Search the Community
Showing results for tags 'Workgroup'.
-
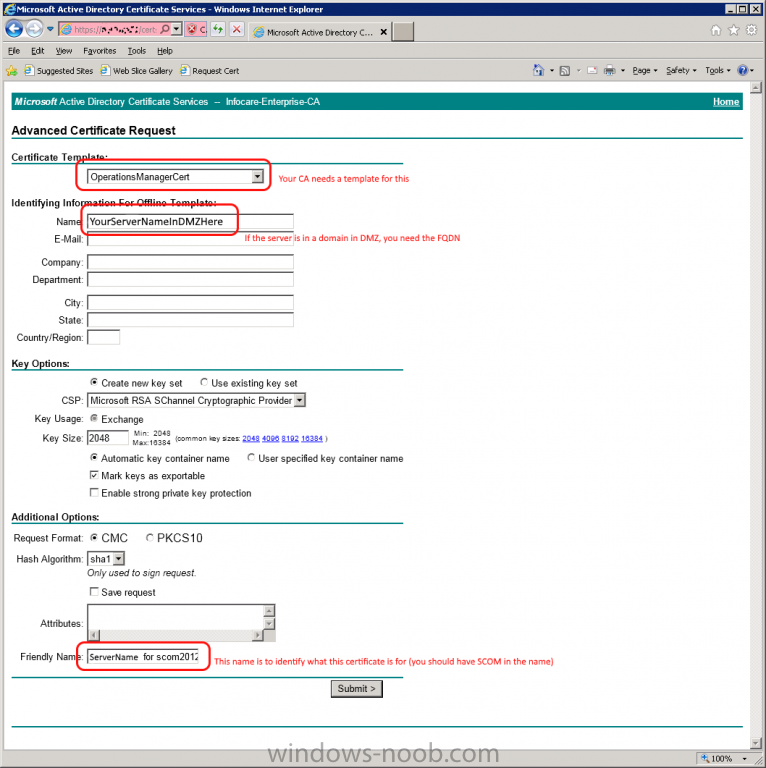
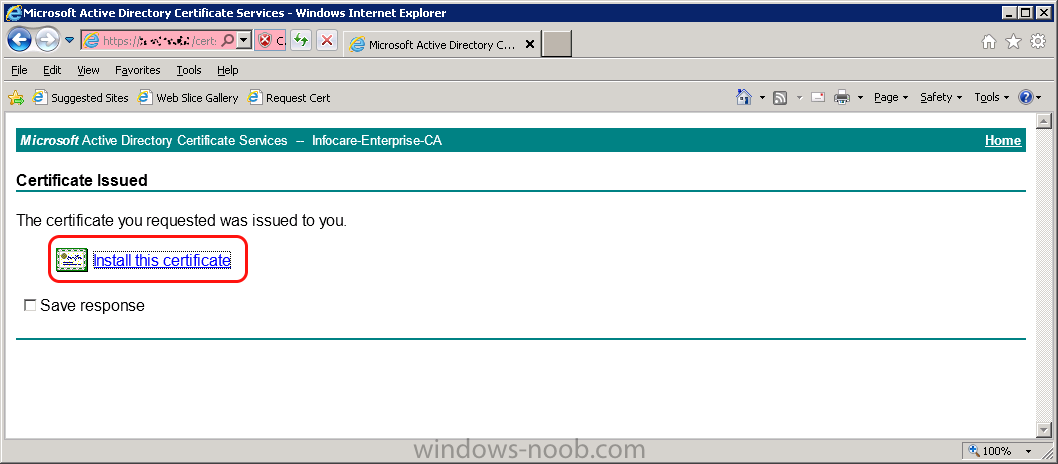
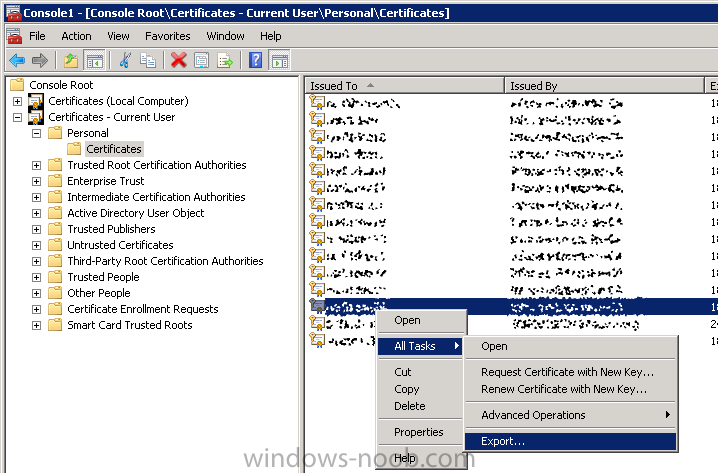
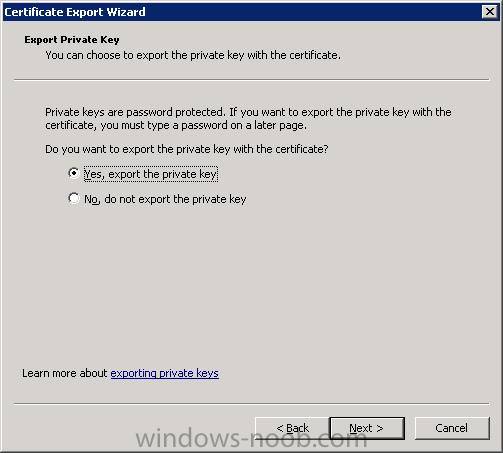
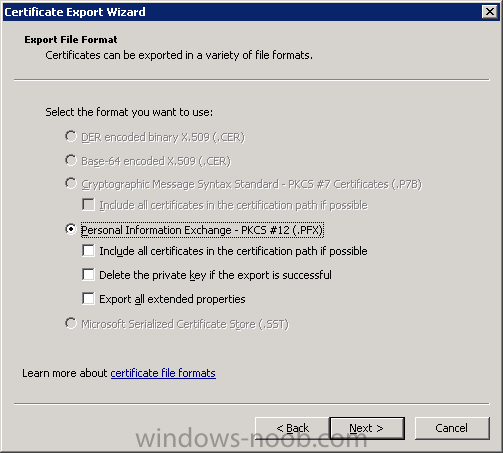
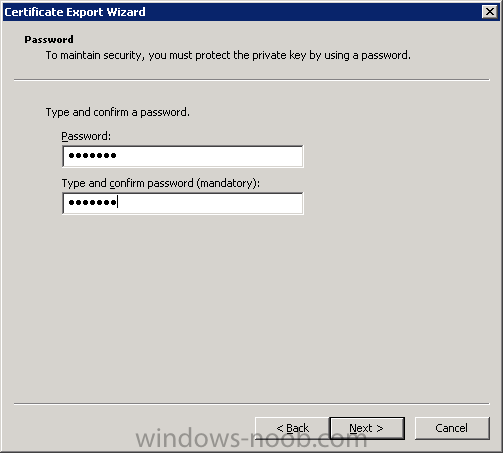
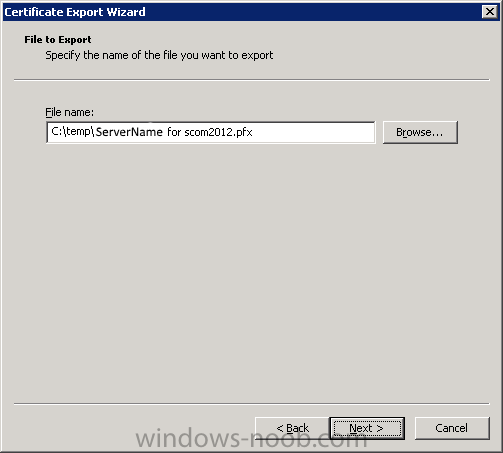
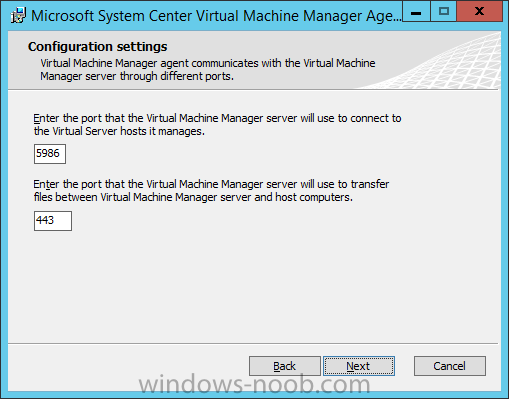
Same procedure for a gateway server in DMZ 1.1 - Generating the certificate RDP to your Operations Manager (it's a good idea to have all the certificates at one server) Start Internet Explorer and navigate to: https://yourCAserver/certsrv If the server in DMZ is in a do...
-
- SCOM
- Operations
-
(and 5 more)
Tagged with:
-
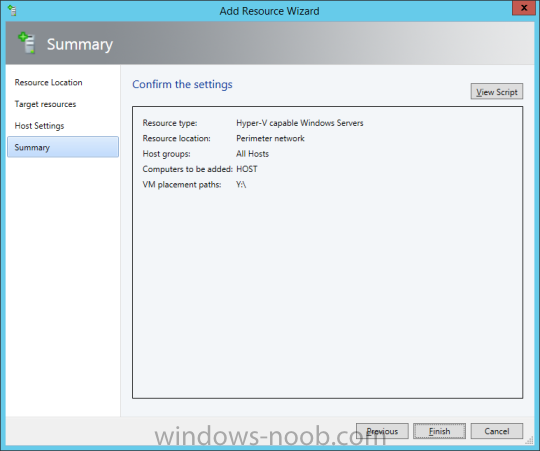
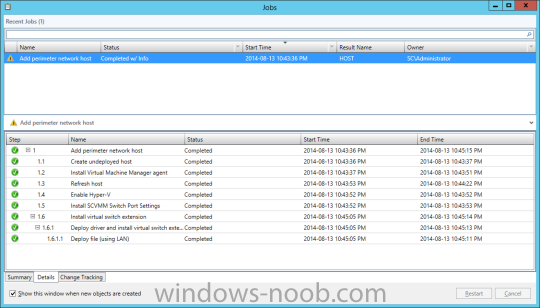
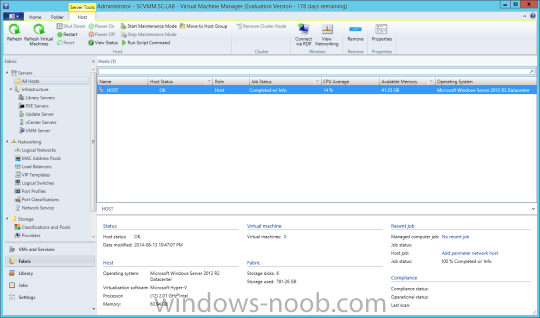
In my home lab environment, I have a single host, which is NOT a member of my lab’s domain. This is due to the fact that I am constantly re-building my lab environment, which includes my Active Directory Domain Controllers. Therefore, I don’t want to add my host to the domain, and then potentially l...
-
- Hyper-V Host
- SCVMM
-
(and 1 more)
Tagged with:
-
When I try to deploy windows 8 updates follow Anyweb's guide SCCM 2012 RC Part 6 - Deploying Software Updates, Step Install Software Updates failed with 0X800705B4 while system join workgroup instead of domain. If I config system to join domain everything is fine. I have specified SMSMP=CM01.cor...
- 2 replies
-
- 0x800705b4
- sccm 2012
-
(and 4 more)
Tagged with:
-
Sysprep issues; Workgroup and Original Computer Name
mt204 posted a question in Windows Deployment Services (WDS)
Couple of issues that I can't quite remember when dealing with sysprep. 1) I have a couple images that aren't to be joined to our domain, yet when I set <JoinWorkgroup>WORKGROUP</JoinWorkgroup> in sysprep.xml AND in WDS I select "Do not join the client to a domain after an installation", it stil...