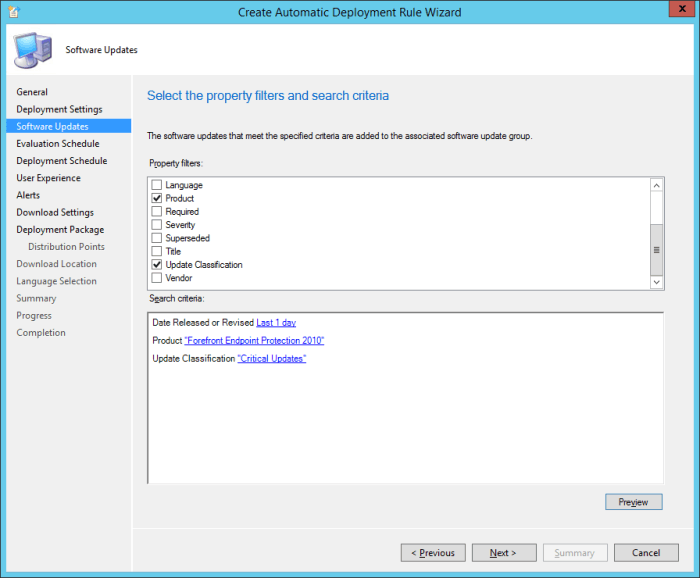
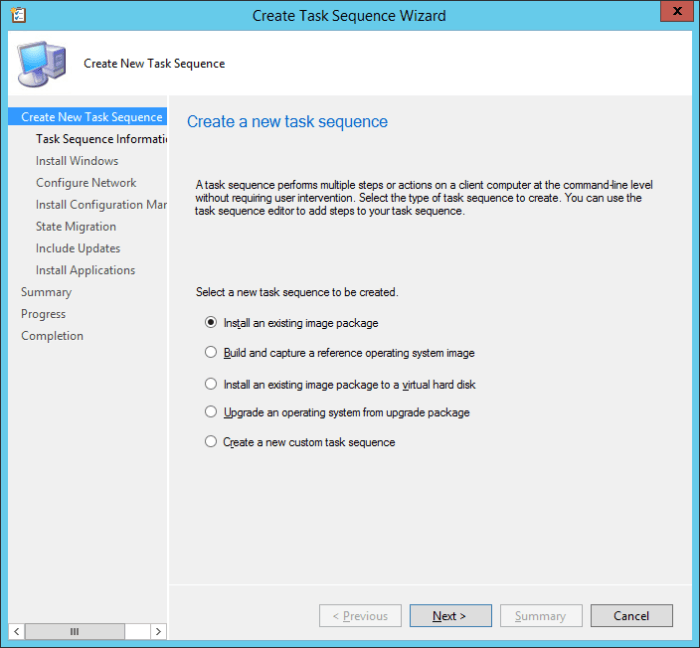
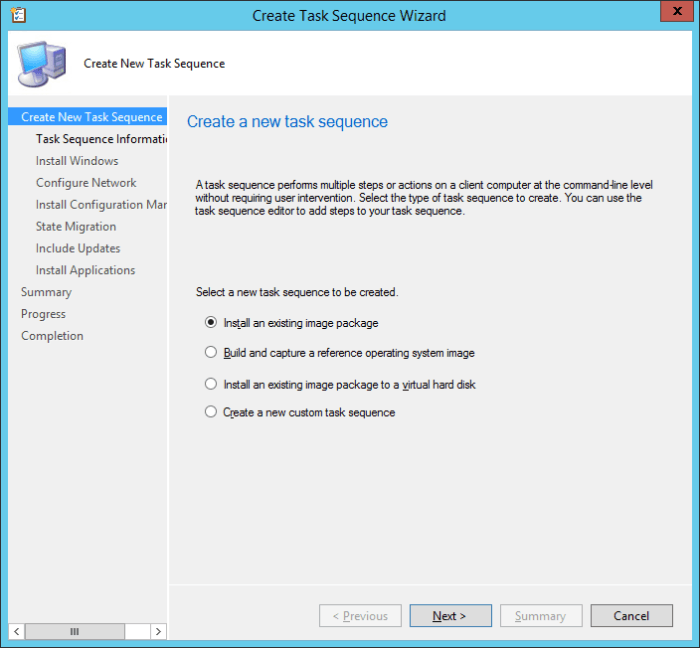
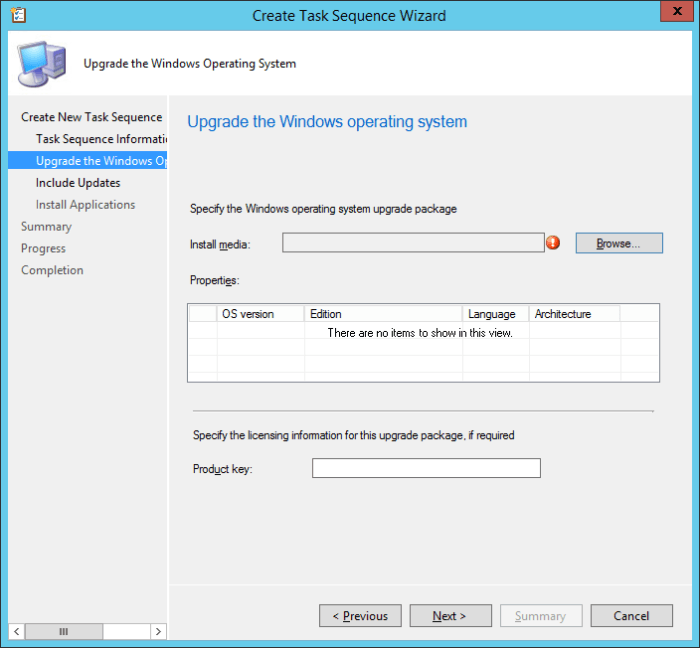
Search the Community
Showing results for tags 'configuration manager'.
-
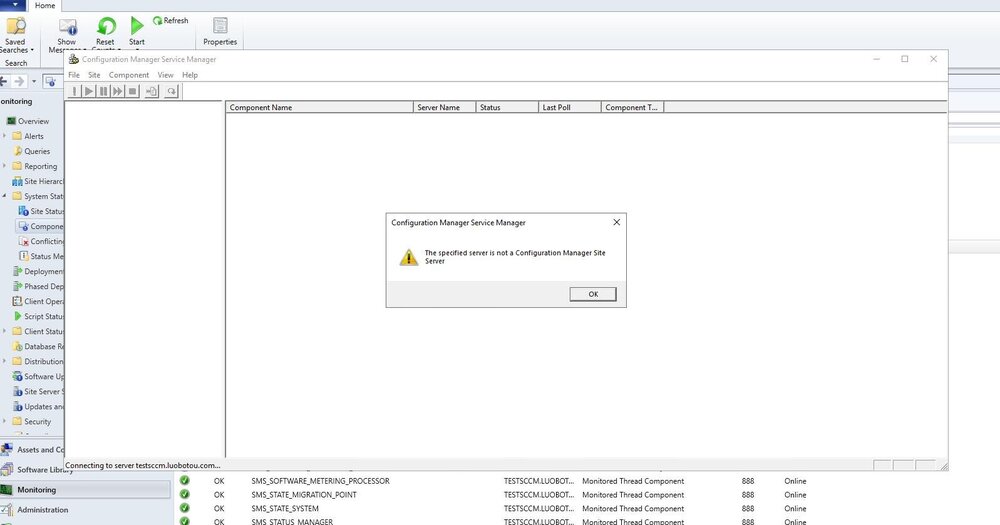
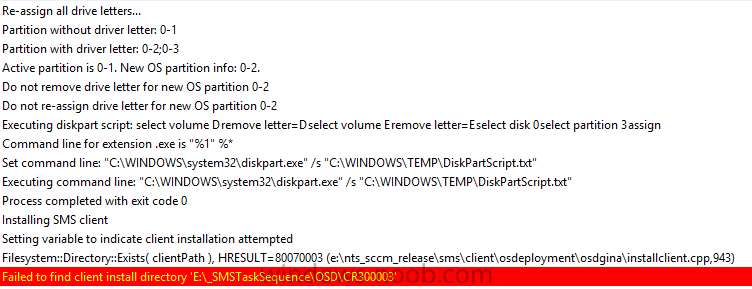
Hi Team, I have been facing an strange issue. After the machine built by OSD TS, client isn't visible as online in Console and I don't think client is getting policies applied. Validated Firewall ports (80,443,10123) and all are fine. Any clue or troubleshoot approach would be much appreciated...
-
- client
- configuration manager
-
(and 1 more)
Tagged with:
-
Hi Everyone, I'm a new Level 2 Technician as i was previously Level 1 technician and my main role was helping users troubleshoot issues on their Computer and recently had a few colleagues from Level 3 started helping me get into SCCM environment were i flourishing from their Wisdom, so found you...Read more
-
Hey Windows Pros, I work as a tech-marketer for ManageEngine. We have some exciting news from Patch Connect Plus, which I thought will be valuable to you. We have introduced "Standard edition" which offers third-party software catalogs to your SCCM 1806. These catalogs can also be used to...
-
- patch connect plus
- sccm
- (and 4 more)
-
sccm Manage Blades with ESXi SO via SCCM
DiegoShadow posted a question in Troubleshooting, Tools, Hints and Tips
Good night friends ! Is it possible for SCCM to include HP Blades with ESXi operating system in hardware inventory? Is this type of management possible?-
- microsoft
- current branch
-
(and 3 more)
Tagged with:
-
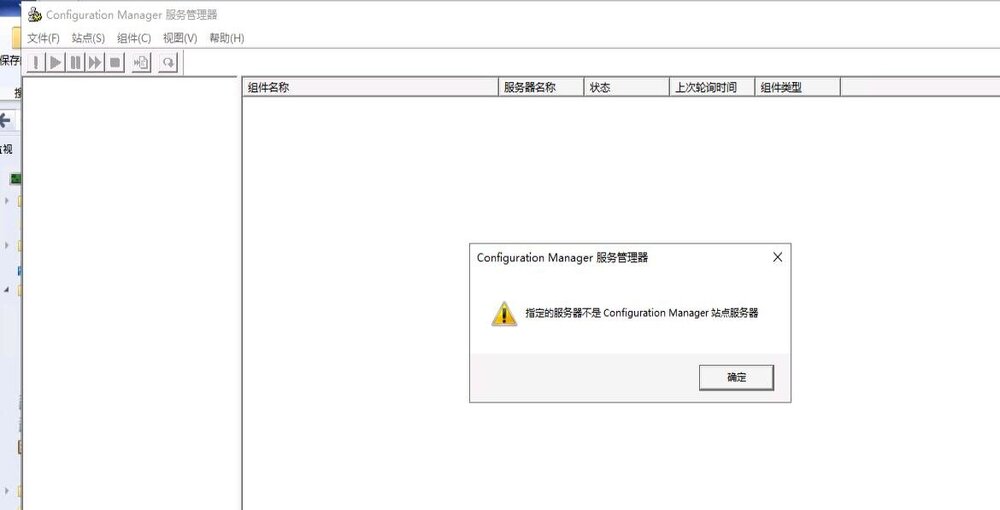
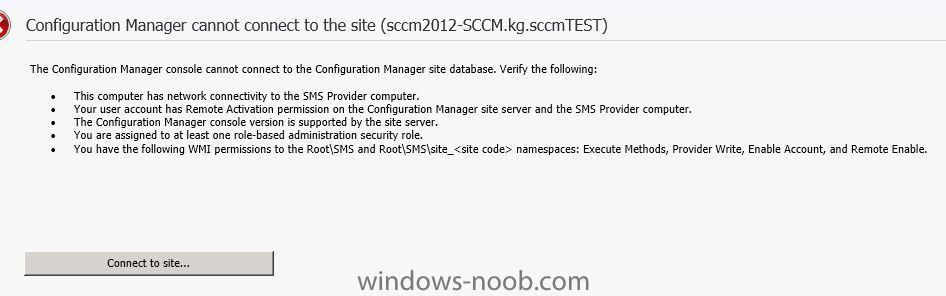
Hei ho, I wonder if anyone can help me with this strange error. I have followed the the instructions here to a tee to install a test of SCCM 2012 but have hit a strange error - Config. Manager cannot connect to the site. And this has me perplexed as the account I am using has full domain...
- 13 replies
-
- sccm 2012
- configuration manager
- (and 8 more)
-
Hi, Console version: 5.0.8355.1306 Site version: 5.00.8355.1000 Having a few issues trying to get 'Configuration Manager 1606' installed using the 'Updates and Servicing' section is SCCM. The 1606 update is in a state of 'Prerequisite check failed'. I have seen a couple of other articles stati...
- 6 replies
-
- SCCM1606
- prerequisite
-
(and 3 more)
Tagged with:
-
Howdy! Has anyone had any luck with gathering HP warranty information in SCCM hardware scans? I have found a bit of information saying that the most common way was a mix of scripts and custom .MOF's using this guide, however apparently these dont really work now as HP has changed the links used...
-
- sccm
- configuration manager
-
(and 2 more)
Tagged with:
-
Hi We are planning a Windows 10 deployment for the not to distant future and I am working on getting a new set of task sequences setup for this, incorporating some of the niggly things we've wanted to do for a long time but haven't had the time or patience. One of those things is setting up...
- 3 replies
-
- SCCM
- Configuration Manager
-
(and 2 more)
Tagged with:
-
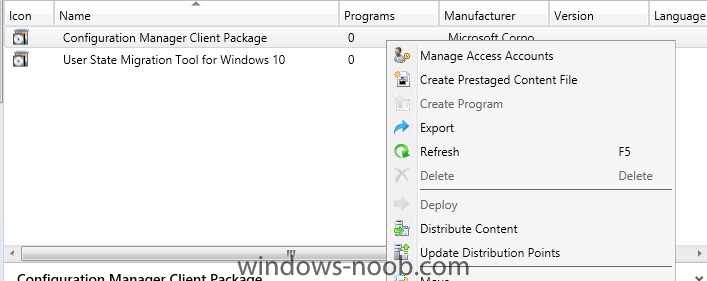
My task sequence fails with - "this task sequence cannot run because the program files for 00100002 cannot be located on a distribution point" (00100002 is config manager client). Does anyone have any idea why? I notice that my client package says 0 programs and has DEPLOY greyed out, so cant be d...
- 1 reply
-
- distribution point
- configuration manager
-
(and 1 more)
Tagged with:
-
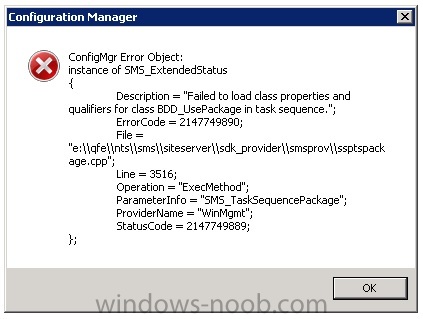
Hello, dear colleagues. We are using SCCM 2012 version 5.00.8239.1000. We have CAS+5 Primary Servers. Some time ago i have noticed that i can't edit task sequences on Cas and on one of Primary servers. Everything is ok on other 4 servers. When i am trying to edit Task Sequences a have error belo...
-
- sccm
- configuration manager
-
(and 1 more)
Tagged with:
-
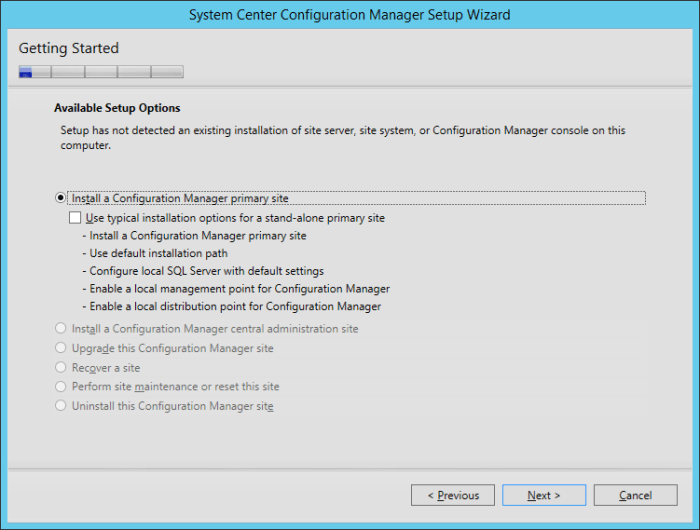
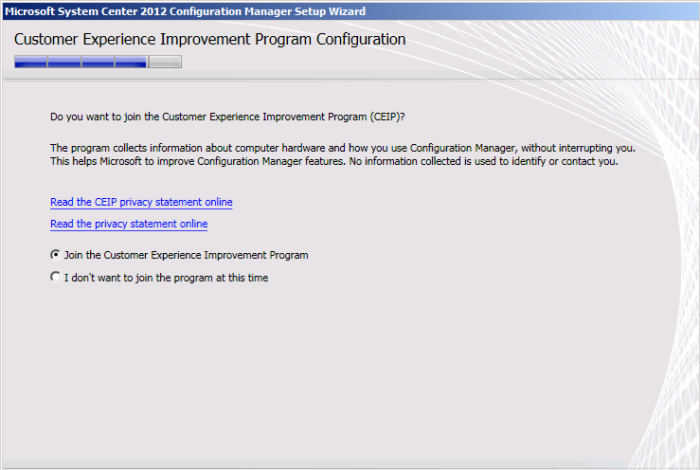
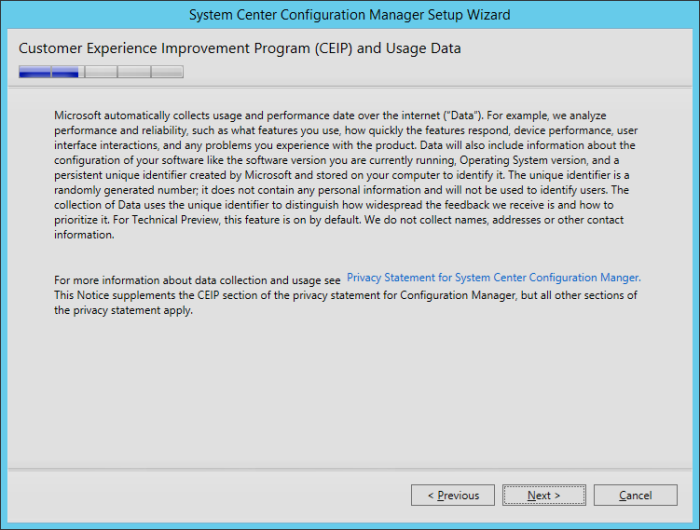
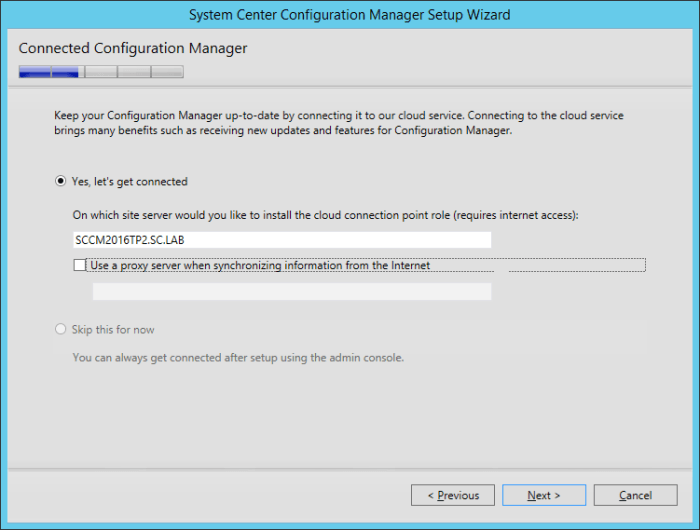
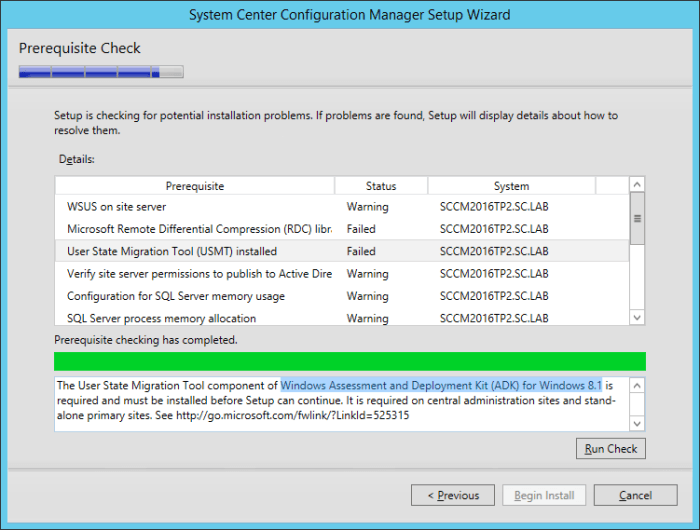
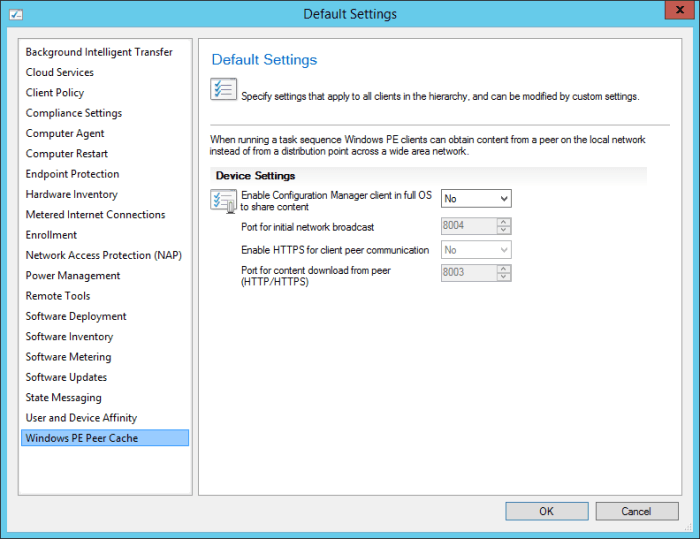
Microsoft recently released the Technical Preview 2 of System Center Configuration Manager 2016: https://technet.microsoft.com/library/dn965439.aspx Per the TechNet article: This release adds the following additional capabilities: Sideloading apps in Windows 10 Windows PE Peer Cache On-premise...
- 1 reply
-
- SCCM 2016 TP2
- Configuration Manager
-
(and 1 more)
Tagged with:
-
By any chance... I am deploying new OS and when I give a name to the new computer before running the task sequence, for some reason if have more than 8 characters when applying the new OS the task sequence fails. Is there any way I can override and set it to take more characters? I noticed i...
- 1 reply
-
- sccm 2012
- Configuration Manager
- (and 3 more)
-
I am attempting to write a powershell script for our 2012 SP1 environment that well ask for the input of a package ID and it will prestage its dependencies all in separate pkgx files so it is easier to tell what has already been pre-staged. Each dependency will be named by package ID. I have th...
- 1 reply
-
- SCCM
- Configuration Manager
-
(and 3 more)
Tagged with:
-
Hi Guys, Today while troubleshooting the MP role installation failure I saw " Failed to grab execution mutex. System error 258." in mpmsi.log file, Is this something because of pending reboot of the system (I noticed that system is pending for reboot in registry and the files that are waiting are...
-
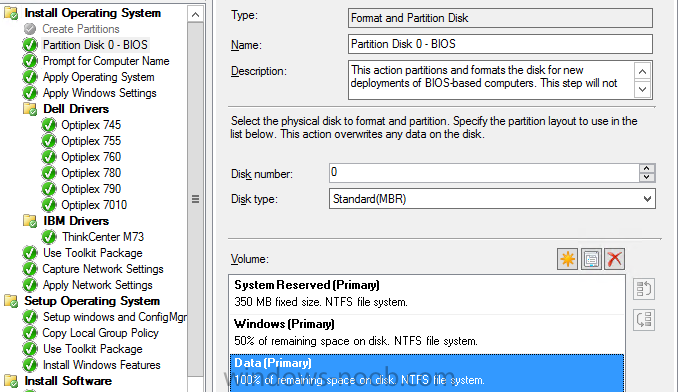
Greetings All, I am having a bit of trouble creating a TS that creates two partitions. If I only have one it works perfectly as soon as I try and add the second the TS fails. I can see what is causing the failure but i don't know why. Let me know if any other info is needed. Desired Outcome:...
- 10 replies
-
- Configuration Manager
- 2012
-
(and 5 more)
Tagged with:
-
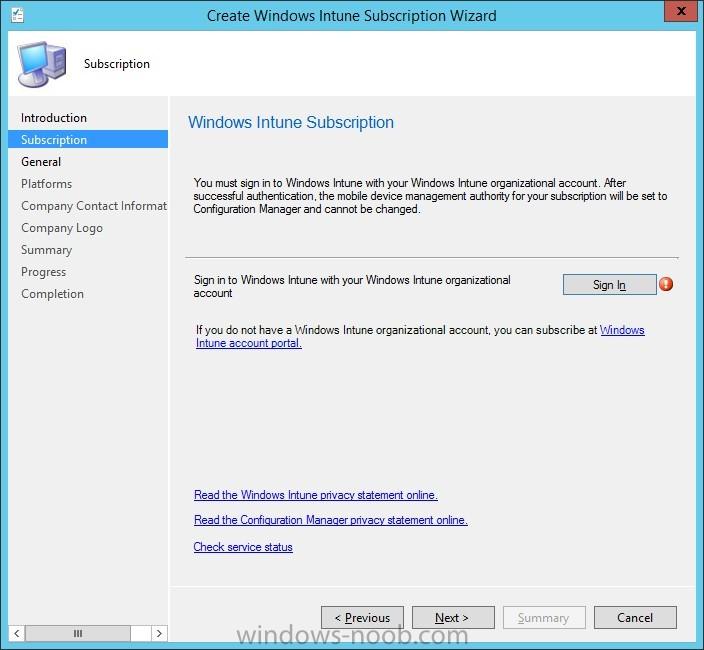
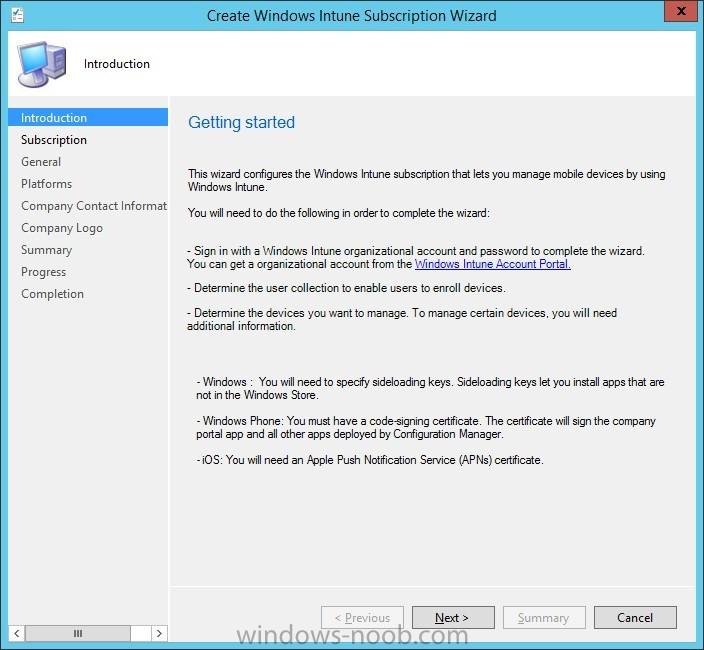
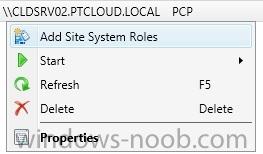
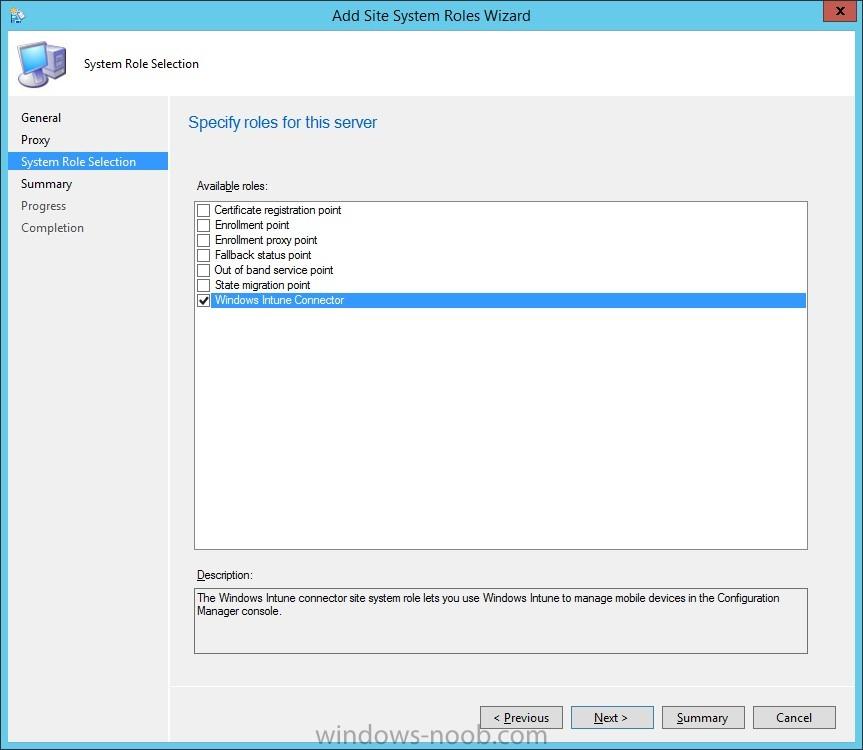
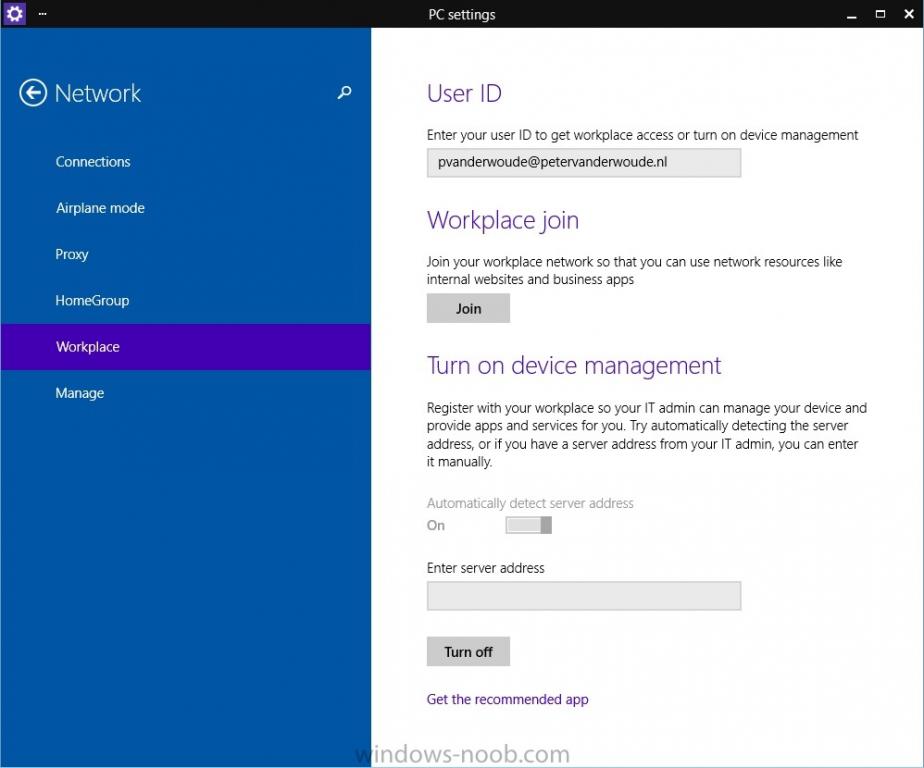
I've created an PDF that contains the content of the series I did about integrating Microsoft Intune and System Center 2012 R2 Configuration Manager with Single Sign-On. All the following parts are covered in the PDF: How to integrate Microsoft Intune and System Center 2012 R2 Configuration Manage...
-
- Microsoft Intune
- Configuration Manager
-
(and 4 more)
Tagged with:
-
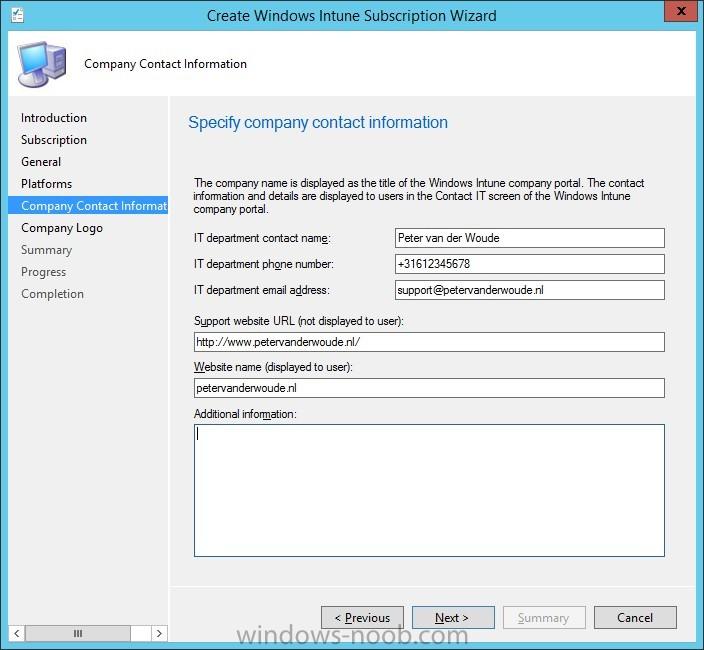
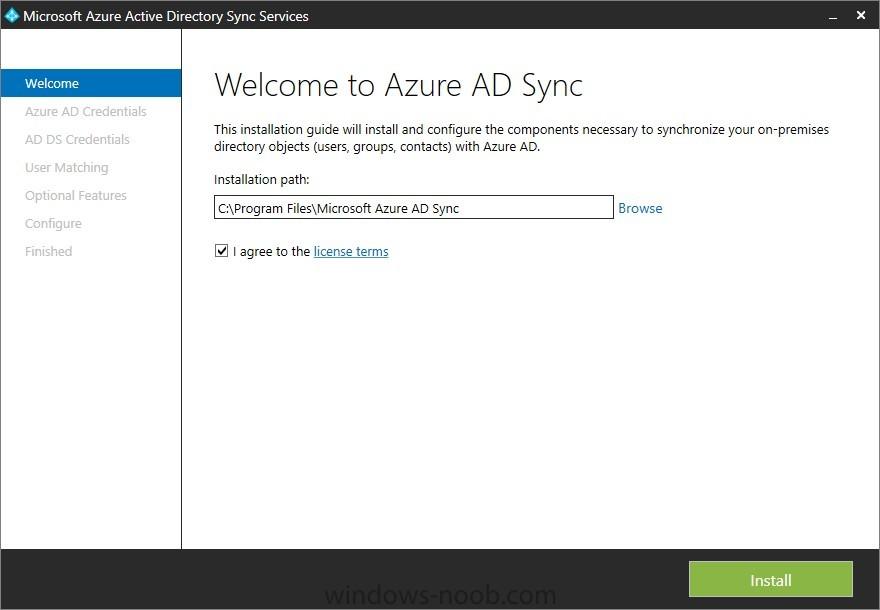
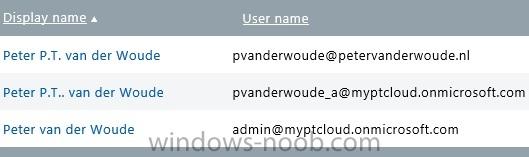
In the first part of this blog series I went through the introduction and the prerequisites, in the second part I went through the installation and configuration of AD FS and in the third part I went through the directory synchronization. This fourth part of the blog series will finally be about Con...
-
- Microsoft Intune
- Configuration Manager
-
(and 3 more)
Tagged with:
-
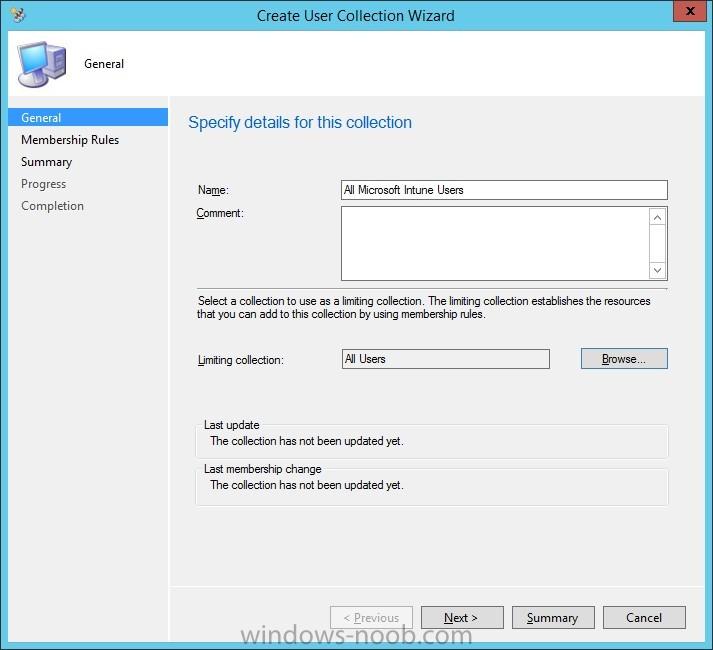
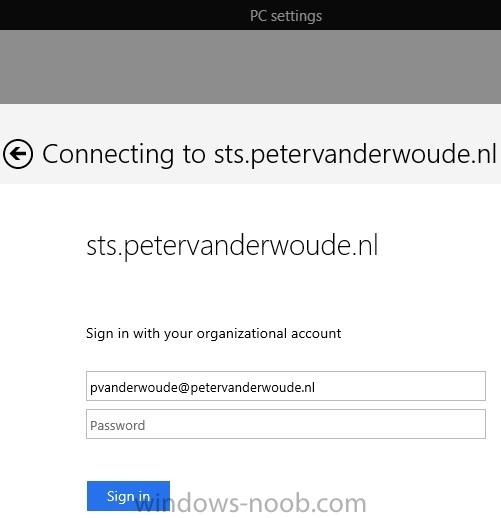
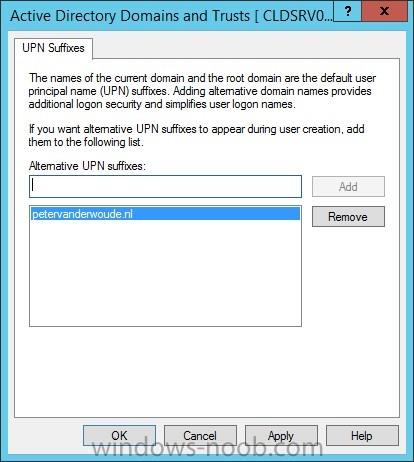
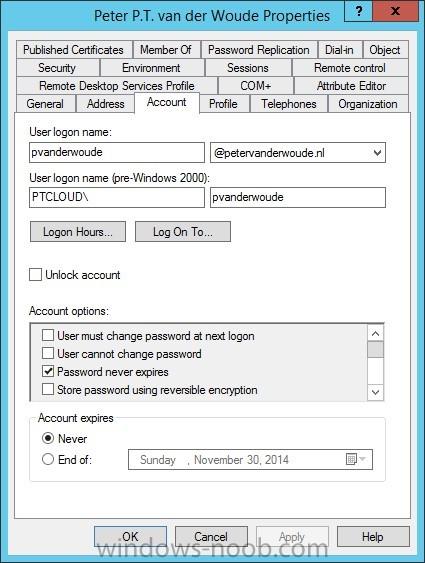
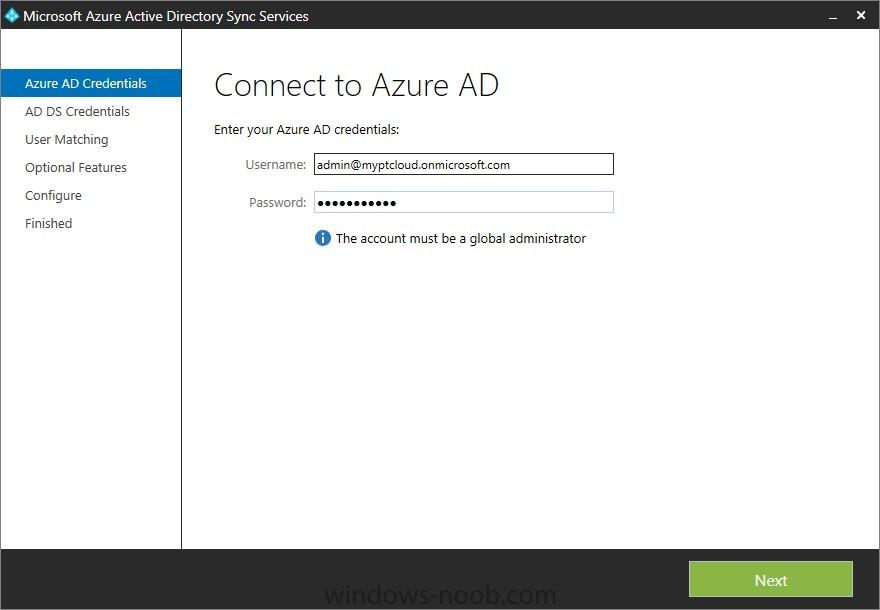
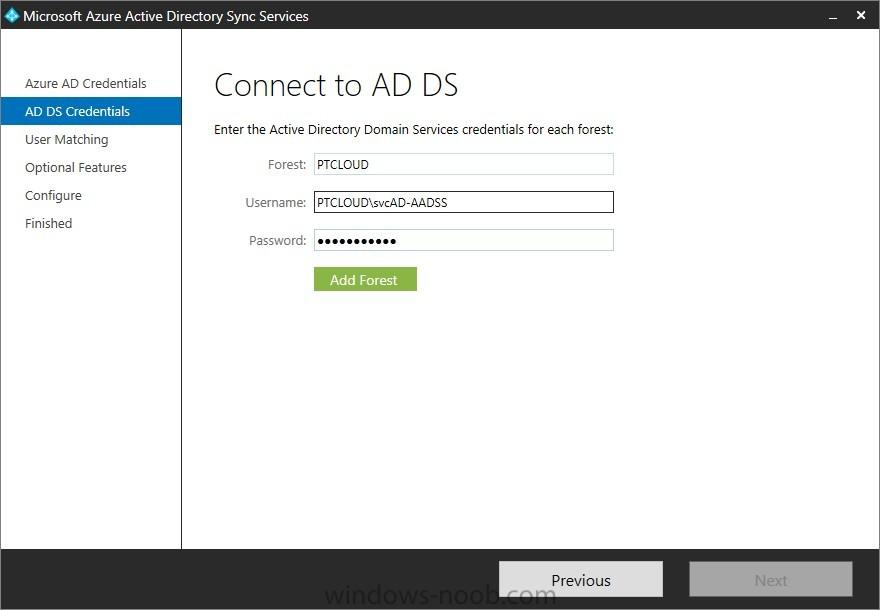
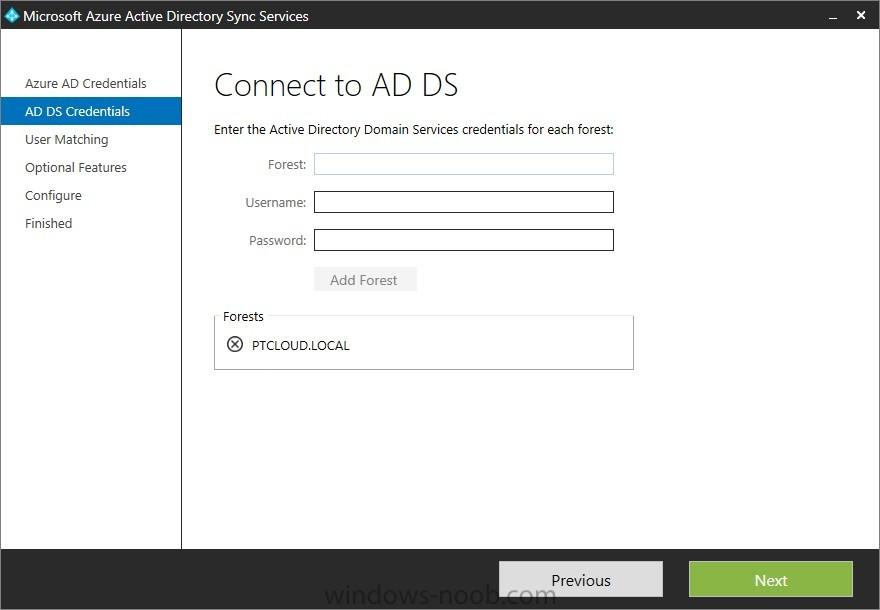
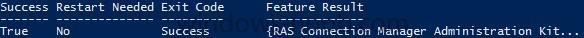
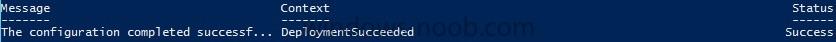
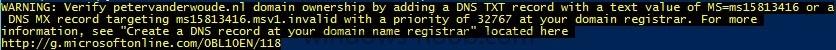
In the first part of this blog series I went through the introduction and the prerequisites and in the second part I went through the installation and configuration of AD FS. This third part of the blog series will be all about configuring, configuring and configuring. First it's required to add the...
-
- Microsoft Intune
- Configuration Manager
-
(and 4 more)
Tagged with:
-
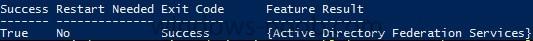
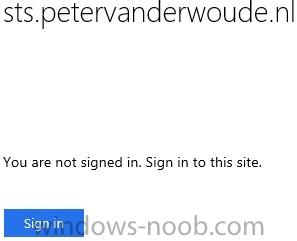
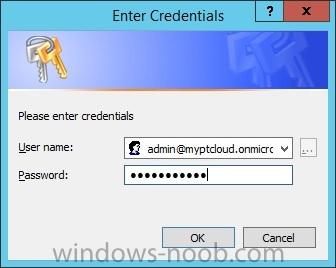
In the first part of this blog series I went through the introduction and the prerequisites. This second part of the blog series will be all about installing and configuring Active Directory Federation Services (AD FS) and the AD FS proxy, which is the Web Application Proxy (WAP) in Server 2012 R2....
-
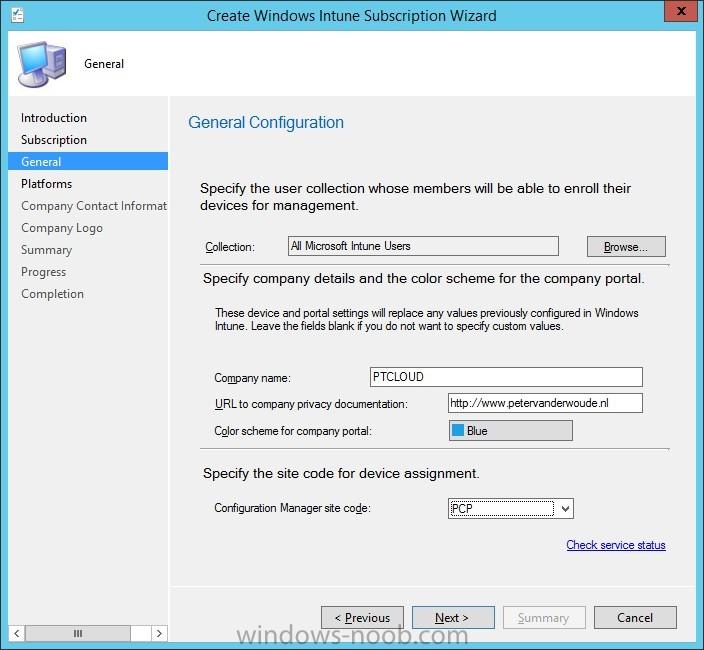
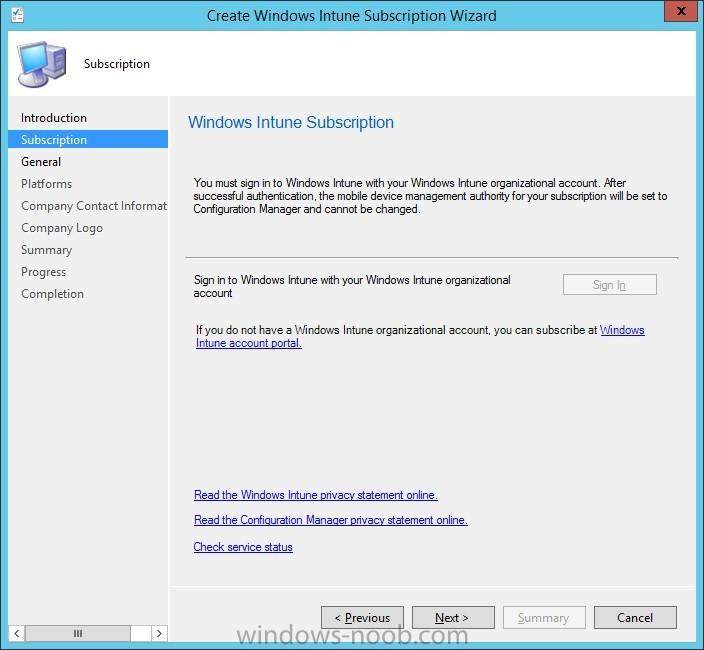
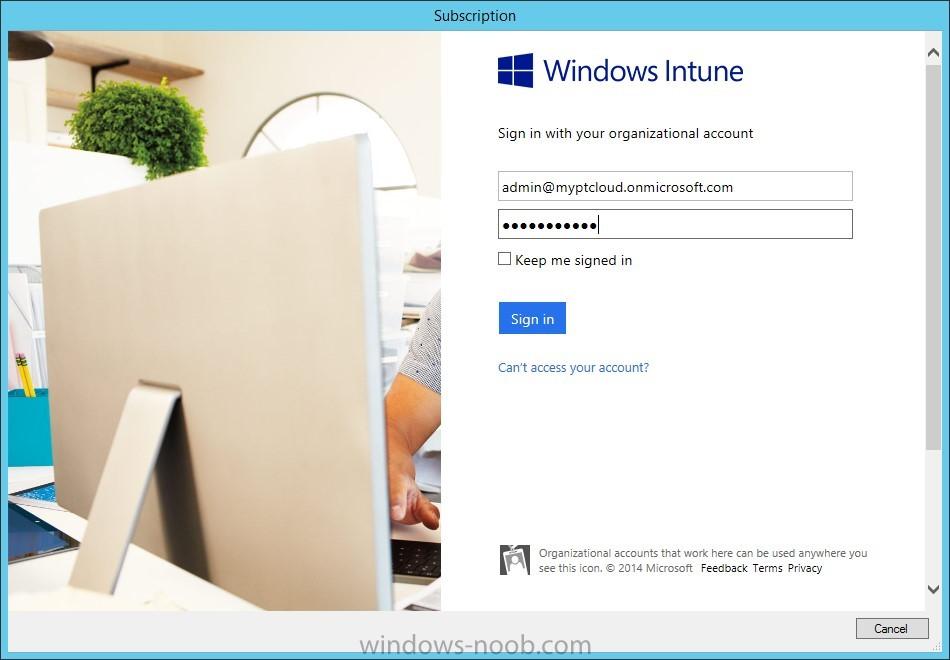
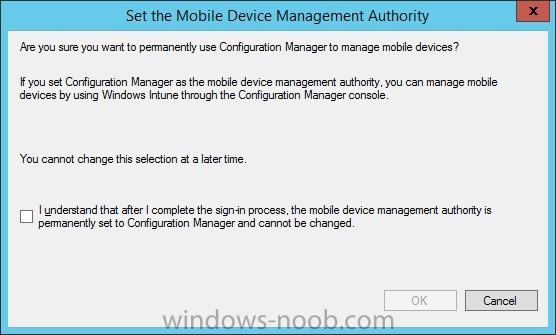
Introduction In this blog series I’m going to show how to setup a basic configuration of Microsoft Intune, integrated with System Center 2012 R2 Configuration Manager, in combination with and on-premises Active Directory Federation Services (AD FS) for a single sign-on experience. After successfully...
-
- Microsoft Intune
- Configuration Manager
-
(and 2 more)
Tagged with:
-
In Configuration Manager, you right click on a resource and select Clear Last PXE Advertisement a window would appear and if a PXE Flag occurred you would see an Advertisement. I am working on a Front End tool for a client and one of their request is to be able to see if a workstation has a PXE Adv...