Search the Community
Showing results for tags 'Software updates'.
-
In my Windows 10 LTSC 1809 task sequence, the Install Software Updates step is failing to run. I have attached the log files for the latest attempt to build a test machine. I have deployed the required software update group to both the Unknown Computer collection (as I am deleting the SCCM object fo...
-
- windows 10
- sccm
-
(and 1 more)
Tagged with:
-
Hello Everyone, I want to get in the habit of cleaning up my SUGs created by my ADRs. I'd like to do this every 6 months but I've run into a problem. Within one of my ADRs, for example, I have the following set for the 'Title' options: -Preview -Security Only Quality Update...
- 1 reply
-
- software updates
- windows update
-
(and 3 more)
Tagged with:
-
We are upgrading to Current Branch and want to include patching from this and not WSUS as curretly used. what is the best way to patch 3rd party applications through SCCM Current Branch?
- 5 replies
-
- software updates
- 3rd party
-
(and 1 more)
Tagged with:
-
Hi. I'm having a bit of trouble with a task sequence. Everything runs fine and quick, until 'Running Action: install Software Updates'. It seems to hang/stall at 60% for hours. I can't see anything in the logs that obvious. I have a Primary in DomainA, and a Secondary in DomainB, and a DP off th...
- 5 replies
-
- sccm
- current branch
-
(and 4 more)
Tagged with:
-
Hello All, I have a Powershell script that I use to create multiple Software Update Deployments and it works perfectly (well almost). The last piece I'm missing is automating the deadline date. Currently I just have it getting the current date and adding 5 days. I then go into each deployments p...
- 2 replies
-
- SCCM 2012
- Powershell
- (and 3 more)
-
Hello everyone, I was wondering if anyone could give me some help setting up my software updates. I understand the concepts and such, but I struggling with setting up the Update Groups and Deployment Packages. From what I am reading, a lot of people are saying to create a Update Group pe...
- 5 replies
-
- SUP
- Software Updates
-
(and 1 more)
Tagged with:
-
Gents, Do you know if software updates are stored in the content library and then distributed by the distribution points or if they are stored on the SUP (so clients need to download them from SUP) If there is an article dealing about this please do not hesitate to send the link.
- 2 replies
-
- Software Updates
- DP
-
(and 1 more)
Tagged with:
-
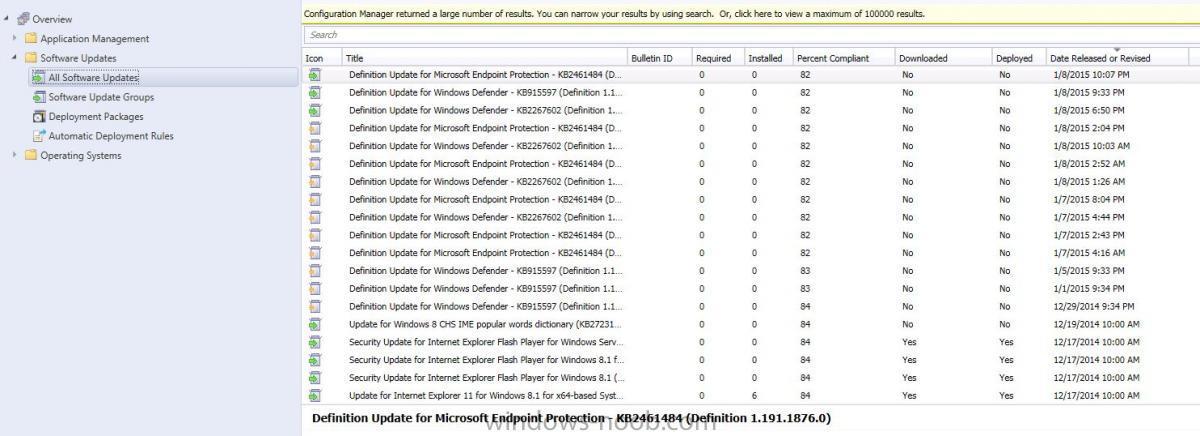
Hi Everyone, I wanted to let you know that this month's free report giveaway is Patch Compliance Progression by Collection For each PC within a collection, the Patch Compliance Progression by Collection report will provide you with a count of missing software updates (patches) and the last hardw...
-
So I'm trying to better automate my update process in SCCM 2012 R2 SP1. Right now I have an ADR that runs in the evening on Patch Tuesday that finds the appropriate updates based on update classification, product, date, not expired or superseded. It downloads the updates it finds into the Deployme...
-
Hi, I've noticed something odd about my Windows Updates. I have ADRs which run on Patch Tuesday, one for Windows 7, 8, Office 2010 and 2013. The updates are placed in four respective Software Update Groups. It seems like older updates are removed from those SUGs. The rules have been in place...
- 6 replies
-
- adr
- software updates
-
(and 2 more)
Tagged with:
-
Gents, We are managing MS updates through SCCM and it is working well. We are now facing to a reboot issue. We enable the following GPO : No auto-restart with logged on users for scheduled automatic updates So there is no automatic restart but there is still a reboot required at the end of...
- 1 reply
-
- grace period
- software updates
-
(and 1 more)
Tagged with:
-
Hello, I am getting ready to deploy some Office Service Packs. However I have no service packs for Microsoft Project 2013 or Visio 2013. Google search shows that these service packs are available however I cannot for the life of me find these in WSUS/SCCM Software Updates. I see SPs for Windows,...
- 1 reply
-
- Software Updates
- SCCM
-
(and 4 more)
Tagged with:
-
Gents, I recently set up software updates through automatic deployment rules. All works fine but some days after the deployments, users' laptops restart without any notification. Do you have an idea in order to suppress these unwanted reboots. Thanks in advance. Syparon
- 4 replies
-
- Software Updates
- windows updates
-
(and 2 more)
Tagged with:
-
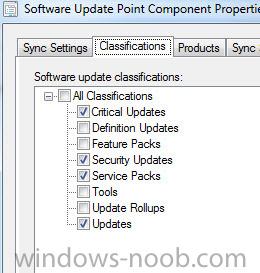
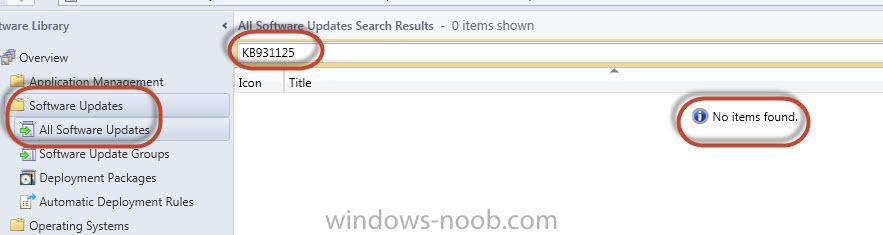
Wondering if anyone knows the proper Update classifications to make the client Root Certificate updates (i.e. http://support.microsoft.com/kb/931125) available to deploy? Can't seem to find any documentation on exactly what classes to include. Here are my classification settings (Administration > C...
- 1 reply
-
- Root Certificate
- SCCM2012
-
(and 2 more)
Tagged with:
-
Afternoon All, Hopefully there are some experienced SCUP users here on the forums. I seem to have an issue with the "Automatic" publishing feature of SCUP. They publish metadata only, despite client requesting that they need the update. My understanding is that if any Configuration Manager clien...
- 3 replies
-
- SCUP
- Configuration Manager 2012
- (and 3 more)
-
I wanted to put this topic in the main CM2012 forum, but I can't, for some reason. That's why it's posted here. Hello, I was really hoping someone could help me with this. Background information: - We have a CM07 server in a production environment. - I've set up a CM12 RTM server, foll...
-
Hi, I've been using SCCM 2012 R2 for some time know, but there are still some mysteries to me. I have been asked to start deploying software updates through it rather than WSUS or Windows Updates itself. Before i came along, people got their updates the old fashion way-Windows Updates. So after...
- 4 replies
-
- sccm
- software updates
-
(and 3 more)
Tagged with:
-
Updates are not showing as expired anymore in my update lists. For years, I would sync WSUS, then sync my SCCM repository and several updates each month would get flagged as expired. I would then remove them from my list and my deployment. Recently over the past few months, I've noticed that...
-
Hi All, Just wondering how people do there software updates for servers and workstations using SCCM 2012. Do you use ADR's to create a new update group each month after patch Tuesday, and have a separate one for out of bands updates? Do you then have several different collections for servers and wo...
- 1 reply
-
- Software Updates
- SCCM
- (and 4 more)