Search the Community
Showing results for tags 'WIndows 10'.
-
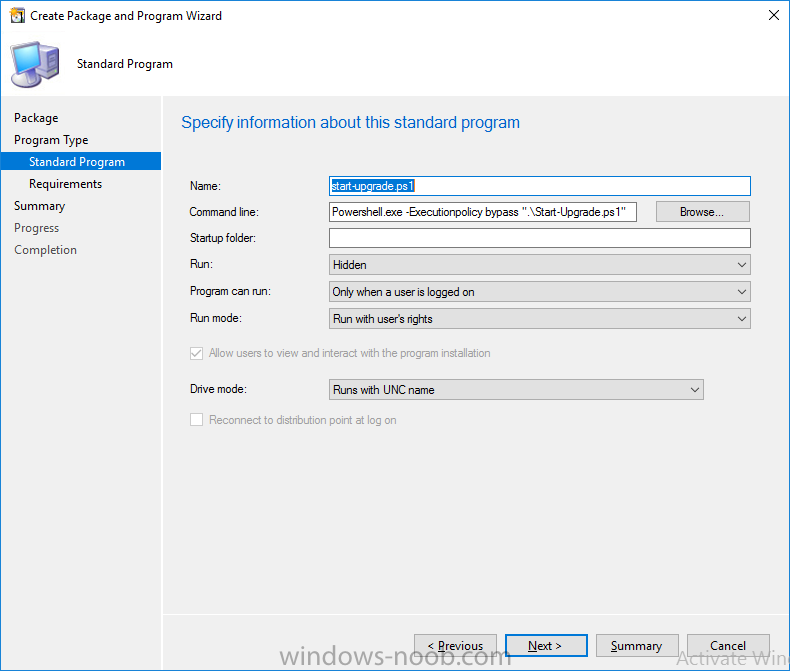
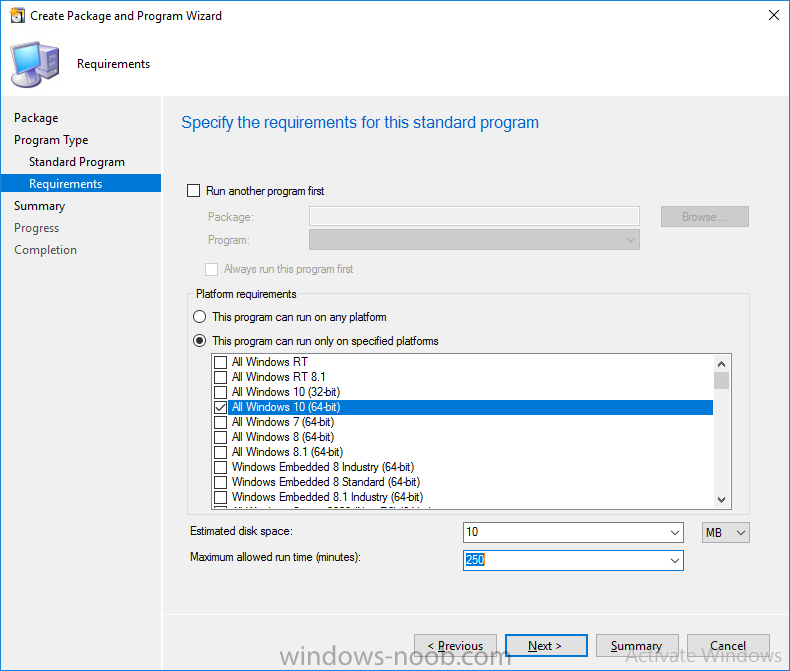
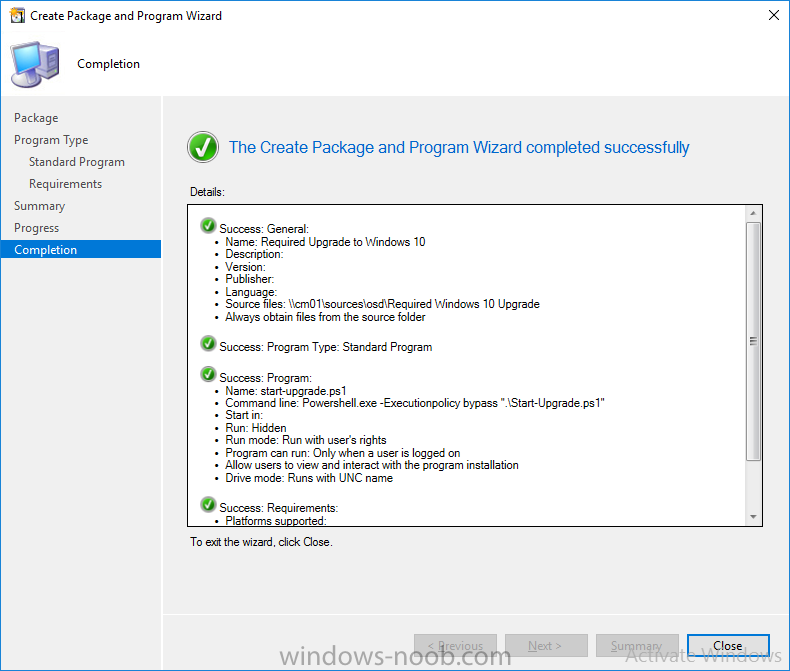
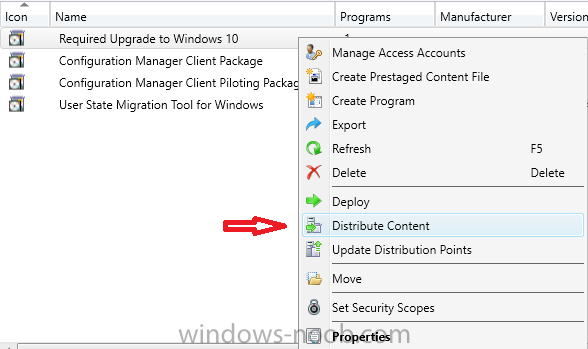
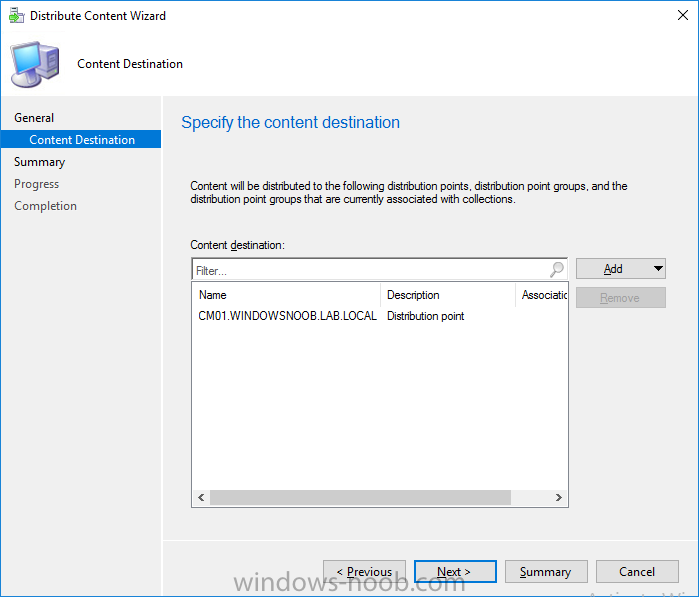
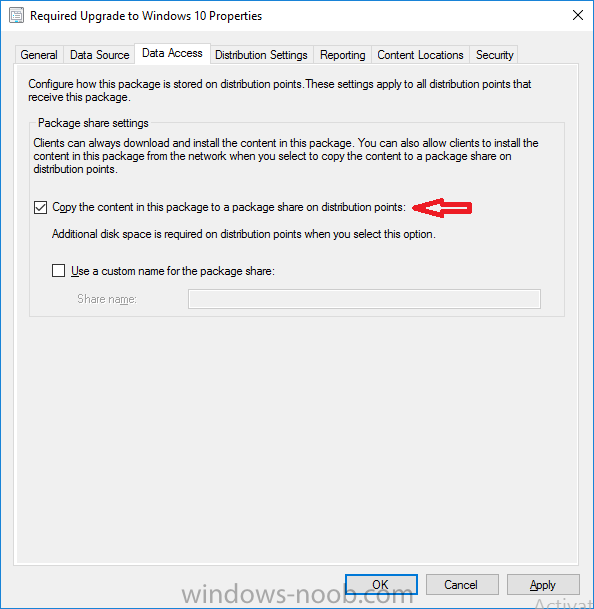
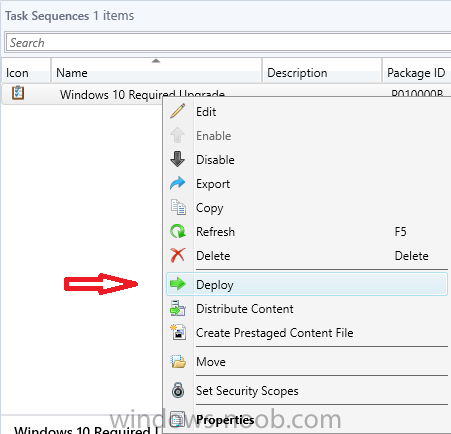
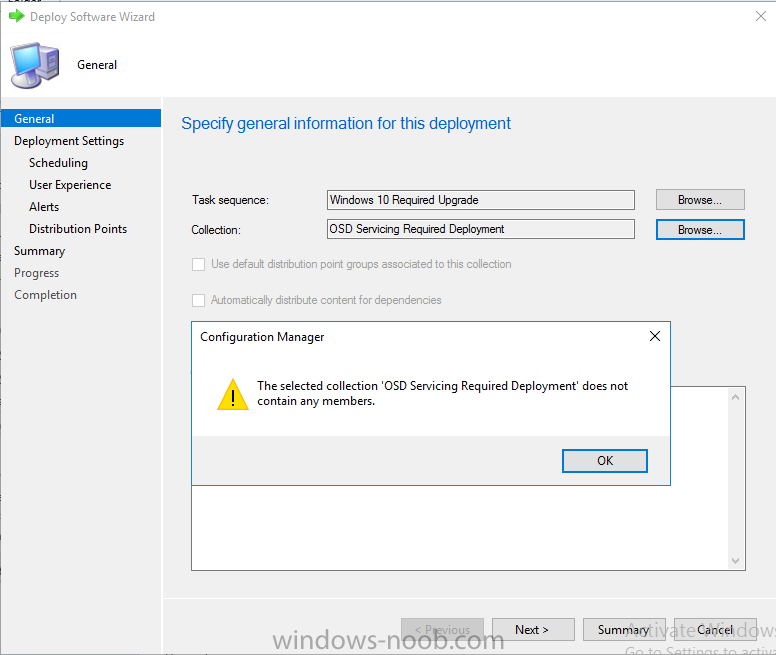
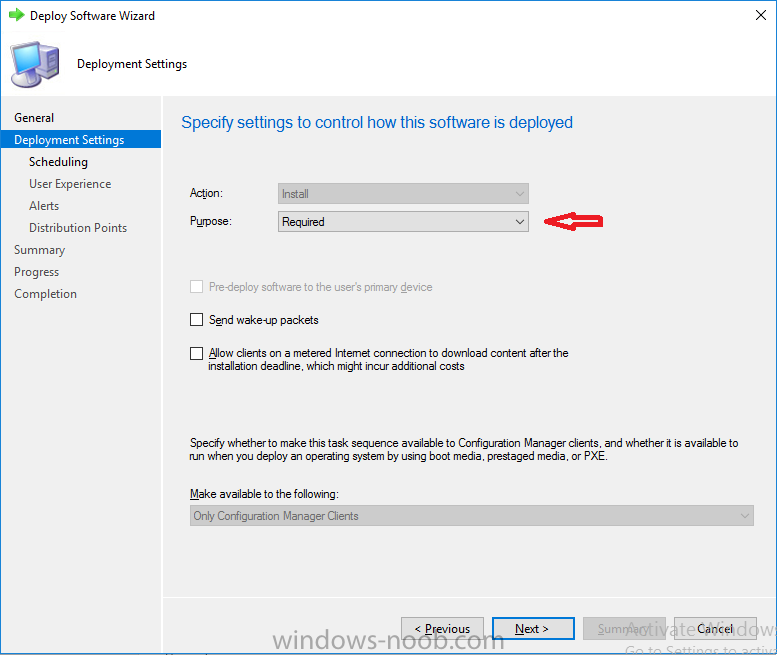
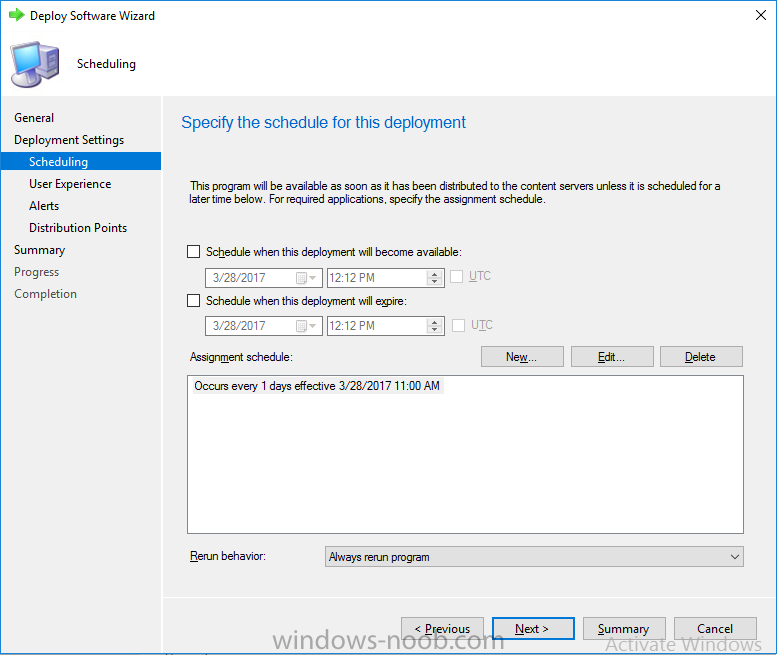
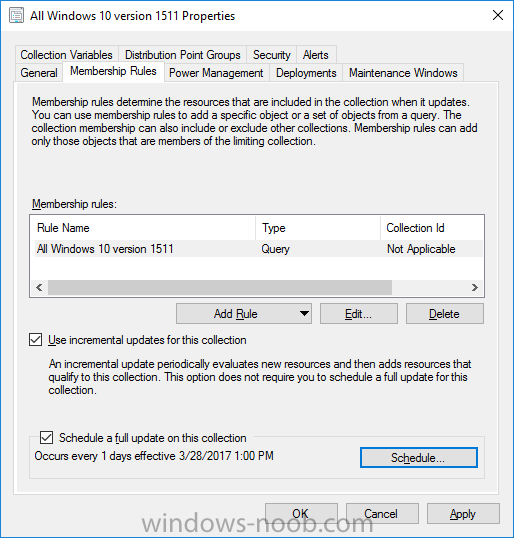
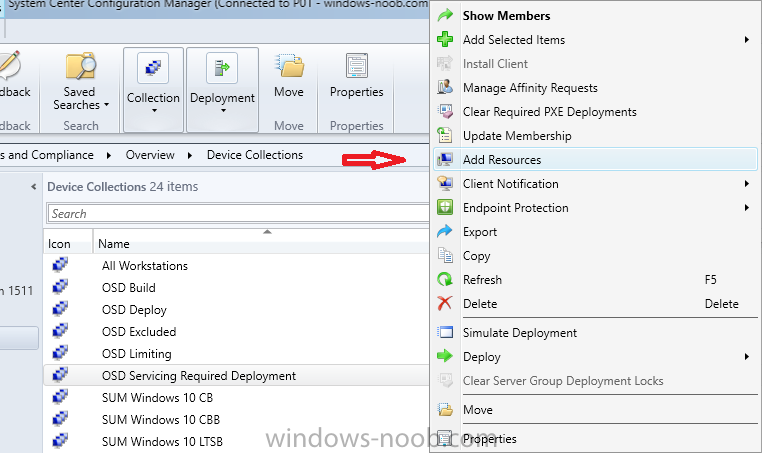
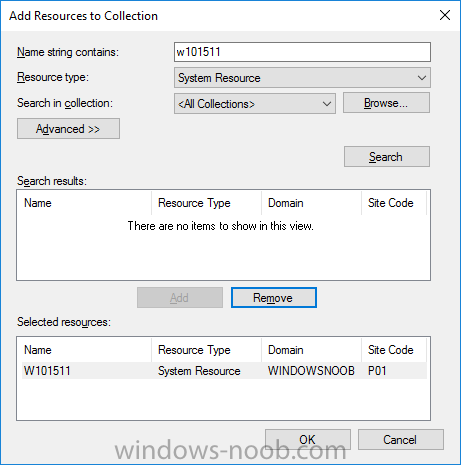
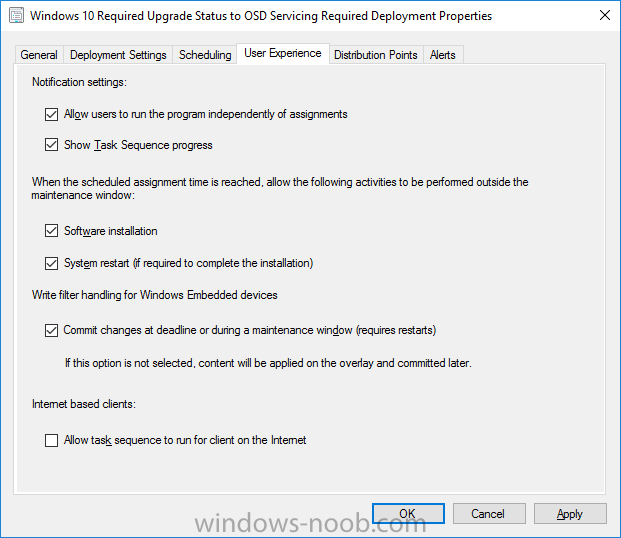
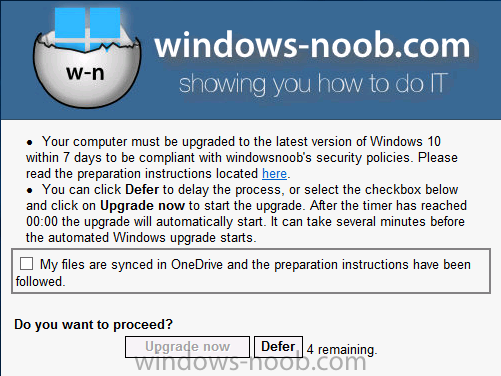
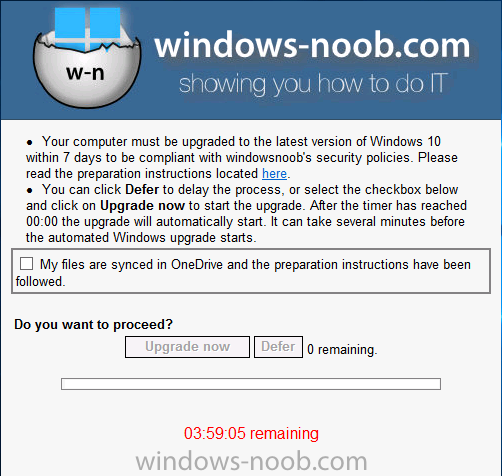
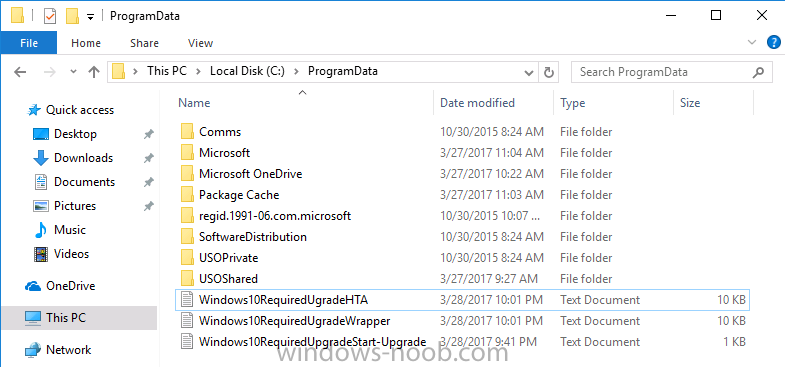
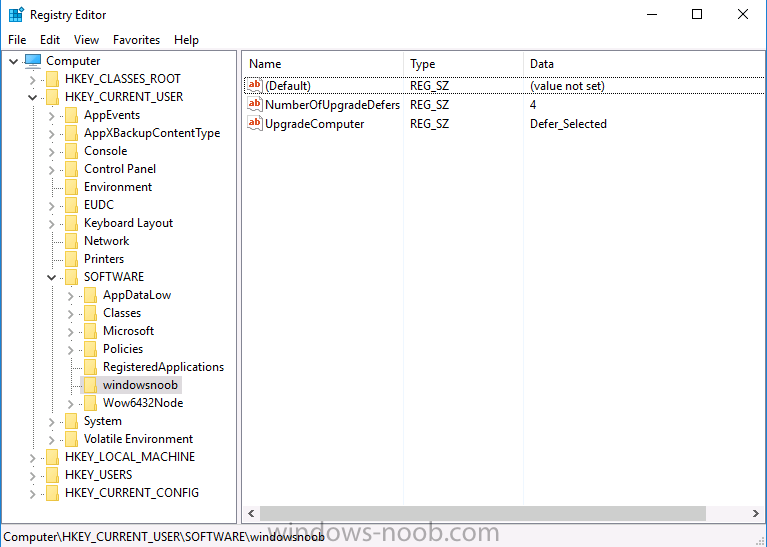
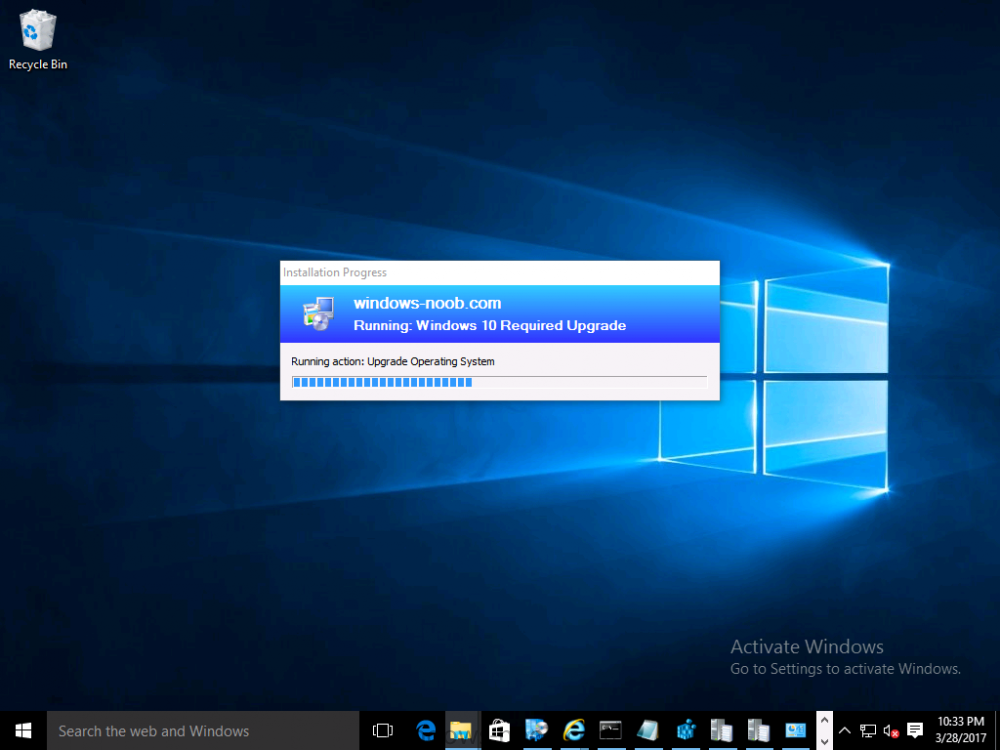
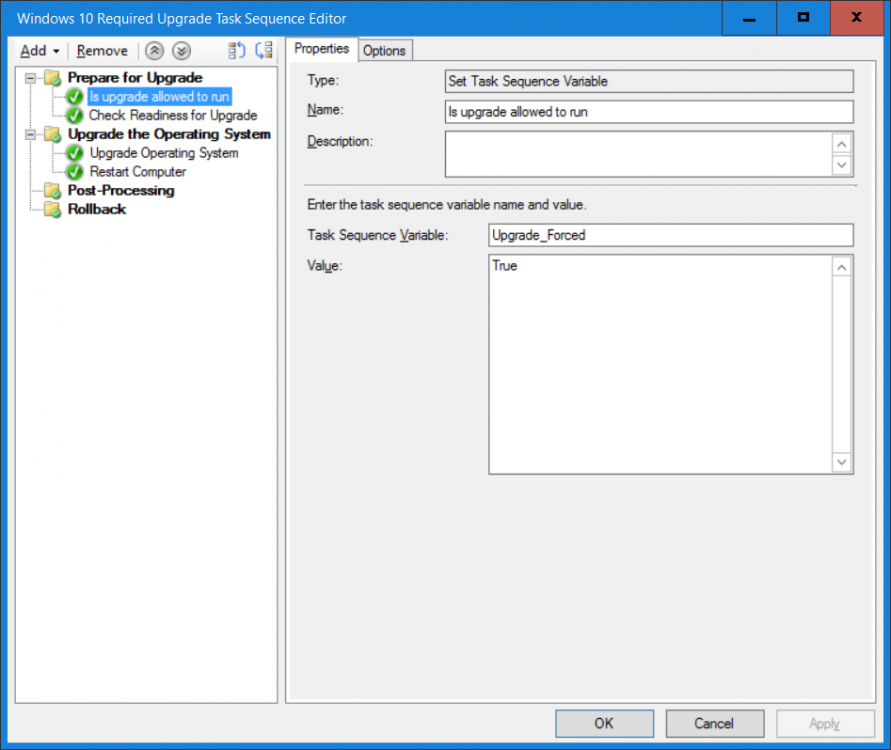
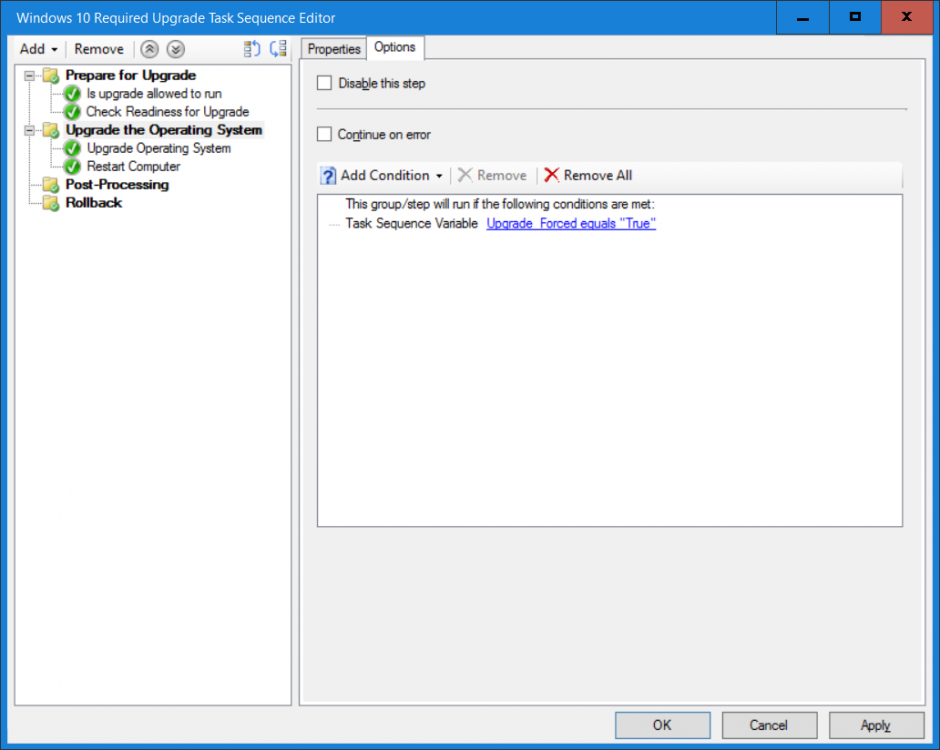
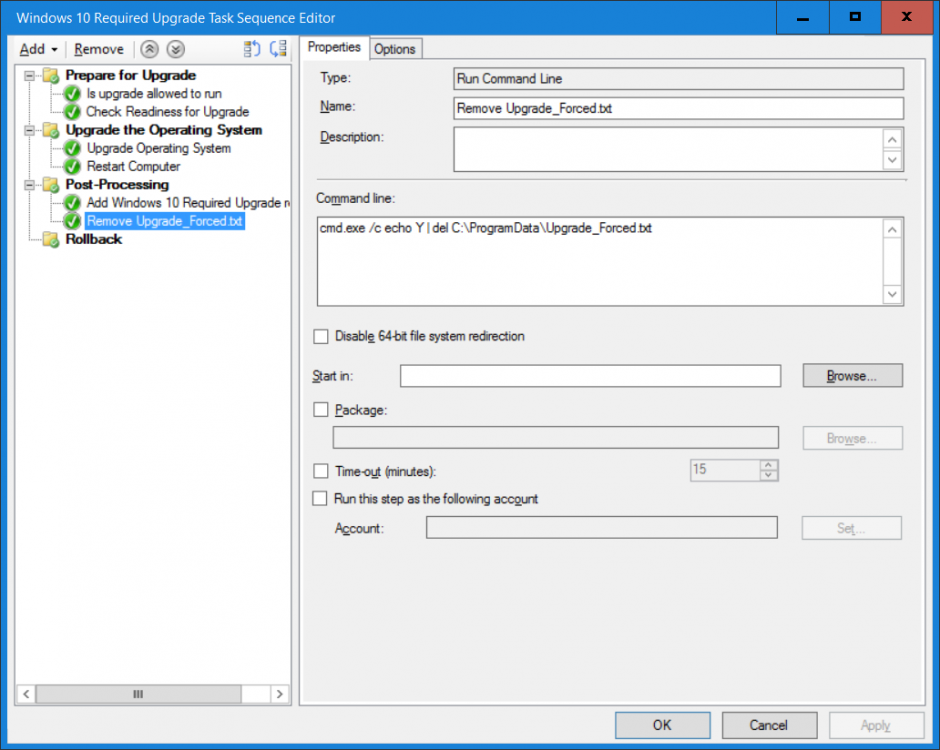
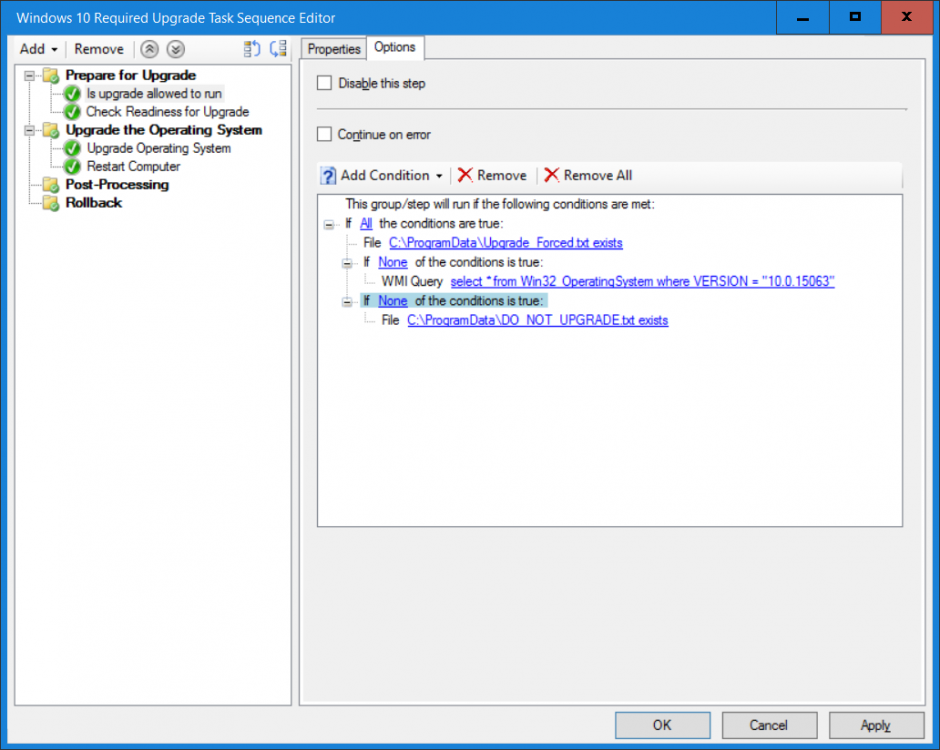
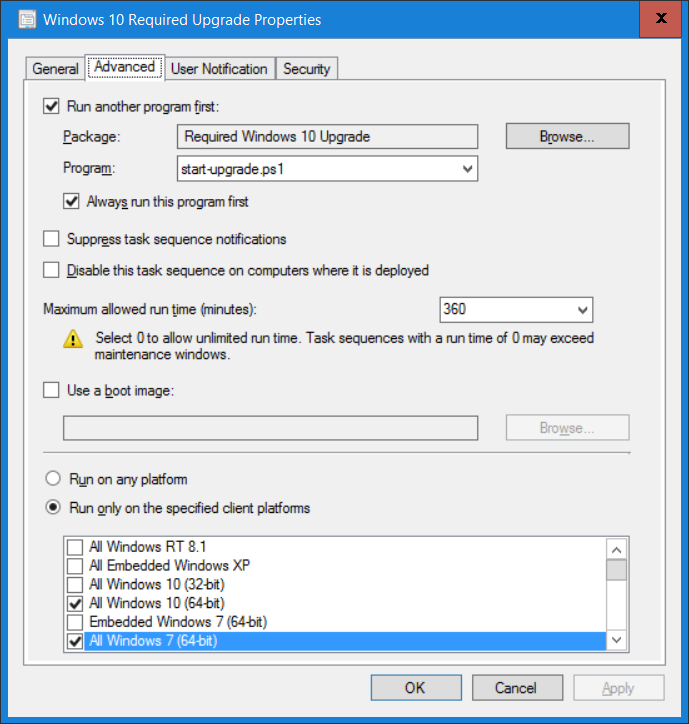
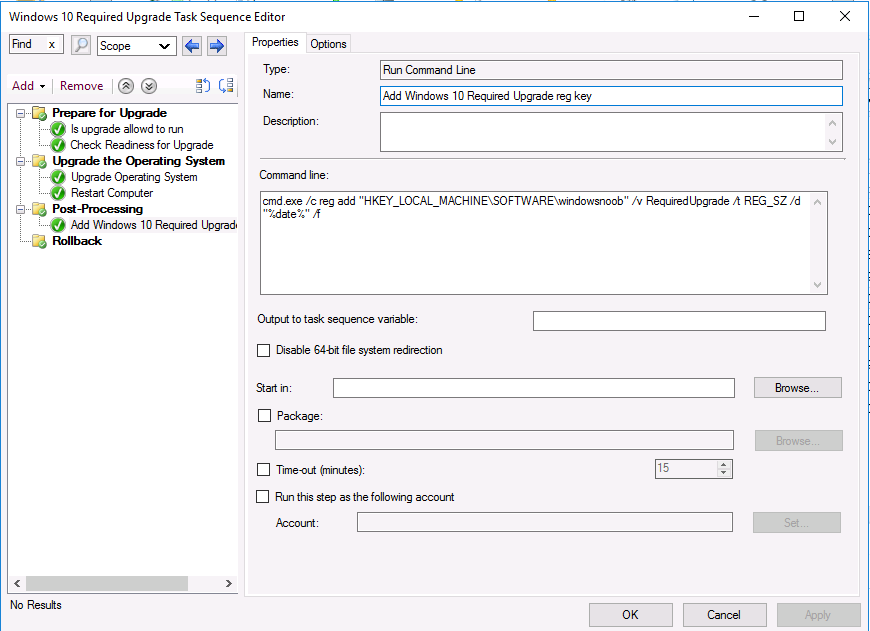
Note: I've upgraded the wrapper to PowerShell 2019/01/06 as explained here. Introduction This blog post is all about upgrading to Windows 10, either from Windows 7 or from an earlier release of Windows 10 to the latest release of Windows 10. Windows 10 is probably one of the fastest developing operating systems from Microsoft yet, and was initially released in July 2015 as Windows 10 version 1507. The version 1507 nomenclature equates to (YYMM) or year year, month month so you'll always know when a version was released to manufacturing (declared RTM). So far we've seen the following Windows 10 mainstream versions (not including LTSB/LTSC) Windows 10 version 1507 Windows 10 version 1511 Windows 10 version 1607 Windows 10 version 1703 Windows 10 version 1709 Windows 10 version 1803 Windows 10 version 1809 As each new version of Windows 10 is released, the new features it contains ensure that it is desirable to some and it's just a matter of time before people want to upgrade to that version given the chance, but even with all the latest and greatest features, some users just won't upgrade if given the choice for whatever reason. There is however another element to consider and that how long Microsoft will release security updates for any given release of Windows 10 (i.e. how long is that release supported by Microsoft). Michael Niehaus discusses simplifying Windows As A Service (WAAS) here but in a nutshell there is an 18-month servicing timeline for each release however, Microsoft have added an additional 6 months to ease your pain, for now. Update: In September 2018, Microsoft blogged the following after years of listening to customers complaining about the WAAS support lifecycle. In a nutshell, there are two main releases of Windows 10 for the Enterprise to think about going forward, the 03 releases (18 month support) and the 09 releases (30 months support). Based on that statement alone, Enterprises will most likely opt for the 09 releases to avoid disruption to business and to their end users. This leads you to deal with the security support ability in a couple of ways, you can make the new upgrade available in Software center and hope your users will upgrade (seriously do you think they will ?), or you can get tough and decide when and where they will upgrade. To do that you have two options: servicing plans task sequences I've discussed servicing plans here so I won't go over that subject again, they are a valid option for many but are not very dynamic. With task sequences you have far greater control over how to deal with things that can break servicing plans (such as incompatible AntiVirus software or Windows Language packs). Assuming that you've made the choice to use task sequences to forcefully upgrade your computers to the next version of Windows the next problem is how do you force the upgrade. The answer is defined by the purpose of the task sequence deployment, namely Required (or mandatory). Just mentioning the words Required and Task Sequence is usually enough to make any seasoned ConfigMgr admin shiver. Why ? well there are many cases of people who've had career changing events in relation to required task sequences, therefore using them must come with a big fat warning, so here it is. WARNING! Using required task sequences is risky! Use them with extreme care and always test thoroughly. Disclaimer: if you choose this method and it all goes wrong, I'm sorry, I cannot accept liability. In this guide I show you how to set it up in a safe way and I include a 'get out of jail free' in case you make a mistake. It's up to you to test what works in your organization and what doesn't. My advice is that you test this thoroughly in a lab and once you are happy with the results, recreate it in production and continue to test it thoroughly. Also, be very careful about how you add computers to the required collection especially if it involves queries. Note: The Get out of Jail free step will help to secure your environment towards any accidental upgrades. Now that that is out of the way, let's get on with it. In this post I'll show you one way of forcefully upgrading your computers from a soon to be unsupported version of Windows 10 to the latest and greatest, and I'll include steps and advice to help you 'protect' yourself from disaster. In this guide we'll be forcing our source Windows 10 version 1511 computers to upgrade to the target Windows 10 version 1607. Note: you can always change the target Windows 10 version to whatever build you want (using the TargetBuild variable) as described in the Troubleshooting section at the end of this guide. Notifying users There is one other thing to consider about required task sequences, they are normally for all intents and purposes zero touch meaning no user interaction. That is fine for simple quick changes such as upgrading applications but if your users are going to have one or two hours downtime due to a forced Windows upgrade, you'll want to notify them and give them options to defer for a limited time period to a time that makes sense for them. In this guide I assume that the client setting Show notifications for new deployments in Computer Agent is set to No, that is a common client setting in organizations as it means less annoyances for the end user and of course there are other ways to notify a user about mandatory actions (PowerShell Application Deployment Toolkit for example). The recently released System Center Configuration Manager (Current Branch) version 1702 contains a great ability to edit the user notification message shown to users but it's limited in ability and it depends on your configured notification settings. So how do we solve that problem in a nice way. ConfigMgr allows us to chain programs before the task sequence begins and that's the key to this solution. Step 1a. Get out of jail free (recommended) The wrapper will not allow the HTA to display if a file called DO_NOT_UPGRADE.txt is present in C:\ProgramData. If you are paranoid about accidental upgrades (and you should be if using required task sequences) then do as follows. 1. Create a package (with no content) with a program to deploy a text file to all computers that are at risk of accidental deployment. Run the package daily. The program is simply a one liner as follows: cmd.exe /c echo "Windows 10 Required Upgrade" > C:\ProgramData\DO_NOT_UPGRADE.txt 2. Target the OSD Servicing Required Deployment collection with another package/program that will remove the Do_NOT_Upgrade.txt file. Run the package every 2 hours. The program is again a one-liner, as follows: cmd.exe /c echo "Y" | del C:\ProgramData\Do_Not_Upgrade.txt The above actions should protect your computers from accidentally being targeted by the task sequence. Any computer that has the Do_NOT_Upgrade.txt file present, will not show the popup (HTA) and will not run the task sequence and thus, will not upgrade until you are ready to do so. Step 1b. Create some collections (optional) This step is optional but recommended as it will give you a base of collections to manage your deployments. To complete this step download the CreateWindows10DeviceCollections.ps1 PowerShell script in the downloads section and run it as Administrator in PowerShell ISE as shown below. This script not only creates collections to make your job of finding different versions of Windows 10 easier, but it adds queries, include and exclude rules as necessary. and below is a subset of the collections created (there are 18 in total). The OSD Servicing Required Deployment collection is limited to Windows 10 version 1511 as that is our target for the required upgrade. This does not mean that it will use all computers in that collection it just means it will only use computers added to the OSD Servicing Required Deployment collection provided that they are also present in All Windows 10 version 1511. This ensures that you are targeting the correct version of Windows 10 for the required upgrade. Step 2. Create a Package/Program In this step you'll add a simple package/program that contains a few scripts. These scripts have error checking, logging and more built in so that you can trace what was done and when. These scripts will be chained to the required task sequence meaning that they must run successfully (with an exit code of 0) before the actual task sequence can start. User actions such as Defer in the popup will force an exit code 99 and the task sequence cannot start. Download the scripts in the downloads section and extract somewhere useful. Copy the Required Windows 10 Upgrade folder to your source folder on your ConfigMgr server. In the ConfigMgr console, select Application Management, Packages and Create Package. Give the new package a suitable name such as Required Upgrade to Windows 10 and point it to the source folder. For Program Type, choose Standard Program. In the Specify information about this standard program screen fill in the following details, Note: keep in mind that if you set Program can run Only when a user is logged on that that becomes a requirement, i.e. that a user must be logged on in order for this to run. You may want to get even tougher and set the Program can run option to Whether or not a user is logged on. If you do set it to Whether or not a user is logged on, and if the user is not logged on, the scripts will write to HKEY_USERS\.DEFAULT\Software\windowsnoob and you may need to update the scripts to detect this change. Name: start-upgrade.ps1 Command line: Powershell.exe -Executionpolicy bypass ".\Start-Upgrade.ps1" Startup folder: Run: Hidden Program can run: Only when a user is logged on Run mode: Run with user's rights Drive Mode: Runs with UNC name Note: If your target computers are running Windows 7, then place a check mark in the All Windows 7 (64 bit) box also. in the Specify the requirements for this standard program screen use the following values This Program can run on only on specified platforms: All Windows 10 (64 bit) Estimated disk space: 10 MB Maximum allowed time (minutes): 250 click next through to completion. Step 3. Modify the package On the newly created package, right click and choose Properties, click the Data Access tab. Select Copy the content in this package to a package share on distribution points Click Apply and OK. Step 4. Distribute the package to your distribution points Right click the package and choose Distribute Content select your distribution points and continue through the wizard until completion Step 5. Modify an existing Windows 10 Required Upgrade task sequence In this step I'll assume you've already created your Windows 10 Required Upgrade task sequence. If you haven't already then take a look at this post to see how. Locate the task sequence in the ConfigMgr console, right click and choose Properties, in the Advanced tab place a check mark in Run another program first and select the Windows 10 Required Upgrade program. In the Run only on the specified client platforms screen select All Windows 10 (64 bit). Note: Make sure that Always run this program first is checked. Note: If your target computers are running Windows 7, then place a check mark in the All Windows 7 (64 bit) box also. Next, edit the task sequence and add a new Set Task Sequence Variable step as the first step in the task sequence, name it Is upgrade allowed to run. Fill in the following values Task Sequence Variable: Upgrade_Forced Value: True Click on the options tab and add the following options: If ALL the conditions are true: File C:\ProgramData\Upgrade_Forced.txt exists If None of the conditions is true: WMI Query: select * from Win32_OperatingSystem where VERSION = "10.0.15063" If None the conditions are true: File C:\ProgramData\DO_NOT_UPGRADE.txt exists These three checks allow us to halt the task sequence on computers that don't meet our upgrade criteria. Note: You'll need to decide what build is deemed 'the latest version' of Windows 10 in your organization and change accordingly. In this post I'm assuming that is Windows 10 version 1703 (build 10.0.15063). On the Upgrade Operating System step, edit the Options and include the following Task Sequence Variable: Upgrade_Forced=True Note: This will ensure that the required upgrade only occurs if the Upgrade_Forced.txt file was present in C:\ProgramData. Next in the Post-Processing group add a new Run Command Line step called Add Windows 10 Required Upgrade reg key with the following command line: cmd.exe /c reg add "HKEY_LOCAL_MACHINE\SOFTWARE\windowsnoob" /v RequiredUpgrade /t REG_SZ /d "%date%" /f This will allow you to run reports on when computers were upgraded using this method. Close the task sequence. Next create a new Run command line step called Remove Upgrade_Forced.txt with a cmd line of cmd.exe /c echo Y | del C:\ProgramData\Upgrade_Forced.txt Step 6. Deploy the task sequence In this step we deploy the task sequence with a purpose of required. Note: I'd strongly advise you to test this thoroughly in your lab and make sure to pick your collections correctly and to populate them very carefully. Right click on the task sequence and choose Deploy For collection choose OSD Servicing Required Deployment, and ignore the popup telling you it's empty, you can add computers to that collection later. Change the Purpose to Required For Scheduling click on New, then choose Schedule, then change it to run daily at 11am. For rerun, choose Always rerun program as you will update the limiting collection (All Windows 10 version 1511) membership daily @ 1pm and upgraded computers will fall out of the collection. In case they don't (for whatever reason) the wrapper checks for the targetbuild and if the computer matches that build, it will abort and not start the upgrade. Note: The above schedule will run our popup daily at 11am for 6 days prior to forcing the upgrade to Windows 10. You should change the schedule according to your preferences. Continue through the wizard until completion. Note: If you want to test run the Task Sequence from the Software Center or if you want your users to do this, then enable the Allow users to run the program independently of assignments checkbox on the User Experience tab. Step 7. Adjust Windows 10 limiting collections membership schedule Below you can see the membership rules update frequency on the limiting collection, it's set to run two hours after our Upgrade, adjust as necessary for your organization and your agreed schedule. Step 8. Add test computers to the OSD Servicing Required Deployment collection Note: Before doing this step, carefully read the Warning and Disclaimer at the top of this guide! Right click on the collection and choose Add Resources (or use your own chosen method to add computers) to add one or more test computer to the OSD Servicing Required Deployment collection. As this collection now has a live required task sequence deployed to it, do this step very very carefully, if in doubt stop what you are doing, go and have a coffee and try again when your nerves are calm. and add your test computers as you see fit.. Step 8. Monitor the experience on test computers Login to a test computer, do a machine policy update in the ConfigMgr client actions and wait for the popup or kick it off via software center. After the computer receives the policy and the scheduled time is reached a popup is shown offering the user to Defer the upgrade or Upgrade now by selecting the appropriate checkbox and then clicking on Upgrade Now. Note: The clickable link goes to a non-existant url, you need to point it to whatever documentation you want your users to read in preparation for the upgrade. As each day passes (or based on your custom schedule) the counter reduces by 1 every time the popup appears. When there are no more deferrals left, a 4 hour countdown starts and when it reaches 00:00:00 the Windows 10 Required Upgrade will start. If the user closes the popup, the timer will resume where it left off when it is restarted. Alternatively, if the user doesn't want to defer, and they want to run the upgrade right now, they can place a checkmark in the 'My files are synced in OneDrive...' and then click Upgrade Now to start the task sequence. Either way, regardless of what your user clicks on, (based on the schedule in this guide) the computer will start the upgrade within 7 days (or earlier or later if you adjust the schedule). Once the Upgrade Now button is clicked on, or once the Timer reaches 00:00:00 the task sequence will automatically start (assuming that the DO_NOT_UPGRADE.txt is not present). Branding Simply replace the banner.png file included with one matching your Company Name, edit the upgrade.hta and locate the 'windowsnoob' name in the text field (line 347) and replace it with your own Company Name. Troubleshooting The popup creates 3 log files to troubleshoot the process, they are located in C:\ProgramData and named Windows10RequiredUpgradeHTA.log Windows10RequiredUpgradeWrapper.log Windows10RequiredUpgradeStartUpgrade.log The wrapper writes to the registry in HKCU\Software\windowsnoob Note: The collections, scripts and task sequence assume you are upgrading from Windows 10 version 1511 to Windows 10 version 1607, you'll need to edit the WMI Query in the task sequence to change Windows 10 build version when you move to creators update and for later versions of Windows, and you'll need to edit the TargetBuild variable in the wrapper.vbs script accordingly. Once done, you should change the Limiting Collection for the OSD Servicing Required Deployment collection to match the n-1 version of Windows 10 you want to migrate from. Tip: If you have rendering issues with the popup on different devices then edit the call ResizeWindow(425,335,500,375) values and ResizeWindow Function to fit your specific needs, I don't have access to too much hardware to test this on. The popup is fixed, if you want the user to be able to move it change the line caption="no" to caption="yes". If you want to programmatically use it then add a Window.moveTo(x, y) line. Downloads You can download the scripts used above in the following zip files: windowsnoob Required Upgrade HTA.zip CreateDeviceCollectionsWindows10.zip Summary Forcefully upgrading computers is a tricky area but hopefully this method gives you one more option to consider.
- 242 replies
-
- 1
-

-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
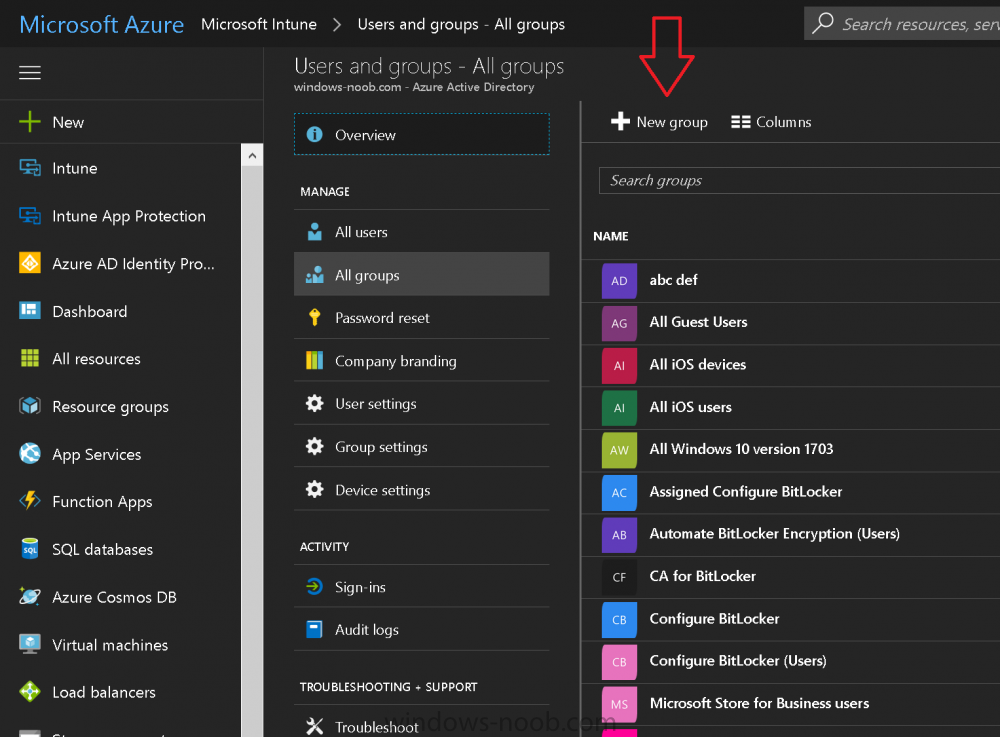
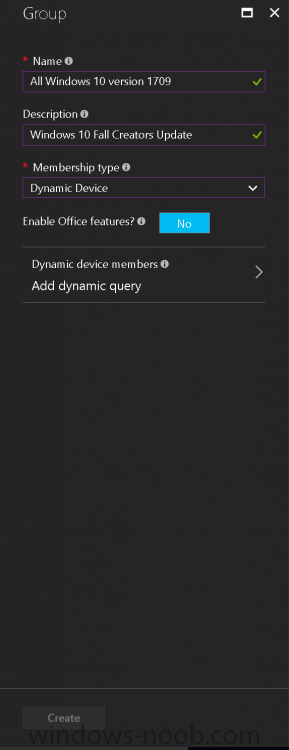
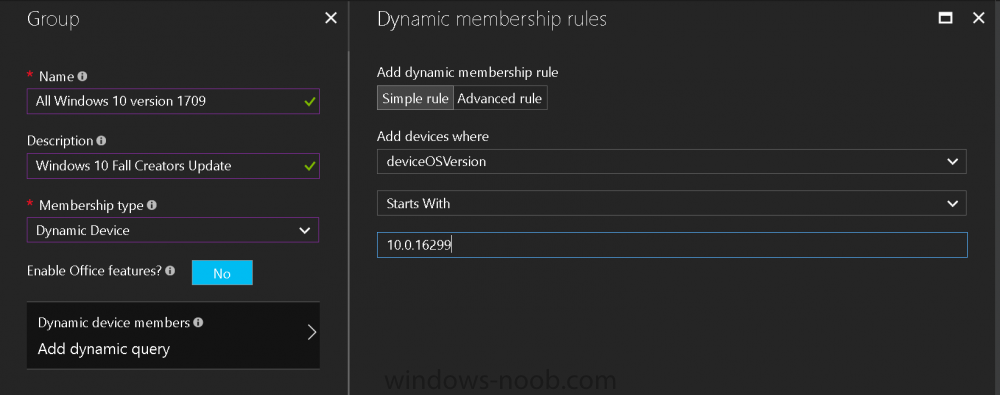
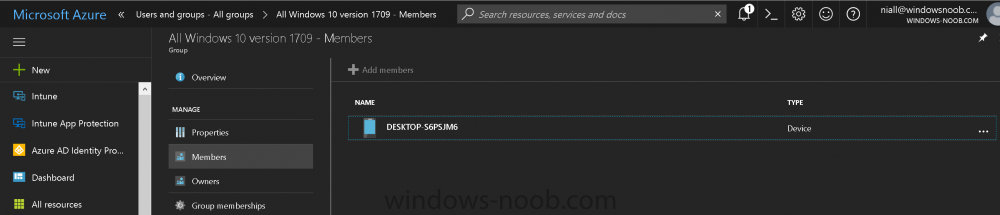
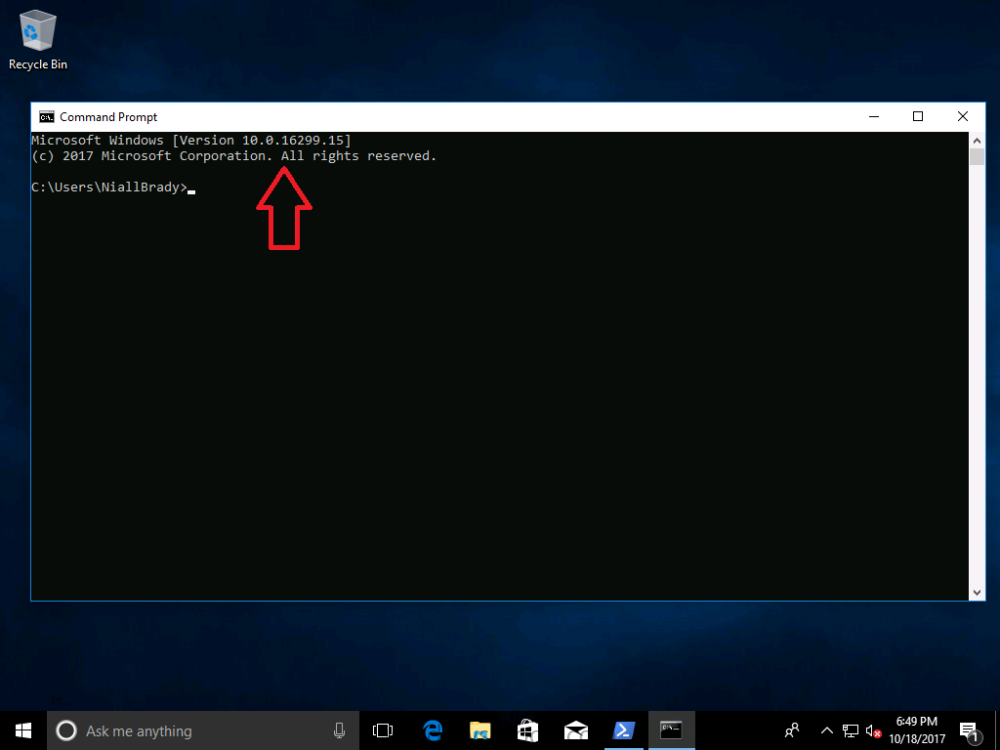
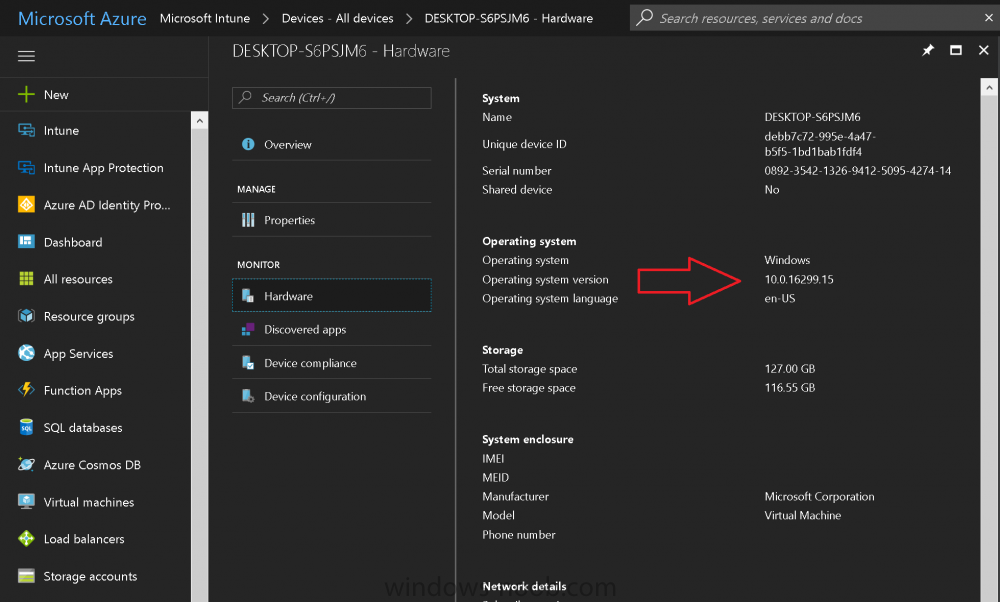
Introduction Microsoft released Windows 10 version 1709 to VLSC and MSDN yesterday, so of course people are deploying it and testing it in their environments. If you want to create a dynamic Group (that auto populates) of Windows 10 version 1709 in Microsoft Intune then do as follows. Note: In this blog post I assume you have configured MDM auto-enrollment in Azure. This isn't mandatory but makes enrollment into Microsoft Intune for Windows devices much easier. To see how to enable that functionality, click here. Step 1. Login to Azure Login to https://portal.azure.com and select the Intune service. Step 2. Create a dynamic devices group Click on Groups. Select New Group (highlighted with the Red Arrow). In the New Group blade, use the following options Name: All Windows 10 version 1709 Description: Windows 10 Fall Creators Update Membership Type: Dynamic Device In the Dynamic Device members Add Dynamic Query option, enter the following Add device membership rule: SimpleRule Add devices where DeviceOsVersion StartsWith 10.0.16299 Next, click on Add Query Followed by Create. You'll get a notification in the top right that the group was successfully created. Step 3. AzureAD join a Windows 10 version 1709 device Go through OOBE on a Windows 10 version 1709 device, at the account screen enter your Azure AD credentials. and after the device has joined Azure AD, it'll show up in Intune soon after in the correct Group. Job done ! You can verify the build number on a Windows 10 version 1709 device by opening a command prompt, in this screenshot it's 10.0.16299.15, the .15 at the end will increase as new cumulative updates are installed on this base build number. and that full string can be seen in Intune in Devices, select All Devices, select the device in question and click on Hardware. Note: If you'd like to create a collection in SCCM for Windows 10 version 1709 please see the following blog post. For a list of deployment resources for Windows 10 version 1709 please see here.
- 3 replies
-
- windows 10
- fall creators update
-
(and 2 more)
Tagged with:
-
Hi is it possible to disable Bluetooth file transfer but sill allow Bluetooth to attach Mice, keyboards, etc. Ideal apply this via group policy. Thanks Rob
-
Hi All, We are experiencing a weird issue with BitLocker when re-installing existing Windows 10 1709 machines with Windows 10 1903. The machines are hybrid AD joined and the BitLocker recovery information is stored in Active Directory. During a new installation of the device with Windows 10 1903, the BitLocker key fails on storing the recovery information in Active Directory. After examining the Windows event log, it turns out the device is trying to store the recovery information in Azure AD. Is this new behavior of Windows 10 1903 and can we modify this behavior?
-
- bitlocker
- windows 10
-
(and 3 more)
Tagged with:
-
Hello all, I have a windows 10 image that I am deploying to devices which is currently version 1703. This is obviously not ideal being almost 3 years old. Is there a relatively painless way to update this image or will I need to install and update on a system and then recapture this install image? Thanks.
-
In my Windows 10 LTSC 1809 task sequence, the Install Software Updates step is failing to run. I have attached the log files for the latest attempt to build a test machine. I have deployed the required software update group to both the Unknown Computer collection (as I am deleting the SCCM object for the test machine before each test build) and to a common collection that all of the test machines are put into. The machine does receive and install updates post-build successfully so it is not the software update group or the deployment package as far as I can tell. smsts.zip UpdatesDeployment.log UpdatesHandler.log UpdatesStore.log WUAHandler.log
-
- windows 10
- sccm
-
(and 1 more)
Tagged with:
-
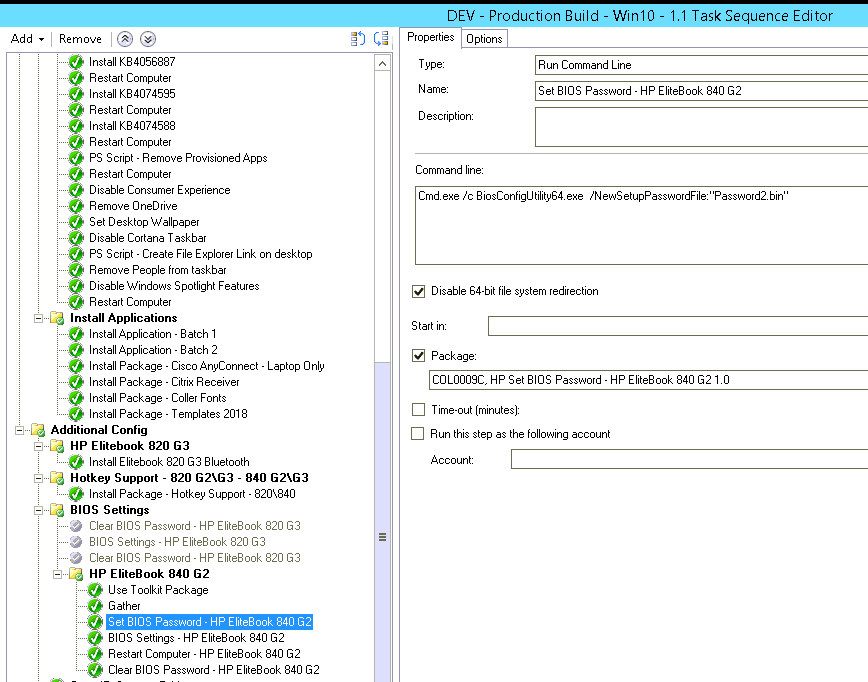
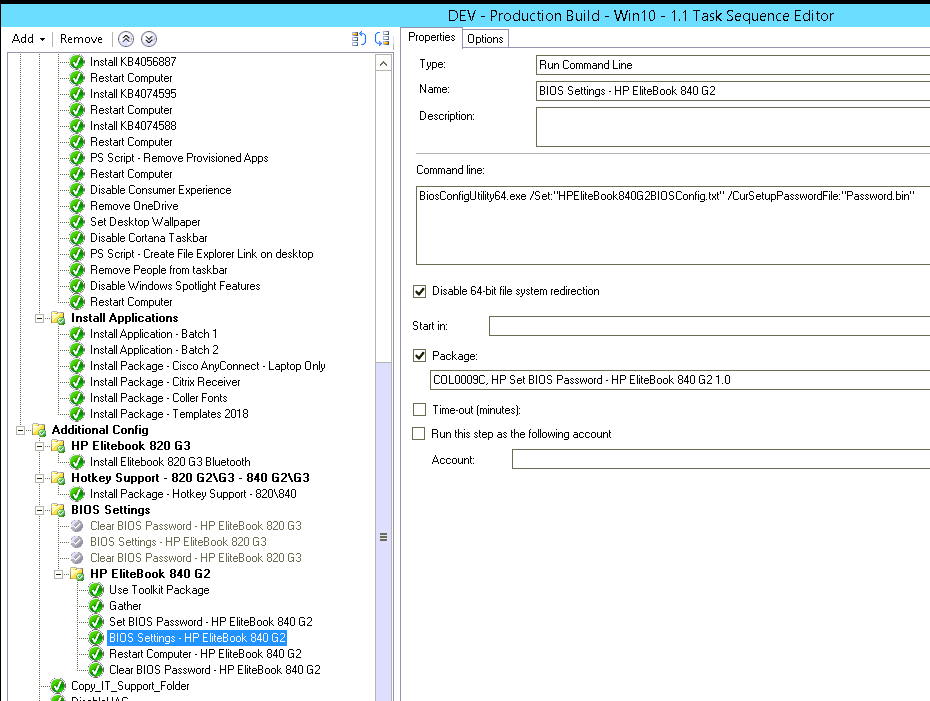
Hi guys, Hoping to find people that have managed to push HP BIOS settings via OSD (Windows 10), I've pretty much followed this guide (only the folder structures are slightly different) but I'm having issues actually deploying the settings, setting the BIOS password seems to work okay and I've read that for certain TPM settings to be pushed then a BIOS password must be set prior. My folder setup: BIOS Config settings to push: BIOSConfig 1.0 ; ; Originally created by BIOS Configuration Utility ; Version: 4.0.24.1 ; Date="2018/03/20" Time="14:53:23" UTC="0" ; ; Found 215 settings ; Virtualization Technology (VTx) Disable *Enable Reset to default TPM Reset to Factory Defaults *No Yes Reset of TPM from OS *Disable Enable OS Management of TPM Disable *Enable Activate TPM On Next Boot Disable *Enable TPM Device Hidden *Available TPM Activation Policy F1 to Boot Allow user to reject *No prompts Hide TPM Device Security Level Change *View Hide OS Management of TPM Security Level Change *View Hide Reset of TPM from OS Security Level Change *View Hide Task sequence setup: The bios password sets just fine, but in the SMSTS log I see the following for BIOS settings - HP EliteBook 840 G2 itself: Have attached the SMSTS.log. Any help would greatly be appreciated, I've been working on this for the last couple of days without success, I've tried: Adding CMD.exe /C prefix (same error) Changing the format of the file to repset (same error) Ran the command manually on the device and works just fine with the same configuration files (as .txt and .repset) Tried running the steps in WinPE rather than in the operating system (same error) Thanks in advance. smsts.log
-
Hi, I'm in the process of deploying Windows 10 (x64 Enterprise Build 1809) at a customer site using Configuration Manager Current Branch (1806 + Hotfix). Office 365 Click-to-Run is a Tier 1 application that I am installing during deployment of the OS to the endpoint machine. In order to ensure the O365 C2R content is the latest "Semi-Annual Channel" version (client is bound by regulation to patch applications, so testing this with Office) I've setup the following: "Content" for the Application in CM is JUST setup.exe plus XML files for the install. Two XML files for install for two different locations (one of which is on at a low-speed WAN site). Each XML refers to source content in an open share on the Distribution Point servers - one of which is at the low-speed WAN site. Two deployment types in the Application - one for each XML. Setup a Scheduled Task on the Distribution Point servers to update the share (not the Application content) on a regular basis So my plan was then to use a "Requirement" on the application using a custom Global Condition that determines the Active Directory site (created using PowerShell). The idea then being that during deployment, the application installs using the latest available SAC version and administrators don't need to worry about the Application content being updated. And of course, the XML file then tells it to grab the content from the local site, which is highly connected. Works wonderfully well in Software Center in my testing. BUT, doesn't seem to work in OSD Task Sequence ☹️. If I am reading error logs right, it seems as though the PowerShell in the Global Condition is not being allowed to run (even when I set Execution Policy to "Bypass" earlier in the Task Sequence. So, perhaps I am making things more complex than they should be. Simplest thing to do would be to create two separate applications using the same method (i.e. not just two deployment types) and use a Dynamic Variable in the Task Sequence that installs one or the other dependent upon gateway IP. However, throwing it out there for some thoughts on how I could do this using the multiple deployment methods on the single app. Thanks, Matt
-
- office 365
- click-to-run
-
(and 8 more)
Tagged with:
-
Hi, I have a Windows 10 1607 image I configured and captured ages ago that I want to update to 1803. I thought I could use Scheduled Updates option to patch it up and I did install a number of updates into the image but it is still showing version 10.0.14393 (1607). Is there any way to offline service this image up to 1803 or am I going to have to recapture the image? Thanks in advance! Regards, Andrew.
- 2 replies
-
- windows 10
- 1607
-
(and 1 more)
Tagged with:
-
I recently went through the trouble of configuring the use of Windows 10 Servicing Plans only to discover that they are close to redundant. Servicing Plans (SP) are literally Automatic Deployment Rules (ADR) which has some different options. You could achieve something almost identical using ADRs only. I discovered this because I had started testing my deployments of SPs and all was going well, then I noticed that Feature Updates were also being added to my ADRs for Windows 10. This is where I discovered SPs are ADRs with extra bits. My understanding is that SPs were going to be put in place for ease of upgrade to new versions of Windows 10 and to make it as easy as possible for SCCM admins. This has been a catastrophic failure due to the huge bugs in each release of Windows 10, even once they are classed as "business ready." The most recent one is a problem with certificates. Is anyone using Servicing Plans as they were originally intended, that is completely automating it? Are you finding it is more trouble than it is worth?
-
- automatic deployment rules
- servicing plans
-
(and 1 more)
Tagged with:
-
Hi all, First time poster, so apologise in advance if I post incorrectly. Currently building Windows 10 devices, some are upgrades from Windows 7 to Windows 10 and others are fresh Windows 10 using SCCM (MDT integrated). This works as expected, but when I log in and check TPM Administration the following message show up Reduced Functionality errors codes 0x400900 = The Device lock counter has not be created 0x2900 = The monotonic counter incremental during the boot has not been created Do I need to do something in the Task Sequence to clear the protectors or clear TPM before BitLocker is enabled Cheers all
-
I've been pushing the upgrade from Windows 7 to Windows 10 1607 for a couple of months. Have done 600+ machines succesfully. All of a sudden, starting a few weeks ago ALL upgrades are failing and rolling back to Windows 7 with one of the following errors: The task sequence execution engine failed execution of the task sequence. The task sequence manager could not successfully complete the execution of the task sequence. I suspect it's failing at the Intel HD video driver that's incompatible because I have to accept the removal when manually updating. Before, it would just delete and add the Microsoft generic, and I'd have to load the Win10 Intel Driver later in the task sequence. ...but that's just a guess. Where should I look and what do I look for? Why all of a sudden would this stop working?
- 1 reply
-
- upgrade
- windows 10
-
(and 1 more)
Tagged with:
-
Hi all, I really hope someone can help as I've spent an unbelievable amount of time trying to get this working with no success. I'm using USMT from the 1607 ADK and I'm trying to relocate a legacy Sticky Note file (.snt) from a windows 7 machine to the new Sticky Note modern app location on a Windows 10 machine. W7 location = %AppData%\Roaming\Sticky Notes\StickyNotes.snt W10 (1607) location = %LocalAppData%\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalState My USMT script is currently able to sucessfully collect up the snt file from a W7 machine and return it to the exact same place on a W10 machine but a manual step is then required to move this file to the new loaction. A legacy snt file can be migrated to W10 by creating a new folder called "Legacy" and putting the "StickyNotes.snt" file in there and renaming it to "ThresholdNotes.snt". So I require the USMT restore to create the "Legacy" folder, put the "StickyNotes.snt" file in it, then rename it to "ThresholdNotes.snt so that the new path looks like: %LocalAppData%\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalState\Legacy\ThresholdNotes.snt This is explianed here: http://www.winhelponline.com/blog/recover-backup-sticky-notes-data-file-windows-10/ I have found the following info online where someone has apparently got USMT sucessfully migrating snt files to the correct location but I can't get it working: https://www.mail-archive.com/mdtosd@lists.myitforum.com/msg03057.html Has anyone successfully managed to migrate StickyNote files over in this way with USMT? Thanks, Westy
- 11 replies
-
- windows 10
- sticky notes
-
(and 1 more)
Tagged with:
-
Windows 10 (code named Redstone 4) version 1803, is finally available for download on MSDN. This is the successor to Windows 10 Fall Creators Update (version 1709). It is also available for download here. https://www.microsoft.com/en-us/software-download/windows10 Here's a video about the new TimeLine functionality incuded in Windows 10 April 2018 Update. and for details about what's new, see here: https://docs.microsoft.com/en-us/windows/whats-new/whats-new-windows-10-version-1803 To get the feature update via Microsoft Update see the following Blog Post: https://blogs.windows.com/windowsexperience/2018/04/30/how-to-get-the-windows-10-april-2018-update/#.WudkRA_6qwM.twitter and here is the Windows 10 release information for all releases of Windows so far: https://www.microsoft.com/en-us/itpro/windows-10/release-information
-
- timeline
- redstone 4
-
(and 2 more)
Tagged with:
-
Hi all, I'm hoping that someone can help as I'm really struggling to find anyone else that's had this specific problem. When trying to build brand new HP equipment with an SCCM (MDT integrated) OSD task sequence I am seeing the following error when the machine runs the "Invoke-MbamClientDeployment.ps1" script: Failed to escrow TPM owner-auth to http://MBAMSERVER.domain/MBAMRecoveryAndHardwareService/CoreService.svc. HRESULT: 0x80280012 I've found that 0x80280012 means "There is no Storage Root Key (SRK) set." but I'm struggling to understand why this error only effects some new machines and not others even though they are all the same model and spec. We have a workaround which seems to be working every single time which is to turn on a new machine and let it run through OOBE of the shipped W10 OS then once completed, reboot the machine and PXE boot to the W10 Task Sequence. So something during the OOBE of a brand new machine seems to be creating/setting the SRK for the very first time. Does anyone have any ideas as to what might be causing this and how/when a TPM SRK is initially created? Thanks in advance, Westy
-
- windows 10
- 1703
-
(and 3 more)
Tagged with:
-
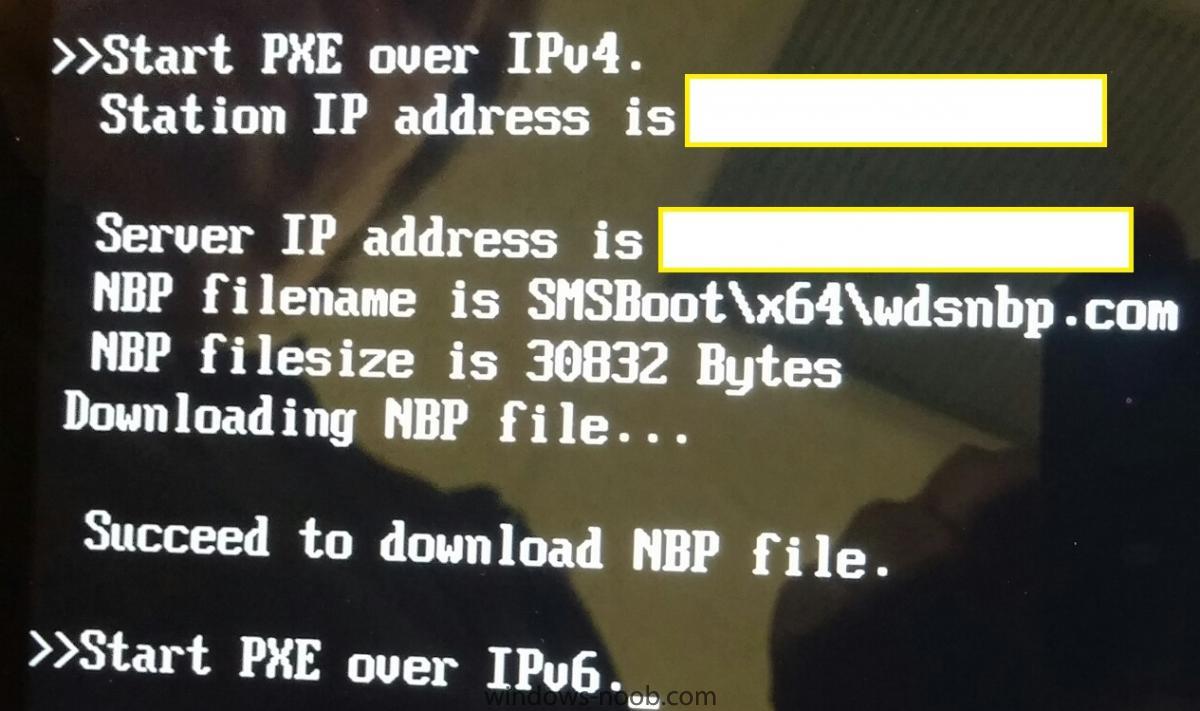
Hello, I am trying to PXE boot surface pro 4 and for some reason it does not boot. I get the attached message. It tries to PXE over IP v4, then reaches my correct DP that has PXE and WDS, it finds the correct NBP file SMSBoot\x64\wdsnbp.com (this is specified in DHCP option), it appears to be downloading and NBP file is successfully downloaded. Then without prompting to press Enter key for PXE boot, it moves to IPV6. I have tried below but no luck Upgrade firmware to latest disable secure boot Removed DHCP option - but this time it doesn't even finds my PXE server Verified and made sure MAC address of network adapter is not registered with SCCM DB Tried docking station and no luck I can PXE boot a desktop on same network with no issues. Any suggestions would be helpful Thanks.
- 29 replies
-
- Surface
- Surface pro
-
(and 5 more)
Tagged with:
-
Hello, I'm currently using a wsus server on my domain. It is used with SCCM 2012 R2 (as per the sccm 2012 installation documentation to use SCCM to deploy updates). On a machine running Windows 10 enterprise, I'm trying to get some language pack installed. Problem is, it's checking the WSUS server and it's saying that no language pack are available. I launch the admin console and downloaded all language pack and deployed them as available to my workstation. Still no language pack available. I got the same problem if I try to add a feature, it want to download something from Microsoft Update but since I have a WSUS server set, it doesn't work. For now, I delete the policies key that set the wsus and do it online, but I'd like to fix this. What do I need to do on my WSUS/SCCM to be able to download language pack and others from my local wsus? Thank you
- 2 replies
-
- Windows 10
- SCCM
-
(and 2 more)
Tagged with:
-
As someone who is installing his first SCCM solution, I hope this is something easy. I believe that SCCM is deleting kodak scanner drivers from our Windows 10 LTSB 2016 clients, however I don't believe I have any drivers set to update within SCCM. I currently have our Windows 10 ADR set to run on the 2nd Friday of each month and SCEP / Defender updates running each morning @ 1:00am. (Users report seeing the Config Manager Taskbar notification on occasion throughout the month though) When looking at the Driver events all clients seem to lose their Kodak i2xxx scanner driver between 10:30am and 10:50am Finally, when I disabled my ADR's for a few days the drivers were not deleted during that time. Current Site settings: Current Windows 10 Automatic Deployment Rule Settings:
- 2 replies
-
- adr
- windows 10
-
(and 1 more)
Tagged with:
-
I deployed the latest March Update for Office 365 to one Test Machine and it was marked as compliant even though it hasn't installed the update and is still on the old Office 365. I have checked the logs, nothing there. I went through the logs mentioned here https://technet.microsoft.com/en-gb/library/bb693878.aspx Can you someone please point me in the right direction of troubleshooting? Thank you
-
Hi guys, Trying to deploy Windows 10 Fall Creators Update 1709 using SCCM 1606. Everything works fine until a restart step and it gets stuck on a black screen until you press a key or tap the mouse pad and then it carries on to the next step. Deploying to Surface Pro 4s SCCM 1606 Simple TS - Install OS from WIM, join domain, install few apps, and that's it. https://i.imgur.com/BuGSczP.png https://i.imgur.com/EQYmeYW.png It happens to every restart i have in the TS. Can someone please assist me? Thank you
- 3 replies
-
- 1709
- windows 10
-
(and 2 more)
Tagged with:
-
Hello, We are planning a Win10 migration in the next few months, we have about 1300 endpoints. The management team wants to split the migration on 2 weenkends. Here is our SCCM infrastructure Architecure : 1 Site server \MP 7 DPs with SMP role (one for each location on different timezones) 1 SUP server. My question is, would you think that we should scale up our architecture? what changes you may want to make to adjust to the migration? Thanks,
- 2 replies
-
- osd
- windows 10
-
(and 2 more)
Tagged with:
-
Dear Experts, I Would like to get some inputs from you Please. My Data Center is located in 2 Regions. This data center is supplying the services (Windows Server, Network., etc) At Present we are planning to perform SCCM CB Implementation with High Availability for SCCM Client Roles. In fact not for SQL (Due to Commercial items) Single Standalone Primary Site is fair enough for the environment. However, We would like to reduce the usage of SQL Server, and make the Client facing roles with HA. Hence your inputs would be helpful for us Data Center Region A: Server 1 - SCCM Site Server - A Primary Site with Roles (Component Server, Site Server, Site System, Reporting Service Point, Other Non Client Facing Roles) Server 2 - SCCM Site System - Client Facing Roles (Management Point, Software Update Point/WSUS, Distribution Point (With WDS/PXE OSD Capabilties) Data Center Region B: Server 3 - SCCM Site System - Client Facing Roles (Management Point, Software Update Point/WSUS, Distribution Point (WithOut WDS/PXE OSD Capabilties) So all Client facing role, will be working with HA Option. However, PXE Boot for OSD will work only with SERVER 2 from WDS (Which respond to the Client during the OS Imaging) - To make this happen I need to mention the IP Details of WDS Server (Server 2 from Region A) in the DHCP Scope. Am I correct? The reason, I do not preferred to give the SERVER 3 (From Region B)as WDS Role with PXE, which we do not need to give the multiple entries with DHCP Scope (Option 66, 67) for OSD Please suggest, if this is looks good for an organization. The Ultimate goal is to reduce the SQL CPU Utilization.
- 8 replies
-
- sccm
- current branch
-
(and 8 more)
Tagged with:
-
Hi Everybody, We are working on a new image with Windows 10 1703 en-US, but now we have a customer who wants the nl-NL languagepack to be installed. What I have done: - Created an unattended.xml with settings <InputLocale>0413:00020409</InputLocale> <SystemLocale>nl-NL</SystemLocale> <UILanguage>nl-NL</UILanguage> <UserLocale>nl-NL</UserLocale> <UILanguageFallback>en-US</UILanguageFallback> - Created a package for the languagepack - Created a MDT task sequence step to install the offline languagepack Started the deployment, languagepack seems to be installed alright, but when the machine boots up, only the date/time are in Dutch. So the display-language is still in English. After that I installed the Dutch languagepack via lpksetup.exe, rebooted the machine and now everything is in Dutch. It seems that Windows 10 is trying to contact Windows Update to search for the display language packages, but Windows Update is blocked, because everything is going via SCCM. Any advice is very welcome on how to install this on the right way.
- 7 replies
-
- windows 10
- 1703
-
(and 1 more)
Tagged with:
-
Dear Experts, Very Shortly - I will be having SCCM CB in my environment. I would like to get an advice/inputs from you to perform the Windows 10 Deployment Scenario's. Would like to get an advice, what are the topics - I should cover for Windows 10 Readiness with SCCM CB Environment My Organization preferred to perform the Management in the same way which I am doing for Windows 7. However, I would like to give some value added proposal's Any recommendations from you Experts?
-
Dear Experts, I would like to get an advice from you Please. You may see multiple forums from me – As my Environment is bit complicated. Environment implemented by 3rd party and handover to us as part of transformation – Which we are struggling to upgrade or proceed further. Current Infrastructure: SCCM 2012 SP2 with Windows 7 Clients (Managing – Application, Patch, Operating System Deployment) This is running on Windows Server 2008 with SQL 2008 Required Infrastructure: It is required to Manage Windows 10 Clients, Windows 7 Operating System (Application, Patch, OS Deployment) After being and hearing more responses from our Engineer’s/Experts. It is planned to progress the Green Field Implementation 1. Windows Server 2016 2. SQL Server 2014 or SQL Server 2016 3. Windows 10 ADK with Version ADK 1709 - 10.1.16299 4. System Center Configuration Manager V1710 New Implementation along with Distribution Point 5. Making the Environment with Complete Readiness for all Application Source, OSD Task Sequences, Software Updates., etc., This New Infra will be completely ready with supporting all contents. IP Assignment: We are already having the Boundary Groups, which is based on the IP Range with Region wise in the OLD Environment. New Environment – Client Movement from Old Infrastructure: Let us consider we have the IP Range called 192.168.1.1 to 192.168.1.254 is active and supplying the service with Windows 7 Client OS on Old Infrastructure (SCCM 2012 SP2) Now, the New Infrastructure is ready with all sources (SCCM CB V1710) – If the Client IP Range, Boundary Settings for Site assignment is getting moved from Old Infra to New Infra By Using Automatic Site Client Push Installation 1. SCCM Agent Will get install/upgrade with Version CBV1710 2. Since the IP Range, Boundary Group is allocated with New Environment All the Deployments will get started to run on new Environment. By performing this activity 1. All Windows 7 Clients will be running with SCCM CBV1710 Agent Version 2. All Windows 7 Clients will be reporting to SCCM CBV1710 Infrastructure 3. Slowly, I can prepare myself for Windows 10 Upgrade Projects. Hence, it is require to have 2 Environments in the Same System Management Container (SCCM 2012 SP2, and SCCM CB V1710). If I hold the 2 Environment with Different Site code and host name, Will that be Okay.. Please Advice!! My Sincere apologize to have separate post. Earlier was discussed for the Migration (With in the same server)., but now we preferred to install the SCCM CB V1710 Infra with new server *Windows 2016 & SQL 2016 * and move all the Clients to the new Infrastructure.
-
- system management container
- sccm cb
- (and 7 more)