Search the Community
Showing results for tags 'Software Updates'.
-
In my Windows 10 LTSC 1809 task sequence, the Install Software Updates step is failing to run. I have attached the log files for the latest attempt to build a test machine. I have deployed the required software update group to both the Unknown Computer collection (as I am deleting the SCCM object for the test machine before each test build) and to a common collection that all of the test machines are put into. The machine does receive and install updates post-build successfully so it is not the software update group or the deployment package as far as I can tell. smsts.zip UpdatesDeployment.log UpdatesHandler.log UpdatesStore.log WUAHandler.log
-
- windows 10
- sccm
-
(and 1 more)
Tagged with:
-
Hi, I have to deploy windows updates on critical servers which gets patched very rarely due to some team dependency. I have SCCM CB 1706 installed. My client set below conditions: 1. Updates should get downloaded beforehand 48 hours actual Installation date. 2. If needed, installation time may change. Deployment should accomodate that. 3. Deployment time is 2 hours for 1 batch. So in case if deployment gets carried over 2 hours, second batch should not start. How to achieve this 1. Without maintenance window 2. With maintenance window 3. Any other way apart from above 2 options
-
Hello Everyone, I want to get in the habit of cleaning up my SUGs created by my ADRs. I'd like to do this every 6 months but I've run into a problem. Within one of my ADRs, for example, I have the following set for the 'Title' options: -Preview -Security Only Quality Update -Security Only Update -x86 If I want to roll-up updates from the last 6 months into a single SUG, I am unable to enter in these items for the 'Title' option when searching from the 'Software Updates' node. I can only choose one. Aside from that, what is the best practice for rolling up these patches? Do I delete the SUGs, delete the content within the current package, and then when the next ADR runs things will have a fresh start? My SCEP ADR uses the same SUG so what is the best method of cleaning that up?
- 1 reply
-
- software updates
- windows update
-
(and 3 more)
Tagged with:
-
Hi guys, I am currently looking at the patch status of our devices, especially given everything that's happening at the moment. When I filter on Security Updates, I can see an update (KB4019472 for example) and the required column says 4, but I have at least 200 devices that should be requesting that patch. What am I missing? The Software Updates section for my clients are:- Enable Software Updates = Yes Software update scan schedule = Simple schedule running every day Schedule deployment re-evaluation = Simple schedule running every day When any sofwtare deployment deadline is reached..... = No Enable Management of Office 365 Client Agent = Not Configured If you need any more information then let me know. thanks, James
-
We are upgrading to Current Branch and want to include patching from this and not WSUS as curretly used. what is the best way to patch 3rd party applications through SCCM Current Branch?
- 5 replies
-
- software updates
- 3rd party
-
(and 1 more)
Tagged with:
-
Hi. I'm having a bit of trouble with a task sequence. Everything runs fine and quick, until 'Running Action: install Software Updates'. It seems to hang/stall at 60% for hours. I can't see anything in the logs that obvious. I have a Primary in DomainA, and a Secondary in DomainB, and a DP off the Secondary in DomainB. The client PXE boots off the DP, seems to to do everything fine until the 'Install Software Updates' part. It does eventually complete after a few hours. As far as I can tell, all the updates are distributed to the DP. Can anyone point me in the right direction of where to look. Thanks.
- 5 replies
-
- sccm
- current branch
-
(and 4 more)
Tagged with:
-
Hello all, On Tuesday afternoon I searched for the new updates and nothing showed up. I figured I might be too early so I went about my business. This morning (Thursday) I searched and it still finds no updated released in the last month. I searched the last 2 months and it found the November Rollups that have already been deployed. Last month in our monthly maintenance window we updated to CU4. Could that be the problem? I have not heard of any issues regarding CU4, although it's still early in it's release. I am not even sure where to look to see why it's not finding the latest updates.
-
Hello All, I have a Powershell script that I use to create multiple Software Update Deployments and it works perfectly (well almost). The last piece I'm missing is automating the deadline date. Currently I just have it getting the current date and adding 5 days. I then go into each deployments properties and change the date/time to the desired info. I've been trying to work out automating this a little bit by adding a variable for a static date/time. I can then change this date (time will always be the same) to the desired info at script run. Below is what I've come up with so far. The -EnforcementDeadlineDay piece works on it own, in that it outputs the correct date with an incremented time. However once I put it in the full script i get the below errors. Any help is much appreciated. Cheers, Mike Script: # Monthly Deployment Date #$DeploymentDate = Get-Date -Format "yyyy-MM" $DeploymentDate = (Get-Date).AddDays(-30).ToString("yyyy-MM") $DeadlineDate = Get-Date -Month 08 -Day 07 -Year 2016 -Hour 17 -Minute 0 -Second 0 # Software Update Groups $SUPGroupName1 = "EN5 - EDC - Year 2013- ($DeploymentDate) Reference 1" $SUPGroupName2 = "EN5 - EDC - Year 2013+ ($DeploymentDate) Reference 2" #Load Configuration Manager PowerShell Module Import-module ($Env:SMS_ADMIN_UI_PATH.Substring(0,$Env:SMS_ADMIN_UI_PATH.Length-5) + '\ConfigurationManager.psd1') #Get SiteCode and set Powershell Drive $SiteCode = Get-PSDrive -PSProvider CMSITE Set-location $SiteCode":" # Create Standard Deployments (Group 1) $DeploymentName = "EN5 - PM Dev ($DeploymentDate) Reboot Deployment # 1" $DeploymentCount = 6 $Count = 0 1..$DeploymentCount | ForEach-Object { $Count++ Write-Progress -Activity "Creating Deployment Group 1" -Id 1 -Status "Running $($Count) / $($DeploymentCount)" -PercentComplete (($Count / $DeploymentCount) * 100) Start-CMSoftwareUpdateDeployment -SoftwareUpdateGroupName "$SUPGroupName1" -CollectionName "EN5 - PM - Deployment $Count (Lab)" -DeploymentName "$DeploymentName-$Count" -DeploymentType Required -VerbosityLevel AllMessages -TimeBasedOn LocalTime -DeploymentAvailableDay (Get-Date) -EnforcementDeadlineDay $DeadlineDate.ToLongDateString()$DeadlineDate.Addhours($Count).ToLongTimeString() -UserNotification HideAll -SoftwareInstallation $True -AllowRestart $True -RestartServer $False -RestartWorkstation $False -ProtectedType RemoteDistributionPoint -UnprotectedType UnprotectedDistributionPoint -GenerateSuccessAlert $False -DisableOperationsManagerAlert $False -GenerateOperationsManagerAlert $False -PersistOnWriteFilterDevice $False -UseBranchCache $False } Write-Progress -Activity "Creating Deployment Group 1" -Id 1 -Completed Errors: Start-CMSoftwareUpdateDeployment : A positional parameter cannot be found that accepts argument '6:00:00 PM'. At E:\scripts\EN5 - CreateDeployments - LAB.ps1:24 char:5 + Start-CMSoftwareUpdateDeployment -SoftwareUpdateGroupName "$SUPGroupName1" - ... + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : InvalidArgument: ( [Start-CMSoftwareUpdateDeployment], ParameterBindingException + FullyQualifiedErrorId : PositionalParameterNotFound,Microsoft.ConfigurationManagement.Cmdlets.Sum.Commands.StartSoftwareUpdateDeploymentCommand Start-CMSoftwareUpdateDeployment : A positional parameter cannot be found that accepts argument '7:00:00 PM'. At E:\scripts\EN5 - CreateDeployments - LAB.ps1:24 char:5 + Start-CMSoftwareUpdateDeployment -SoftwareUpdateGroupName "$SUPGroupName1" - ... + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : InvalidArgument: ( [Start-CMSoftwareUpdateDeployment], ParameterBindingException + FullyQualifiedErrorId : PositionalParameterNotFound,Microsoft.ConfigurationManagement.Cmdlets.Sum.Commands.StartSoftwareUpdateDeploymentCommand Start-CMSoftwareUpdateDeployment : A positional parameter cannot be found that accepts argument '8:00:00 PM'. At E:\scripts\EN5 - CreateDeployments - LAB.ps1:24 char:5 + Start-CMSoftwareUpdateDeployment -SoftwareUpdateGroupName "$SUPGroupName1" - ... + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : InvalidArgument: ( [Start-CMSoftwareUpdateDeployment], ParameterBindingException + FullyQualifiedErrorId : PositionalParameterNotFound,Microsoft.ConfigurationManagement.Cmdlets.Sum.Commands.StartSoftwareUpdateDeploymentCommand Start-CMSoftwareUpdateDeployment : A positional parameter cannot be found that accepts argument '9:00:00 PM'. At E:\scripts\EN5 - CreateDeployments - LAB.ps1:24 char:5 + Start-CMSoftwareUpdateDeployment -SoftwareUpdateGroupName "$SUPGroupName1" - ... + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : InvalidArgument: ( [Start-CMSoftwareUpdateDeployment], ParameterBindingException + FullyQualifiedErrorId : PositionalParameterNotFound,Microsoft.ConfigurationManagement.Cmdlets.Sum.Commands.StartSoftwareUpdateDeploymentCommand Start-CMSoftwareUpdateDeployment : A positional parameter cannot be found that accepts argument '10:00:00 PM'. At E:\scripts\EN5 - CreateDeployments - LAB.ps1:24 char:5 + Start-CMSoftwareUpdateDeployment -SoftwareUpdateGroupName "$SUPGroupName1" - ... + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : InvalidArgument: ( [Start-CMSoftwareUpdateDeployment], ParameterBindingException + FullyQualifiedErrorId : PositionalParameterNotFound,Microsoft.ConfigurationManagement.Cmdlets.Sum.Commands.StartSoftwareUpdateDeploymentCommand Start-CMSoftwareUpdateDeployment : A positional parameter cannot be found that accepts argument '11:00:00 PM'. At E:\scripts\EN5 - CreateDeployments - LAB.ps1:24 char:5 + Start-CMSoftwareUpdateDeployment -SoftwareUpdateGroupName "$SUPGroupName1" - ... + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : InvalidArgument: ( [Start-CMSoftwareUpdateDeployment], ParameterBindingException + FullyQualifiedErrorId : PositionalParameterNotFound,Microsoft.ConfigurationManagement.Cmdlets.Sum.Commands.StartSoftwareUpdateDeploymentCommand
- 2 replies
-
- SCCM 2012
- Powershell
- (and 3 more)
-
Hello everyone, I was wondering if anyone could give me some help setting up my software updates. I understand the concepts and such, but I struggling with setting up the Update Groups and Deployment Packages. From what I am reading, a lot of people are saying to create a Update Group per month, every month, then eventually roll these updates into a yearly software update group. This makes sense to me. My question is, should I have software update groups per product? Example, one for Windows 7 and one for Windows 8.1? Or should I just have one software update group per month, with all the products I need to support? I'm aware that the client will only grab the updates it needs if its all in one. Should I have one single deployment package? Or several, one for each product? I'm really looking for best practices. Or any "gotchas" from people who have been doing software updates through SCCM for awhile. I realize the general answer will be "it depends on your environment", so I'm really just looking for some tips/suggestions/guidance that will help streamline the process Appreciate any help/suggestions
- 5 replies
-
- SUP
- Software Updates
-
(and 1 more)
Tagged with:
-
Gents, Do you know if software updates are stored in the content library and then distributed by the distribution points or if they are stored on the SUP (so clients need to download them from SUP) If there is an article dealing about this please do not hesitate to send the link.
- 2 replies
-
- Software Updates
- DP
-
(and 1 more)
Tagged with:
-
I apologize if this is obvious and is answered somewhere else, but I wasn't able to find by searching. SCCM 2012. I have a few thousand Windows Embedded Standard 7 (SP1) systems. I have a Software Update Group with the latest updates and I've deployed it to a collection with a test system. When I check that system it says "There are no updates available for your computer". If I run a report in SCCM it shows "Not required" for all the updates in the update group. However, if I click "Check online for updates from Windows Update" from the client it eventually comes back with a list of required updates... including those that are in the deployed software update group. I have tried changing the deadline for the deployment from 'As soon as possible' to a specific time with no change. I did see this in UpdatesDeployment.log "no current service window available to run updates assignment with the time required = 1". This machine has several maintenance windows but none are greater than 180 minutes. I've temporarily disabled all maintenance windows for this collection and that message has disappeared from UpdatesDeployment.log, but the problem persists. Another thing that is strange to me is that when I take an example KB and look at compliance, about 80% of my 3,000+ machines are "Not Required" but there are some that are required (unfortunately none of my labs)... these are all the same OS and built from the nearly the same image (it has changed a bit over time so I can't say 100%, but certainly none of them have the March-2016 updates installed yet). Any nudge in useful direction would be appreciated. Thanks
-
Hi Everyone, I wanted to let you know that this month's free report giveaway is Patch Compliance Progression by Collection For each PC within a collection, the Patch Compliance Progression by Collection report will provide you with a count of missing software updates (patches) and the last hardware inventory date. The deployed state report parameter allows you to select the deployed state of the software update. The deployed states are: Yes – The effected software update is deployed within your environment No – The effected software update is NOT deployed within your environment Both The status count parameter allows you to select whether or not expired software updates are included in the status count. In ConfigMgr, software updates that are expired are still listed. When complying with standards such as the Payment Card Industry Data Security Standard (PCI DSS), expired software updates should always be excluded from status counts. Yes – Expired software updates are included within the status count No – Expired software updates are NOT included within status count The classification report parameter enables you to select which software update classification to display within the report. The update classifications, listed in order of severity, are: Critical Updates, Security Updates, Definition Updates, Service Packs, Update Roll-ups, Updates, Tools, and Feature Packs. Click here to read more about update classifications. To learn more about it see our website. http://www.enhansoft.com/resources#current-monthly-report
-
So I'm trying to better automate my update process in SCCM 2012 R2 SP1. Right now I have an ADR that runs in the evening on Patch Tuesday that finds the appropriate updates based on update classification, product, date, not expired or superseded. It downloads the updates it finds into the Deployment Package, creates a new SUG for the month and deploys it out to the first pilot group. Then the next morning I come in and change the name of the SUG and the deployment to meet the naming standard, deploy it out to the remaining pilot and prod groups and email the end users affected in each group. I know I can use powershell to automate the deployment to the additional groups that I currently do manually. I could probably even automate the renames and the email notifications. The question I have not been able to find an answer for though is can I script what the ADR is doing with powershell? Can I script out finding the appropriate updates based on the search criteria (product, classification, date, etc) and create a SUG and do all of this all in one self contained PS script setup as a scheduled task? I've looked through the PS cmdlets but have not found a way to search for the applicable updates based on the criteria like i can in the ADR wizard.
-
Hi, I've noticed something odd about my Windows Updates. I have ADRs which run on Patch Tuesday, one for Windows 7, 8, Office 2010 and 2013. The updates are placed in four respective Software Update Groups. It seems like older updates are removed from those SUGs. The rules have been in place since the beginning of January. Right now there should be a few dozen updates in this SUG but there are only two. If I filter all my updates like below (to double check that the updates aren't expired/superseded) it finds 24 updates. Why aren't these in my SUG above? The ADR is set to add updates to an existing SUG. Here are the filters. I can't figure out what's happening. My goal was to not really have to pay updates any attention but it seems like I now have to spend time double-checking that all my updates are deployed correctly.
- 6 replies
-
- adr
- software updates
-
(and 2 more)
Tagged with:
-
Gents, We are managing MS updates through SCCM and it is working well. We are now facing to a reboot issue. We enable the following GPO : No auto-restart with logged on users for scheduled automatic updates So there is no automatic restart but there is still a reboot required at the end of the grace period I think. I would like to increase this period or delete the reboot any idea ? Sypa
- 1 reply
-
- grace period
- software updates
-
(and 1 more)
Tagged with:
-
Hello, I am getting ready to deploy some Office Service Packs. However I have no service packs for Microsoft Project 2013 or Visio 2013. Google search shows that these service packs are available however I cannot for the life of me find these in WSUS/SCCM Software Updates. I see SPs for Windows, Office, Visio Viewer, SharePoint, etc so the classification is definitely being polled and added to SCCM. Do these two (Project/Visio) service packs need to be pushed out as packages? If anyone could shed some light on this it'd be much appreciated. Thanks, Mike
- 1 reply
-
- Software Updates
- SCCM
-
(and 4 more)
Tagged with:
-
Gents, I recently set up software updates through automatic deployment rules. All works fine but some days after the deployments, users' laptops restart without any notification. Do you have an idea in order to suppress these unwanted reboots. Thanks in advance. Syparon
- 4 replies
-
- Software Updates
- windows updates
-
(and 2 more)
Tagged with:
-
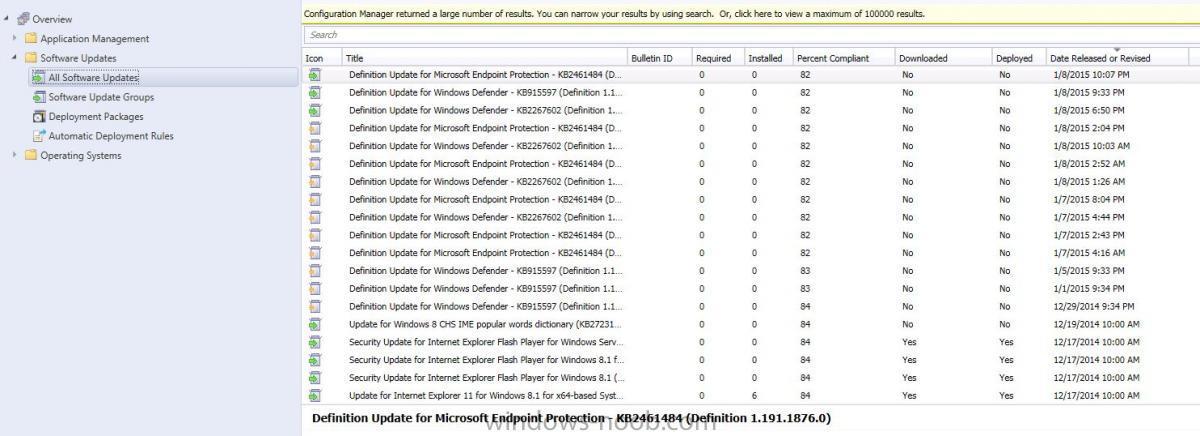
We had an Admin that "Accidentally" uninstalled the WSUS, settings and DB from the SCCM 2012 R2 Server. After reinstalling the WSUS server, settings and DB with the same settings, nothing is syncing with the SCCM 2012 R2 software updates group. When refreshing the "All Software Updates" it only shows the updates from December 2014 and nothing from January. Is there a way to "re-link" SCCM with WSUS or do I have to reconfigure all the groups again from scratch? The original setup of the Software Update Service were followed using the Step-By-Step guides on this site.
-
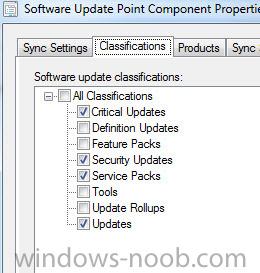
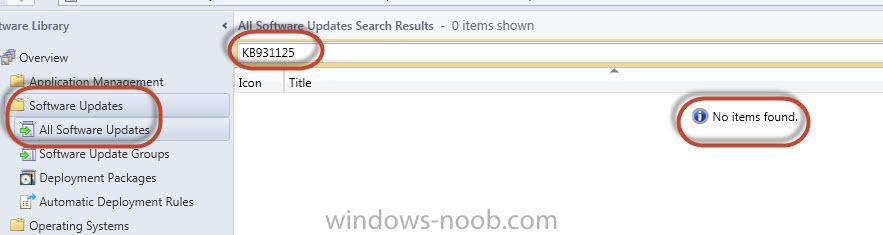
Wondering if anyone knows the proper Update classifications to make the client Root Certificate updates (i.e. http://support.microsoft.com/kb/931125) available to deploy? Can't seem to find any documentation on exactly what classes to include. Here are my classification settings (Administration > Configure Site Components > Software Update Point): Doesn't look available in the All Software Update node.
- 1 reply
-
- Root Certificate
- SCCM2012
-
(and 2 more)
Tagged with:
-
Afternoon All, Hopefully there are some experienced SCUP users here on the forums. I seem to have an issue with the "Automatic" publishing feature of SCUP. They publish metadata only, despite client requesting that they need the update. My understanding is that if any Configuration Manager clients are requesting the update a full content will be initiated otherwise only metadata will be published. Am i missing something? Is there a specific log I can look at to see why it's not switching to full content automatically when requested?
- 3 replies
-
- SCUP
- Configuration Manager 2012
- (and 3 more)
-
I wanted to put this topic in the main CM2012 forum, but I can't, for some reason. That's why it's posted here. Hello, I was really hoping someone could help me with this. Background information: - We have a CM07 server in a production environment. - I've set up a CM12 RTM server, following the guides in this forum, with the hopes of migrating soon. - I wanted to do OSD from scratch to learn more and to take advantage of new features in CM12. - I have a few virtual machines running for testing OSD/apps (these are the only clients managed by my CM12 server). - Since it's not possible to have two WDS servers running at the same time AFAIK (without using registry tweaks, the F11 trick, that by the way doesn't work for me) I have created a bootable TS media that I mount on the virtual machines whenever I want to test OSD. Now, to my problem: I can't figure out why my Build and Capture TS is failing on the Install Software Updates step. smsts.log file says: Failed to RefreshUpdates, hr=087d00272, followed by: Failed to run the action: Install Software Updates. Component is disabled (Error: 87D00272; Source: CCM). I have read about similar issues occurring in CM07 capture task sequences since the machine is joined to a Workgroup. The proposed solution was adding SMSSLP=FQDN to the client installation properties, but since that functionality is moved to the MP in CM12, it should be enough to specify SMSMP=FQDN in my case. It's not working anyway. Tried it to a Deploy TS also, where the machine is domain joined, but I got the same error. The error code 87D00272 returns no results on Google. This stumps me, as someone surely has had the same problem? Here is the relevant portions of the smsts.log file If someone had the chance to look at this, I would greatly appreciate it. Thank you! Refreshing Updates InstallSWUpdate 2012-06-13 10:15:33 228 (0x00E4) spInstall->RefreshTargetedUpdates( spCallback, &bAlreadyCompleted ), HRESULT=87d00272 (e:\nts_sccm_release\sms\client\osdeployment\installswupdate \installswupdate.cpp,467) InstallSWUpdate 2012-06-13 10:15:34 228 (0x00E4) Failed to RefreshUpdates, hr=0x87d00272 InstallSWUpdate 2012-06-13 10:15:34 228 (0x00E4) RefreshTargetedUpdates(spInstall, spCallback, bAlreadyCompleted), HRESULT=87d00272 (e:\nts_sccm_release\sms\client\osdeployment\installswupdate \installswupdate.cpp,1295) InstallSWUpdate 2012-06-13 10:15:34 228 (0x00E4) RefreshUpdates(), HRESULT=87d00272 (e:\nts_sccm_release\sms\client\osdeployment \installswupdate\installswupdate.cpp,906) InstallSWUpdate 2012-06-13 10:15:34 228 (0x00E4) InstallUpdates(pInstallUpdate, tType, sJobID, sActiveRequestHandle), HRESULT=87d00272 (e:\nts_sccm_release\sms\client\osdeployment\installswupdate \main.cpp,248) InstallSWUpdate 2012-06-13 10:15:34 228 (0x00E4) Setting TSEnv variable SMSTSInstallUpdateJobGUID= InstallSWUpdate 2012-06-13 10:15:34 228 (0x00E4) Process(pInstallUpdate, tType), HRESULT=87d00272 (e:\nts_sccm_release\sms\client \osdeployment\installswupdate\main.cpp,304) InstallSWUpdate 2012-06-13 10:15:34 228 (0x00E4) Process completed with exit code 2278556274 TSManager 2012-06-13 10:15:34 912 (0x0390) !----------------------------------------------------------------------------------- ---------! TSManager 2012-06-13 10:15:34 912 (0x0390) Failed to run the action: Install Software Updates. Component is disabled (Error: 87D00272; Source: CCM) TSManager 2012-06-13 10:15:34 912 (0x0390) MP server http://CFGMGR-SRV.zenit.brummer.se. Ports 80,443. CRL=false. TSManager 2012-06-13 10:15:34 912 (0x0390) Setting authenticator TSManager 2012-06-13 10:15:35 912 (0x0390) Set authenticator in transport TSManager 2012-06-13 10:15:35 912 (0x0390) Sending StatusMessage TSManager 2012-06-13 10:15:35 912 (0x0390) Setting message signatures. TSManager 2012-06-13 10:15:35 912 (0x0390) Setting the authenticator. TSManager 2012-06-13 10:15:35 912 (0x0390) CLibSMSMessageWinHttpTransport::Send: URL: CFGMGR-SRV.zenit.brummer.se:80 CCM_POST /ccm_system/request TSManager 2012-06-13 10:15:35 912 (0x0390) Request was succesful. TSManager 2012-06-13 10:15:35 912 (0x0390) Set a global environment variable _SMSTSLastActionRetCode=-2016411022 TSManager 2012-06-13 10:15:35 912 (0x0390) Set a global environment variable _SMSTSLastActionSucceeded=false TSManager 2012-06-13 10:15:35 912 (0x0390) Clear local default environment TSManager 2012-06-13 10:15:35 912 (0x0390) Let the parent group (Setup Operating System) decides whether to continue execution TSManager 2012-06-13 10:15:35 912 (0x0390) The execution of the group (Setup Operating System) has failed and the execution has been aborted. An action failed. Operation aborted (Error: 80004004; Source: Windows) TSManager 2012-06-13 10:15:35 912 (0x0390) Failed to run the last action: Install Software Updates. Execution of task sequence failed. Component is disabled (Error: 87D00272; Source: CCM) TSManager 2012-06-13 10:15:35 912 (0x0390) MP server http://CFGMGR-SRV.zenit.brummer.se. Ports 80,443. CRL=false. TSManager 2012-06-13 10:15:35 912 (0x0390) Setting authenticator TSManager 2012-06-13 10:15:35 912 (0x0390) Set authenticator in transport TSManager 2012-06-13 10:15:35 912 (0x0390) Sending StatusMessage TSManager 2012-06-13 10:15:35 912 (0x0390) Setting message signatures. TSManager 2012-06-13 10:15:35 912 (0x0390) Setting the authenticator. TSManager 2012-06-13 10:15:35 912 (0x0390) CLibSMSMessageWinHttpTransport::Send: URL: CFGMGR-SRV.zenit.brummer.se:80 CCM_POST /ccm_system/request TSManager 2012-06-13 10:15:35 912 (0x0390) Request was succesful. TSManager 2012-06-13 10:15:35 912 (0x0390) Launching command shell. OSDSetupHook 2012-06-13 10:15:45 1932 (0x078C) executing command: C:\WINDOWS\system32\cmd.exe /k OSDSetupHook 2012-06-13 10:15:45 1932 (0x078C) executed command: C:\WINDOWS\system32\cmd.exe /k OSDSetupHook 2012-06-13 10:15:45 1932 (0x078C) Execution::enExecutionFail != m_eExecutionResult, HRESULT=80004005 (e: \nts_sccm_release\sms\client asksequence smanager smanager.cpp,756) TSManager 2012-06-13 10:16:57 912 (0x0390) Task Sequence Engine failed! Code: enExecutionFail TSManager 2012-06-13 10:16:57 912 (0x0390) **************************************************************************** TSManager 2012-06-13 10:16:57 912 (0x0390) Task sequence execution failed with error code 80004005 TSManager 2012-06-13 10:16:57 912 (0x0390)
-
I've just setup SCUP 2011 on my SCCM 2012 (2008 R2) server and managed to do the following: Configured: WSUS on same server, connected to Config Manager. Downloaded Adobe Updates via the SCUP Catalogue. Got the updates Published to SCCM 2012 and assigned to a Package and Software Group within SCCM Exported the WSUS cert and reimported as Trusted Publisher and Root on the test client and also the server. Assigned deployment to test collection that has one computer in need of those updates. However, on the client itself, I cannot get it to detect and download the relevant updates for Adobe Reader, I've been trawling through the logs looking for evidence that the updates were detected and downloaded, and also manually checked the ccmcache and also (WSUS) softwaredownload folders, all had no downloaded files or references of the Adobe updates. I can't think of anything else and there is nothing obvious in the logs that I can see, hopefully someone with experience can point me in the right direction? The client has the following set via a test GPO: AcceptTrustedPublisherCerts = 1 WUServer = http:sccm-server:80 WUStatusServer = http:sccm-server:80 UpdatesHandler.log Successfully initiated scan. UpdatesHandler 08/04/2013 13:33:39 4036 (0x0FC4) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 13:33:39 3608 (0x0E18) Successfully initiated scan. UpdatesHandler 08/04/2013 13:33:39 3608 (0x0E18) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 13:33:40 4036 (0x0FC4) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 13:33:44 4980 (0x1374) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 13:33:48 3608 (0x0E18) Successfully initiated scan. UpdatesHandler 08/04/2013 13:33:49 3608 (0x0E18) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 13:34:54 4980 (0x1374) CUpdatesAgent::FinalConstruct entered UpdatesHandler 08/04/2013 14:50:07 3332 (0x0D04) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 14:56:43 3524 (0x0DC4) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 14:56:43 3108 (0x0C24) Successfully initiated scan. UpdatesHandler 08/04/2013 14:56:43 3524 (0x0DC4) Successfully initiated scan. UpdatesHandler 08/04/2013 14:56:43 3108 (0x0C24) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 14:56:43 3524 (0x0DC4) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 14:56:43 3416 (0x0D58) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 15:31:26 3864 (0x0F18) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 15:31:26 5916 (0x171C) Successfully initiated scan. UpdatesHandler 08/04/2013 15:31:26 3864 (0x0F18) Successfully initiated scan. UpdatesHandler 08/04/2013 15:31:26 5916 (0x171C) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 15:32:20 5232 (0x1470) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 15:32:21 5232 (0x1470) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:24:32 4816 (0x12D0) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:24:32 3068 (0x0BFC) Successfully initiated scan. UpdatesHandler 08/04/2013 16:24:32 4816 (0x12D0) Successfully initiated scan. UpdatesHandler 08/04/2013 16:24:33 3068 (0x0BFC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:25:21 4824 (0x12D8) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:25:21 3068 (0x0BFC) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:30:13 3744 (0x0EA0) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:30:13 4824 (0x12D8) Successfully initiated scan. UpdatesHandler 08/04/2013 16:30:13 3744 (0x0EA0) Successfully initiated scan. UpdatesHandler 08/04/2013 16:30:13 4824 (0x12D8) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:30:19 2160 (0x0870) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:30:21 3744 (0x0EA0) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:39:13 4016 (0x0FB0) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:39:13 4572 (0x11DC) Successfully initiated scan. UpdatesHandler 08/04/2013 16:39:13 4016 (0x0FB0) Successfully initiated scan. UpdatesHandler 08/04/2013 16:39:13 4572 (0x11DC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:40:02 2524 (0x09DC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:40:02 2524 (0x09DC) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:54:11 5192 (0x1448) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:54:11 3692 (0x0E6C) Successfully initiated scan. UpdatesHandler 08/04/2013 16:54:11 3692 (0x0E6C) Successfully initiated scan. UpdatesHandler 08/04/2013 16:54:11 5192 (0x1448) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:55:14 5624 (0x15F8) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:55:15 4904 (0x1328) CUpdatesAgent::FinalConstruct entered UpdatesHandler 08/04/2013 17:09:42 2604 (0x0A2C) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:11:17 4780 (0x12AC) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:11:17 4872 (0x1308) Successfully initiated scan. UpdatesHandler 08/04/2013 17:11:18 4872 (0x1308) Successfully initiated scan. UpdatesHandler 08/04/2013 17:11:18 4780 (0x12AC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:13:03 3812 (0x0EE4) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:13:03 4780 (0x12AC) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:13:37 3812 (0x0EE4) Successfully initiated scan. UpdatesHandler 08/04/2013 17:13:37 3812 (0x0EE4) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:13:37 4780 (0x12AC) Successfully initiated scan. UpdatesHandler 08/04/2013 17:13:37 4780 (0x12AC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:14:16 5180 (0x143C) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:14:16 1056 (0x0420) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C) Successfully initiated scan. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C) Successfully initiated scan. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:47:07 4500 (0x1194) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:47:07 964 (0x03C4) UpdatesDeployment.log Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_499fc6e1-f6de-4e4c-b98d-41ca21bee49b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e93c80ff-812b-4640-a7fb-d3712b86e3b1) added to the targeted list of deployment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B}) UpdatesDeploymentAgent 08/04/2013 16:55:15 5624 (0x15F8) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_49ddec56-93f2-48e7-98af-ecd54526d34c) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_5c22235f-a3d9-48db-95eb-a60ec1886e8e) added to the targeted list of deployment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B}) UpdatesDeploymentAgent 08/04/2013 16:55:15 5624 (0x15F8) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9e40eb5c-184a-494d-be46-8b140386179b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_da767d4a-8677-4b9d-9f0b-365f14e19ae1) added to the targeted list of deployment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B}) UpdatesDeploymentAgent 08/04/2013 16:55:15 5624 (0x15F8) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_d0fbac2f-d08f-4a7b-a826-92b1c5ae0bc5) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328) EnumerateUpdates for action (UpdateActionInstall) - Total actionable updates = 0 UpdatesDeploymentAgent 08/04/2013 16:56:29 2892 (0x0B4C) User logoff system task UpdatesDeploymentAgent 08/04/2013 17:03:45 4708 (0x1264) Service startup system task UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) Software Updates feature is enabled UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) Total Pending reboot updates = 0 UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) No pending reboot updates at system restart. UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) No current service window available to run updates assignment with time required = 1 UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) CUpdateAssignmentsManager::OnThirdPartyOrchestrationSettingChange - No pending install assignment UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) Startup task completed UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) User logon system task UpdatesDeploymentAgent 08/04/2013 17:09:50 988 (0x03DC) Assignment {0ADCDD92-9E6F-4796-AFFD-7013EB4E554B} has total CI = 20 UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) OnPolicyDelete for assignment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B})... UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_27fc50b4-5982-4d58-a13d-53bd1f3806ea", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_957317cf-ef0d-4fa7-a2ad-5d2db2cf355e", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_1f6d4200-fcb6-4a4c-8ad7-ab76c529bff3", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_7ad922e0-685f-4723-9da3-4d7acefb4706", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e9e8a81d-ed5a-4af3-963e-2dc4413e3c3e", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_42cc6726-c3fe-464b-b8ac-38ec00766262", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_f51bc4bd-7424-4c47-ae97-714a8e3895b5", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_04874d8a-71a5-43d9-8531-eb19fdf319e6", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_0e79069c-cdca-4c91-aad3-e21ede710634", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_6d8590bd-038e-4455-9764-30875ccbf0c7", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_02fe5101-40eb-4d91-aa9d-5727060aefba", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_07151137-3b83-4064-8fc2-7bf983d6b08b", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_421e86ff-37e0-4199-9a0c-4976332bbcdf", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_521d70cd-3256-4c26-96f8-b7c3c4adc113", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9b65fe9a-721e-4390-860d-02c1dbffa10f", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9caf7699-d7f8-4cbb-95c9-002cbe3df07d", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_022d7dab-a021-4318-9c71-16323944584d", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e93c80ff-812b-4640-a7fb-d3712b86e3b1", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_5c22235f-a3d9-48db-95eb-a60ec1886e8e", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_da767d4a-8677-4b9d-9f0b-365f14e19ae1", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) EnumerateUpdates for action (UpdateActionInstall) - Total actionable updates = 0 UpdatesDeploymentAgent 08/04/2013 17:10:10 3484 (0x0D9C) Message received: '<?xml version='1.0' ?><SoftwareUpdatesMessage MessageType='EvaluateAssignments'><UseCachedResults>False</UseCachedResults></SoftwareUpdatesMessage>' UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Removing scan history to force non cached results UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Assignment {47ABB848-E3B5-405B-AA5E-01514176142F} has total CI = 7 UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Detection job ({C92EAD93-F8F7-4257-BD47-FF953B523427}) started for assignment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Started evaluation for assignment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Assignment {28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C} has total CI = 20 UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Detection job ({4BDCE35B-6B75-4DE8-BB1D-9ADD513CA2D0}) started for assignment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Started evaluation for assignment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Evaluation initiated for (2) assignments. UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) DetectJob completion received for assignment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:03 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9703dec9-deaf-4566-b966-aeca447a4ba4) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_a13356e5-6224-44e0-9020-9a3c924da131) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_244b7a38-eb9e-4632-a299-b085587d477c) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_499fc6e1-f6de-4e4c-b98d-41ca21bee49b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_49ddec56-93f2-48e7-98af-ecd54526d34c) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9e40eb5c-184a-494d-be46-8b140386179b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_d0fbac2f-d08f-4a7b-a826-92b1c5ae0bc5) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) DetectJob completion received for assignment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_27fc50b4-5982-4d58-a13d-53bd1f3806ea) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_957317cf-ef0d-4fa7-a2ad-5d2db2cf355e) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_1f6d4200-fcb6-4a4c-8ad7-ab76c529bff3) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_7ad922e0-685f-4723-9da3-4d7acefb4706) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e9e8a81d-ed5a-4af3-963e-2dc4413e3c3e) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_42cc6726-c3fe-464b-b8ac-38ec00766262) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_f51bc4bd-7424-4c47-ae97-714a8e3895b5) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_04874d8a-71a5-43d9-8531-eb19fdf319e6) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_0e79069c-cdca-4c91-aad3-e21ede710634) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_6d8590bd-038e-4455-9764-30875ccbf0c7) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_02fe5101-40eb-4d91-aa9d-5727060aefba) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_07151137-3b83-4064-8fc2-7bf983d6b08b) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_421e86ff-37e0-4199-9a0c-4976332bbcdf) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_521d70cd-3256-4c26-96f8-b7c3c4adc113) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9b65fe9a-721e-4390-860d-02c1dbffa10f) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9caf7699-d7f8-4cbb-95c9-002cbe3df07d) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 WUAHandler.log Async searching completed. WUAHandler 08/04/2013 15:32:17 4964 (0x1364) Successfully completed scan. WUAHandler 08/04/2013 15:32:19 1032 (0x0408) Scan results will include all superseded updates. WUAHandler 08/04/2013 15:32:20 1044 (0x0414) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 15:32:20 1044 (0x0414) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 15:32:20 1044 (0x0414) Async searching completed. WUAHandler 08/04/2013 15:32:20 4960 (0x1360) Successfully completed scan. WUAHandler 08/04/2013 15:32:20 1044 (0x0414) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 16:24:30 4816 (0x12D0) Existing WUA Managed server was already set (http://:80), skipping Group Policy registration. WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Async searching completed. WUAHandler 08/04/2013 16:31:08 1096 (0x0448) Successfully completed scan. WUAHandler 08/04/2013 16:31:11 3744 (0x0EA0) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Async searching completed. WUAHandler 08/04/2013 16:39:58 3424 (0x0D60) Successfully completed scan. WUAHandler 08/04/2013 16:40:00 4016 (0x0FB0) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:40:01 6024 (0x1788) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 16:40:01 6024 (0x1788) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:40:01 6024 (0x1788) Async searching completed. WUAHandler 08/04/2013 16:40:01 4956 (0x135C) Successfully completed scan. WUAHandler 08/04/2013 16:40:01 6024 (0x1788) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 16:54:09 5244 (0x147C) Enabling WUA Managed server policy to use server: http://sccmserver:80 WUAHandler 08/04/2013 16:54:09 5244 (0x147C) Waiting for 2 mins for Group Policy to notify of WUA policy change... WUAHandler 08/04/2013 16:54:09 5244 (0x147C) Waiting for 30 secs for policy to take effect on WU Agent. WUAHandler 08/04/2013 16:54:16 5244 (0x147C) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 16:54:46 5244 (0x147C) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:54:46 5244 (0x147C) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 16:54:46 5244 (0x147C) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:54:46 5244 (0x147C) Async searching completed. WUAHandler 08/04/2013 16:55:11 5944 (0x1738) Successfully completed scan. WUAHandler 08/04/2013 16:55:13 5624 (0x15F8) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:55:14 5244 (0x147C) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 16:55:14 5244 (0x147C) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:55:14 5244 (0x147C) Async searching completed. WUAHandler 08/04/2013 16:55:14 5516 (0x158C) Successfully completed scan. WUAHandler 08/04/2013 16:55:14 4904 (0x1328) CWuaHandler::SetCategoriesForLeafStateReportingExclusion called with E0789628-CE08-4437-BE74-2495B842F43B WUAHandler 08/04/2013 17:09:26 2604 (0x0A2C) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Async searching completed. WUAHandler 08/04/2013 17:13:00 4208 (0x1070) Successfully completed scan. WUAHandler 08/04/2013 17:13:02 4780 (0x12AC) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'E1D507BE-497C-D8FD-61D7-B0D93EE399CA') OR (DeploymentAction=* AND Type='Software' AND CategoryIDs contains '3B36FCFD-0384-EA97-2D49-1349AE748647') OR (DeploymentAction=* AND Type='Software' AND CategoryIDs contains '70CFAD70-6629-B54B-5819-C809A605515E')) WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4) Async searching completed. WUAHandler 08/04/2013 17:13:03 4344 (0x10F8) Successfully completed scan. WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Async searching completed. WUAHandler 08/04/2013 17:14:13 5476 (0x1564) Successfully completed scan. WUAHandler 08/04/2013 17:14:15 1056 (0x0420) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4) Async searching completed. WUAHandler 08/04/2013 17:14:16 5648 (0x1610) Successfully completed scan. WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Async searching completed. WUAHandler 08/04/2013 17:47:03 4948 (0x1354) Successfully completed scan. WUAHandler 08/04/2013 17:47:05 964 (0x03C4) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:47:06 4764 (0x129C) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 17:47:06 4764 (0x129C) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:47:06 4764 (0x129C) Async searching completed. WUAHandler 08/04/2013 17:47:06 5180 (0x143C) Successfully completed scan. WUAHandler 08/04/2013 17:47:07 4764 (0x129C) UpdateStore.log Update status from update (eb303398-da7c-4ce6-b8db-254409b32c39) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (eb30575d-51df-4c24-87dc-9b9c6dc8aa04) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (eb7a169f-6bca-4e00-a52a-623c063c162d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (ebbdc330-bd19-47b9-9e08-c4f32694429b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (ec1f4a29-8828-4fbe-b101-5a89321d8e7f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (edcc7a72-ffa0-4753-b59a-976044bbb012) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (efb911ae-5fba-48c7-8060-51734e3c1144) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f019d0aa-dfcf-4af8-b846-d38f8f7239e7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f0b50507-6c86-41d6-9350-6a8af21f76c7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f120b7a8-9ee3-4e95-8628-ac27b0d1df85) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f19502ff-7637-4ed8-bbc1-1b2508e56e2b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f1b1b1e1-2b22-4445-8a9c-5924bf945d32) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f21b0303-4d18-4a9b-9bda-8a796062189b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f284dc51-5659-4534-a1c7-6b9dbfe9453a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f2b28914-a6bc-44c5-ac04-9e7fbdea657e) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f2c6b0b8-f2cf-4f6c-8d64-6a21b9ca86d2) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f307ffeb-f424-4a79-8bc3-d472be542dec) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f45f3c72-427b-4889-a627-836244bf1ce1) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f4683760-71cc-4e3f-82a0-e1c164955163) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f51a0e5b-24a9-4be1-8b36-0f22f99949e7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f5202a56-ff34-401d-a040-f97c7f70891c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f53b1817-e327-438b-afb8-0cd5a0f95cb2) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f54ace97-a003-44a4-9e36-ef7071f6ce9d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f591538a-2c8f-4dc4-8b17-8b07c9a851ca) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f808dbaf-bec7-4dfb-a0cc-25290a7cd368) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f9b10375-898c-4d12-8722-b2f7f6e81521) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fabc6fae-c385-4543-a483-1b1cadfade98) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fabea4ad-b256-4b4e-b9cf-988bcfd5463f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fbc62e30-1128-4af5-9cb7-e1e349eb1b23) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fc5608e4-a70d-4344-b358-2847f4a57434) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fc5b1588-f912-4c1b-9f87-4ee1b427c5b1) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fc7c3752-4c17-473c-8bff-75eed375fd61) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fd8b7365-bc78-48e5-96c0-53682b94a607) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fdc8ef3a-11eb-45e6-9e0e-38a193f7b48c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (ff1d0808-8bb8-47ea-90c4-f7e806f7bde0) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Successfully done with SetStatus() operation. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (097d6f40-e0dc-4410-893f-24d5326aed8a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (0aa3cf0a-2269-4356-ad99-0e3ca8eb439f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (0b92accc-057d-408a-8e6e-0867f21f015f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (138bccfd-40ac-4a5d-84f0-3e5bf9743e42) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (161ed7f2-9f54-4625-914c-2b3c93040db4) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (2b487f1d-e072-4be7-986c-4355c3372cd1) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (324f1032-de0c-406e-b611-34b99c64e21d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (3abe760c-4578-4c84-a1cb-bf1df019efe4) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (40bd5a76-a368-4088-b172-a9e5dd1e5e3a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (40ccd4f1-cc6f-4368-968b-29d10e57b05f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (48f658bc-fec4-4464-8f01-db68c5ab1720) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (596adb47-108d-482d-85ba-a513621434b7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (5eca77b2-63e0-4df3-b1b0-acb90f28c532) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (7079beeb-6120-4afd-ad07-fb4dfa284fbe) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (71a29c39-e160-4b00-9b2f-d9924c8e09d5) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (744f9366-c308-44b2-8542-ca31c229179d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (75914178-2bdf-4fd3-b537-e2a517734bc7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (79f342ab-66e7-42a7-8315-2677f99f20c5) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (7c25aee0-71f5-4fda-8763-effae905b564) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (82538218-b3eb-4c56-a9b8-fdb358869d2b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (979b9aa2-dcf8-45d6-a31d-63df2a02d043) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (97e091c7-35eb-4da0-9346-e6f33115c8ed) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (98c62b24-a3dd-4843-ad1a-e08d95624f00) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (a429515b-9216-4277-bd4d-bf0593542c0d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (a61bd9f9-6940-408c-a80e-5a7dc4f5e1a2) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (a643a7c6-aa86-480c-b9e8-7f9abca811e6) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (ac8b33b5-2df2-4e6a-8d48-105ba0cc3bff) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (af91fcf0-fc28-4293-acc6-598fdcea359a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (afdd5d5e-2cc2-4a6a-a44f-e45a275702f5) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (b047a38c-47a5-4ac7-b42a-0c4d80f3341c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (b14fba1c-2b3b-4746-8801-104180701e7e) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (b628f40e-33de-4a37-81ae-9c2868c75373) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (c6164205-7295-4670-8a2f-8dad2d0682b0) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (d7568b8a-3d37-43de-8d65-b6a0a73b010c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (de4cbbf4-443f-4bb7-aebf-8da2fcc7b706) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (e5cbc9ff-0953-4efc-8acc-6a130bd4385b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (eb30575d-51df-4c24-87dc-9b9c6dc8aa04) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (fc5608e4-a70d-4344-b358-2847f4a57434) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Successfully done with SetStatus() operation. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Querying update status of 20 updates. UpdatesStore 08/04/2013 17:47:07 4500 (0x1194) Querying update status completed successfully. UpdatesStore 08/04/2013 17:47:07 4500 (0x1194) Querying update status of 7 updates. UpdatesStore 08/04/2013 17:47:07 964 (0x03C4) Querying update status completed successfully. UpdatesStore 08/04/2013 17:47:07 964 (0x03C4) Querying update status of 20 updates. UpdatesStore 08/04/2013 18:01:00 6032 (0x1790) Querying update status completed successfully. UpdatesStore 08/04/2013 18:01:00 6032 (0x1790) Querying update status of 20 updates. UpdatesStore 08/04/2013 18:01:00 3748 (0x0EA4) Querying update status completed successfully. UpdatesStore 08/04/2013 18:01:00 3748 (0x0EA4)
-
Hi, I've been using SCCM 2012 R2 for some time know, but there are still some mysteries to me. I have been asked to start deploying software updates through it rather than WSUS or Windows Updates itself. Before i came along, people got their updates the old fashion way-Windows Updates. So after the grueling task of figuring that out, i've got it working-ish! My main concern with this method (and also Endpoint) is that the majority of our users are NOT on the domain/network at all times. We do have several hub offices whose machines are on the network, but our line of work is mostly remote. Meaning these users are on home, hotel or data card wifi--not the network. They also rarely get on VPN. So my question is: are these people going to receive updates or endpoint definitions while being "offline?" I have a bunch of machines listed as inactive in Devices since they are never on our network. Is there a call home feature I'm unaware about with the sccm client? Keep in mind, when the machines are sent out, they are all sent out the same and with the client installed and working properly. Is this a bad setup in our environment? Any help or advice would be greatly appreciated!
- 4 replies
-
- sccm
- software updates
-
(and 3 more)
Tagged with:
-
Updates are not showing as expired anymore in my update lists. For years, I would sync WSUS, then sync my SCCM repository and several updates each month would get flagged as expired. I would then remove them from my list and my deployment. Recently over the past few months, I've noticed that even though WSUS is showing that x number of updates have expired, SCCM is not showing them as expired. Right now, I am specifically talking about MS14-045 that MS recalled. I synced WSUS yesterday, looked at the sync report and MS14-045 was expired. But when I go to my SCCM repository and sync it, it does not show that MS number or any associated KB's as expired. This has been happening for a few months now. Does anyone know why my WSUS updates expire like normal but that is not transitioning to SCCM?
-
Hi All, Just wondering how people do there software updates for servers and workstations using SCCM 2012. Do you use ADR's to create a new update group each month after patch Tuesday, and have a separate one for out of bands updates? Do you then have several different collections for servers and workstations for pilot, dev and production phases? Just trying to get an idea as to how to create a software update plan for my environment.
- 1 reply
-
- Software Updates
- SCCM
- (and 4 more)