Search the Community
Showing results for tags 'bitlocker'.
-
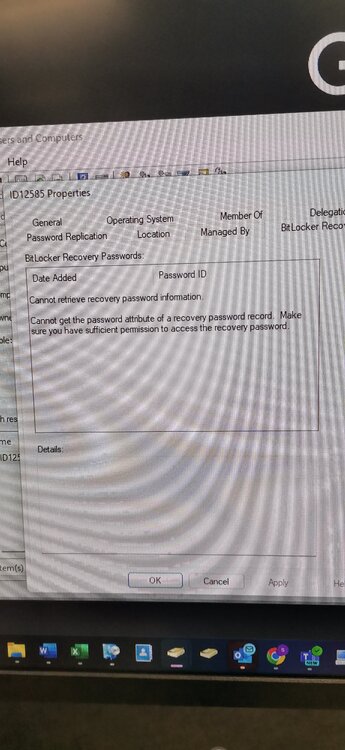
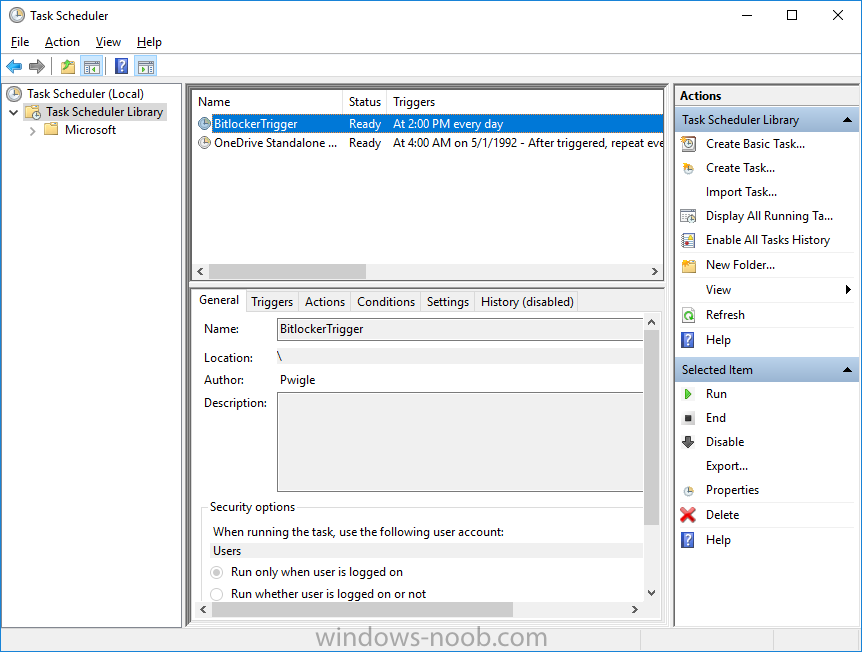
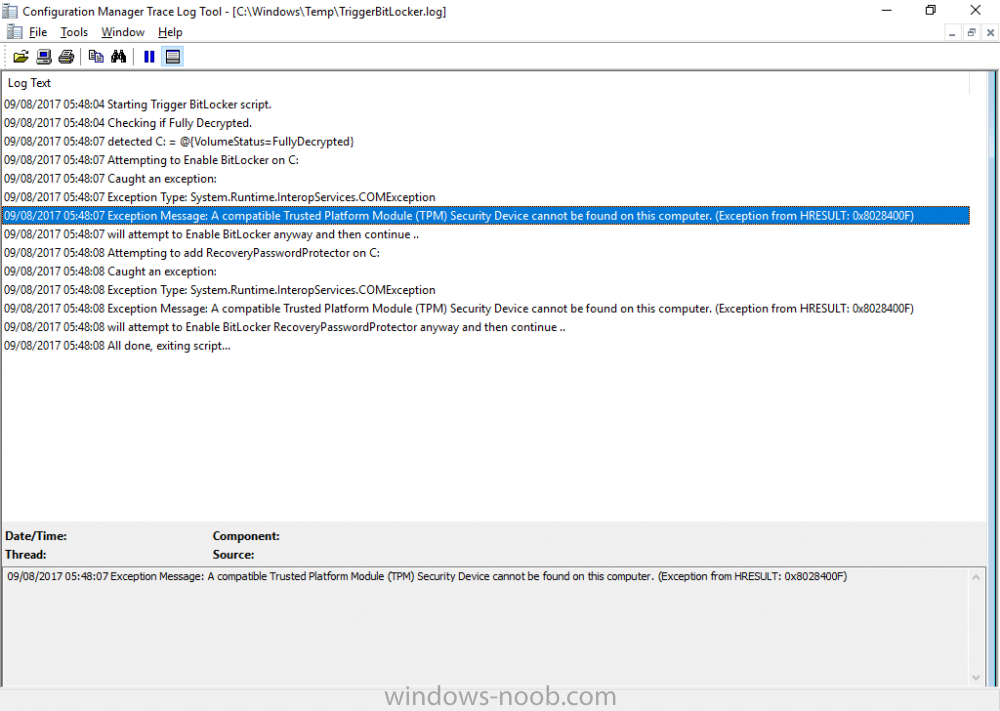
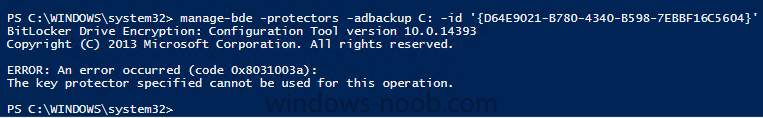
Bitlocker issue:- Task Sequence tries to escrow the key to AD it can't read it from registry. After deploying bitlocker i can see Bitlocker Recovery Tab on AD under the relevant PC im using for testing but there are no recovery keys and gives this message as per screenshot.
- 2 replies
-
- bitlocker
- recovery key
-
(and 4 more)
Tagged with:
-
We use SCCM to enable/configure BitLocker on Windows 10 computers. The BitLocker PIN must follow our password policy for changing the password every 60 days. We don't see that as a selection when configuring the policy. Can this be done?
- 3 replies
-
- sccm 2103
- bitlocker encryption
-
(and 1 more)
Tagged with:
-
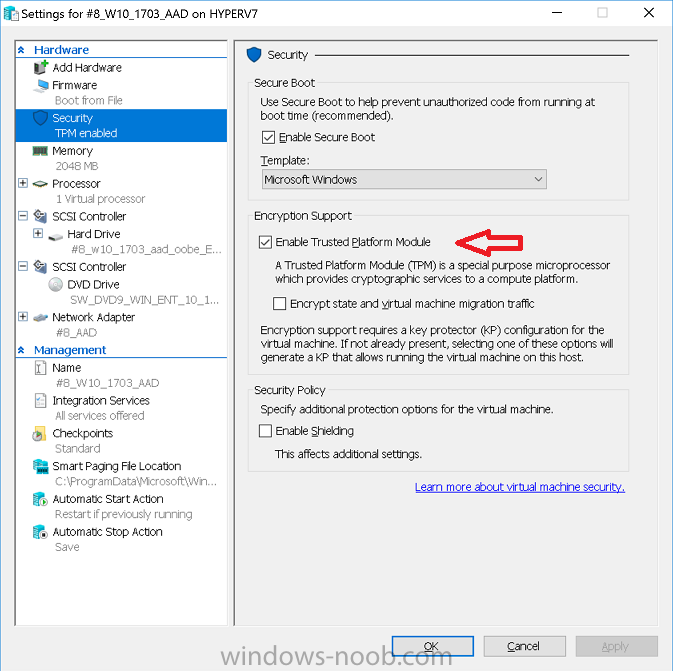
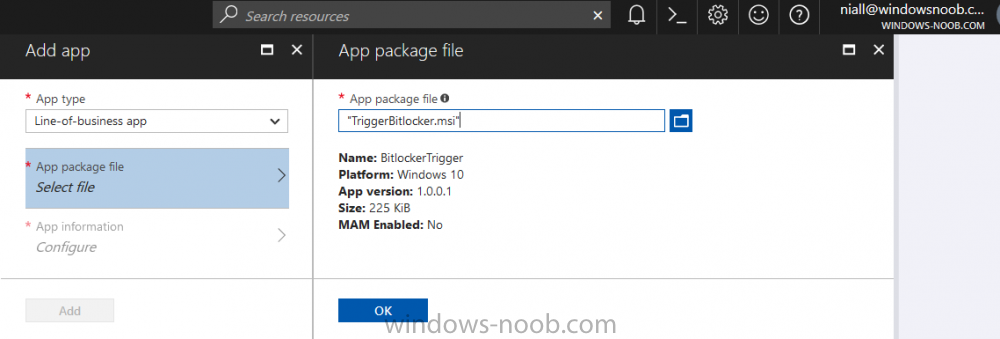
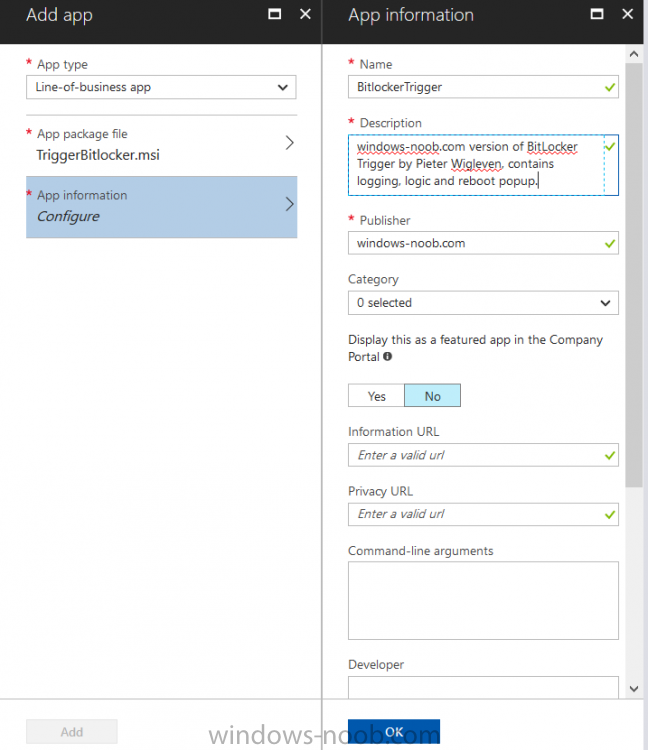
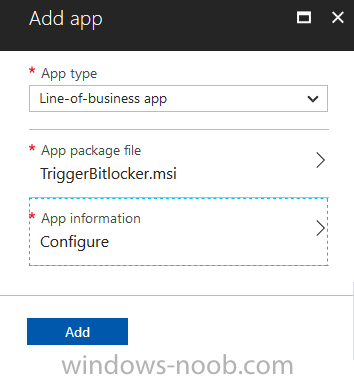
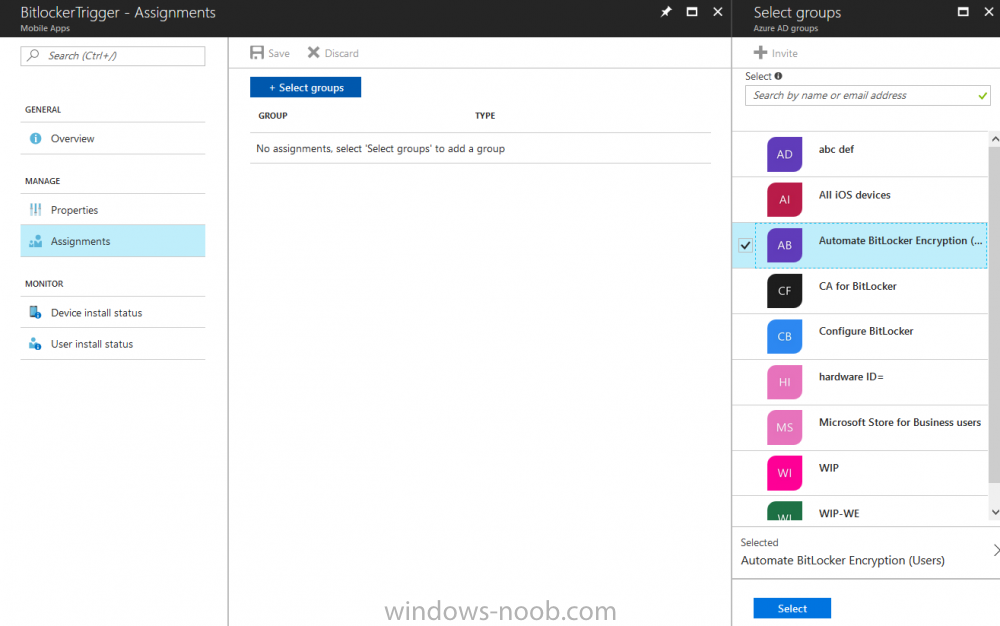
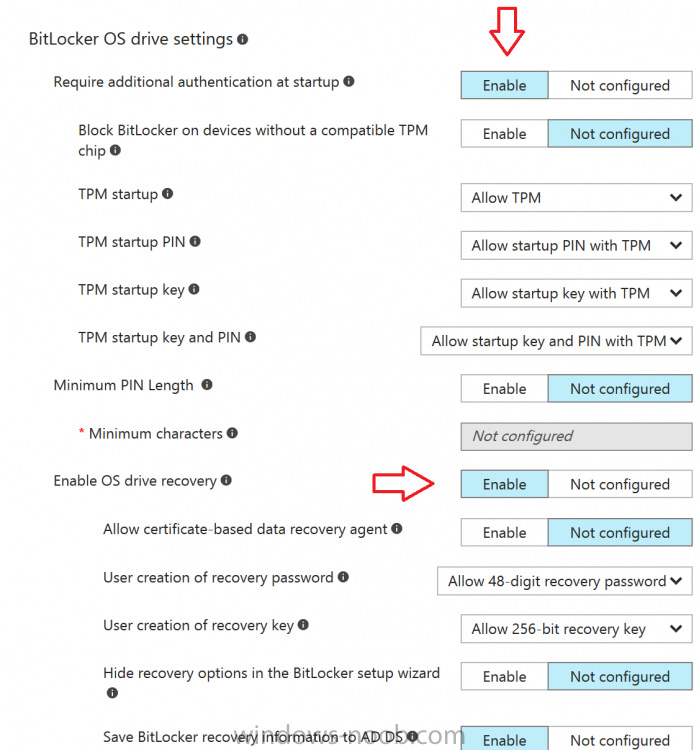
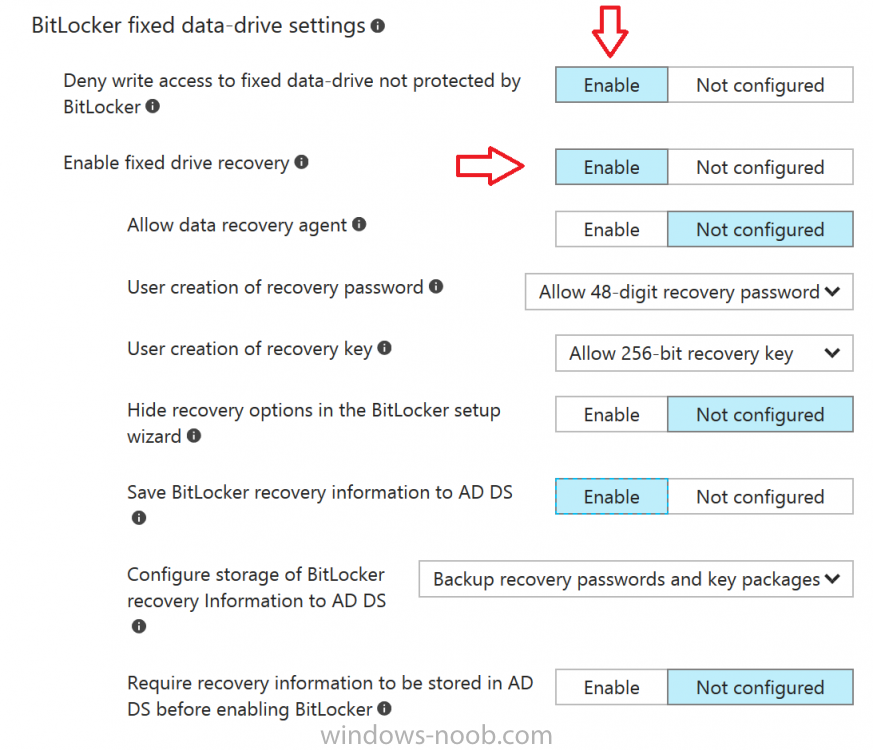
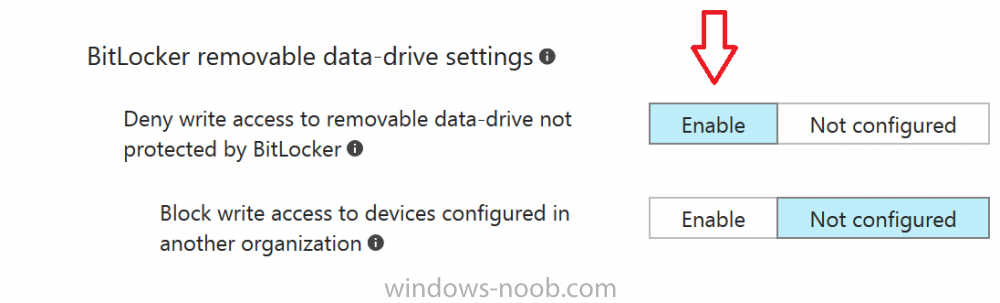
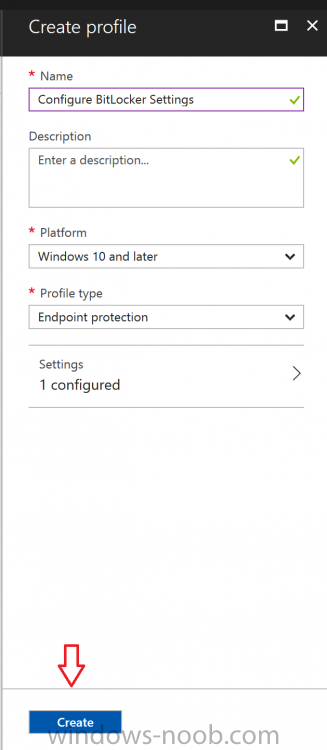
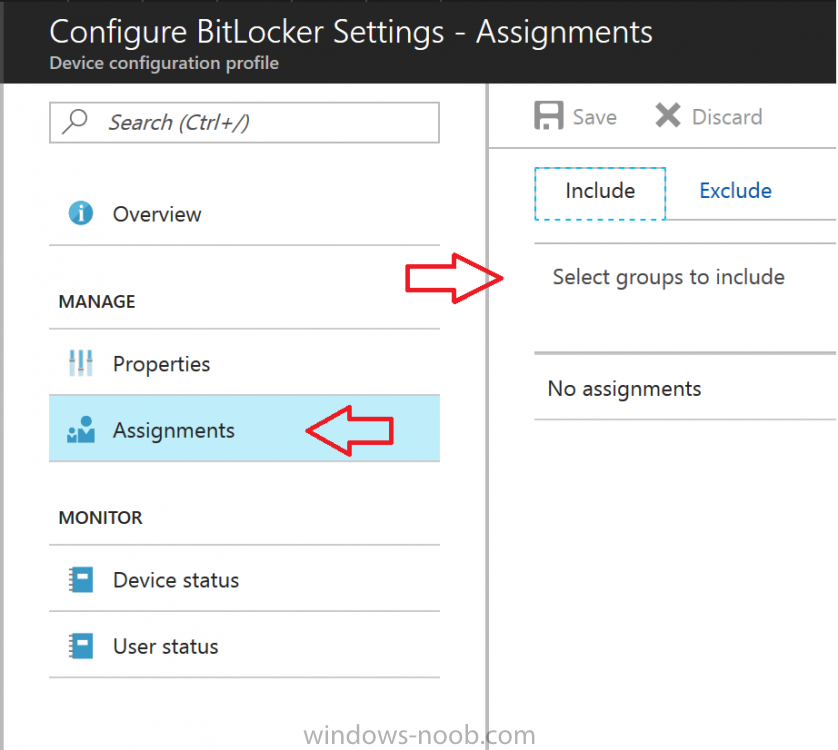
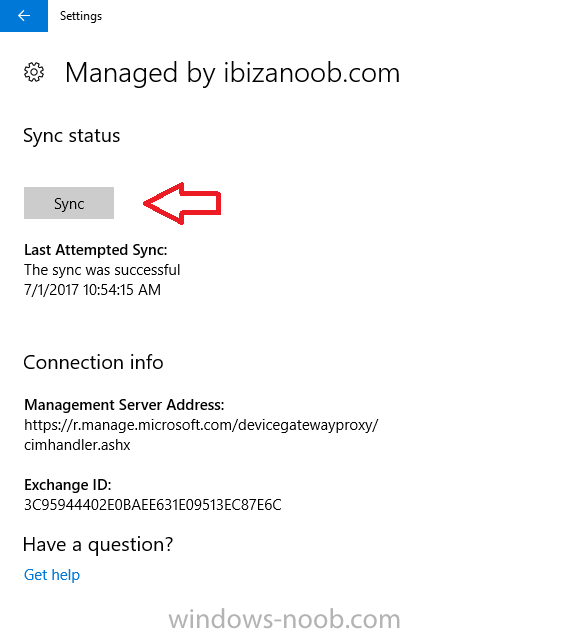
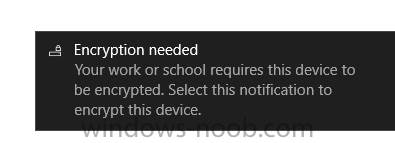
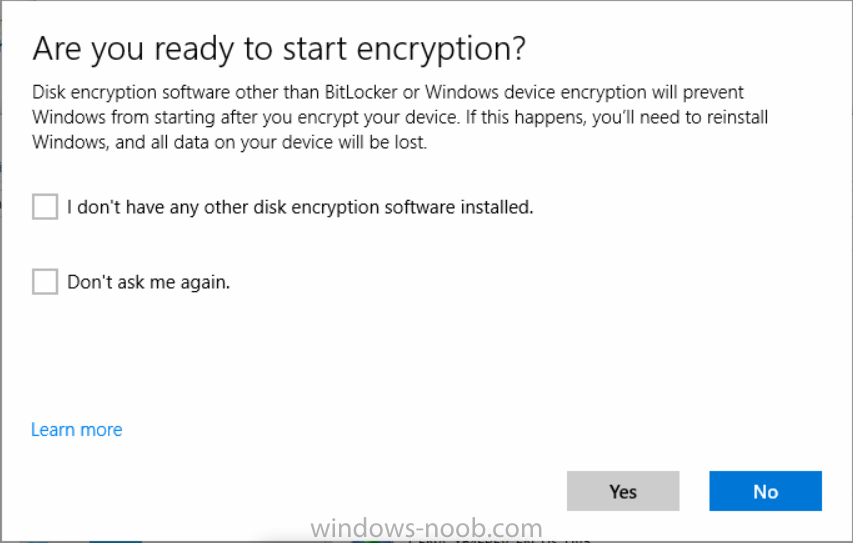
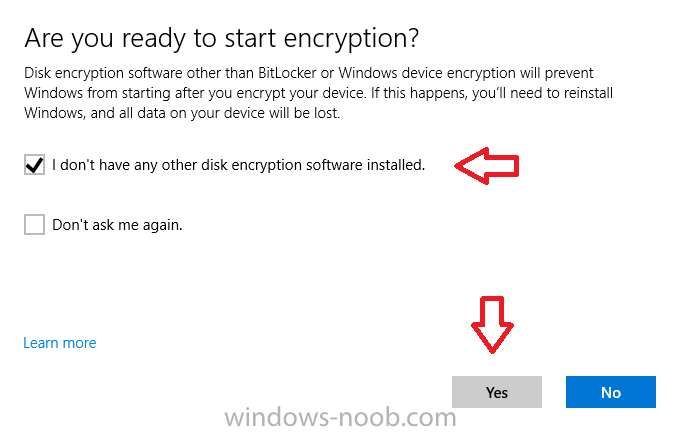
Introduction In Part 1 I showed you how you can configure BitLocker on Windows 10 devices using Microsoft Intune, but that method relies on the end user actually clicking on the notification in Windows and then continuing through the wizard until completion. In this post I'll show you how...
-
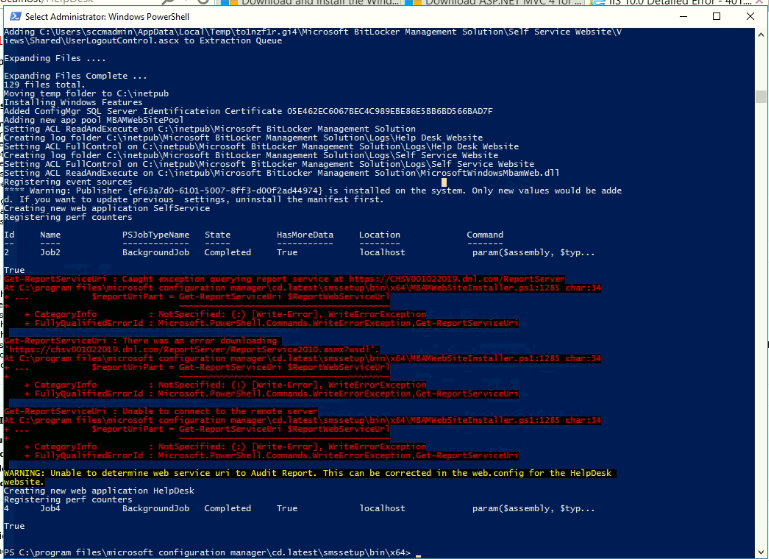
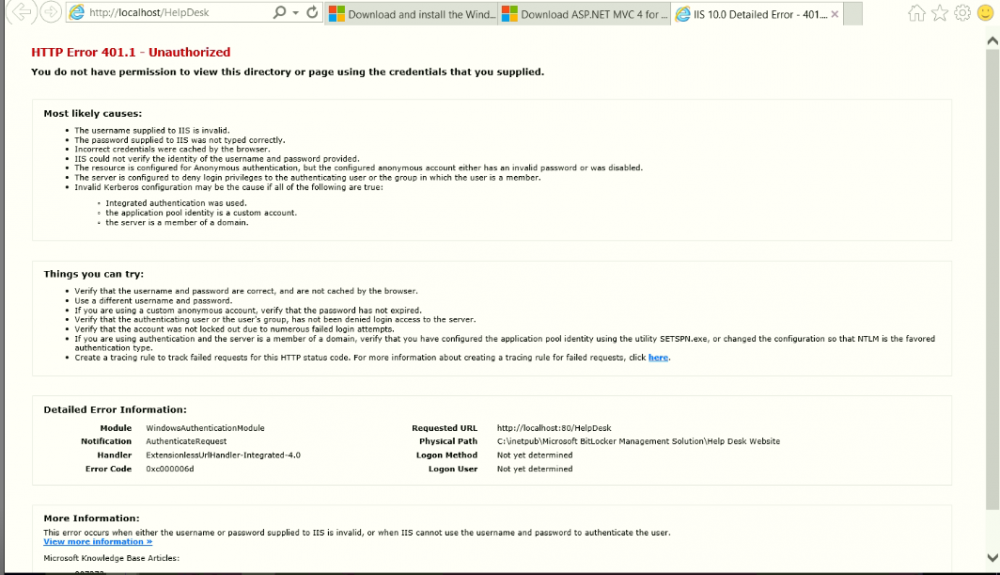
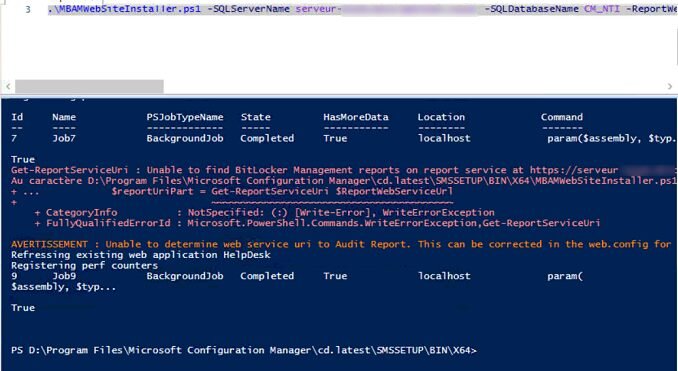
I run the script for creating a BitLocker portals. , I tried to access the portal but cannot connect it keeps prompting for the credential.
- 23 replies
-
Does anyone know of a way to create a report that shows a list of Windows 10 Pro devices that are configured with BitLocker from Intune? Since they are using Pro Edition, Endpoint Protection Policies don't work so I am using the default Windows Device Restriction Policy that includes device encrypti...
-
Hi All, We are experiencing a weird issue with BitLocker when re-installing existing Windows 10 1709 machines with Windows 10 1903. The machines are hybrid AD joined and the BitLocker recovery information is stored in Active Directory. During a new installation of the device with Windows 10 190...
-
- bitlocker
- windows 10
-
(and 3 more)
Tagged with:
-
Hi There, Anyone here has hands-on experience on implement Bit-Locker To-Go? In my environment we use SCCM CB-1902 and MBAM server & client. We have single drive in all the client and it has been protected using MBAM agent. Now looking for encryption the removal disc \USB automatically, when i...
-
- bitlocker
- bitlocker encryption
-
(and 4 more)
Tagged with:
-
Customer has upgraded to Config-Mgr 1910 and now would like to use BitLocker management. however currently encryption is happening via McAfee and would like to migrate from McAfee to Bitlocker. anyone has run into this scenario as of now? Windows 7 devices needs Wipe and load to use Bitlocker featur...
-
HI On a Windows 10 OSD TS, i want ot add the Bitlocker recover Key to Azure for Hybrid Joined devices. How can i achive this from an SCCM TS? Thanks
-
- hybrid azuread join
- task sequence
-
(and 3 more)
Tagged with:
-
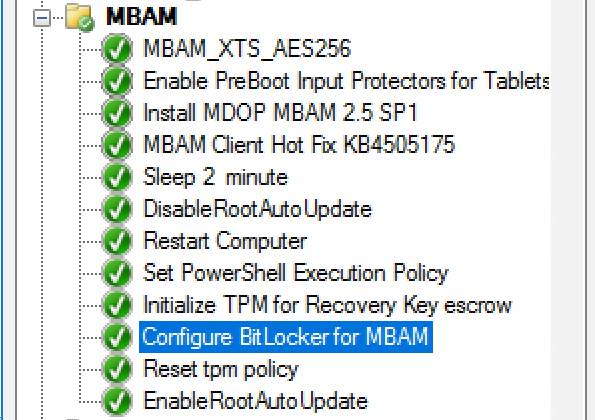
InvokeMbamClientDeployment.ps1 return error 1
Takechico posted a topic in Configuration Manager 2012
Please guys, I need a help, cuz I become a mad. I have spent a lot of time for this problem, and can't solve it. I'm trying to deploy MBAM client 2.5 SP1 (September update) on Windows 10 1803 with storing recovery keys on MBAM server via SCCM2012 r2 task sequence. I have deployed MBAM server at o...-
- sccm2012r2
- bitlocker
-
(and 1 more)
Tagged with:
-
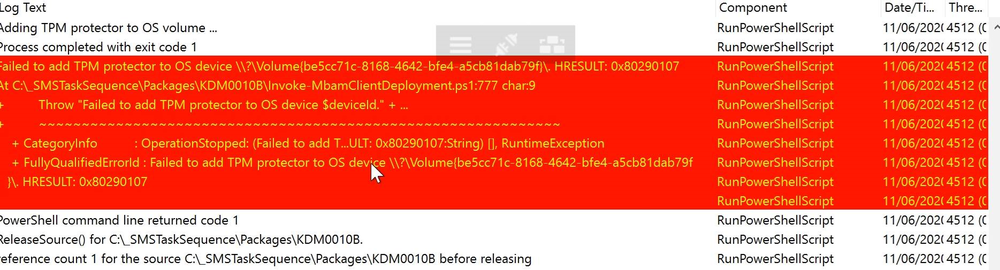
Hi all, I'm hoping that someone can help as I'm really struggling to find anyone else that's had this specific problem. When trying to build brand new HP equipment with an SCCM (MDT integrated) OSD task sequence I am seeing the following error when the machine runs the "Invoke-MbamClientDe...
-
- windows 10
- 1703
-
(and 3 more)
Tagged with:
-
Bitlocker to AD
Nemanja Jovic posted a topic in System Center Configuration Manager (Current Branch)
Hello everyone, I have the client that wants to do something specific with bitlocker and its pins, but that is beyond of this topic. Issues is: When you create a step in task sequence to set up the bitlocker, if you choose TPM and PIN, you will be able to backup the recovery key into Activ... -
Hi, We're looking at a wipe and reload on all of our machines because we're changing our encryption from Checkpoint to BitLocker as we move from Windows 7 to Windows 10. However, I'm wondering if it's possible to use hardlinks for USMT since we do have the Checkpoint filter driver as part of ou...
-
Are you planning to deploy Microsoft Intune and looking for straightforward technical guidance to help you accelerate this effort? Please join us as we share our deployment experience working with customers from all over the world, covering Intune pilot planning, deployment and management. At the en...
-
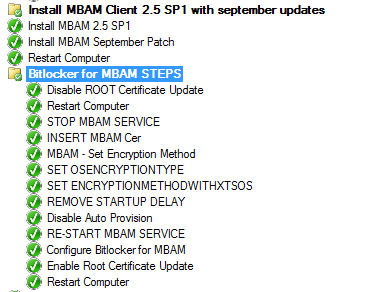
actually i made a task sequence for MBAM to encrypt all drives - it starts only, when i´m login to Windows 10, but i need it while the tasksequence is running, before starting installing Office 365 and so on. Have anyone experience for this step? the mbam-client config (last step) set the regis...
-
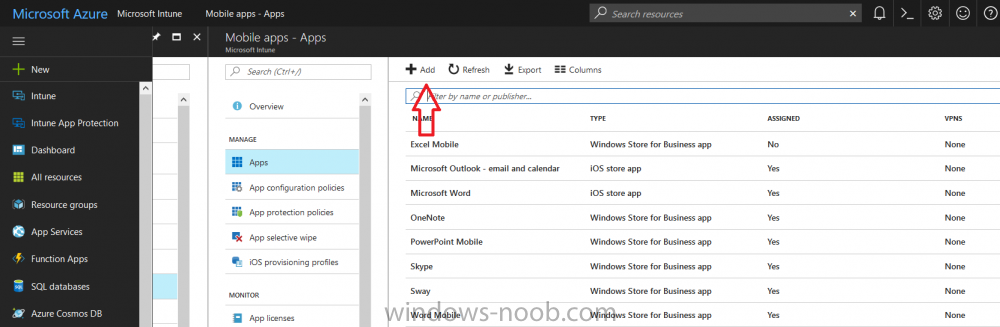
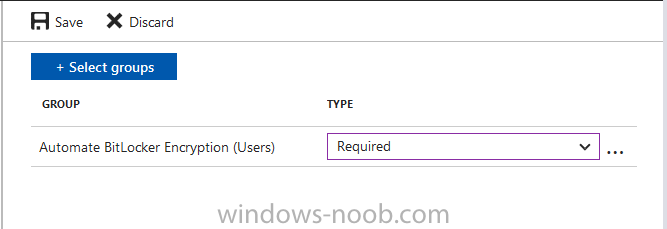
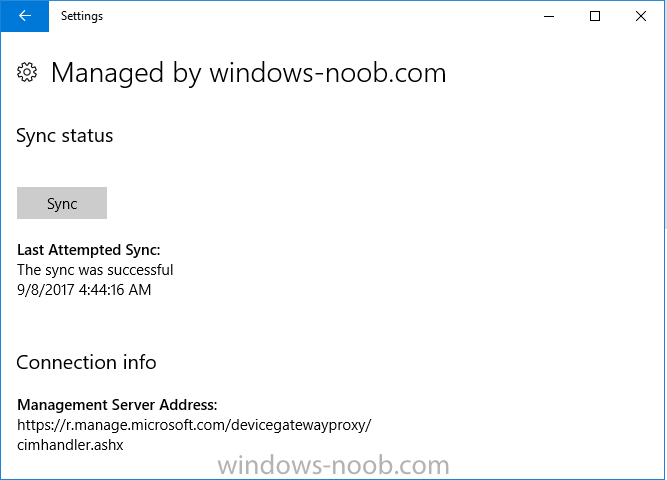
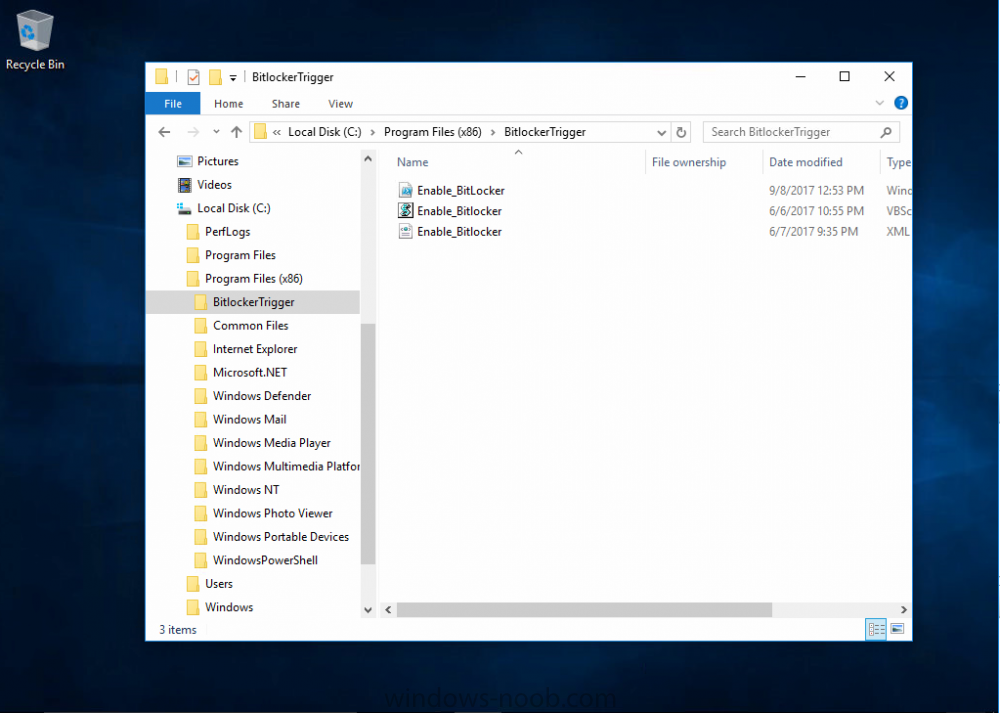
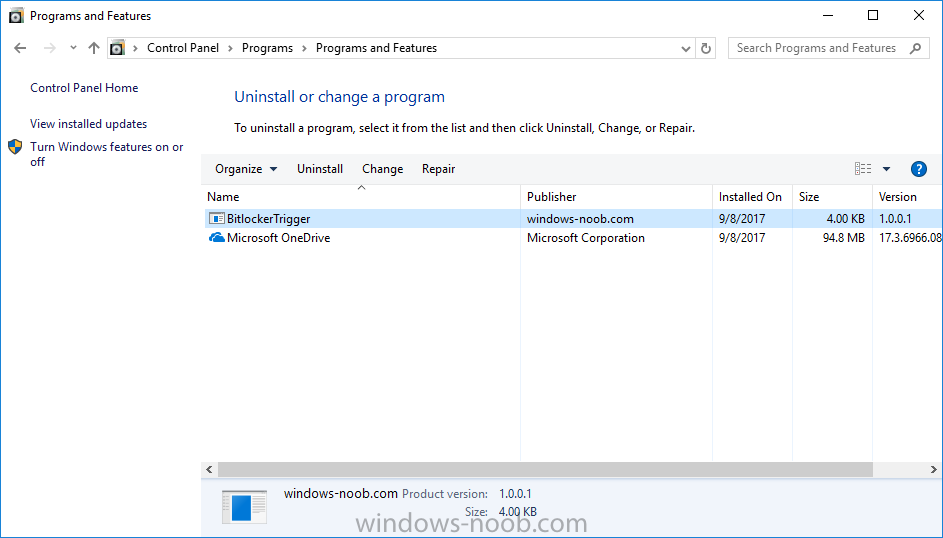
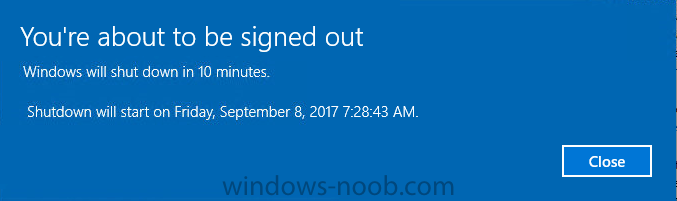
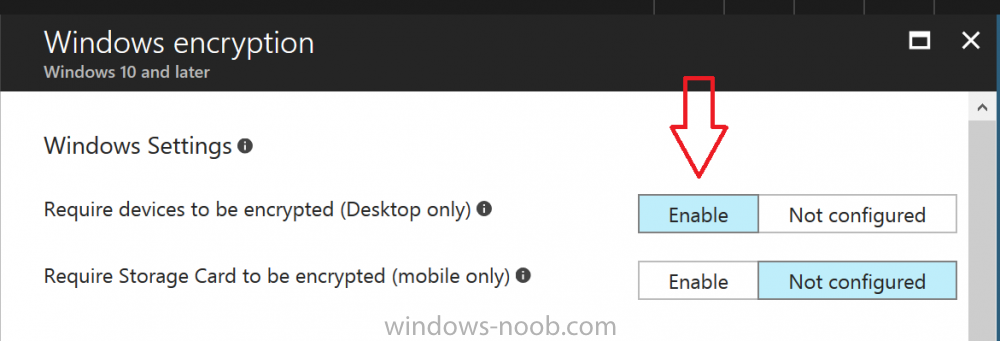
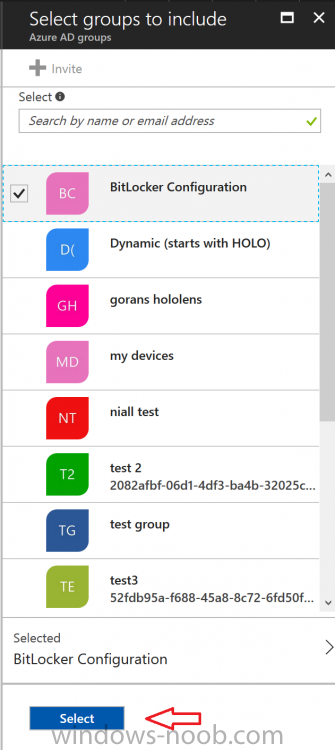
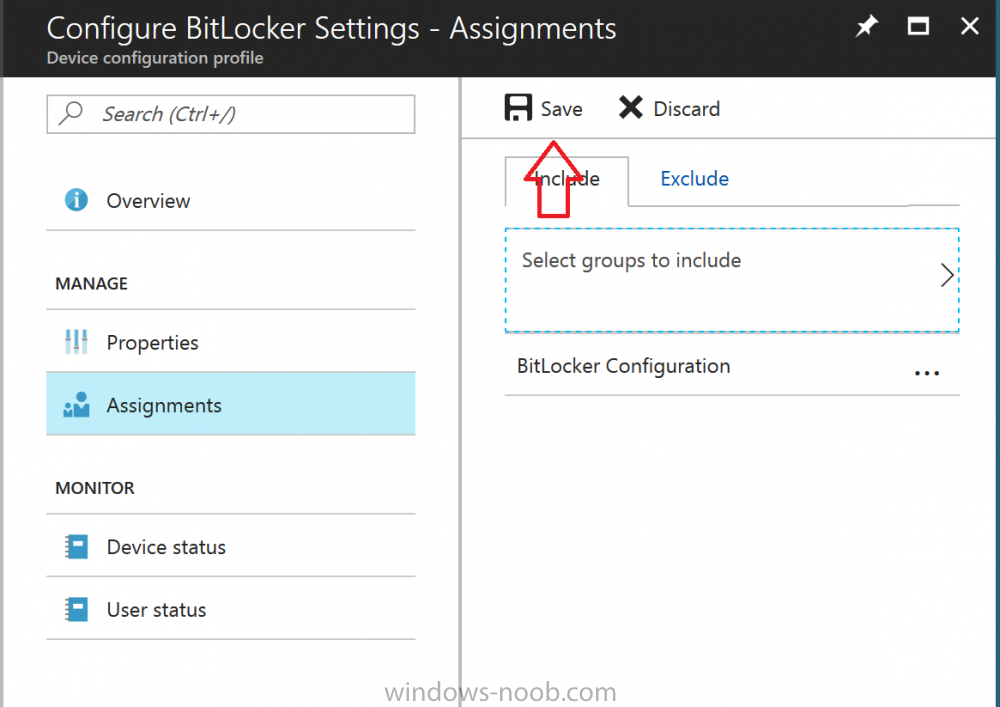
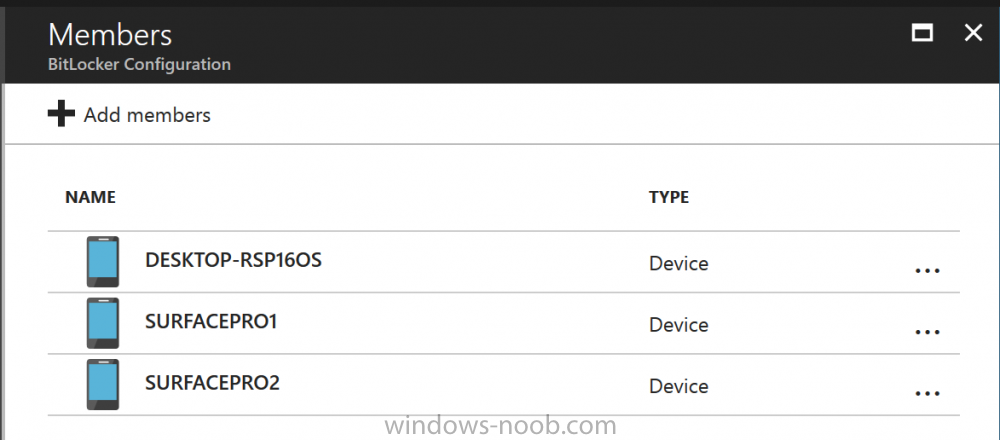
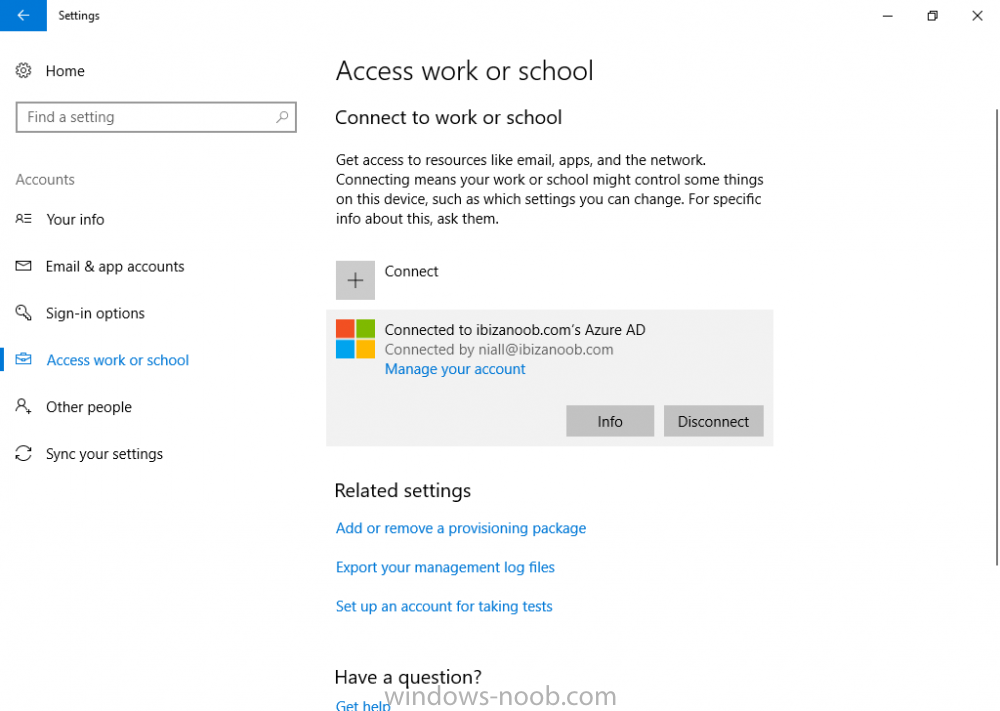
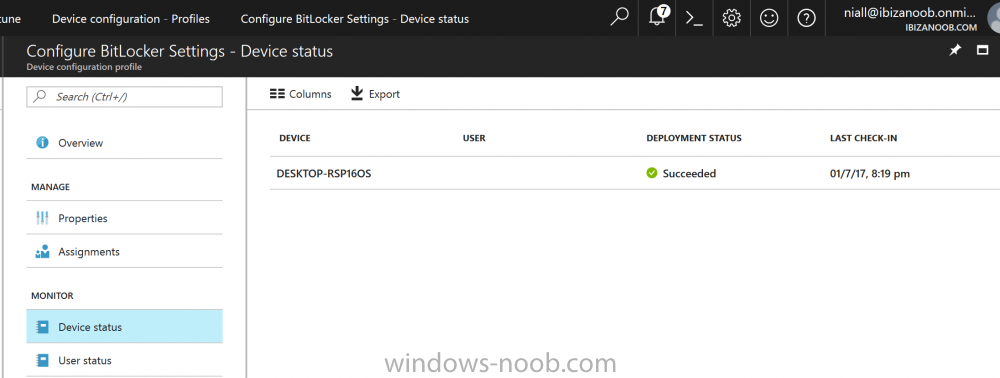
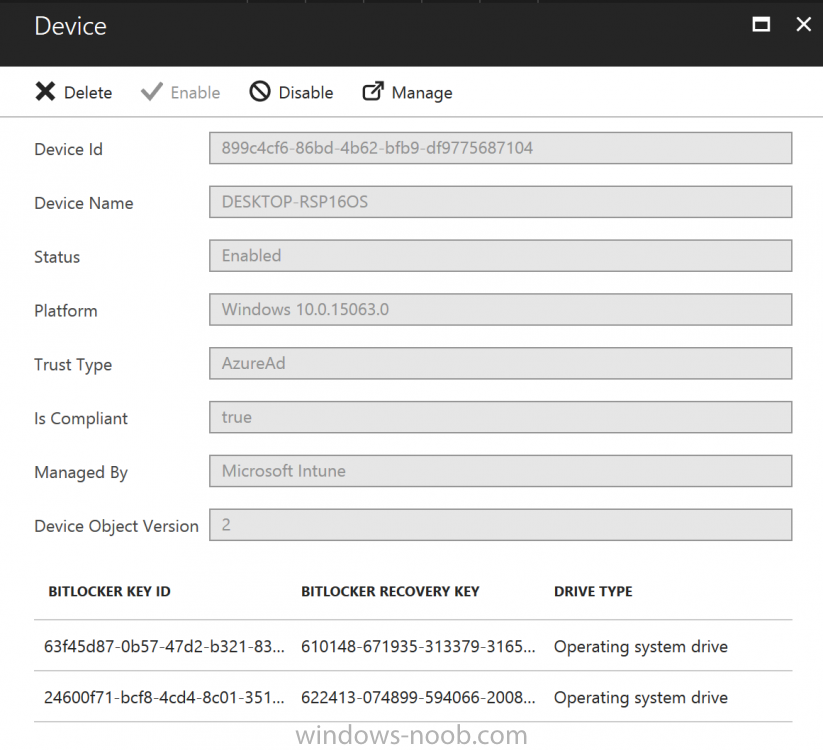
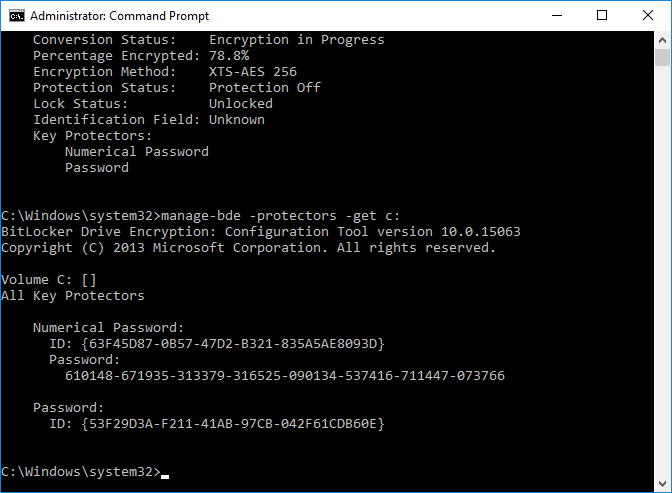
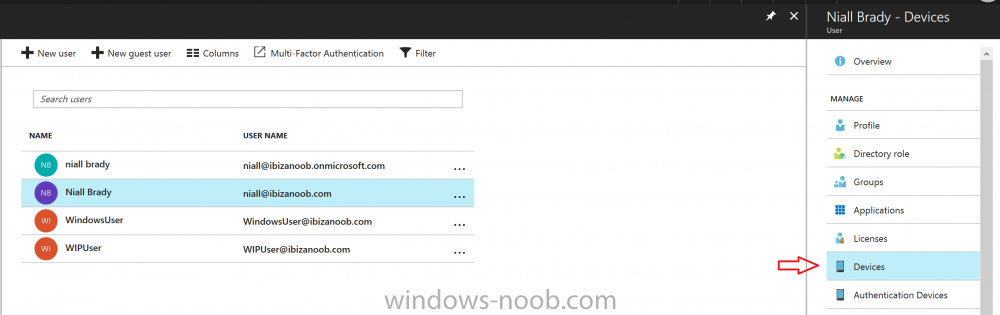
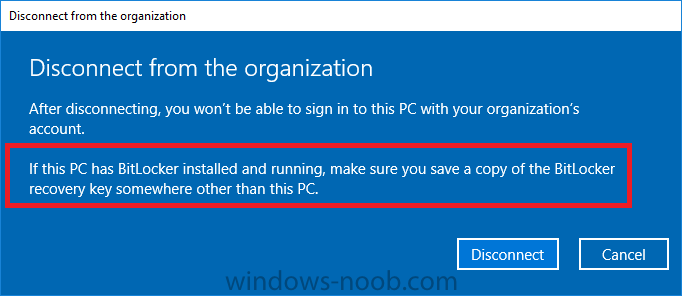
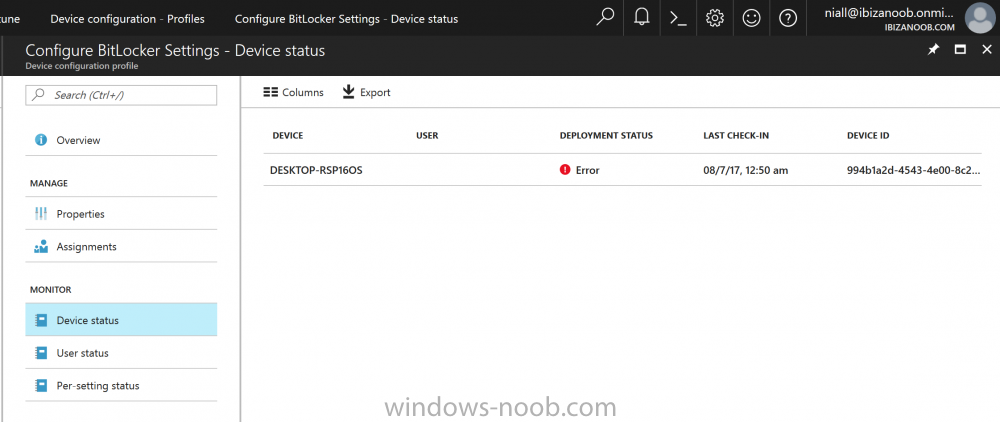
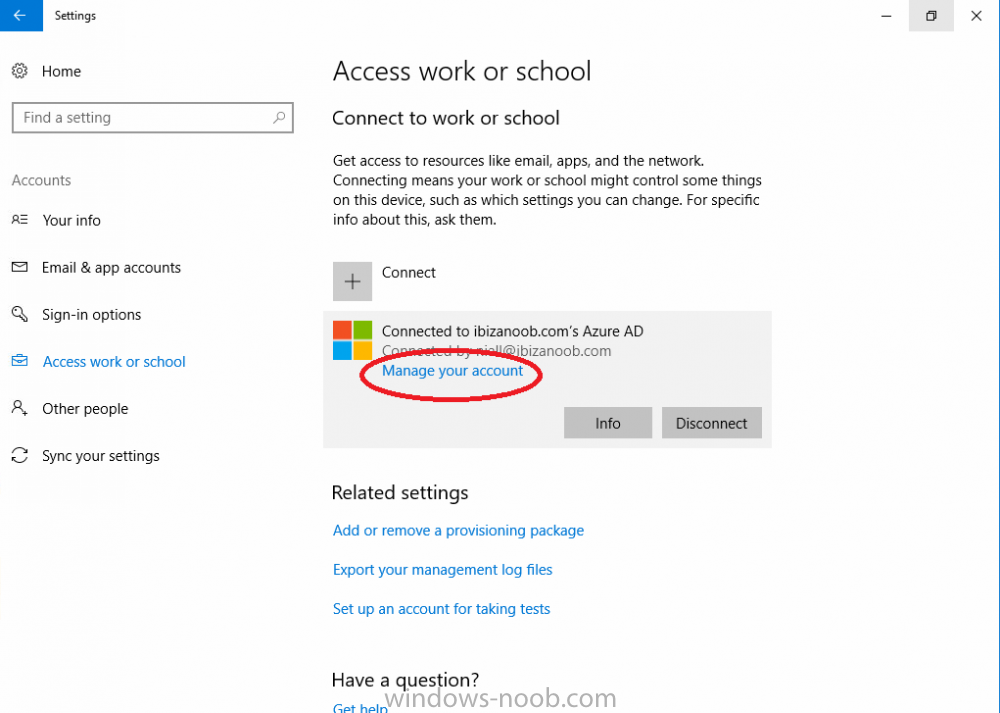
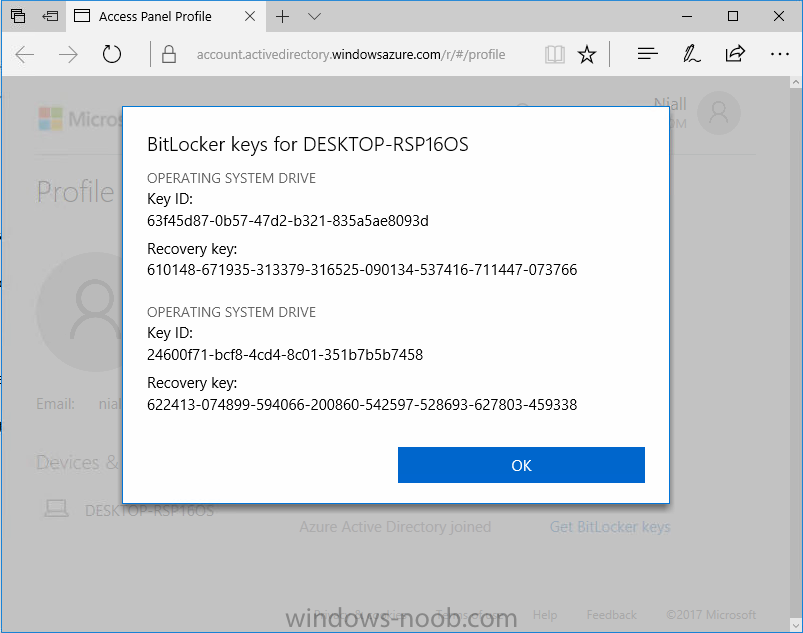
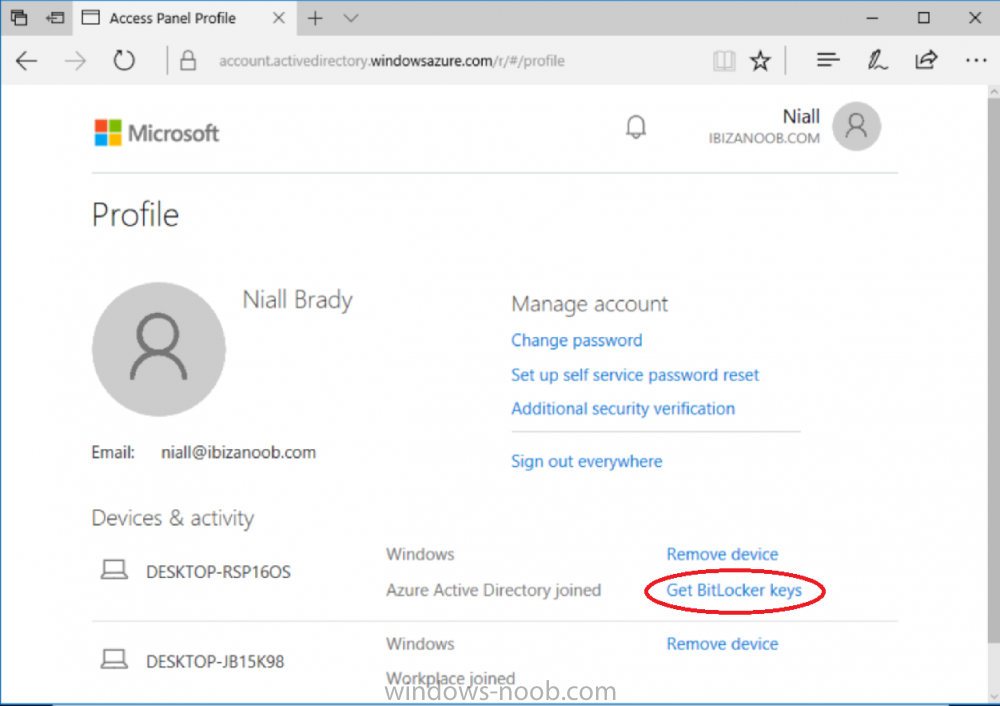
Introduction Security is a big focus for many companies, especially when it comes to data leakage (company data). Encrypting data on Windows 10 devices using BitLocker means that data is protected ("data at rest") . Microsoft Intune got yet more updates on June 30th, 2017, one of which was the...
-
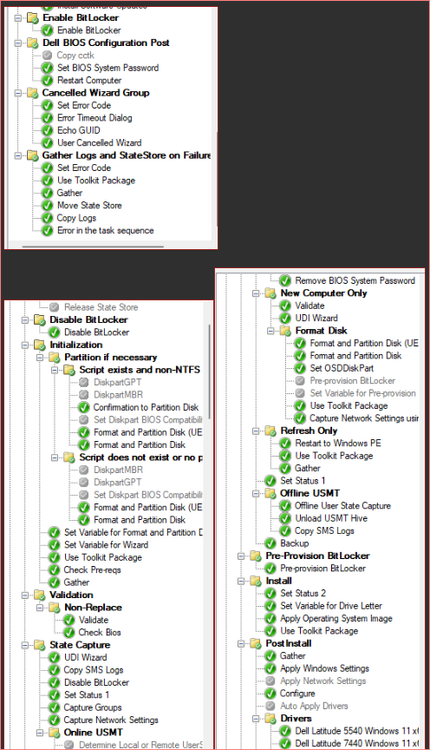
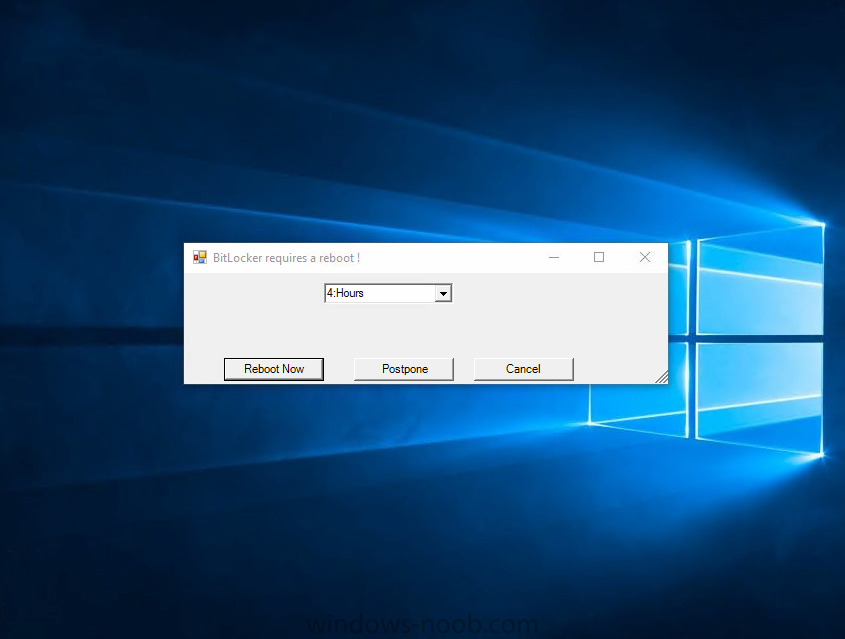
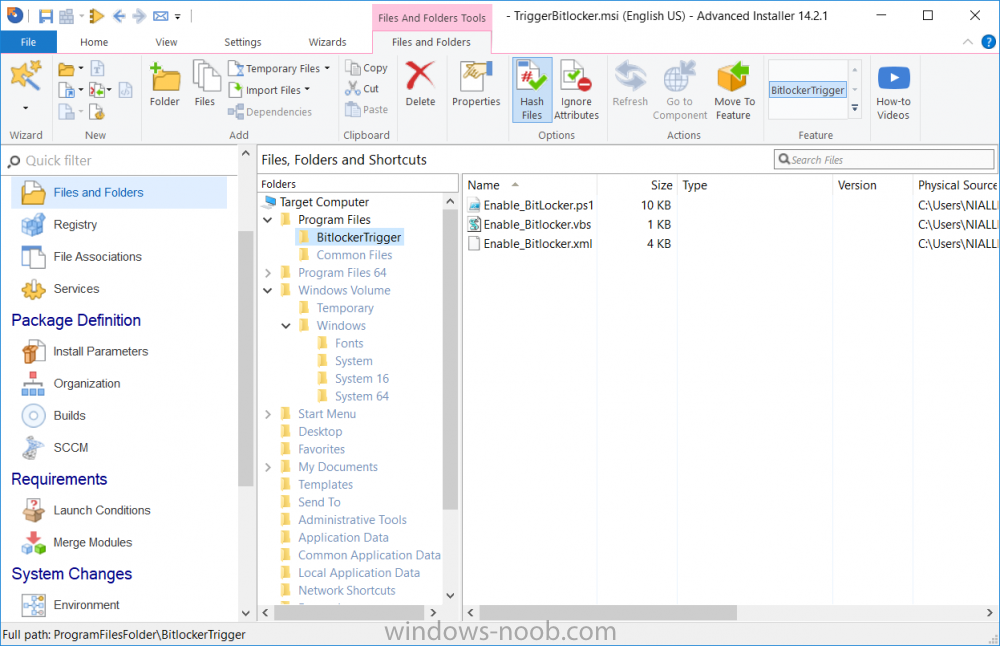
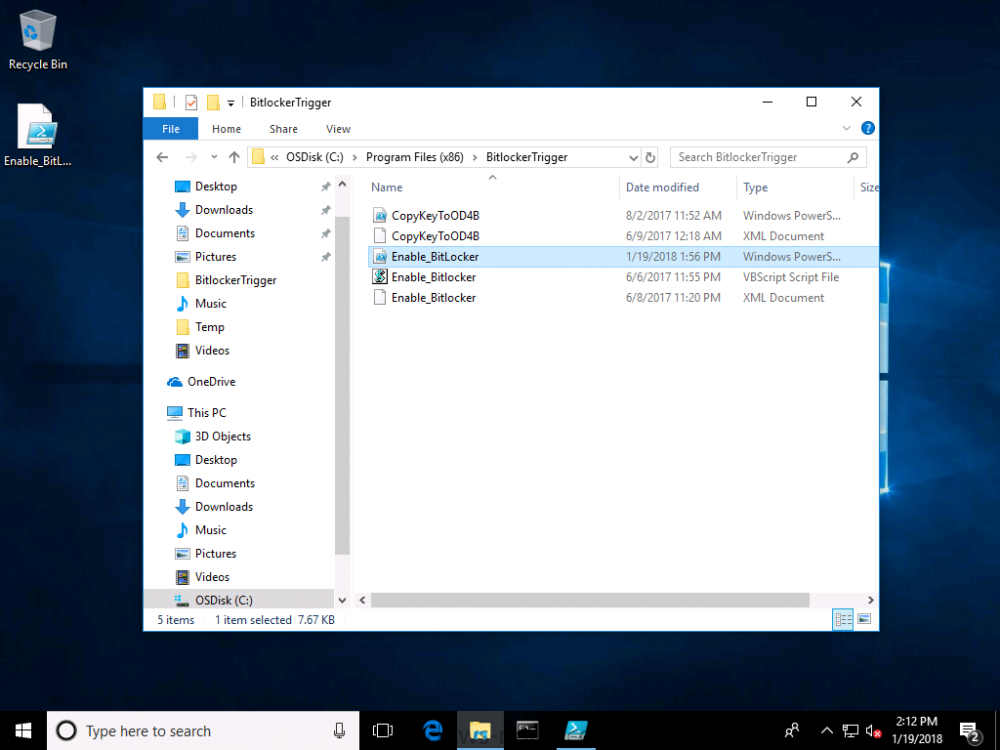
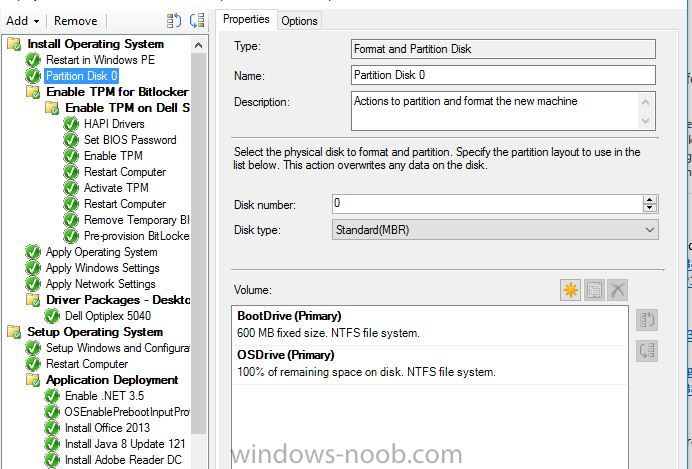
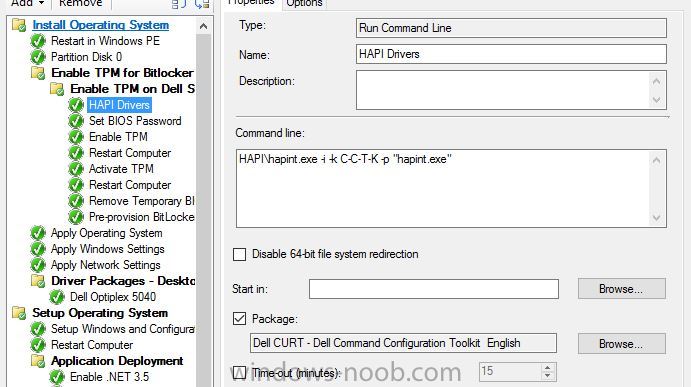
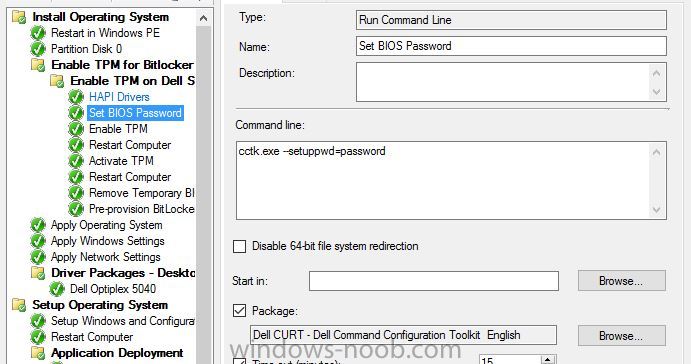
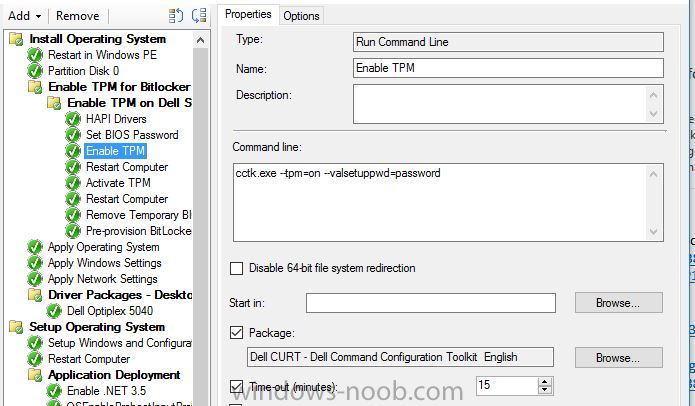
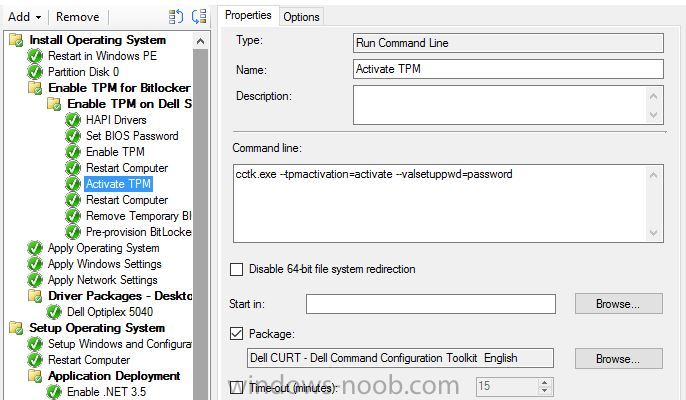
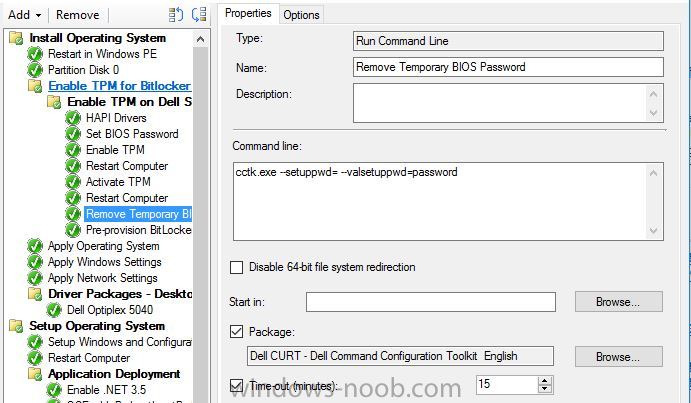
Hello, I've looked on many of forums and I am trying to find a way to enable bitlocker using a task sequence so I don't have to manually do every single laptop separately. I did download and created a package using the Dell CCTK and created a package using the Dell\X86_64 and include all the conte...