Search the Community
Showing results for tags 'web server'.
-
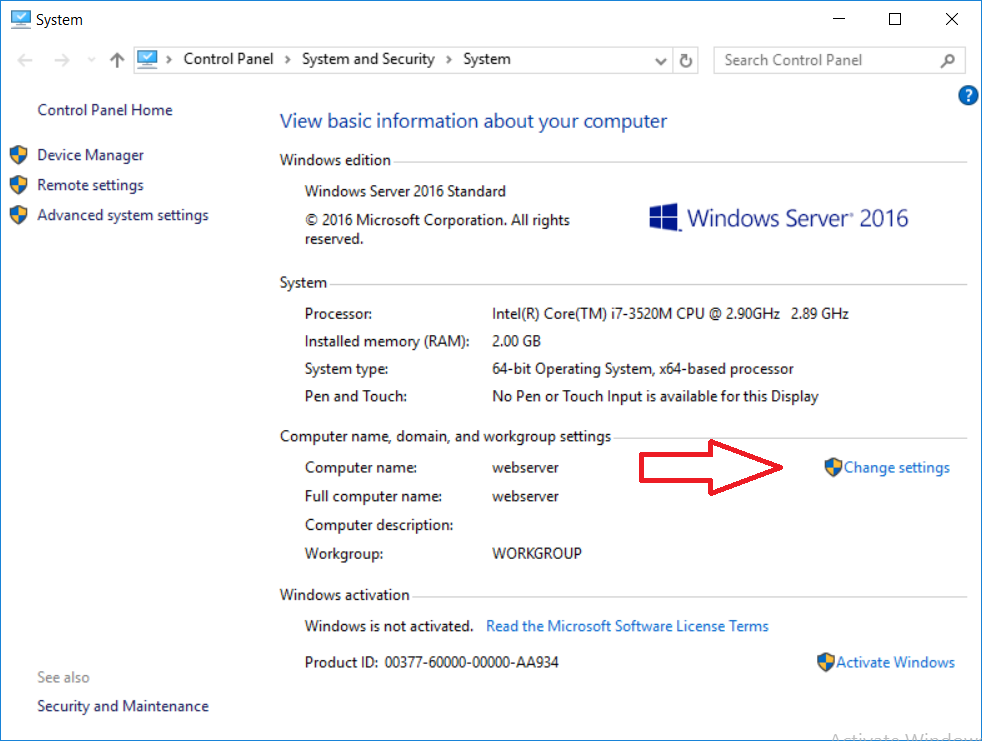
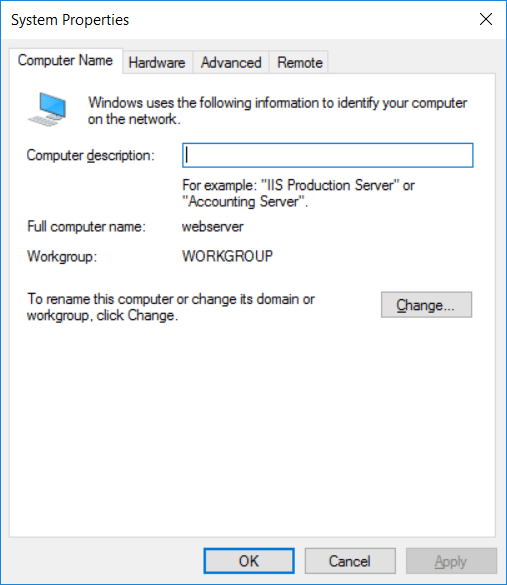
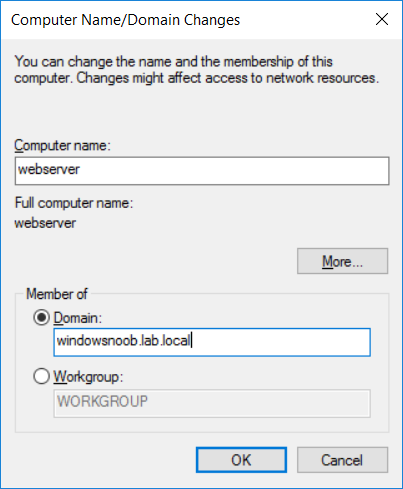
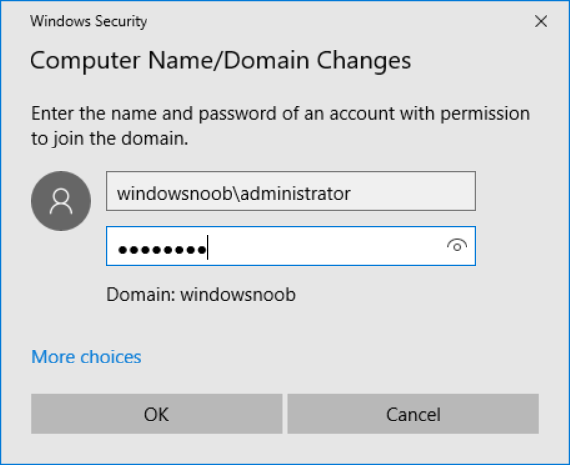
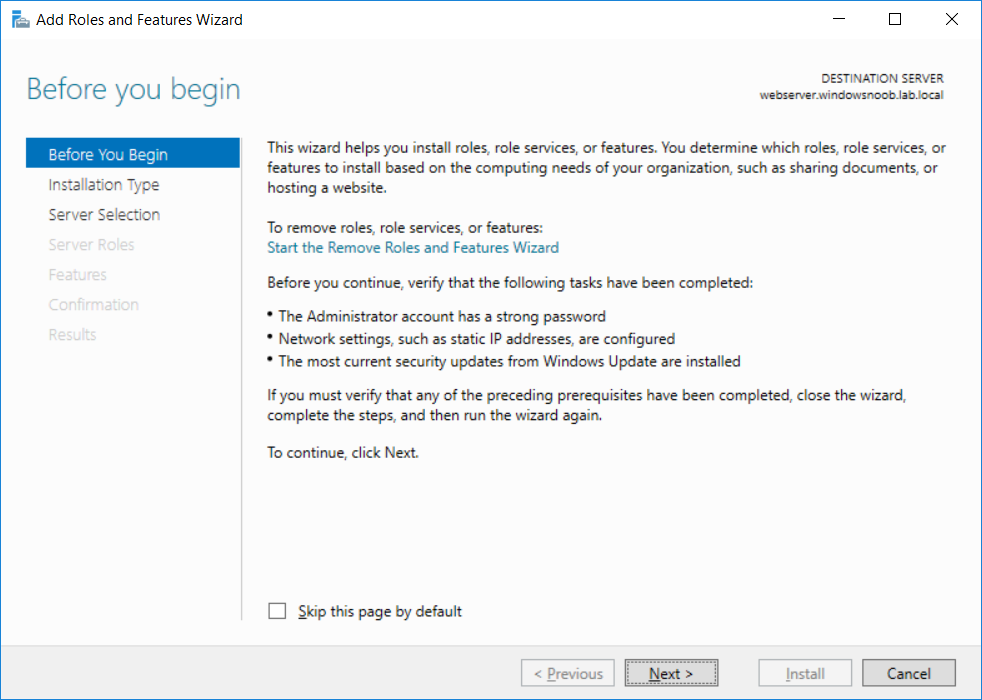
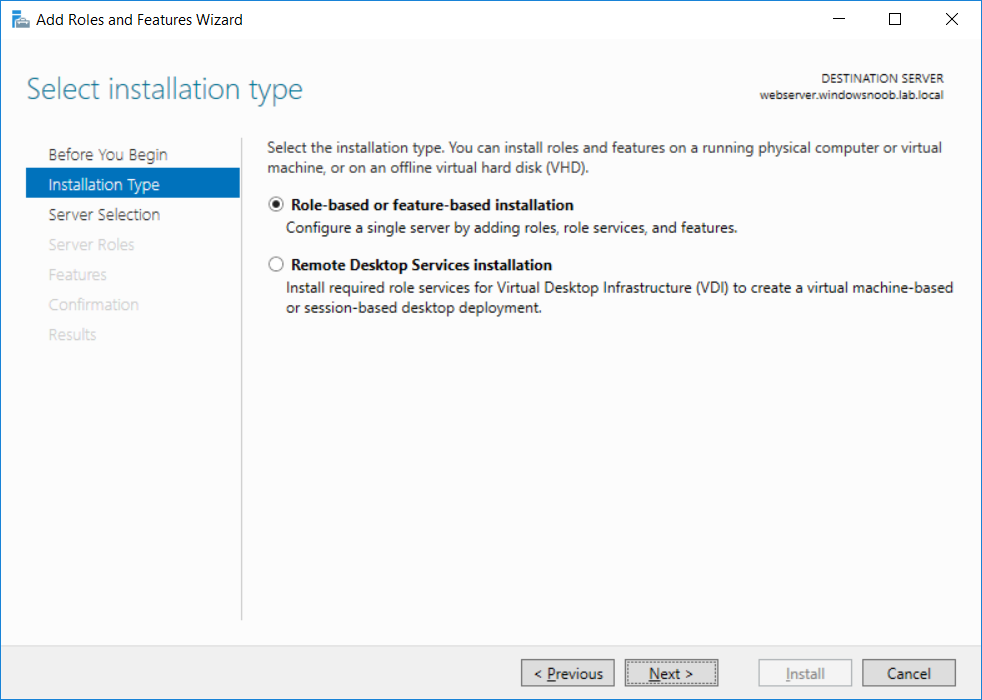
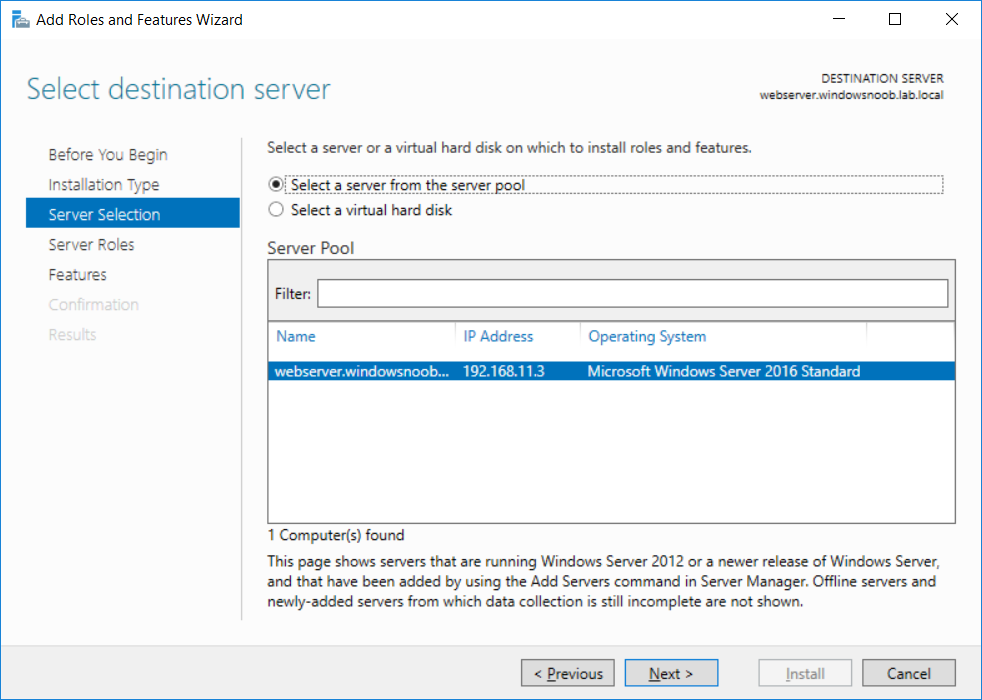
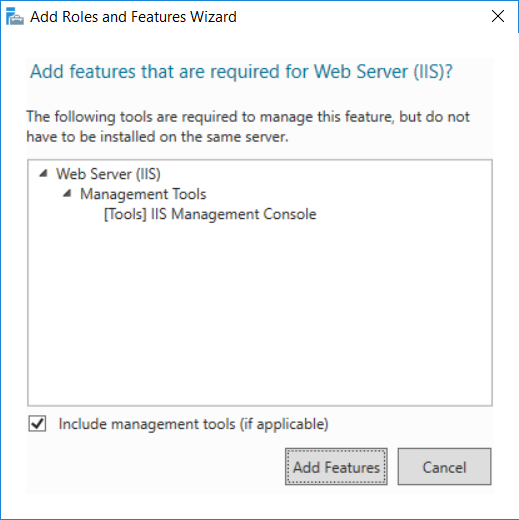
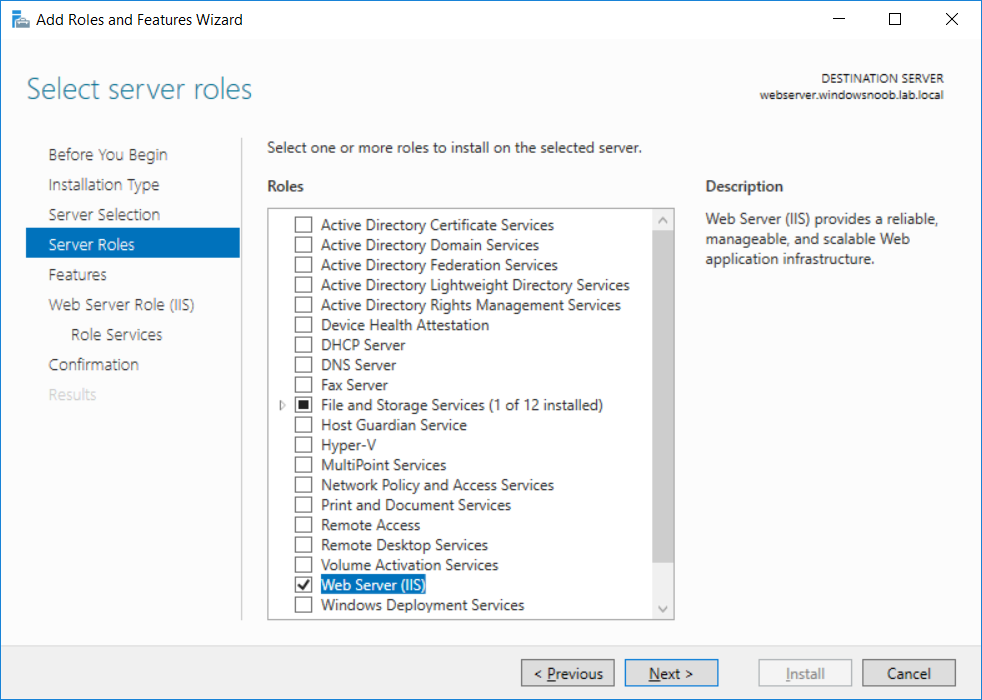
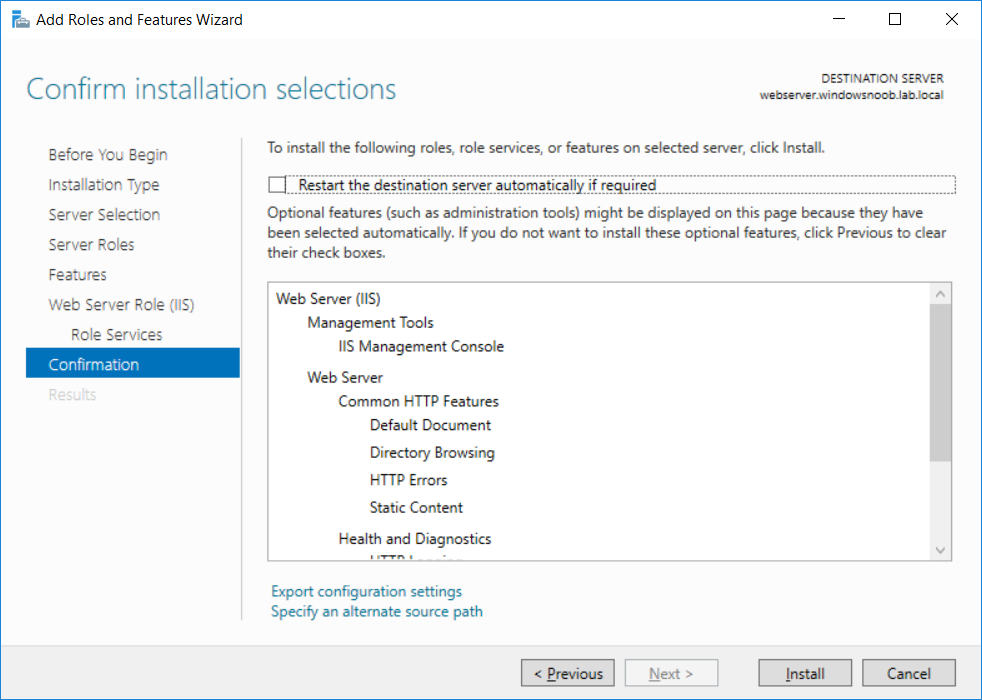
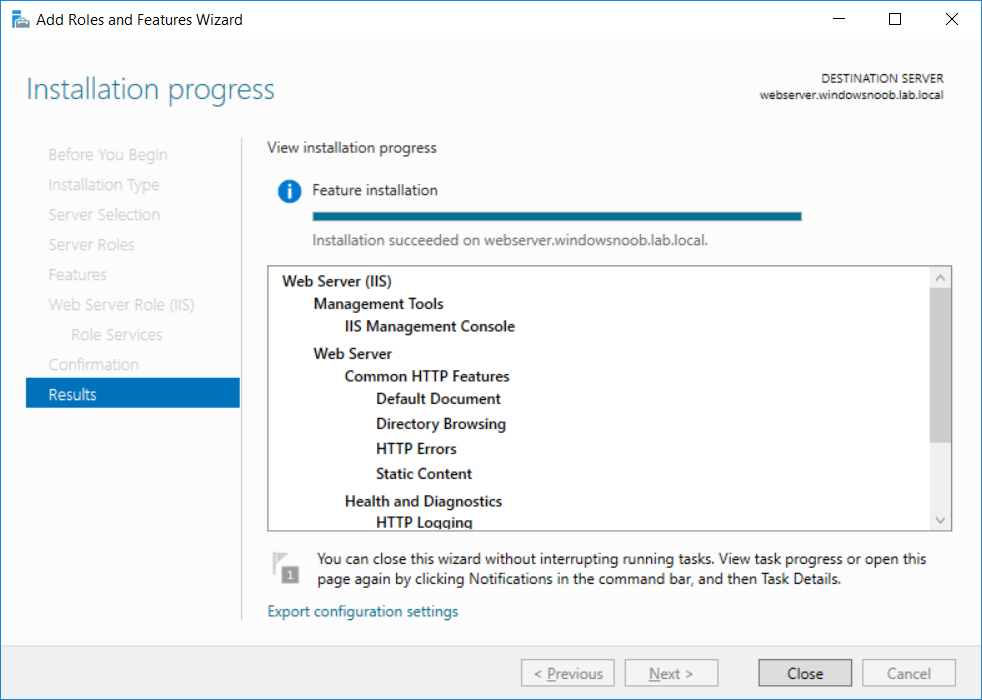
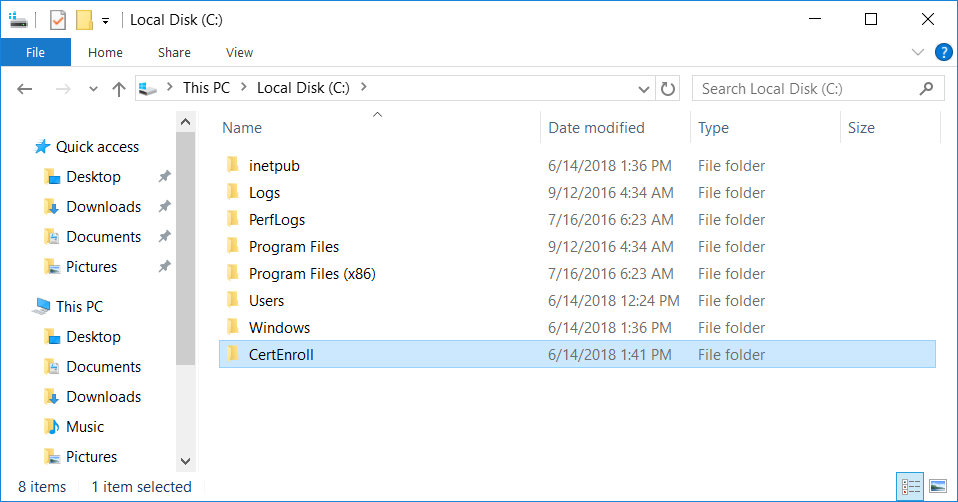
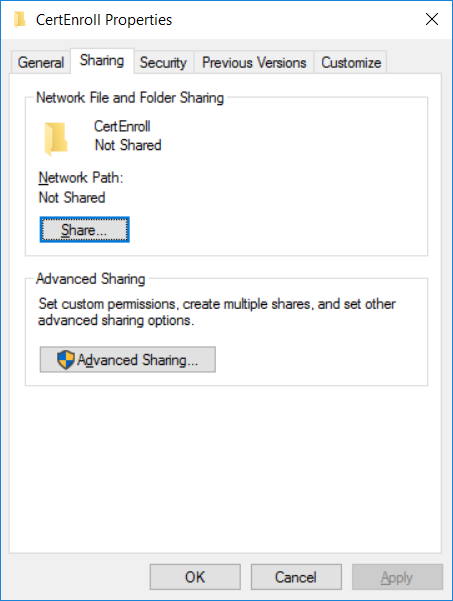
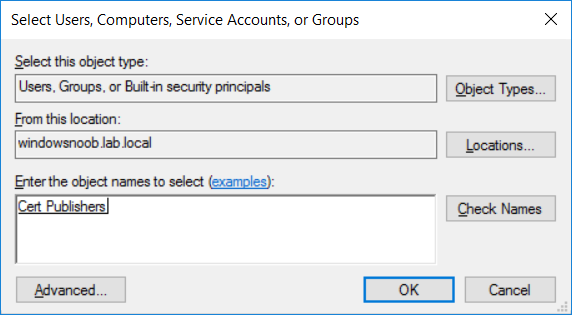
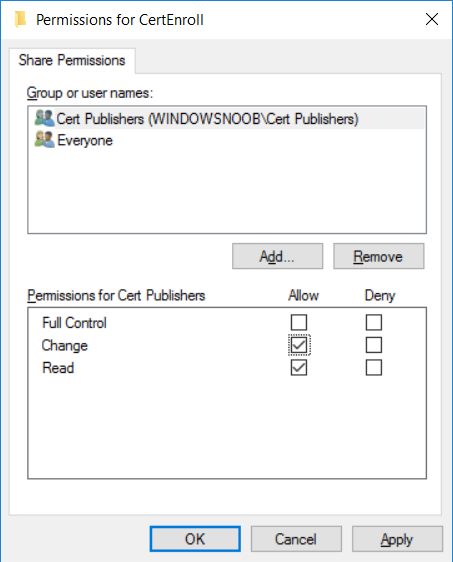
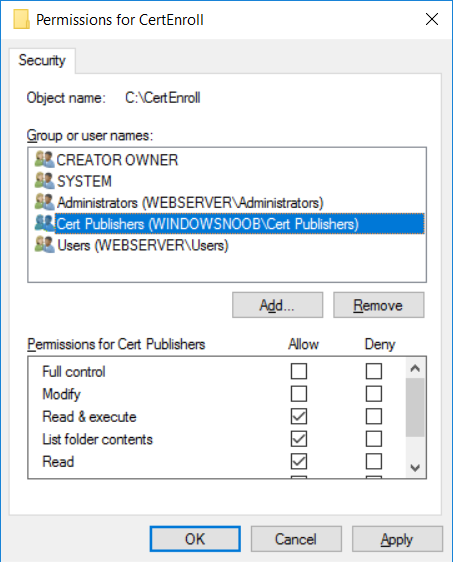
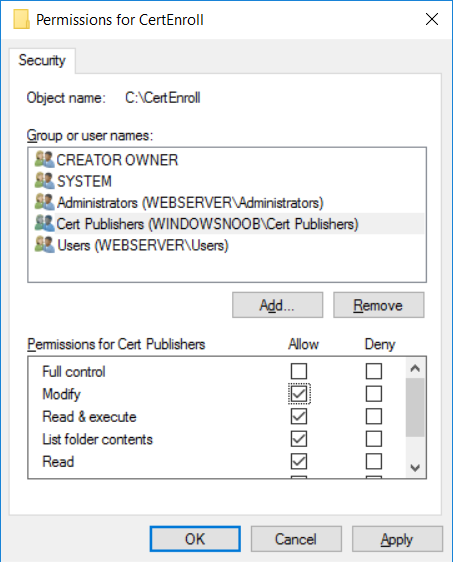
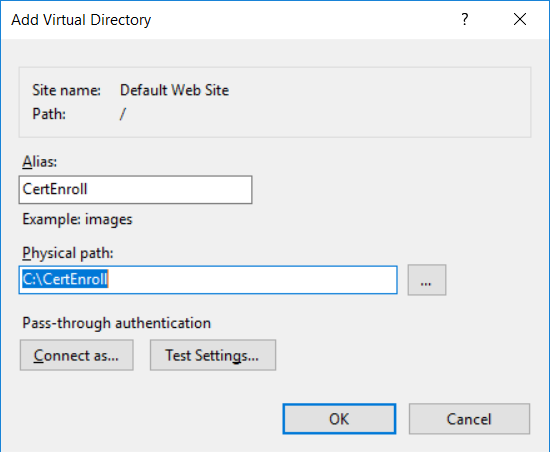
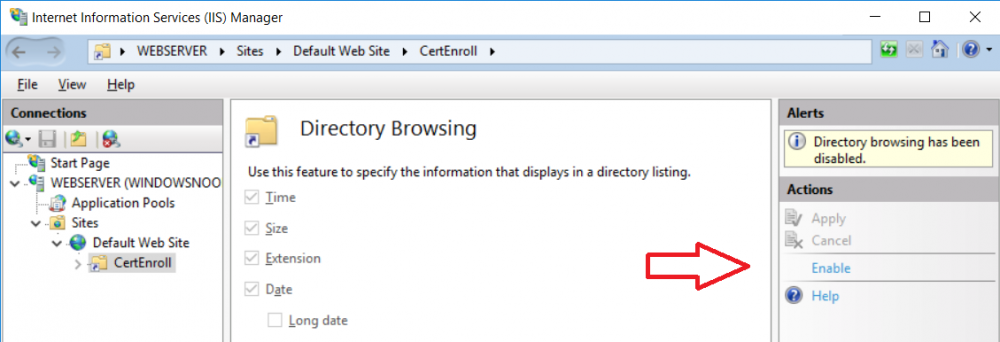
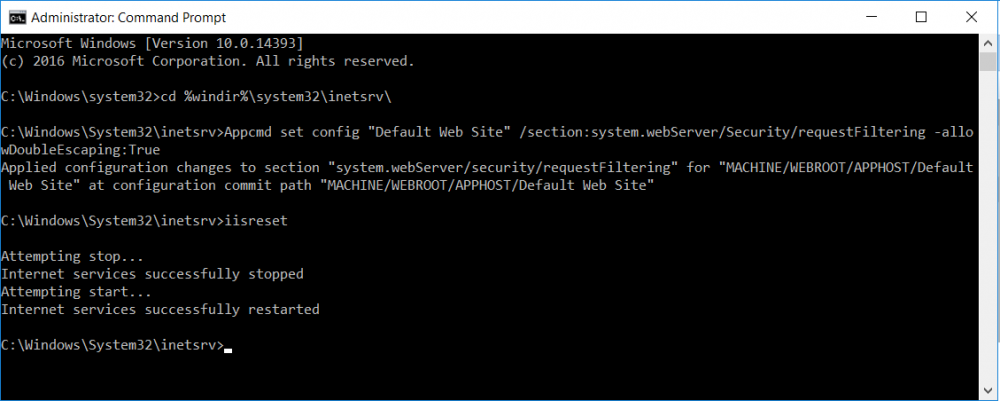
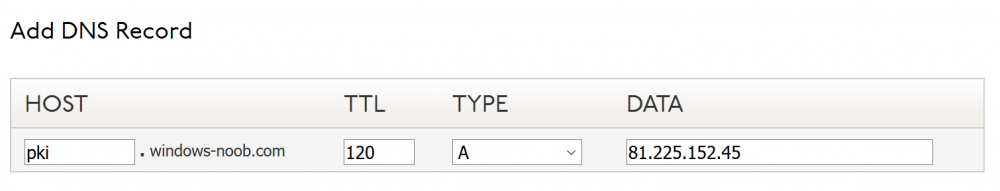
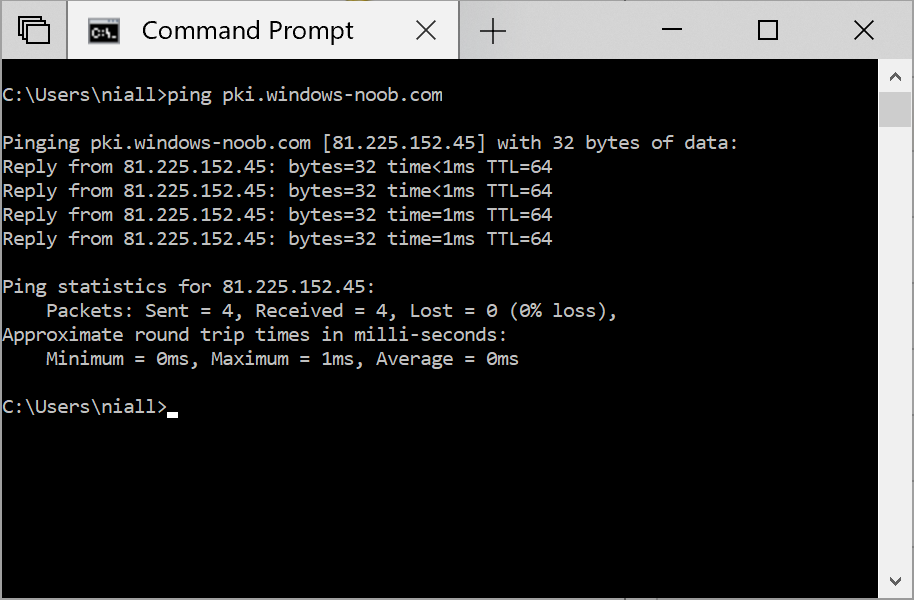
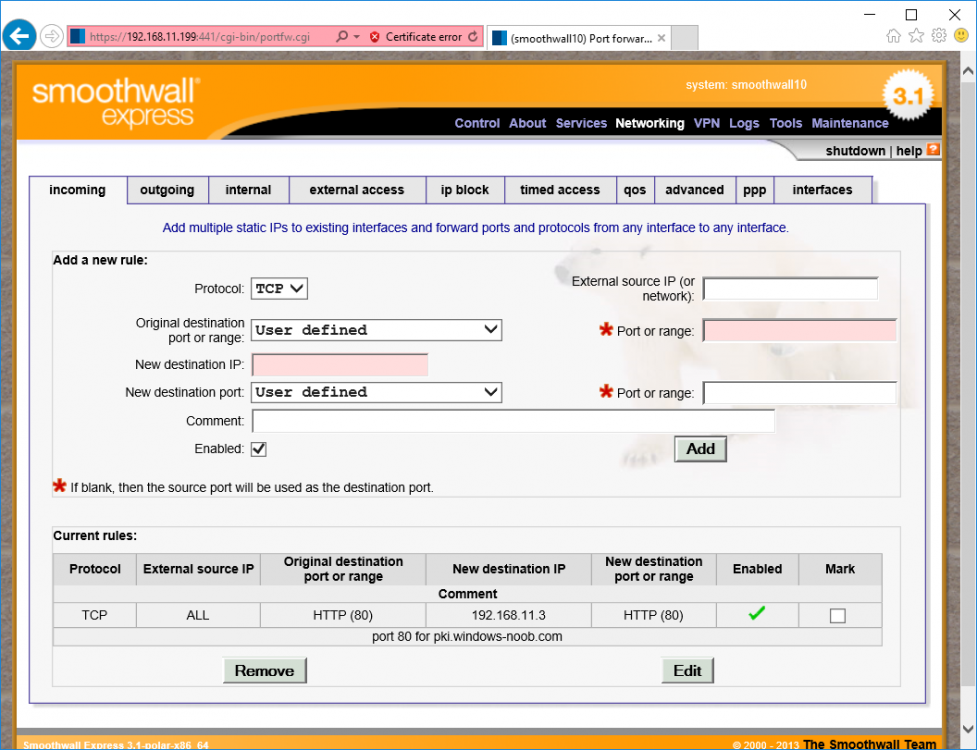
This series is comprised of different parts, listed below. Part 1 - Introduction and server setup Part 2 - Install and do initial configuration on the Standalone Offline Root CA Part 3 - Prepare the HTTP Web server for CDP and AIA Publication (this part) Part 4 - Post configuration on the Standalone Offline Root CA Part 5 - Installing the Enterprise Issuing CA Part 6 - Perform post installation tasks on the Issuing CA Part 7 - Install and configure the OCSP Responder role service Part 8 - Configure AutoEnroll and Verify PKI health In part 1 of this series, you configured your LAB for a 2 tier PKI hierarchy running on Windows Server 2016. You used PowerShell to create some virtual machines, and then installed Windows Server 2016, Windows 10 Enterprise version 1803 and optionally Smoothwall 3.1 before configuring the IP address scheme and Computer Names on the virtual machines. Finally you configured ADDS on DC01 so that you have a working Domain Controller for the rest of this LAB. In part 2 you installed and did the initial configuration on the Standalone Offline Root CA. In this part you will prepare the HTTP Web Server for CDP and AIA Publication. But before you get started with that, please have a read below of what a CDP and AIA actually are. What is a CDP ? A CDP (CRL Distribution Point) is an extension that contains links to the CRL of the issuer of the certificate which is being verified (1). What is an AIA ? An AIA (Authority Information Access) is an extension that contains links to the certificate of the issuer of the certificate which is being verified. Step 1. Join the web server computer to the domain When you installed the web server virtual machine (#11_Webserver) in part 1, it was workgroup joined. To join the domain do as follows. Logon to the web server virtual machine as Administrator. In Windows File Explorer, right click on This PC and choose Properties. Click on Change Settings beside Computer name, domain and workgroup settings. In the System Properties screen, click on Change. In the Member of field select Domain and enter the domain name you configured in part 1. enter credentials required for Domain join membership (eg: windowsnoob\administrator) click OK and click OK again when prompted with the welcome click OK Click OK, click Close then click Restart Now. After the reboot login to the domain as windowsnoob\administrator Alternatively, to join the domain automatically, use the joindomain.ps1 PowerShell script which you can download from here. JoinDomain.ps1 1. Copy the script to C:\Scripts on the webserver. 2. Edit the variables (lines 16-18) as desired before running. 3. Start Windows PowerShell ISE as Administrator and run the script by clicking on the green triangle. Step 2. Install the Web Server (IIS) Role Logon to the web server as windowsnoob\administrator and open Server Manager, select Add Roles and Features. In the wizard that appears click Next. Click Next and select Role-based or feature-based installation. Click Next and Select Select a server from the server pool, ensure that webserver.windowsnoob.lab.local is selected. Click Next and select Web Server(IIS) from the choices available on the Select server roles page, if prompted to Add features that are required for Active Directory Certificate Services, click Add features. Here you can see the Web Server (IIS) role selected. On Select features click Next. In the introduction to Web Server (IIS) screen, select Next. Accept the defaults and click Next. on the Confirm Installation Selections screen click Install. Click Close when the installation succeeds. Step 3. Create a CertEnroll Folder and grant Share & NTFS Permissions to the Cert Publishers group Create the CertEnroll Folder Now you need to create a shared folder where certificates and delta certificates can be stored from the PKI infrastructure. Open Windows File Explorer and then browse to the C:\ drive, Create a folder called CertEnroll at the root of the drive. Share the CertEnroll folder Right-click on the CertEnroll folder and select Properties. On the CertEnroll Properties page select the Sharing tab to configure share permissions. Click on the Advanced Sharing option and then select Share this folder. Click on Permissions and then click Add, on the Select Users or Groups page, in the Enter the object names to select, type windowsnoob\Cert Publishers and then click OK. On Permissions for CertEnroll dialog box, select the Cert Publishers group and then in the Allow column select Change permission. Click OK twice to go back to the CertEnroll Properties page. Edit NTFS permissions on the CertEnroll folder Select the Security tab and click Edit to configure NTFS permissions. On Permissions for CertEnroll page click Add. On the Select Users or Groups page, under the Enter the object names to select, enter windowsnoob\Cert Publishers and then click OK. On the Permissions for CertEnroll page highlight the Cert Publishers group and then under the Allow column select the Modify permission and then click OK. On the Permissions for CertEnroll page, click OK to close the window and click OK again to close CertEnrolls properties page. Step 4. Create a Virtual Directory in IIS Ensure you are logged on to webserver as windowsnoob\Administrator. Click Start, select Administrative Tools and then select Internet Information Services (IIS) Manager. In the Connections pane, expand WEBSERVER and then expand Sites. Right-click on Default Web Site and select Add Virtual Directory. On the Add Virtual Directory page, in Alias, type CertEnroll and for Physical path, type C:\Certenroll, and then click OK. In the Connections pane, under the Default Web Site, ensure the CertEnroll virtual directory is selected then in the CertEnroll Home pane, double-click on Directory Browsing. In the Actions pane click Enable. Step 4. Enable Double Escaping on the IIS Server Allowing double escaping makes it possible for the web server to host Delta CRLs. For more information about this see KB Article 942076 (3). Ensure you are logged on to the webserver as windowsnoob\Administrator. Open an Administrative Command Prompt. Then enter the following cd %windir%\system32\inetsrv\ and press ENTER. Type following command and press Enter. Appcmd set config "Default Web Site" /section:system.webServer/Security/requestFiltering -allowDoubleEscaping:True Type the following to restart IIS. iisreset and press ENTER. Step 5. Create a DNS record for externally accessible website address To answer requests for OCSP and CRL, AIA via a publicly available URL, login to your DNS provider and create a new DNS record for your chosen public URL, eg: http://pki.windows-noob.com Note: http://pki.windows-noob.com is a website address that I own and use, and I'm using it in this guide to show you what you need to do, obviously you need to use your own website address, for example http://pki.yourdomain.com. This should point to the IP address of your internet connection that is being shared via the smoothwall. Once it's setup, you can verify pinging the URL Lastly, you need to configure your Smoothwall (or use another method) to port forward port 80 (http) internet requests to the webserver. To do that, login to https://192.168.11.199:441 (the Smoothwall IP address) via the Internet Explorer Web browser on the WebServer. Note that you may have to disable IE enhanced security information temporarily to allow access. Once connected, login as Admin/password, which you defined when you installed the Smoothwall. Below you can see the Port Forward I've configured for port 80 requests. After doing so, anyone can browse to http://pki.windows-noob.com using a web browser which means they'll be able to retrieve CRL's when they are published to http://pki.windows-noob.com/certenroll Join me in part 4 to further configure the Standalone Offline Root CA. Recommended reading (1) - https://www.sysadmins.lv/blog-en/root-certification-authority-ca-cdp-and-aia-extension-question.aspx (2) - https://blogs.technet.microsoft.com/nexthop/2012/12/17/updated-creating-a-certificate-revocation-list-distribution-point-for-your-internal-certification-authority/ (3) - http://support.microsoft.com/kb/942076