Search the Community
Showing results for tags 'wannacry'.
-
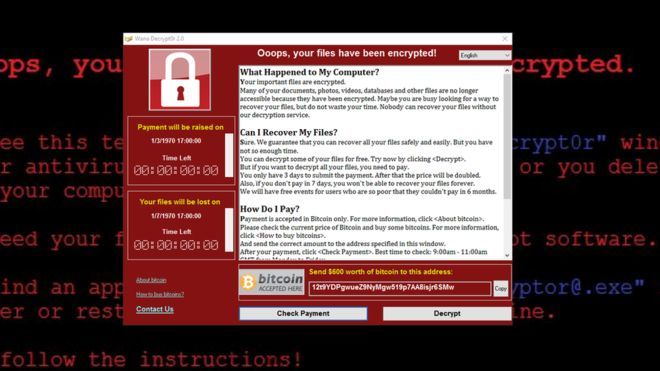
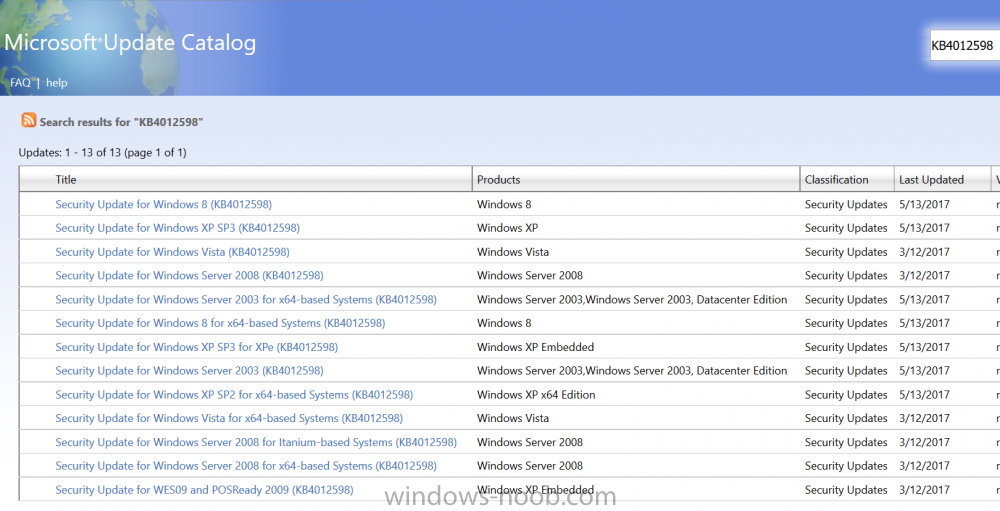
WannaCry was a disaster that could have been prevented if people took notice. If you didn’t hear about it you must have been asleep, here is a refresher. After WannaCry, most businesses took notice and updated their operating systems, patched them and took measures to avoid a furth...
-
- server 2003
- ransomware
-
(and 5 more)
Tagged with: