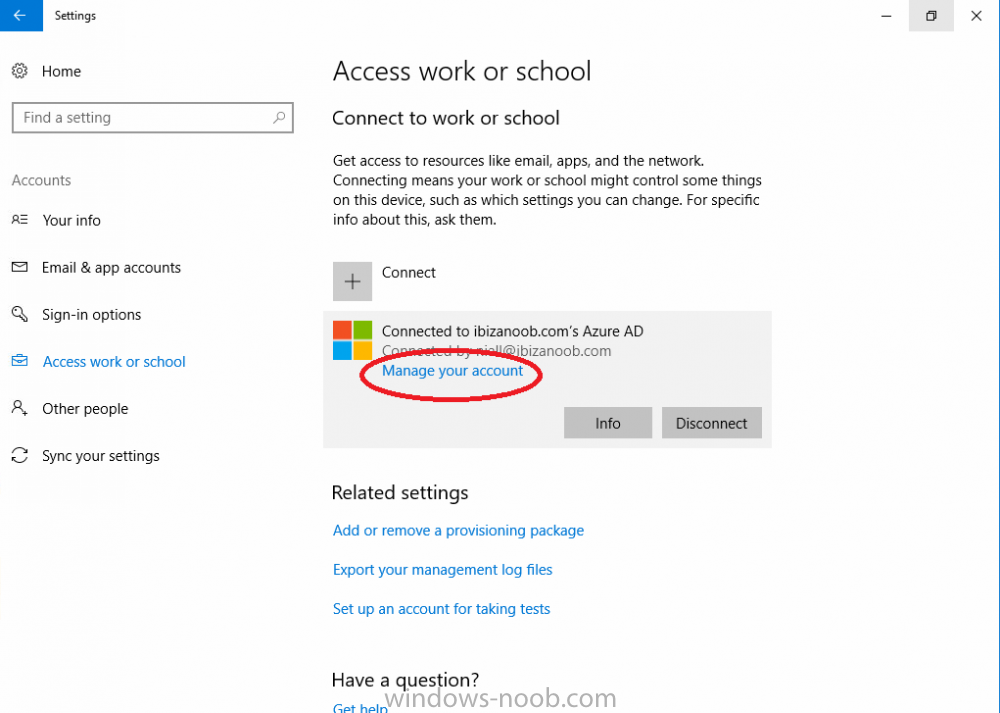
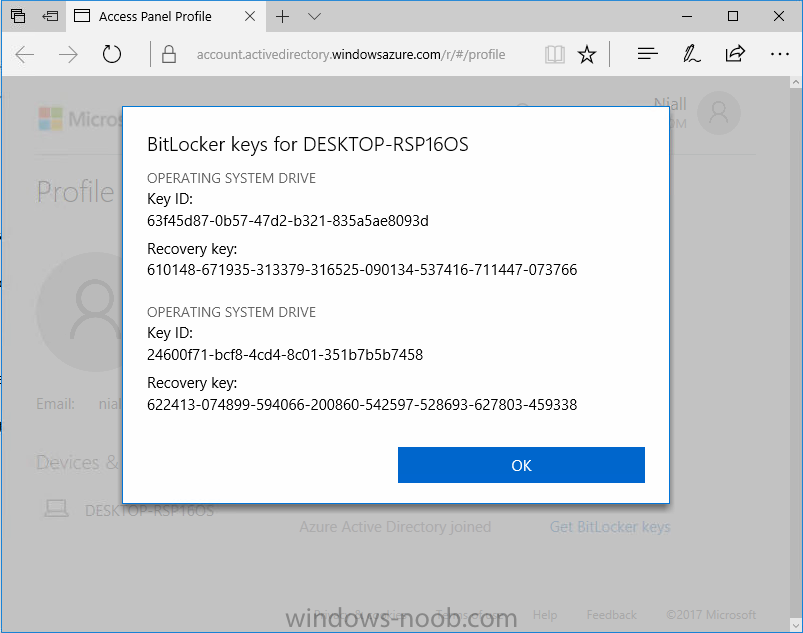
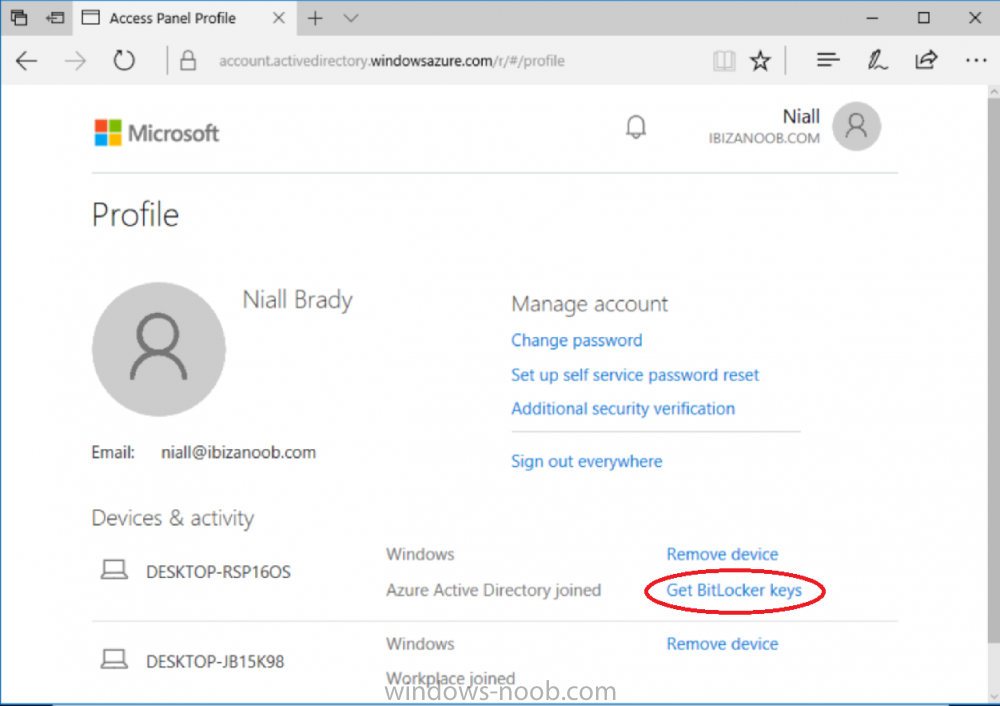
Introduction Security is a big focus for many companies, especially when it comes to data leakage (company data). Encrypting data on Windows 10 devices using BitLocker means that data is protected ("data at rest") . Microsoft Intune got yet more updates on June 30th, 2017, one of which was the...
-
Hi All, Wondering how others are forcing existing Exchange ActiveSync users to enroll in Intune. I've setup Intune integrated into our SCCM Current Branch (1602) environment and configured the Exchange Server Connector to sync devices from our On-Premise Exchange 2013 environment. All EAS device...
- 1 reply
-
- 1
-

-
- Conditional Access
- EAS
-
(and 1 more)
Tagged with:
-
Hi guys, The Microsoft documentation on this is looking pretty sparse on these topics. Does anyone know if it is possible to provision conditional access for mail when InTune is integrated with ConfigMgr? If so, is the process different at all from setting up conditional access when d...
- 1 reply
-
- Intune
- Mail Profiles
-
(and 1 more)
Tagged with: