Search the Community
Showing results for tags 'memcm'.
-
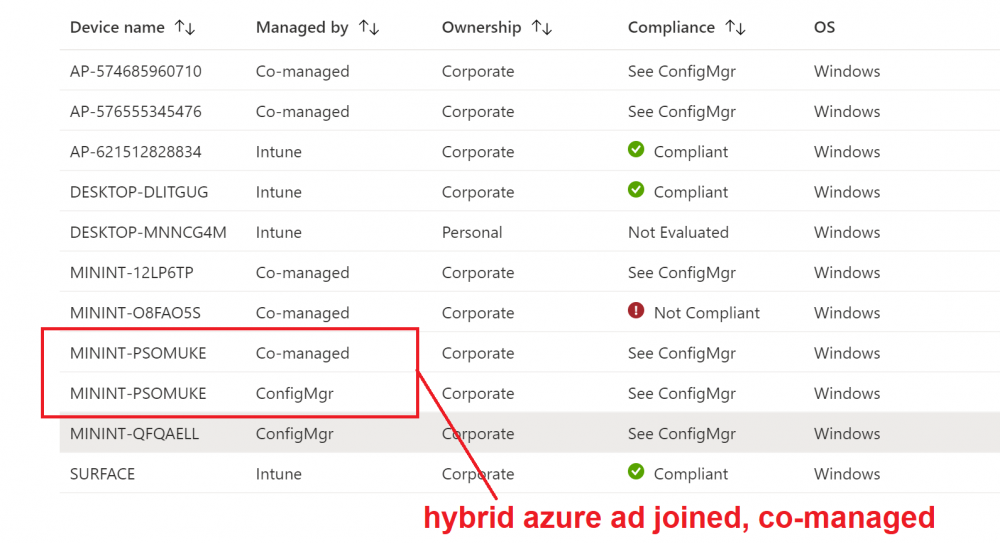
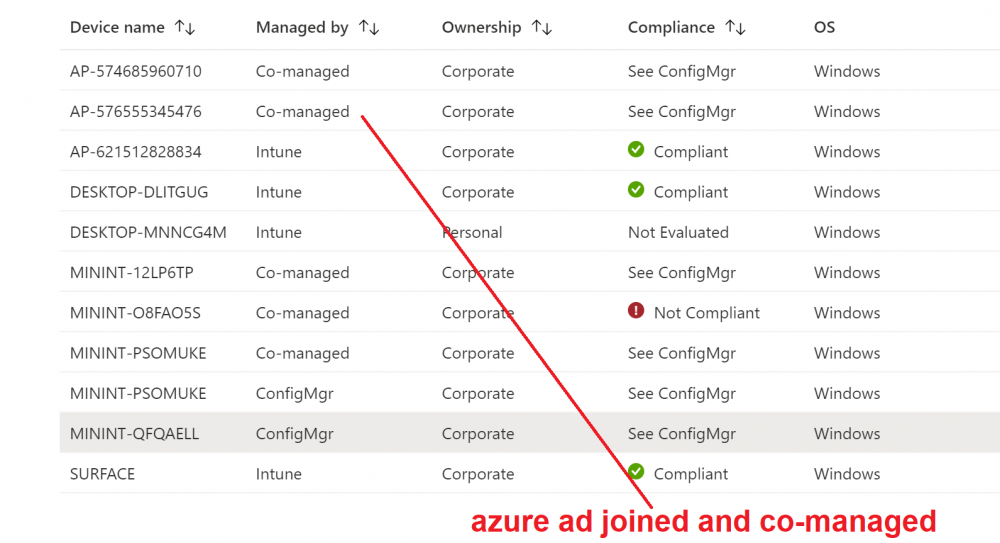
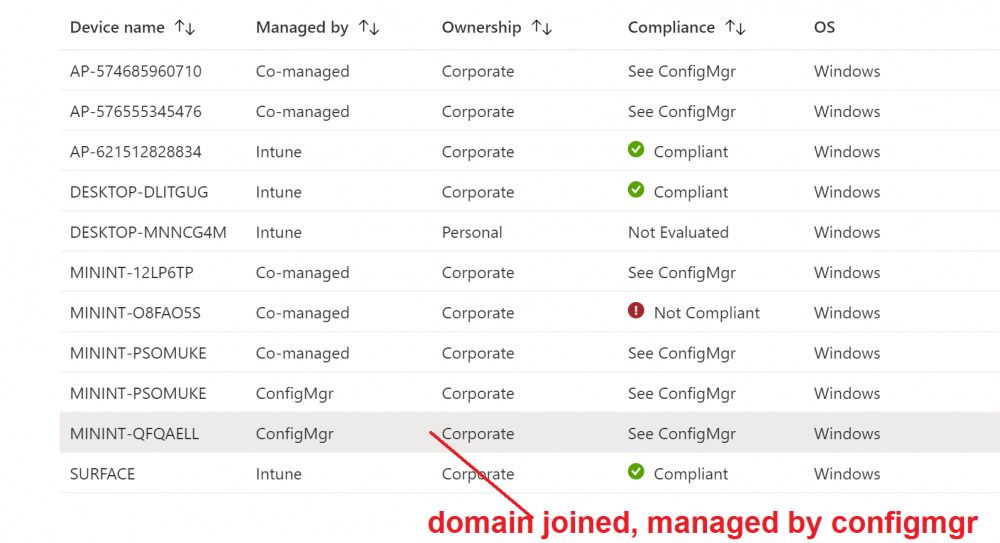
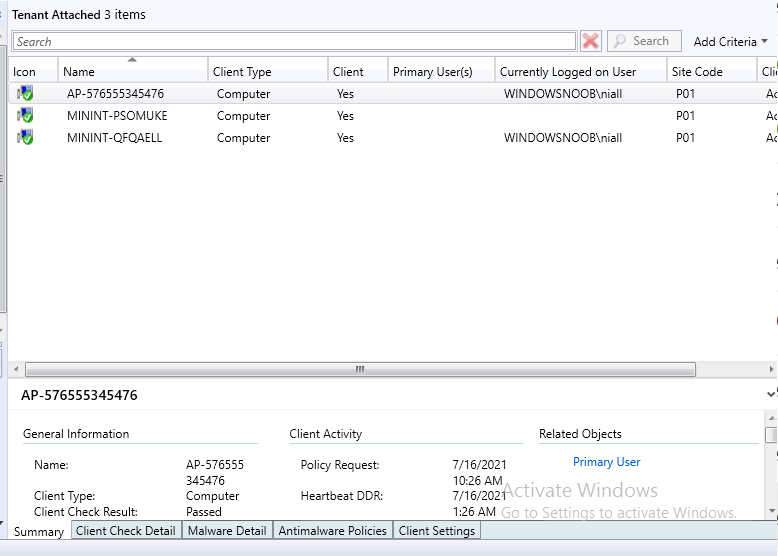
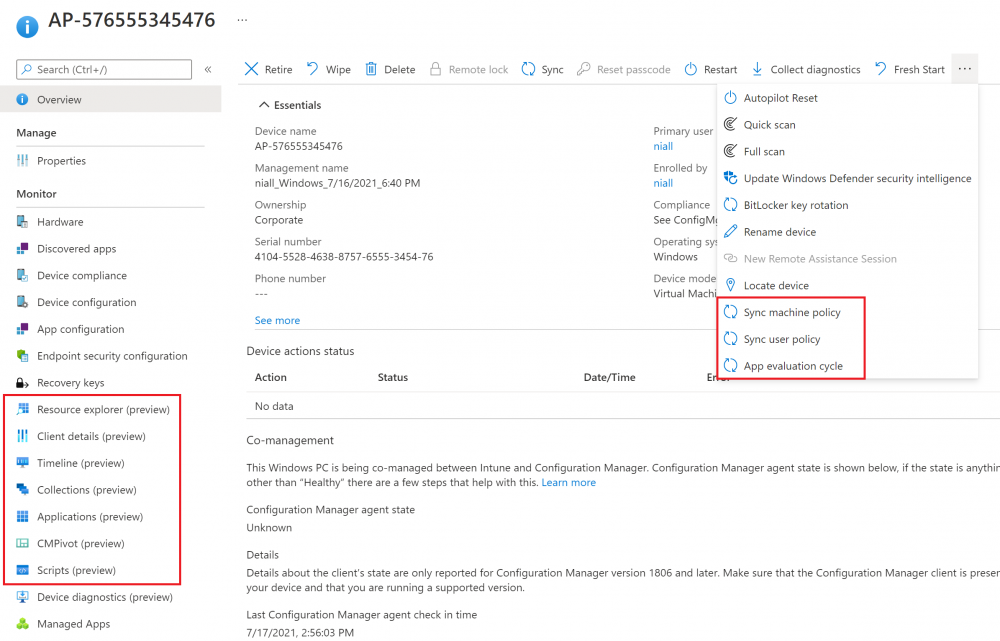
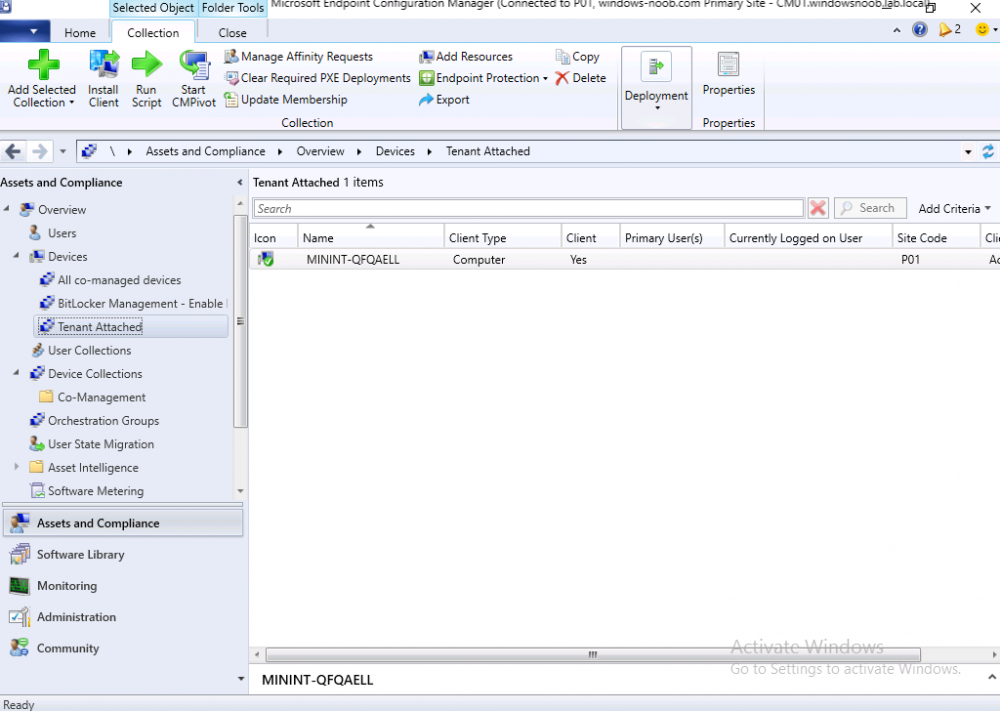
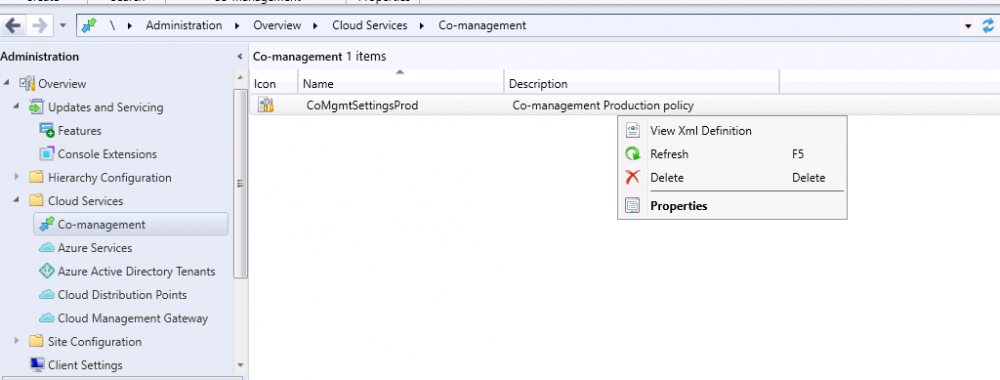
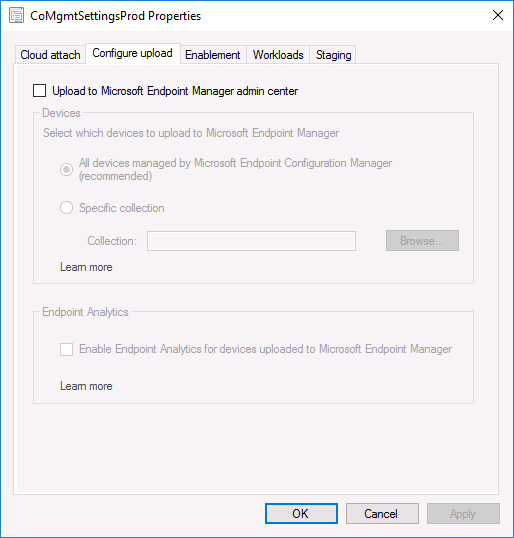
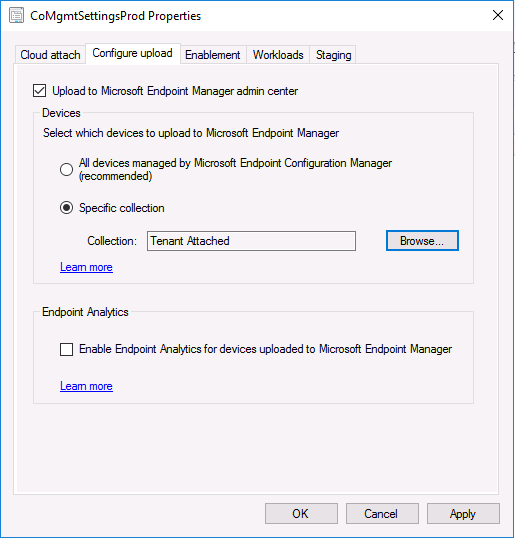
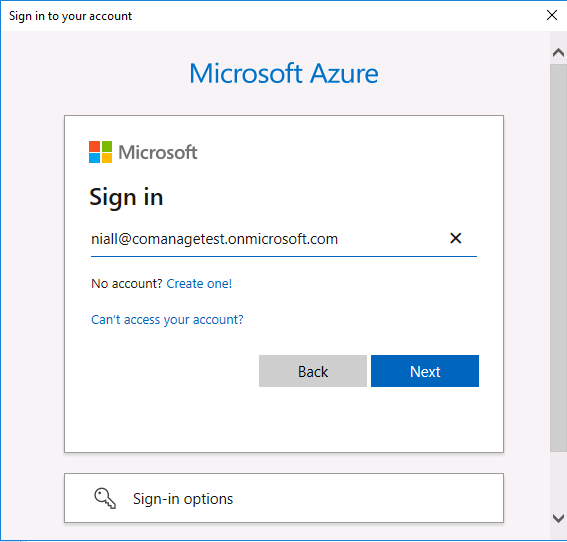
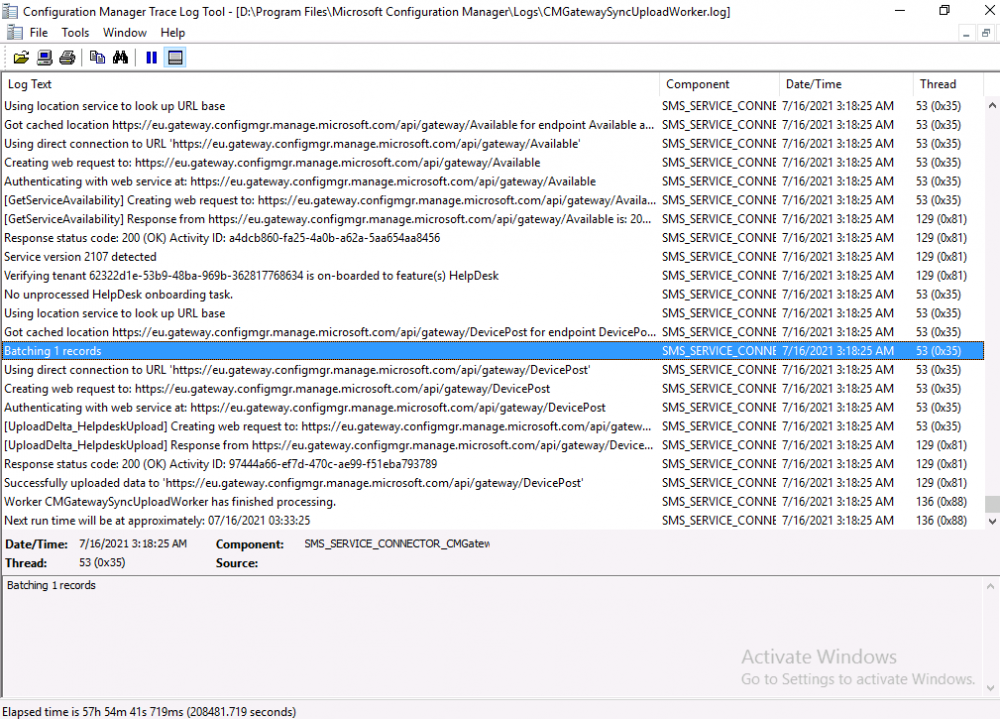
Introduction This is part 8 in a series of guides about cloud attach in Microsoft Endpoint Manager, with the aim of getting you up and running with all things cloud attach. This part will focus on enabling tenant attach. This series is co-written by Niall & Paul, both of whom are Enterprise Mobility MVP’s with broad experience in the area of modern management. Paul is 5 times Enterprise Mobility MVP based in the UK and Niall is 11 times Enterprise Mobility MVP based in Sweden. In part 1 we configured Azure AD connect to sync accounts from the on premise infrastructure to the cloud. In part 2, we prepared Azure resources for the Cloud Management Gateway, in part 3 we created the cloud management gateway and verified that everything was running smoothly. In part 4 we enabled co-management. With co-management, you retain your existing processes for using Configuration Manager to manage PCs in your organization and you gain the additional advantage of being able to transfer workloads to the cloud via Endpoint Manager (Intune). In part 5 we enabled the compliance policies workload and reviewed how that affected a co-managed computer. In this part we will enable conditional access and see how that can be used to deny access to company resources. In part 6 we configured conditional access and used it to deny access to company resources unless the device was encrypted with BitLocker. In part 7 we showed you how to co-manage Azure AD devices. In this part we'll enable Tenant Attach and take a brief look at it's features. Below you can find all parts in this series. Cloud attach - Endpoint Managers silver lining - part 1 Configuring Azure AD connect Cloud attach - Endpoint Managers silver lining - part 2 Prepare for a Cloud Management Gateway Cloud attach - Endpoint Managers silver lining - part 3 Creating a Cloud Management Gateway Cloud attach - Endpoint Managers silver lining - part 4 Enabling co-management Cloud attach - Endpoint Managers silver lining - part 5 Enabling compliance policies workload Cloud attach - Endpoint Managers silver lining - part 6 Enabling conditional access Cloud attach - Endpoint Managers silver lining - part 7 Co-managing Azure AD devices Cloud attach - Endpoint Managers silver lining - part 8 Enabling tenant attach <- you are here Cloud attach - Endpoint Managers silver lining - part 9 Renewing expiring certificates Cloud attach - Endpoint Managers silver lining - part 10 Using apps with tenant attach Tenant attach first showed up in Technical Preview 2002.2, but was released in ConfigMgr 2002 which you can read about here. You can think of tenant attach as being a way to give your Endpoint Manager admins access to ConfigMgr actions/data via the MEM console (login to your tenant at https://aka.ms/memac) without needing to do it via the ConfigMgr console. The prerequisites The user account needs to be a synced user object in Azure AD (hybrid identity). This means that the user is synced to Azure Active Directory from Active Directory. For Configuration Manager version 2103, and later: Has been discovered with either Azure Active Directory user discovery or Active Directory user discovery. For Configuration Manager version 2010, and earlier: Has been discovered with both Azure Active Directory user discovery and Active Directory user discovery. The Initiate Configuration Manager action permission under Remote tasks in the Microsoft Endpoint Manager admin center. For more information about adding or verifying permissions in the admin center, see Role-based access control (RBAC) with Microsoft Intune. Note: In case it’s not clear above, you need to configure Azure AD Connect to sync your on-premise users to the cloud for the user actions to succeed. You also need to go through the Azure services in ConfigMgr and configure cloud management to sync Azure Active Directory User Discovery. During this blog post we used a user that satisfies the above, namely niall@azurenoob.com to perform the tenant attach related actions in MEM. Step 1. Create a collection This is an optional step, but helps you to keep track of which devices are Tenant Attached. Create a collection called Tenant Attached, you will use that collection to populate your tenant attached devices. Once created, place one or more devices into the collection. Step 2. Enable tenant attach In the ConfigMgr console, select the Administration node and expand cloud services, select Co-management (2103 or earlier) or based on what we saw in the recent technical preview (Technical Preview 2106) select Cloud Attach (2107 or later). Select CoMgmgtSettingsProd, right click and bring up the properties. In Co-management properties, click on the Configure upload tab. Next, place a check in the Upload to Microsoft Endpoint Manager admin center checkbox, and select a collection, for example use the Tenant Attached collection we created in step 1, Note: If you select All devices managed by Microsoft Endpoint Configuration Manager then all devices (including servers) will show up in the MEM console. Next, deselect the Enable Endpoint Analytics for devices upload to Microsoft Endpoint Manager. And finally click Apply. When prompted to authenticate to Azure services, enter the credentials of your Global Admin account for the applicable tenant. After correctly entering your credentials, the changes will be applied and you can review the success or failure of your actions via the CMGatewaySyncUploadWorker.log Step 3. Verify upload of data After a device is added to the target collection, you can look at the CMGatewaySyncUploadWorker.log to verify that it uploads data for the number of records you added. So if for example you add one computer to the Tenant Attached collection, then it'll state "Batching 1 records" as shown below. This will only happen when it detects a new device, in the next upload (15 minutes later) it'll return to Batching 0 records and so on unless of course new devices are detected in the collection. This upload of data occurs every 15 minutes. In the below screenshots, all highlighted devices are tenant attached and are in the Tenant Attached collection. Next, login to your tenant at https://aka.ms/memac this will display your devices. After the data is uploaded from ConfigMgr, check devices in Microsoft Endpoint Manager and depending on the type of device you'll see one or more devices matching that device name. In the first example, we have a device that is shown with two records, one is listed as co-managed and the other record as ConfigMgr. That record is tenant attached. The Managed by column will denote how the device is managed and tenant attached co-managed devices (hybrid azure ad joined) may have a second record where it states managed by ConfigMgr. We saw this repeatedly with this specific client, even after clean installing Windows 10 on it...the client version in this particular case was CM2103. If it's an Azure AD joined device that is also co-managed (as we described in Part 7) then the managed by column will state Co-managed and yet this device will have only one record. Lastly if the device is merely managed by ConfigMgr (not co-managed, not azure ad joined) then it will show up with one record. Step 4. Looking into tenant attach features Now that we can identify the different types of devices that are tenant attached, let's take a look at the power of tenant attach. If we look at the Azure AD joined, co-managed device which we deployed in part 7, we can see that the following additional capabilities are now available by enabling tenant attach and adding this computer to that collection so that the device becomes tenant attached. The following are available (in preview): Resource explorer Client details Timeline Collections Applications CMPivot Scripts in addition, you can now trigger the following actions Sync machine policy Sync user policy App evaluation cycle In the MEM console, the tenant attach abilities are highlighted below in red. Below you can see the Timeline feature and some of the data it can provide. To grab more data, click the Sync button and then refresh the screen. And here's a quick look at CMPivot Resource explorer is chock full of data Conclusion Using Tenant attach gives your admins more power to do ConfigMgr actions via the MEM console without needing to even install the ConfigMgr console.
-
- memcm
- endpoint manager
-
(and 1 more)
Tagged with:
-
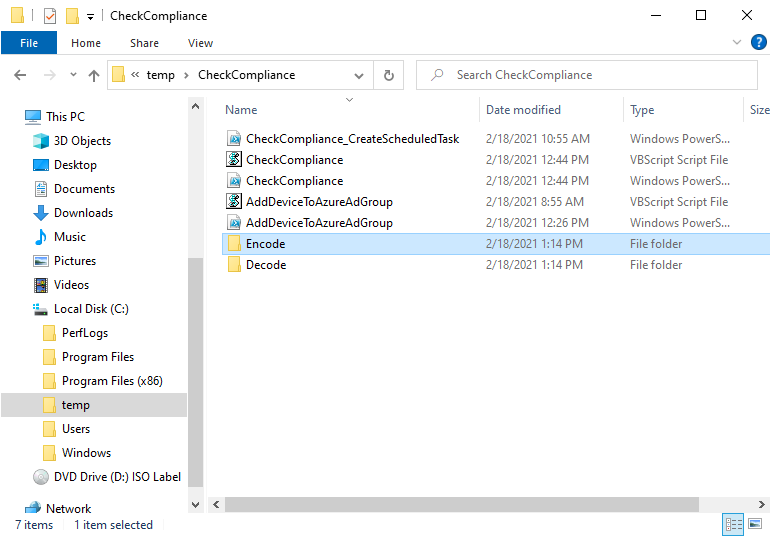
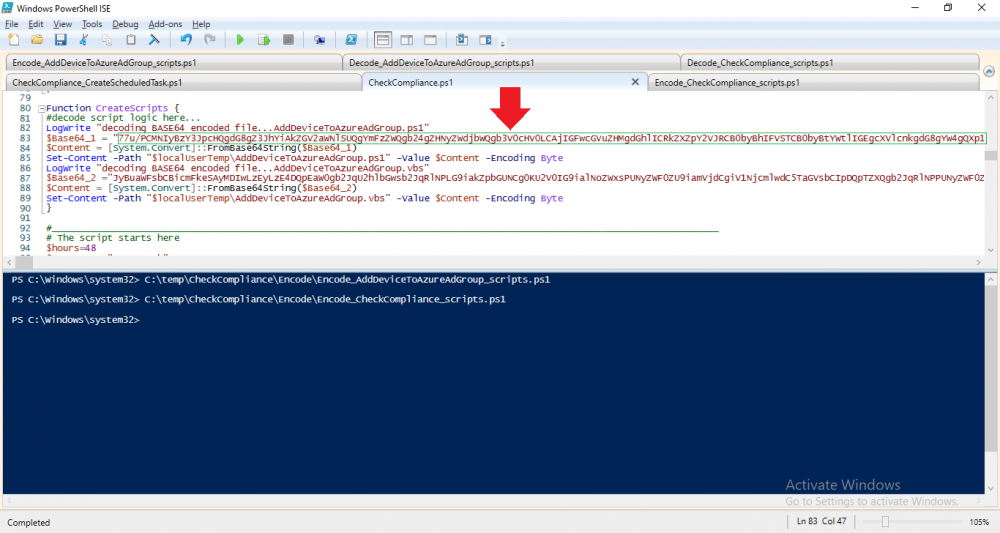
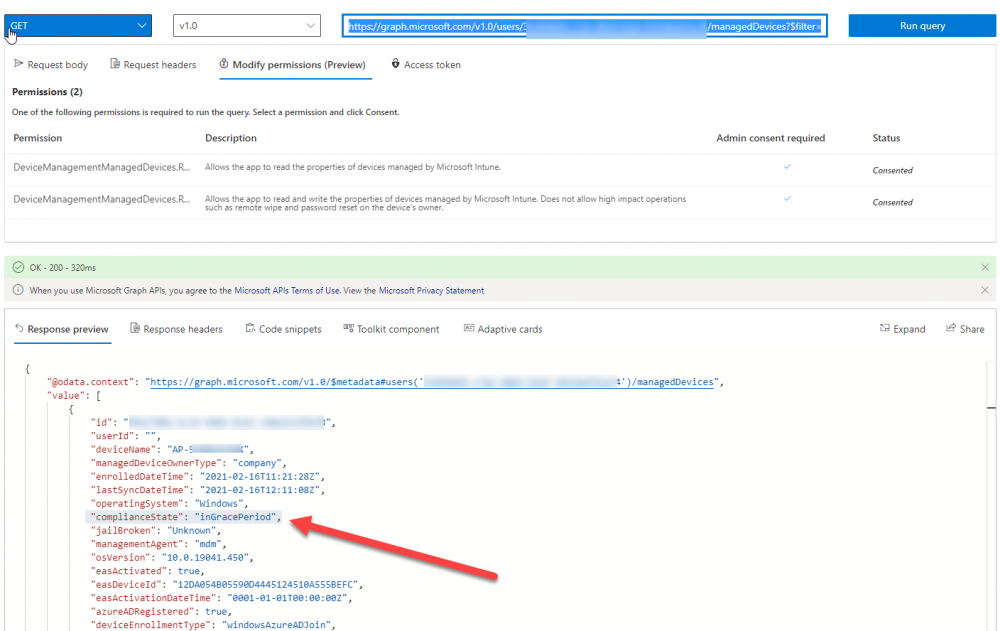
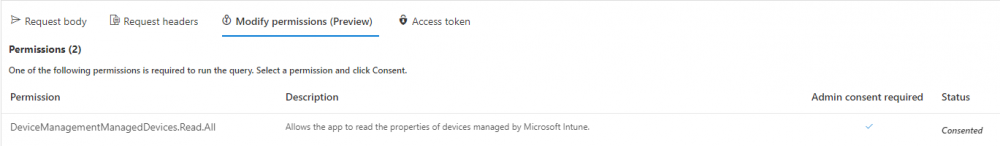
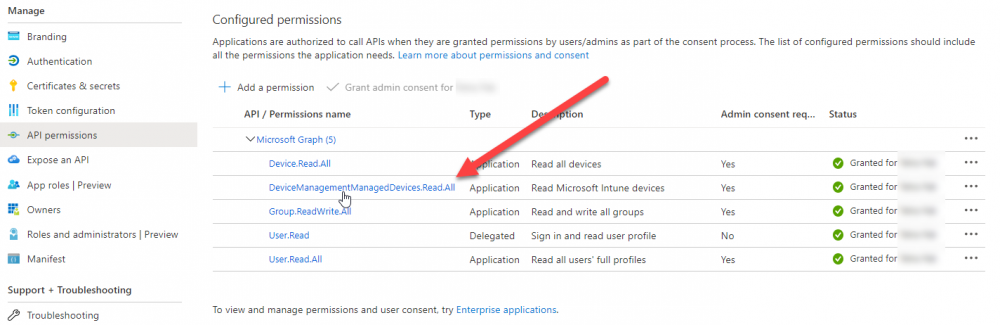
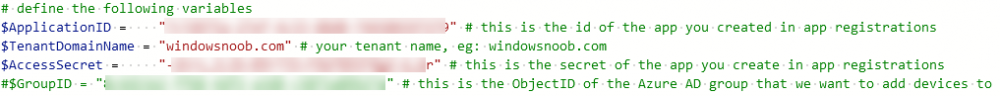
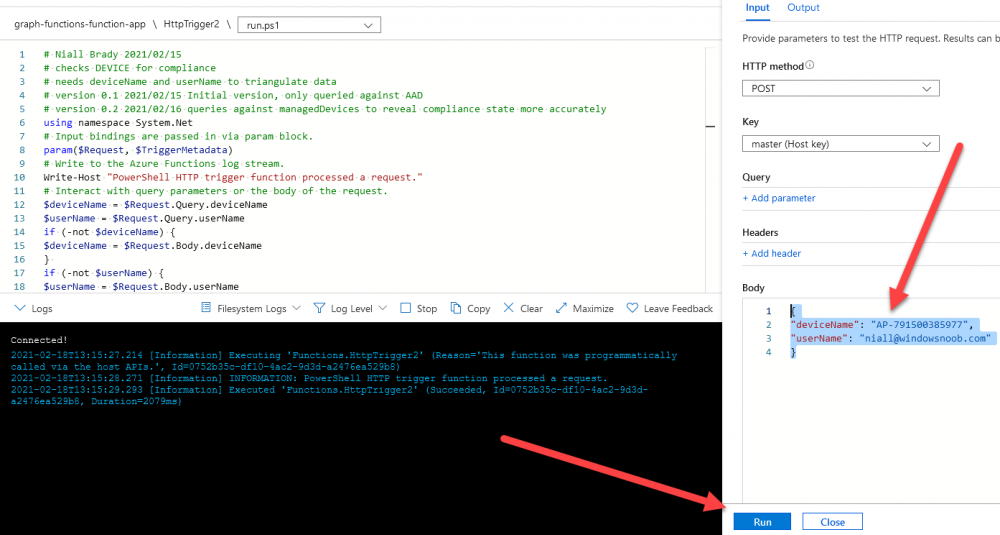
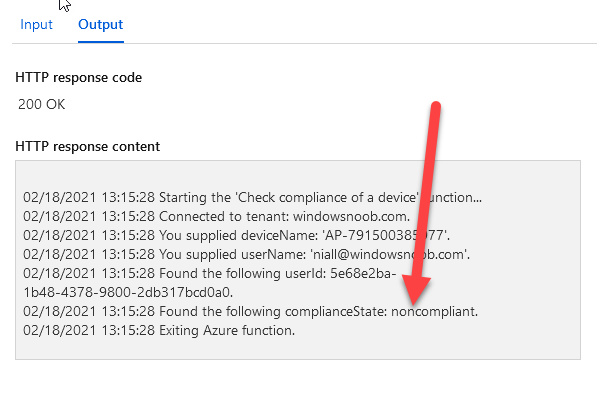
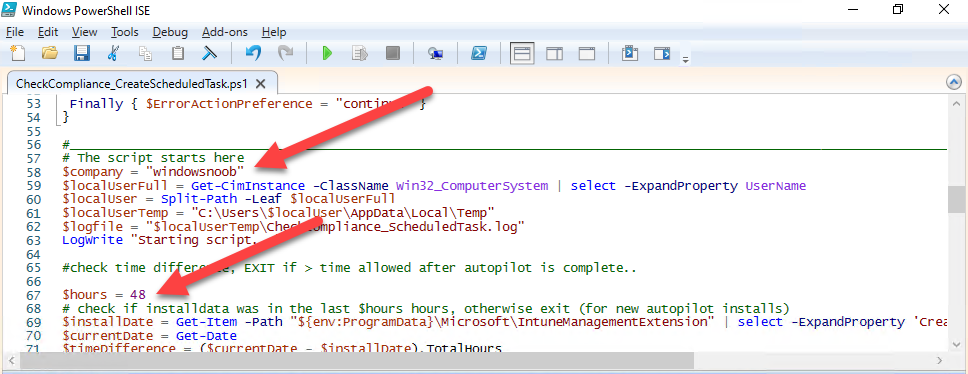
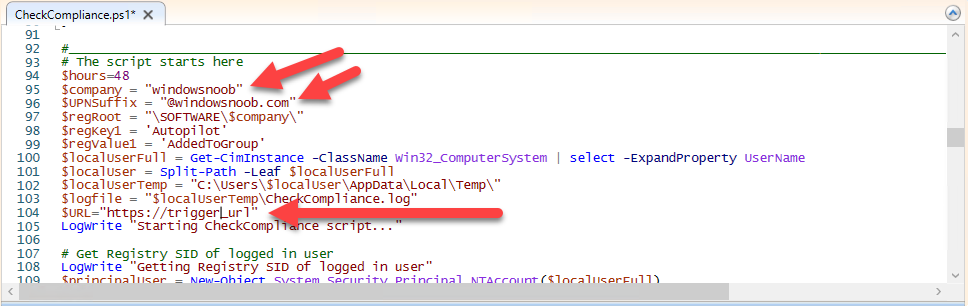
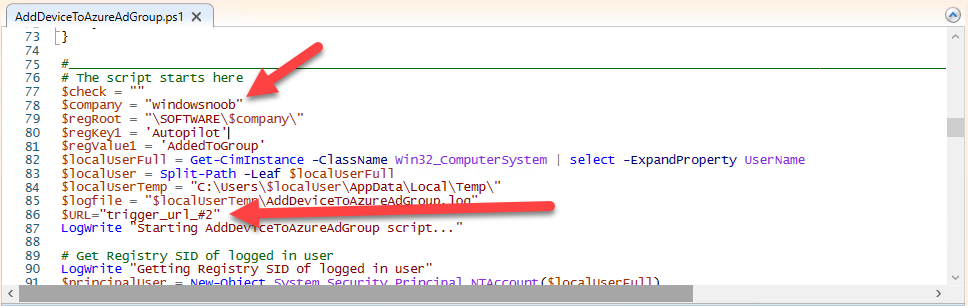
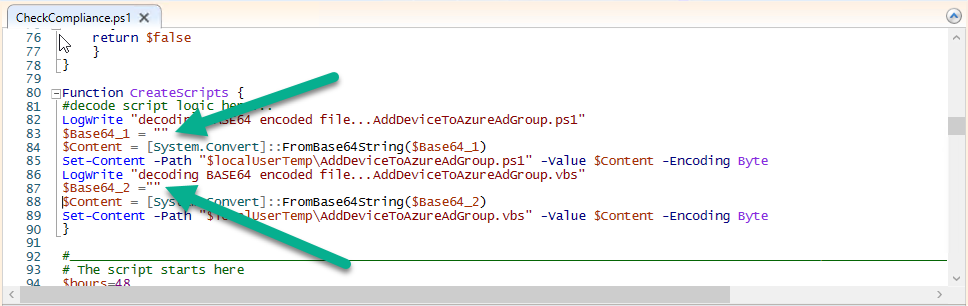
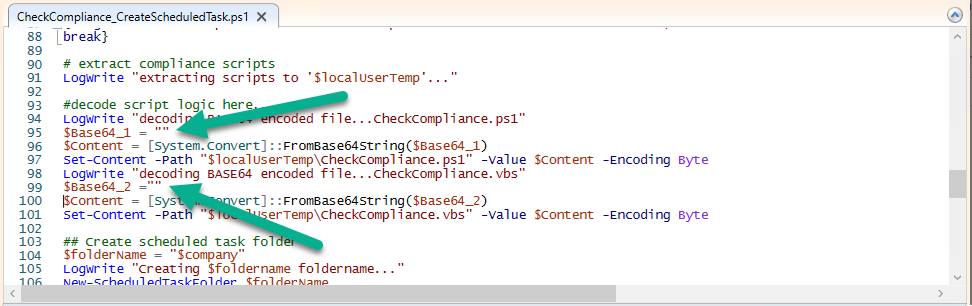
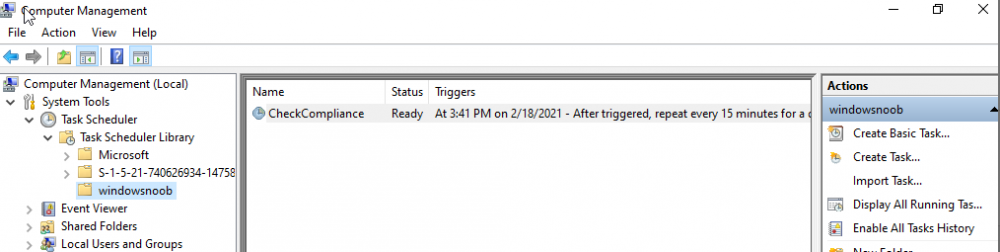
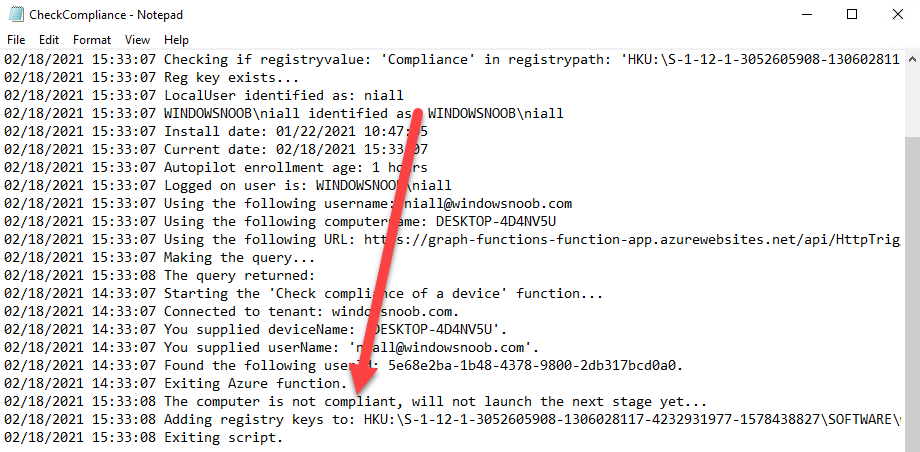
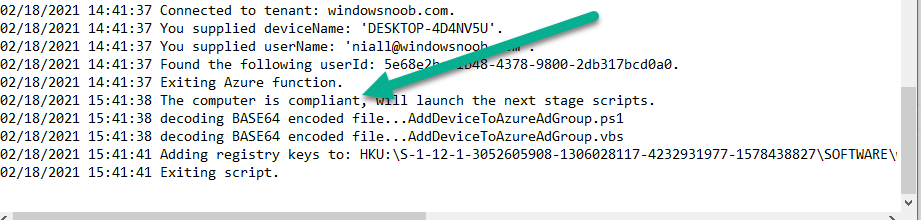
Introduction I've touched on this subject before where I used http triggers to add devices or users to an Azure AD group after Windows Autopilot was completed, however that solution did not check the compliance of the device prior to adding it to that Azure AD group, and you may have assigned profiles to that Azure AD group which depend on a compliant state. After Windows Autopilot is complete the compliance state of a device a can vary between any of the following states depending on various factors (usually time, and the number of compliance policies deployed and how they are configured). Compliant Not Compliant In grace period See ConfigMgr Not Evaluated The initial compliace state can eventually change to a state of compliant can take from a couple of minutes to some hours depending on what compliance policies you have configured. Refer to this docs post for more information about device compliance. Let's imagine you've configured a few compliance policies that check for the status of BitLocker Encryption of a device and Windows Defender anti malware definition updates. If the detected state of those polices don't match the configured policy then the device will be in a state of non compliance or even in something called in grace period. This post should help you solve the problem of adding devices (or users) to an Azure AD group after Windows Autopilot is complete, but only when they are in a state of Compliance that you want, in this case, Compliant. However it is complex, so before you start, please familiarize yourself with the following 2 posts, in fact I'd suggest you get the below working before proceeding as it will prepare you for this solution nicely. Adding devices to an Azure AD group after Windows Autopilot is complete - part 1 Adding devices to an Azure AD group after Windows Autopilot is complete - part 2 Understanding the solution So how does this all work ? The solution is actually made up of several scripts (and a trigger) listed below. CheckCompliance_CreateScheduledTask.ps1 The CheckCompliance_CreateScheduledTask.ps1 script will exit without doing anything if it detects that Autopilot was completed more than 48 hours ago. This script creates a scheduled task called CheckCompliance to run every 15 minutes. The scheduled task runs a CheckCompliance.vbs script which in turn runs a CheckCompliance.ps1 powershell script. Note: Both the CheckCompliance.vbs and CheckCompliance.ps1 scripts are embedded (base64 encoded) within the CheckCompliance_CreateScheduledTask.ps1 script. CheckCompliance.vbs This script is used to launch CheckCompliance.ps1 in hidden mode. CheckCompliance.ps1 This script does the actual call to the http trigger and provides the following data dynamically to the trigger: deviceName userName If the device is determined to be compliant it will then extract two more embedded scripts, then it runs AddDeviceToAzureAdGroup.vbs before finally deleting the scheduled task. Note: Both the AddDeviceToAzureAdGroup.vbs and AddDeviceToAzureAdGroup.ps1 scripts are embedded (base64 encoded) within the CheckCompliance.ps1 script. AddDeviceToAzureAdGroup.vbs This script simply runs the AddDeviceToAzureAdGroup.ps1 script in hidden mode. AddDeviceToAzureAdGroup.ps1 This script gathers the deviceId and userName and adds both items to an Azure AD Group. This uses the methodology of this blog post. httptrigger The http trigger itself uses the data delivered to it via the URL to determine compliance based on the data in managed Devices in Intune. How is compliance determined ? On a high level, compliance state is determined via queries in Microsoft Graph which you can test using Microsoft Graph Explorer. You can experiment yourself using a query such as the following. https://graph.microsoft.com/v1.0/users/USERID/managedDevices?$filter=deviceName eq 'ComputerName' Note: To manually test this you'll need to find valid UserID and ComputerName valuesfrom Intune and the results of this query would look something like below. Keep in mind that the UserID is reported as the id in Intune. The Scripted solution does the hard work for you, using Graph Explorer is where you start to test queries before creating the http trigger or back end scripts. Note that you'll need the following permissions granted in Graph Explorer to read this data (in addition to those listed in the previous blog post). Encoding/Decoding base64 scripts Included in the download are PowerShell scripts to encode/decode scripts. You can then edit them to your needs before re-encoding and adding the new base64 string to the appropriate variables. to set everything up please download the following scripts and extract to C:\Temp CheckCompliance.zip Make modifications as necessary to the CheckCompliance.ps1 and AddDeviceToAzureAdGroup.ps1 scripts before re-encoding. Save edited scripts to C:\Temp\CheckCompliance. To encode scripts simply run the relevant script shown below. There are two scripts, one for generating the base64 encoded scripts for the AddDeviceToAzureAdGroup and the other for the CheckCompliance scripts. The newly encoded scripts will be in the Encoded folder. Opening any of those 4 scripts will reveal the Base64 encoding data. Mark it all (Ctrl+a) and Copy it (Ctrl+c). Paste the Base 64 into the corresponding variable in the selected script. So to make changes to the AddDeviceToAzureAdGroup.ps1 script, simply edit the original Powershell script, then encode it, then copy the Base64 code into the corresponding section of the CheckCompliance.ps1 powershell script as shown below. Note that this is only an example, there are 4 embedded scripts in total, you'll get the hang of it soon enough. Decoding is the reverse process, and there are scripts available for you to do that also. Ok by now you should have all the above understood and working, time to deal with the solution. Step 1. Create a new http trigger I will assume you've already created a functionapp as per Step 4 of this blog post. If not, go ahead and create one and then return to this step. Next add the following code to your new http trigger. # Niall Brady 2021/02/15 # checks DEVICE for compliance # needs deviceName and userName to triangulate data # version 0.1 2021/02/15 Initial version, only queried against Azure AD devices # version 0.2 2021/02/17 queries against managedDevices to reveal compliance state more accurately using namespace System.Net # Input bindings are passed in via param block. param($Request, $TriggerMetadata) # Write to the Azure Functions log stream. Write-Host "PowerShell HTTP trigger function processed a request." # Interact with query parameters or the body of the request. $deviceName = $Request.Query.deviceName $userName = $Request.Query.userName if (-not $deviceName) { $deviceName = $Request.Body.deviceName } if (-not $userName) { $userName = $Request.Body.userName } # define the following variables $ApplicationID = "" # this is the id of the app you created in app registrations $TenantDomainName = "" # your tenant name $AccessSecret = "" # this is the secret of the app you create in app registrations # create the body $Body = @{ Grant_Type = "client_credentials" Scope = "https://graph.microsoft.com/.default" client_Id = $ApplicationID Client_Secret = $AccessSecret } # make initial connection to Graph $ConnectGraph = Invoke-RestMethod -Uri "https://login.microsoftonline.com/$TenantDomainName/oauth2/v2.0/token" -Method POST -Body $Body # get the token $token = $ConnectGraph.access_token # to improve logging... $triggerName = "Check compliance of a device" $a = Get-Date $body = " `n" $body = $body + "$a Starting the '$triggerName' function...`n" $body = $body + "$a Connected to tenant: $TenantDomainName.`n" # if $deviceName and $userName are provided do stuff.... if ($deviceName -and $userName) { $body = $body + "$a You supplied deviceName: '$deviceName'" + ".`n" $body = $body + "$a You supplied userName: '$userName'" + ".`n" # Start FinduserId $FinduserId = Invoke-RestMethod -Method Get -uri "https://graph.microsoft.com/v1.0/users/?`$filter=userPrincipalName eq '$UserName'" -Headers @{Authorization = "Bearer $token"} | Select-Object -ExpandProperty Value if ($FinduserId.userPrincipalName){ $FinduserId = Invoke-RestMethod -Method Get -uri "https://graph.microsoft.com/v1.0/users/?`$filter=userPrincipalName eq '$UserName'" -Headers @{Authorization = "Bearer $token"} | Select-Object -ExpandProperty Value | %{ $userId=$($_.Id) $body = $body + "$a Found the following userId: $userId"+ ".`n" } } else { Write-Host -ForegroundColor Green "$a UPN not found, FATAL." $body = $body + "$a UPN not found, FATAL." + ".`n" } # end $FinduserId # start FindmanagedDevice $FindmanagedDevice = Invoke-RestMethod -Method Get -uri "https://graph.microsoft.com/v1.0/users/$userId/managedDevices?`$filter=deviceName eq '$deviceName'" -Headers @{Authorization = "Bearer $token"} | Select-Object -ExpandProperty Value | %{ $complianceState=$($_.complianceState ) $body = $body + "$a Found the following complianceState: $complianceState"+ ".`n" } # end FindmanagedDevice # wrap things up... } $body = $body + "$a Exiting Azure function." # Associate values to output bindings by calling 'Push-OutputBinding'. Push-OutputBinding -Name Response -Value ([HttpResponseContext]@{ StatusCode = [HttpStatusCode]::OK Body = $body }) Note. Make sure to add in the missing details (application name, tenant, secret) as per step 8 (no need for a groupID in this one). Step 2. Assign API permissions This httptrigger requires more permissions than previously, namely it must be able to read managedDevices. Below are the permissions I've configured. Step 3. Test the solution in Azure In Azure, paste the following into the Input field of the httptrigger, obviously replace the deviceName and userName fields with valid data from your enterprise. { "deviceName": "AP-791500385977", "userName": "niall@windowsnoob.com" } Click on Run when ready If everything went well the compliance state will be returned. The http trigger is working ! Step 4. Customise the scripts After you've downloaded the scripts it's time to customize them somewhat. In the CheckCompliance_CreateScheduledTask.ps1 change the company name and if you want more time to become compliant, increase (or decrease) the hours from the default value of 48 hours. In the CheckCompliance.ps1 script edit the following lines, make sure to paste in the httptrigger url from your environment in here. In the AddDeviceToAzureAdGroup.ps1 script edit the following variables, use the httptrigger to Add devices (and users) url which you created in this blog post Next, save the changes, re-encode the scripts and add the newly encoded base64 changes to the following scripts. Start with the CheckCompliance.ps1 script, paste in your encoded text here (in between the "") And do the same for the CheckCompliance_CreateScheduledTask Save the changes. Step 5. Deploy the solution In Intune, deploy the CheckCompliance_CreateScheduledTask.ps1 to one or more users as required. That script should contain all the other scripts above embedded if you followed the instructions correctly. Step 6. Verify solution Enroll a new Autopilot device and after logging in for the first time you should see a new Scheduled task appear shortly after you login. There is a corresponding log file for this scheduled task creation stored in the C:\Users\<USERNAME>\AppData\Local\Temp Note: In the screenshot above the time difference has been manually set to 1 hour, even though the install date is a month previous, this is just for testing purposes. This process also extracts the CheckCompliance scripts..into the users Temp folder And when 15 minutes has passed the CheckCompliance powershell script will be triggered by the scheduled task. and in this particular example we can see the computer is not compliant yet, therefore it won't kick off the other actions, which extracts scripts and then runs a script to join Azure AD based on a trigger as per this blog post the scheduled task will keep checking for compliance every 15 minutes (you can edit the script to change that) until the device is compliant, and once it is, the final payload will trigger. Below you can see the device is now reported as Compliant from Intune... and as a result it decodes the AddDeviceToAzureAdGroup scripts and then runs them, finally it deletes the scheduled task and the solution is nearly complete. Those scripts are extracted to the users Temp folder and when run create a AddDeviceToAzureAdGroup.log file. The remaining actions are up to you, you can deploy policy or whatever to that Azure AD group and your device/users will magically end up in this Group and receive policy after Windows Autopilot is complete as long as they have become compliant first. That's it ! job done ?
-
- intune
- httptrigger
-
(and 3 more)
Tagged with:
-
This list of guides is a living index covering Windows 365 Cloud PC, Microsoft Intune or Configuration Manager. The Configuration Manager Current Branch releases are meant for your production deployments and the Technical Preview releases are for testing new upcoming features in the product, and are aimed at Lab use only. The PKI guides are added as https communication within ConfigMgr and Intune is desired. These guides are broken down into different sections: Windows 365 Microsoft Intune Configuration Manager - Current Branch Configuration Manager - Technical Preview Setting up PKI Note: The guides in each section are (mostly) sorted in the direction of oldest first. Windows 365 How can I delete a Windows 365 Cloud PC How can I use multiple monitors with Windows 365 Using Windows 365 with Linux Introducing the Windows 365 App How can I resize a Windows 365 Cloud PC USA Windows 365 User Group session – video available Windows 365 – Your connection failed – Error Code 0x3000047 How can I configure alerts for Windows 365 activity in Intune Getting started with Windows 365 - Part 1. Introduction Getting started with Windows 365 - Part 2. Provisioning an Azure Ad Joined Cloud PC Getting started with Windows 365 - Part 3. Provisioning a Hybrid Azure Ad Joined Cloud PC Getting started with Windows 365 - Part 4. Connecting to your Cloud PC Getting started with Windows 365 - Part 5. Managing your Cloud PC Getting started with Windows 365 - Part 6. Point in time restore Getting started with Windows 365 - Part 7. Patching your Cloud PCs with Windows Autopatch Getting started with Windows 365 - Part 8. Windows 365 boot Getting started with Windows 365 - Part 9. Windows 365 switch Getting started with Windows 365 - Part 10. Windows 365 offline Windows 365 app not connecting try this Using alternate ANCs in your Windows 365 provisioning policy Location redirection with Windows 365 Troubleshooting Windows 365 connection issues via the troubleshoot option in the Windows 365 app A quick look at some of the new features in the Windows 365 app An update about location redirection on Windows 365 Cloud PCs Windows 365 end user improvements - open in browser, open in desktop app Windows 365 web client can now use your camera New video: Windows 365 Switch in action Windows 365 boot and Windows 365 switch go GA! Automating Windows 365 part 1 - Introducing Graph and setting up Visual Studio code Automating Windows 365 part 2 - Using Graph X-Ray Automating Windows 365 part 3 - Provisioning Cloud PC's Automating Windows 365 part 4 - Managing your Cloud PC Automating Windows 365 part 5 - Cloud PC reports A quick look at Windows 365 Boot dedicated mode A quick look at Windows 365 Boot shared mode Getting more out of Windows 365 – Windows 365 Boot Getting more out of Windows 365 – Windows 365 GPU Getting more out of Windows 365 – Windows 365 Frontline Getting more out of Windows 365 – Windows 365 Switch Getting more out of Windows 365 – Securing your Windows 365 PC’s Updating the Windows app to the latest version A quick look at using Windows 365 Cloud PC’s via Motorola Thinkphone Automated Provisioning of Windows 365 Cloud PCs: Advanced Scripts Moving one or more Windows 365 Cloud PCs to another location Recovering a Windows 365 Cloud PC that was de-provisioned due to license expiration How healthy are your Windows 365 or Azure Virtual Desktop PC’s ? Using remediation scripts in Intune to grab Windows 365 health check logs Windows 365 and the External Identity preview – using a guest account to access Cloud PCs Cloudy With a Chance of Apps Microsoft Intune How can I find out version info about Intune Preview in Azure ? How can I unlock Windows Holographic for Business features in Intune Preview? How can I determine how long a blade loads in Intune Preview in Azure ? How can I check the status of my Intune service ? Intune Preview in Azure get’s a new look and Software Updates for Windows 10 ! What is Windows Information Protection and how can I use it to protect Enterprise data on Windows 10 devices using Intune Using Intune to enable WIP to protect Enterprise data on Windows 10 devices (MAM-WE) Getting started with Microsoft Graph and using PowerShell to automate things in Intune How can I integrate Microsoft Store for Business with Intune in Azure How can I create a dynamic group containing all Windows 10 version 1709 in Intune in Azure ? How can I enable MDM auto-enrollment in Azure How can I customize the start screen in Windows 10 using Intune How can I use Windows AutoPilot with a Proxy ? Troubleshooting “Something went wrong error 801c0003” during enrollment via Windows AutoPilot and Microsoft Intune Configuring BitLocker in Intune - Part 1. Configuring BitLocker Configuring BitLocker in Intune - Part 2. Automating Encryption Configuring BitLocker in Intune - Part 3. Testing the scripts How can I send notification messages using PowerShell in Microsoft Intune How can I deploy custom favorites in Microsoft Edge to Windows 10 devices using Microsoft Intune Managing devices with Microsoft Intune: What’s new and what’s next – my notes (Part 1 – new features) Managing devices with Microsoft Intune: What’s new and what’s next – my notes (Part 2 – iOS) Managing devices with Microsoft Intune: What’s new and what’s next – my notes (Part 3 – Android) Managing devices with Microsoft Intune: What’s new and what’s next – my notes (Part 4 – macOS) Managing devices with Microsoft Intune: What’s new and what’s next – my notes (Part 5 – Windows) Learn how to leverage Intune support for Microsoft Graph and PowerShell to enable powerful automation and IT security- my notes How Microsoft uses Intune internally to manage Windows devices Android device management with Microsoft Intune – Part 1. Partnerships Android device management with Microsoft Intune – Part 2. Deployment Scenarios Android device management with Microsoft Intune – Part 3. Dedicated device management Android device management with Microsoft Intune – Part 4. Coming soon and what’s new How can I create dynamic groups for different HoloLens devices in Microsoft Intune Troubleshooting app deployment in Windows Autopilot Configuring the Registered Owner and Organization in Windows Autopilot delivered PCs Removing company data from Endpoint Manager enrolled phones Office 365 issues after Windows Autopilot Displaying a welcome page after Windows Autopilot completes Adding devices to an Azure AD group after Windows Autopilot is complete - part 1 Adding devices to an Azure AD group after Windows Autopilot is complete - part 2 Gathering logs and sending an email when resetting Windows Autopilot - part 1 Gathering logs and sending an email when you need to reset Windows Autopilot - part 2 Gathering logs and sending an email when you need to reset Windows Autopilot - part 3 Adding devices or users to an Azure AD group after Windows Autopilot is complete but only when the device is marked as Compliant Using the updated & secure Retire My PC app via Company Portal Prompting standard users to confirm or change Regional, Time Zone and Country settings after Windows Autopilot enrollment is complete Encrypting devices during Windows Autopilot provisioning (WhiteGlove) - Part 1 Encrypting devices during Windows Autopilot provisioning (WhiteGlove) - Part 2 Encrypting devices during Windows Autopilot provisioning (WhiteGlove) - Part 3 https://www.niallbrady.com/2024/04/06/pc-buyback-for-windows-autopilot-devices-part-2/ PC Buyback for Windows Autopilot devices – part 1 PC Buyback for Windows Autopilot devices – part 2 PC Buyback for Windows Autopilot devices – part 3 Deploying KB5030310 to devices as a Win32 app for Copilot Using remediation scripts to automate a setting for Copilot How can I disable Copilot ? Getting started with Azure Key Vault Expediting updates using Windows Autopatch August Cumulative update causing Windows reset problems Configuration Manager Current Branch Installation - How can I install System Center Configuration Manager (Current Branch) Configuring Discovery - How can I configure discovery for System Center Configuration Manager (Current Branch) Configuring Boundaries - How can I configure boundaries in System Center Configuration Manager (Current Branch) Using Updates and Servicing in Offline mode - How can I use Updates and Servicing in Offline mode in System Center Configuration Manager (Current Branch) Using Updates and Servicing in Online mode - How can I use Updates and Servicing in Online mode in System Center Configuration Manager (Current Branch) Setting up the Software Update Point - How can I setup Software Updates in System Center Configuration Manager (Current Branch) Installing the Client agent - How can I configure client settings and install the ConfigMgr client agent in System Center Configuration Manager Current Branch Upgrading to System Center Configuration Manager (Current Branch) version 1602 from System Center Configuration Manager (Current Branch) version 1511 How can I use the Upgrade Task Sequence in System Center Configuration Manager (Current Branch) ? How can I use servicing plans in System Center Configuration Manager (Current Branch) to upgrade Windows 10 devices ? How can I deploy Windows 10 with MDT 2013 Update 2 integrated with System Center Configuration Manager (Current Branch) Setting up PKI Part 1 - Introduction and server setup Part 2 - Install and do initial configuration on the Standalone Offline Root CA Part 3 - Prepare the HTTP Web server for CDP and AIA Publication Part 4 - Post configuration on the Standalone Offline Root CA Part 5 - Installing the Enterprise Issuing CA Part 6 - Perform post installation tasks on the Issuing CA Part 7 - Install and configure the OCSP Responder role service Part 8 - Configure AutoEnroll and Verify PKI health How can I configure System Center Configuration Manager in HTTPS mode (PKI) - Part 1 How can I configure System Center Configuration Manager in HTTPS mode (PKI) - Part 2 New video: Fixing expired Root CA CDP and Crypt_E_REVOCATION_OFFLINE problems cheers niall
-
- 4
-

-

-
- current branch
- step by step
- (and 12 more)